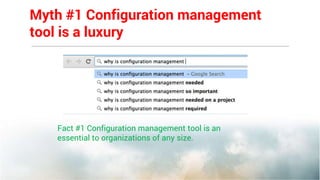
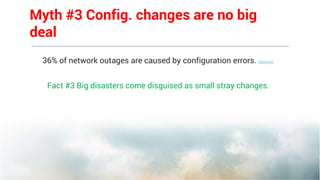
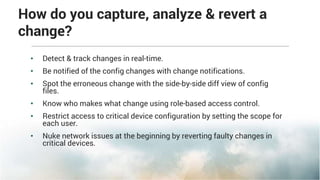
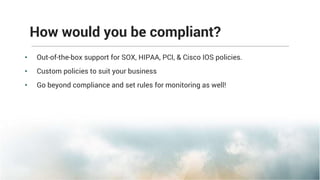
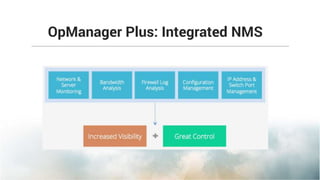
This document summarizes the key features and benefits of Network Configuration Manager (NCM), a configuration management tool. NCM provides increased network efficiency, stability and control through preventive detection of faulty changes. It allows for faster troubleshooting and restoration of service using automated backups and restoration of pre-configured configurations. NCM enhances compliance through out-of-the-box support for regulations and allows custom policies for monitoring networks. It also improves productivity by automating redundant tasks through configuration templates and workflows.