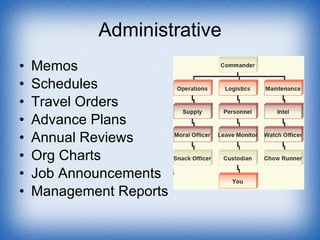
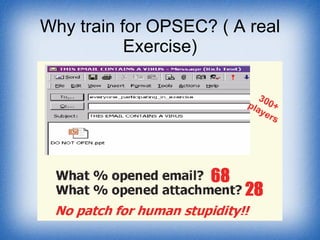
The document discusses vulnerabilities and indicators related to operational security (OPSEC). It defines indicators as detectable activities that can reveal sensitive information or vulnerabilities. Adversaries look for patterns and signatures to build profiles of organizations. Common vulnerabilities include unsecured discussions, lack of security policies, and stereotyped operations. Examples of vulnerabilities are from various areas like operations, physical environment, personnel, and more. The document outlines specific communication, computer, and administrative vulnerabilities and encourages awareness of indicators in family, personnel, public affairs and other areas.