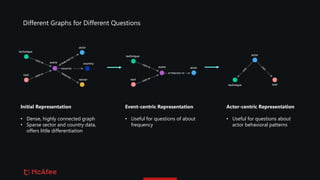
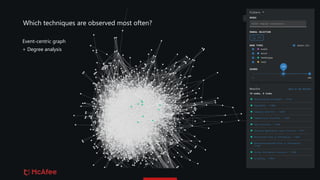
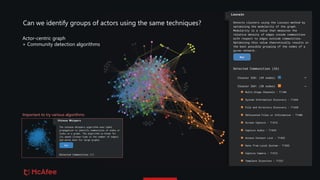
The document discusses the use of graphs for analyzing and visualizing cyber threats and attack data within the MITRE ATT&CK framework. It highlights various representation methods, such as event-centric and actor-centric graphs, to identify patterns and trends among threat actors and techniques. Key questions include the granularity of data, the completeness of received information, and potential additional data sources to enhance threat intelligence analysis.

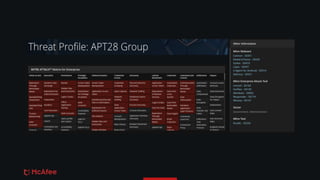








![Data Representation
• MISP's granularity level might not be good enough if we're only using MITRE
metadata to differentiate threat actors
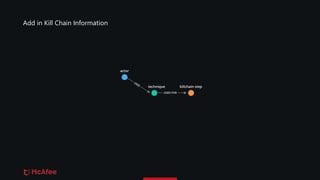
• MISP allow us to associate MITRE techniques with an event, but not to specify
which kill chain step the technique was used for in the context of the event
• Overall, recorded threat actors seem to be using the same techniques
• Desired mapping (actor) - [uses] -> (technique:step)
Remaining Issues](https://image.slidesharecdn.com/thinkingraphs-vm-210120132622/85/ATTACKers-Think-in-Graphs-Building-Graphs-for-Threat-Intelligence-18-320.jpg)