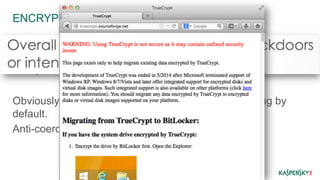
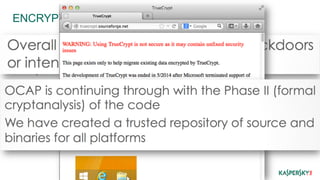
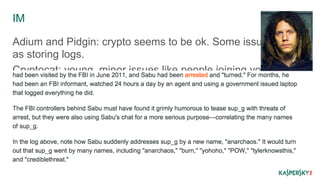
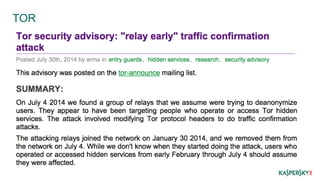
This document discusses operational security (OPSEC) best practices for security researchers. It begins by defining OPSEC and noting its importance for protecting sensitive work from adversaries. It then outlines various adversary threats, including common cybercriminals, organized groups, government agencies, and massive surveillance capabilities. The document provides guidance on implementing OPSEC at both individual and group levels, including compartmentalizing information, training others, and being careful about digital identities and tools. Key recommendations include encrypting all communications and data, using secure email, chat and phones, avoiding metadata leaks, and maintaining high OPSEC standards even internally. The overall message is that while OPSEC is difficult, researchers should start applying basic practices to protect their work and avoid becoming