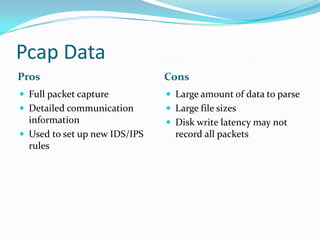
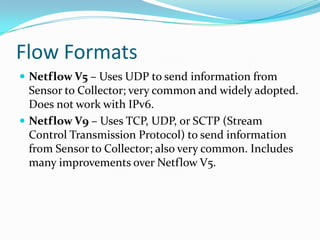
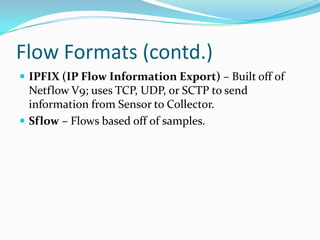
The document discusses network forensics, emphasizing the analysis of packet captures (pcap) to investigate security incidents and anomalies. It outlines methodologies for pcap analysis, including pattern matching and identifying triggering events, and details two scenarios involving malware detection and denial of service attacks. The author provides resources for further reading and tools used in network analysis, aiming to bridge the gap between basic knowledge and practical application in cybersecurity.