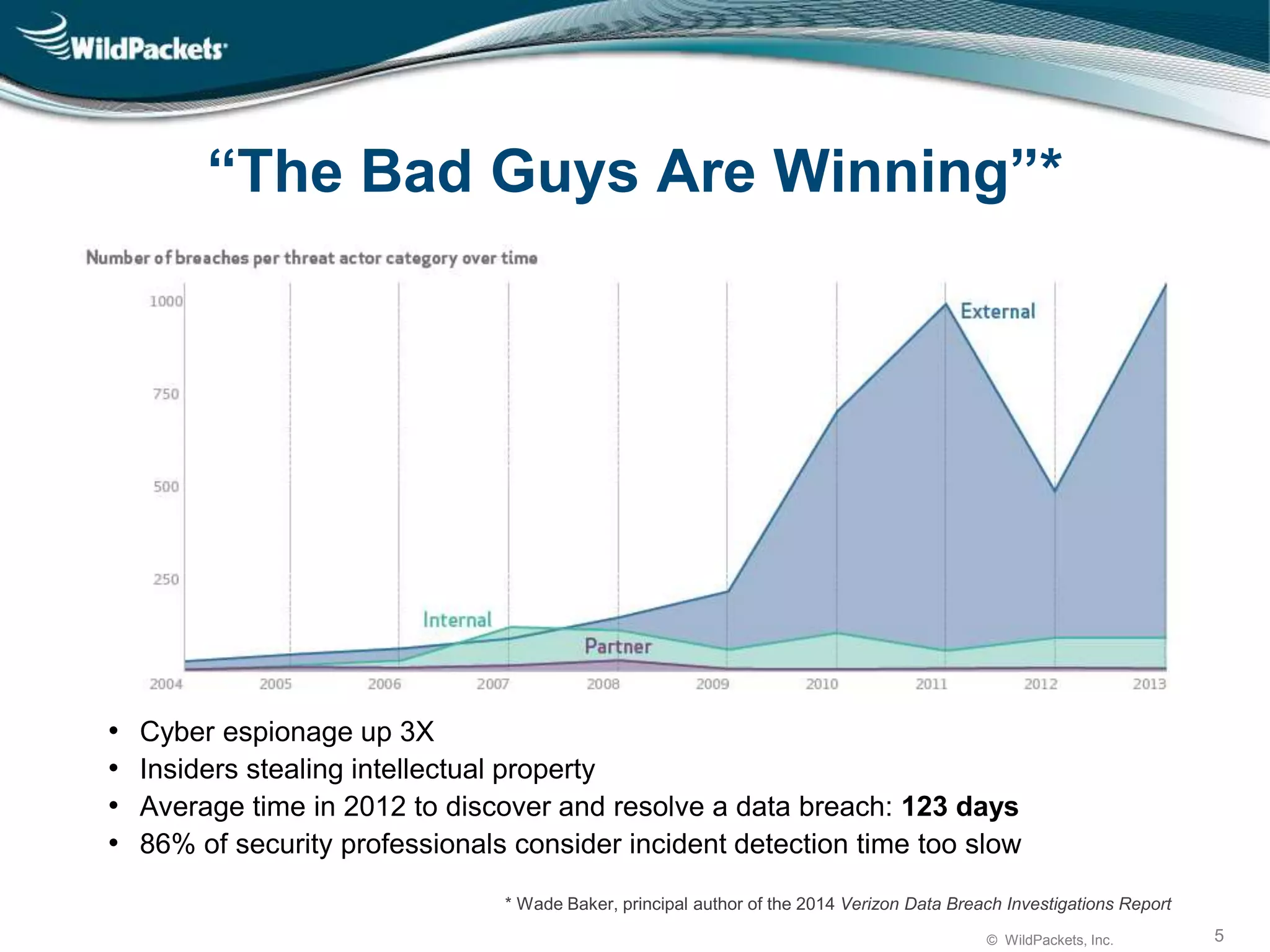
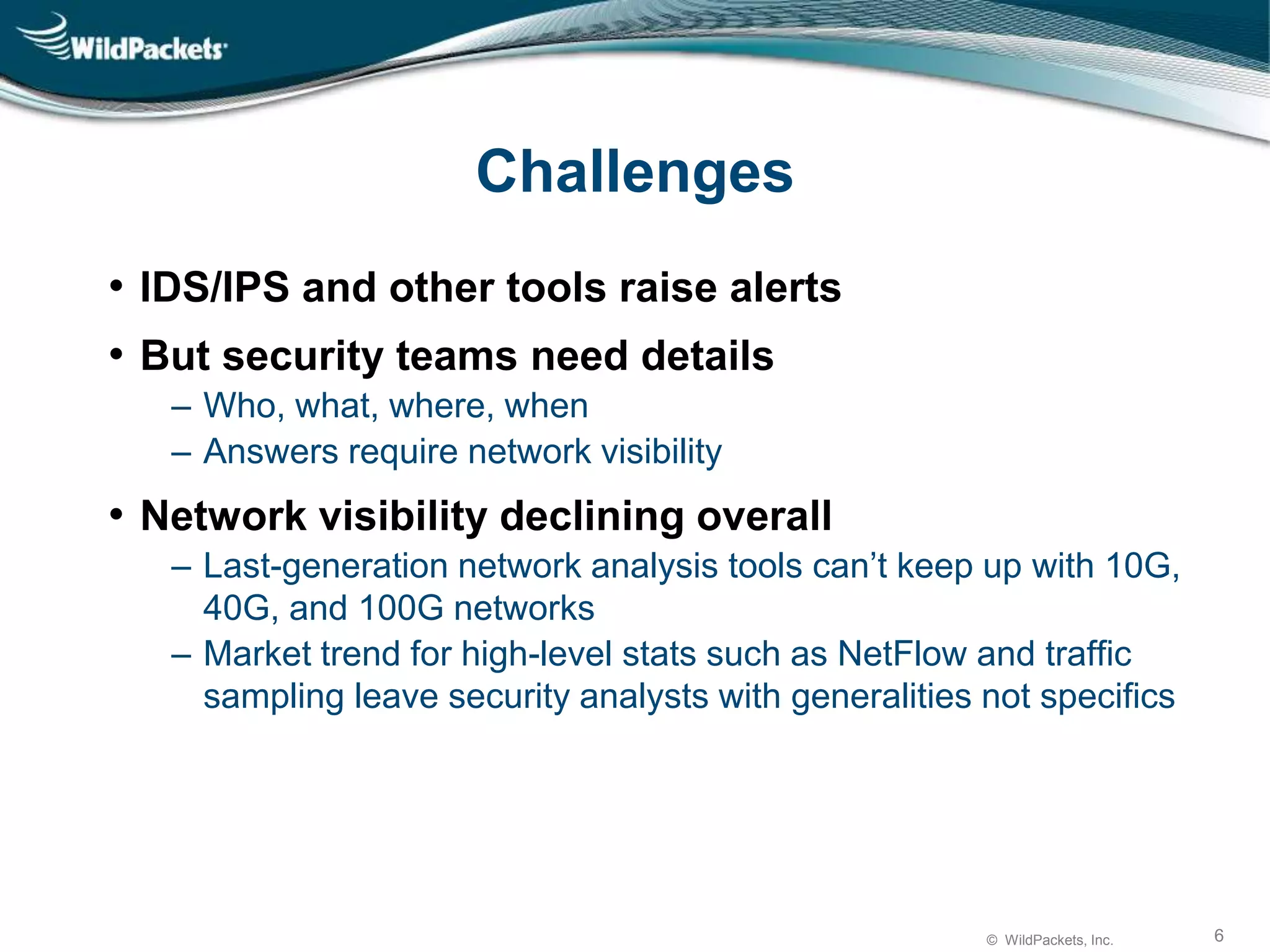
The document discusses the challenges in cybersecurity with a focus on network forensic analysis as a solution to combat rising cyber threats. It highlights the necessity for detailed insights on security incidents, emphasizing that traditional tools are inadequate for modern networks. Wildpackets' approach aims to enhance attack analysis through comprehensive packet capture and network forensics to provide actionable insights for security teams.