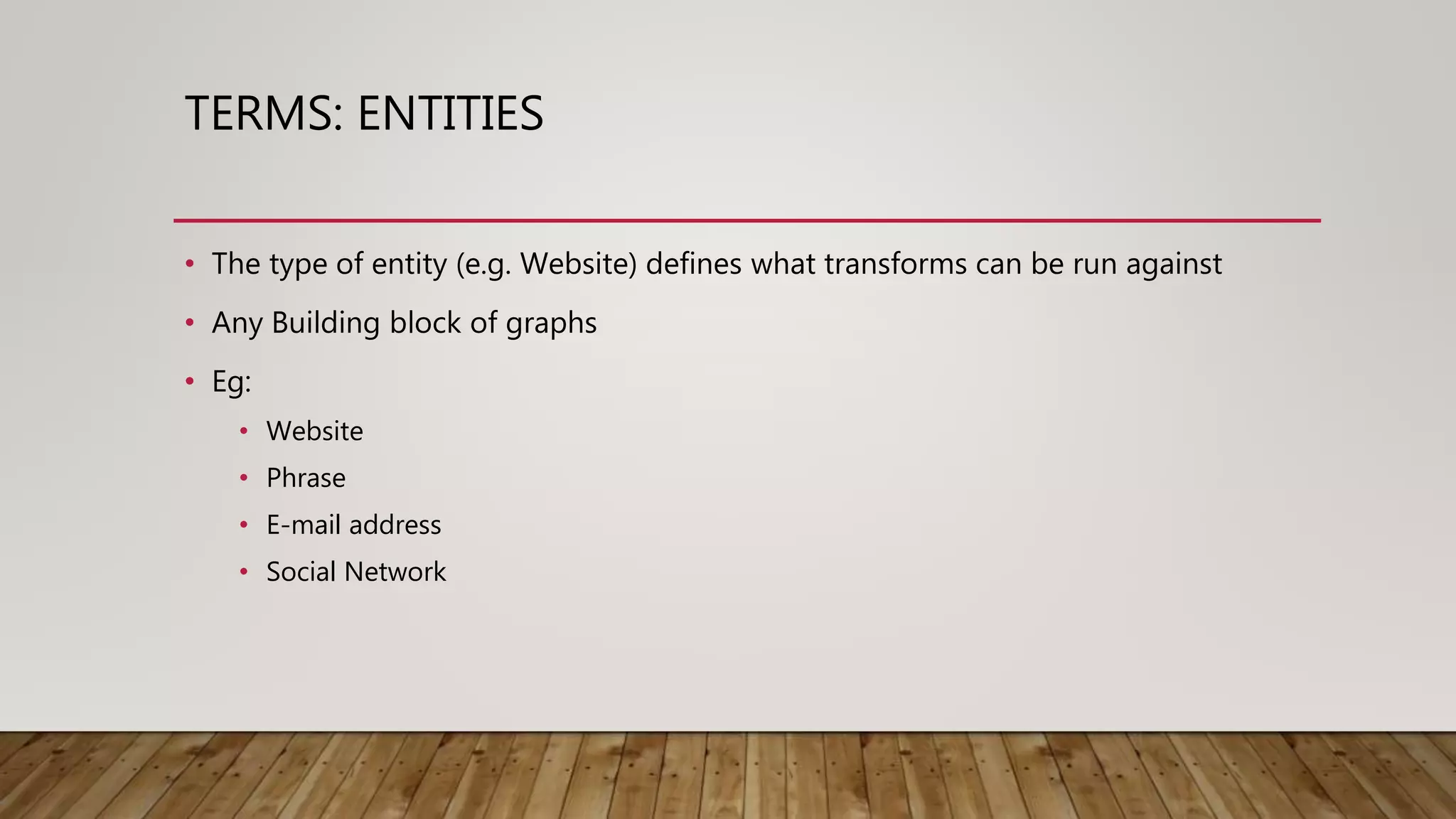
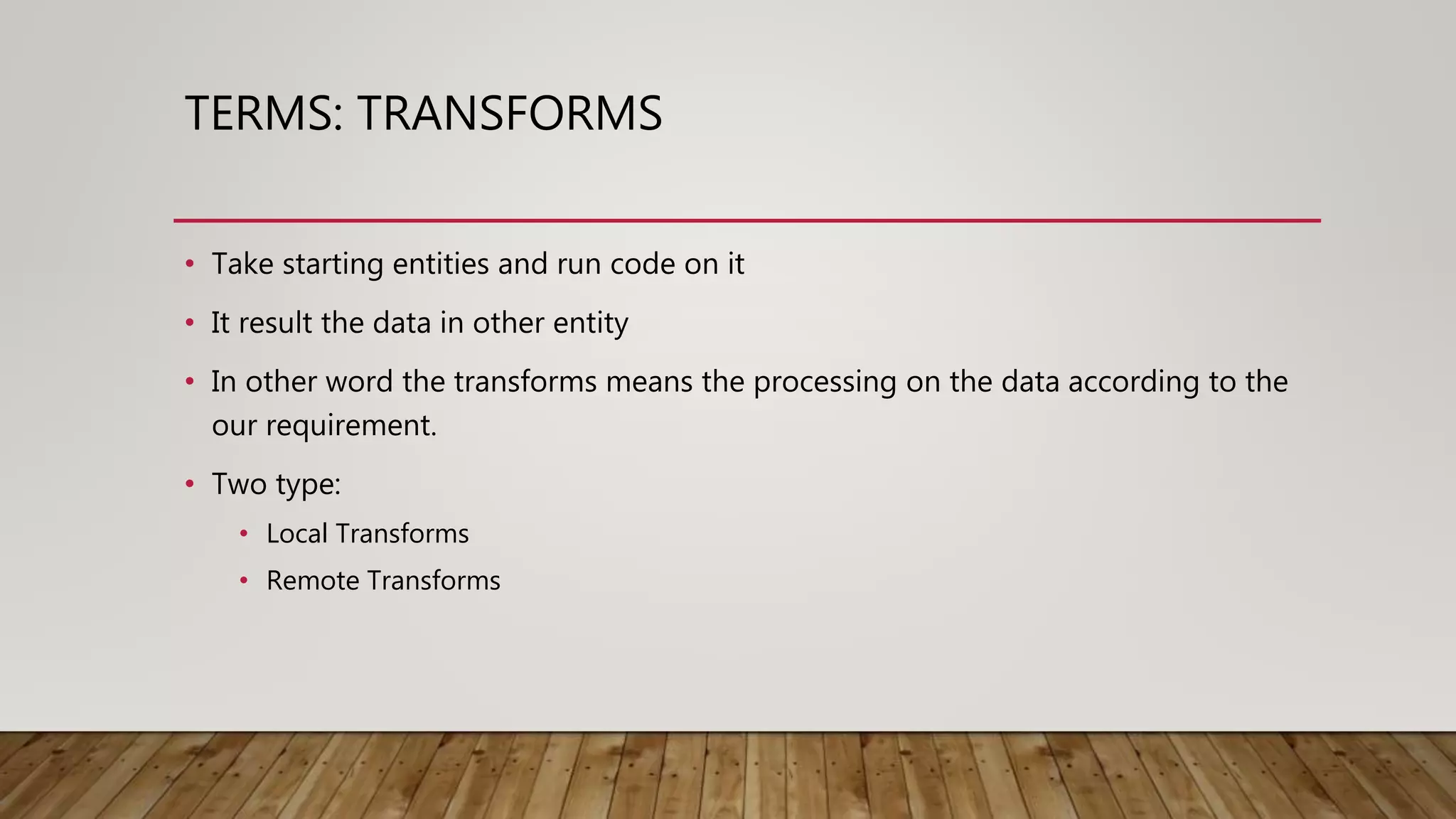
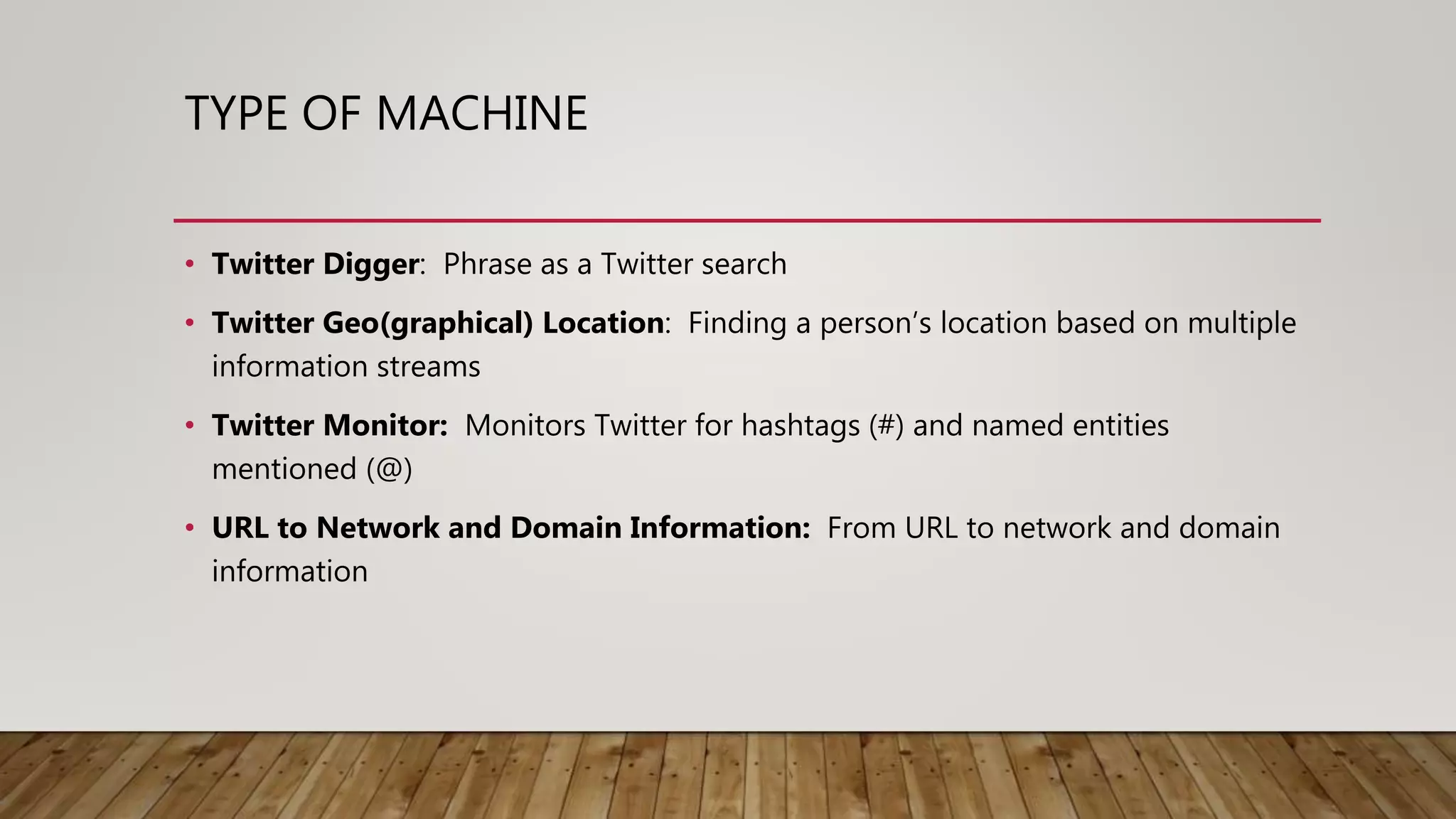
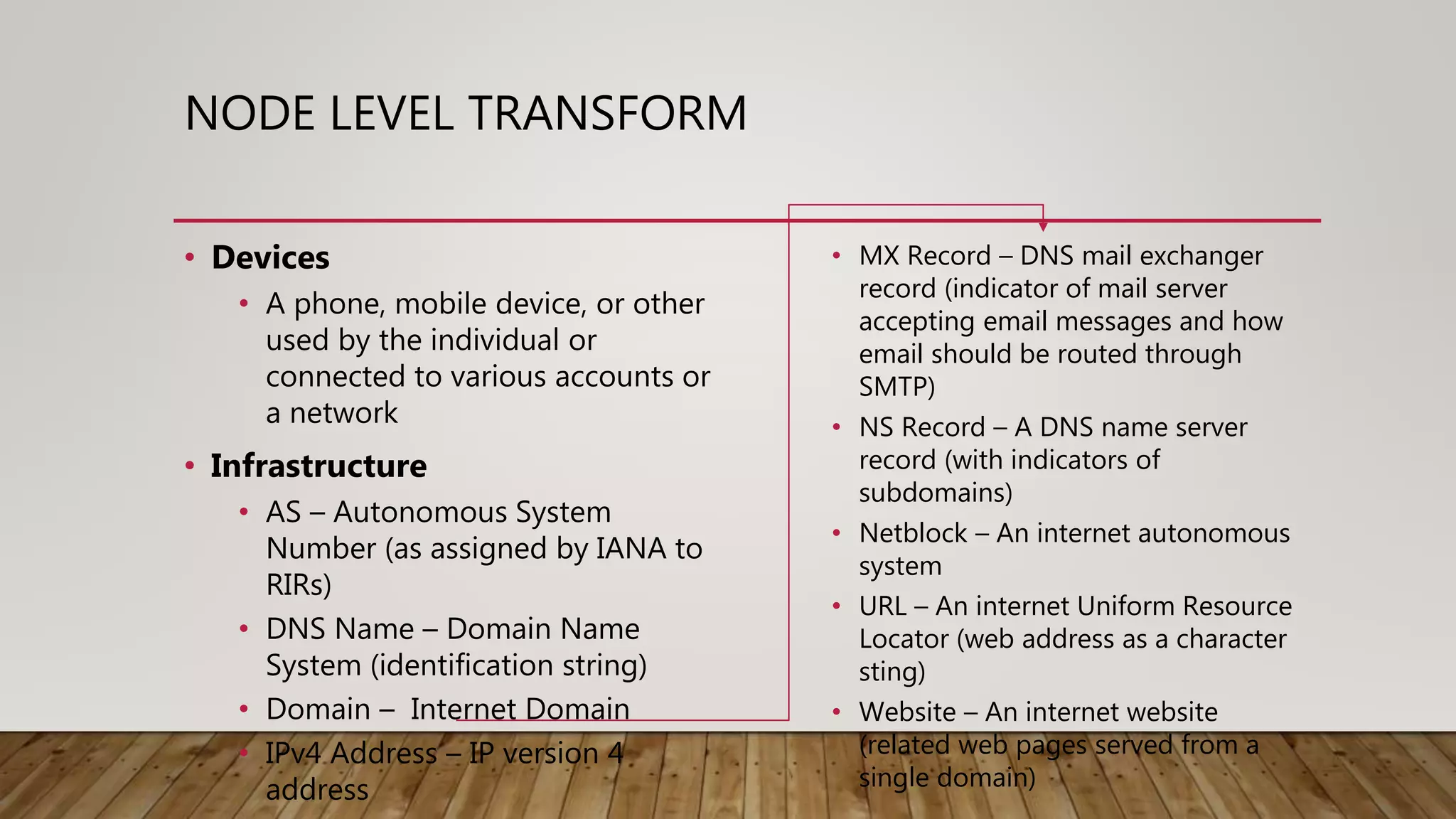
Maltego is an open-source intelligence (OSINT) gathering tool aimed at reconnaissance and data mining to provide insights into organizational environments. It utilizes entities and transforms to visualize complex relationships and potential vulnerabilities within data sets, drawing on publicly available information. Key features include identifying connections among individuals, organizations, and domains, emphasizing the importance of understanding online footprints and associations.