The document provides an overview of the Triton malware, which targets industrial control systems, specifically safety instrumented systems (SIS) used in critical infrastructure. It discusses the history of ICS malware, details the Triton attack's execution and components, and emphasizes the sophisticated nature of the attackers, alongside lessons learned regarding improved security measures. Key insights include the importance of robust IT/OT security integration and vulnerabilities in legacy systems exacerbated by increased connectivity.






![24CNES COMET SSI - Thomas Roccia – 2018
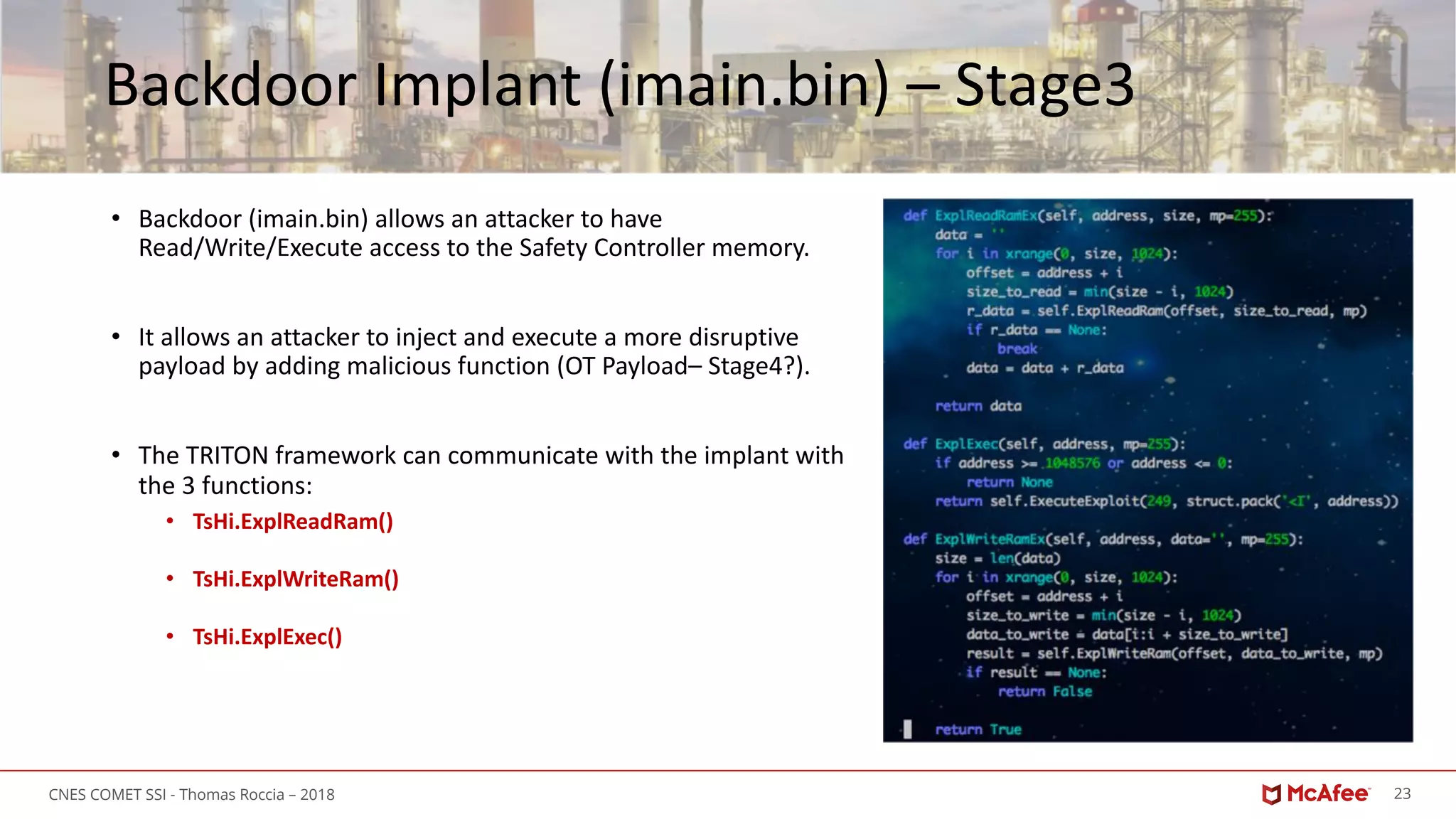
Backdoor Protocol (imain.bin) – Stage3
• The previous three function uses TsBase.ExecuteExploit
• It creates a TriStation « Get Main Processor Diagnostic Data » command with a crafted packet:
• [Standard Tricon packet headers][opcode][special identifier][data]
• Special identifier == 0xFF
• Read == 0x17
• Write == 0x41
• Execute == 0xF9
Special Identifier
READ
WRITE
EXECUTE](https://image.slidesharecdn.com/tritoncnestroccia-181008070758/75/TRITON-The-Next-Generation-of-ICS-Malware-24-2048.jpg)


![31CNES COMET SSI - Thomas Roccia – 2018
McAfee, the McAfee logo and [insert <other relevant McAfee Names>] are trademarks or registered trademarks of McAfee LLC or its subsidiaries in the U.S. and/or other countries.
Other names and brands may be claimed as the property of others.
Copyright © 2017 McAfee LLC.
3](https://image.slidesharecdn.com/tritoncnestroccia-181008070758/75/TRITON-The-Next-Generation-of-ICS-Malware-31-2048.jpg)