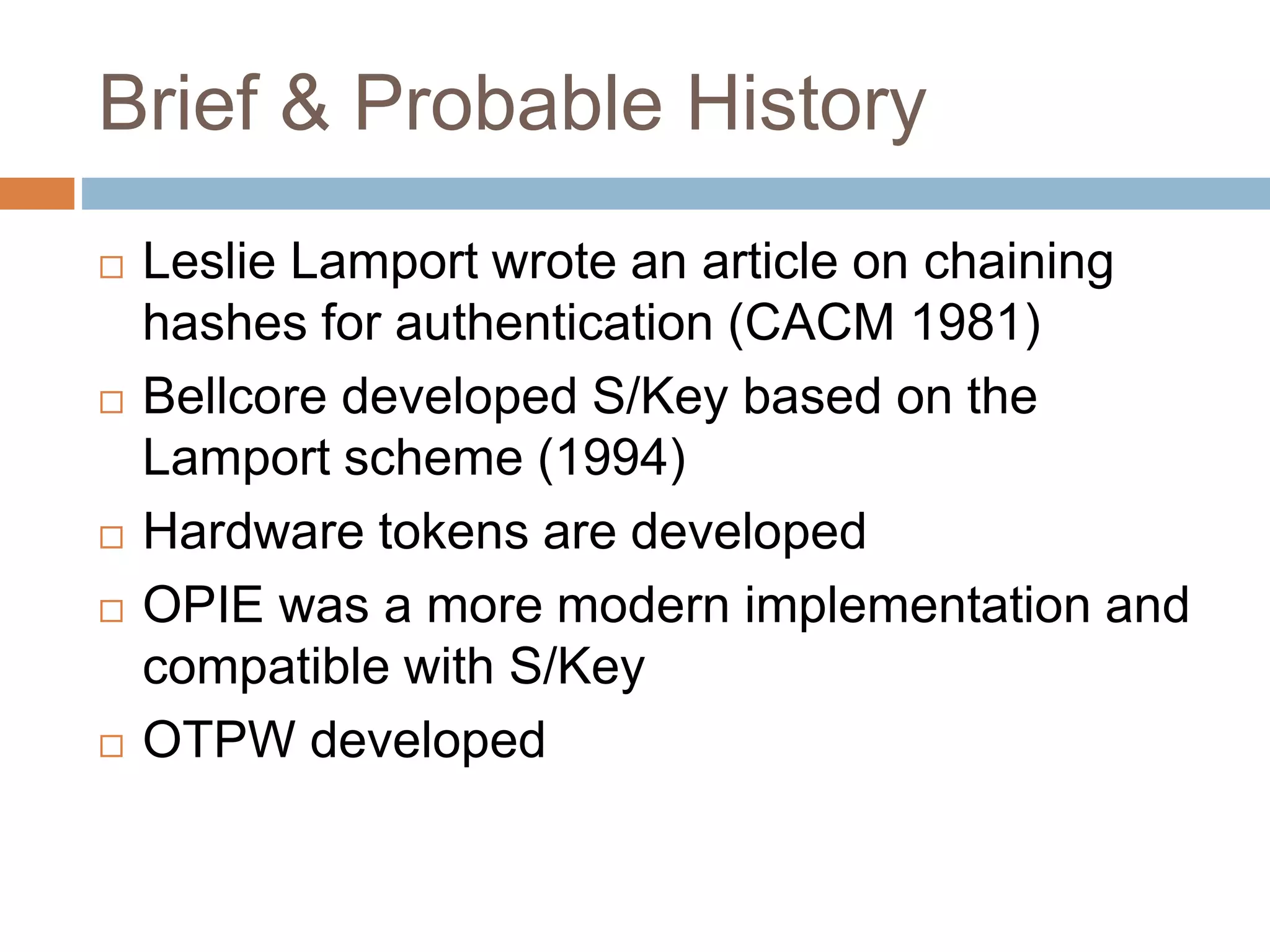
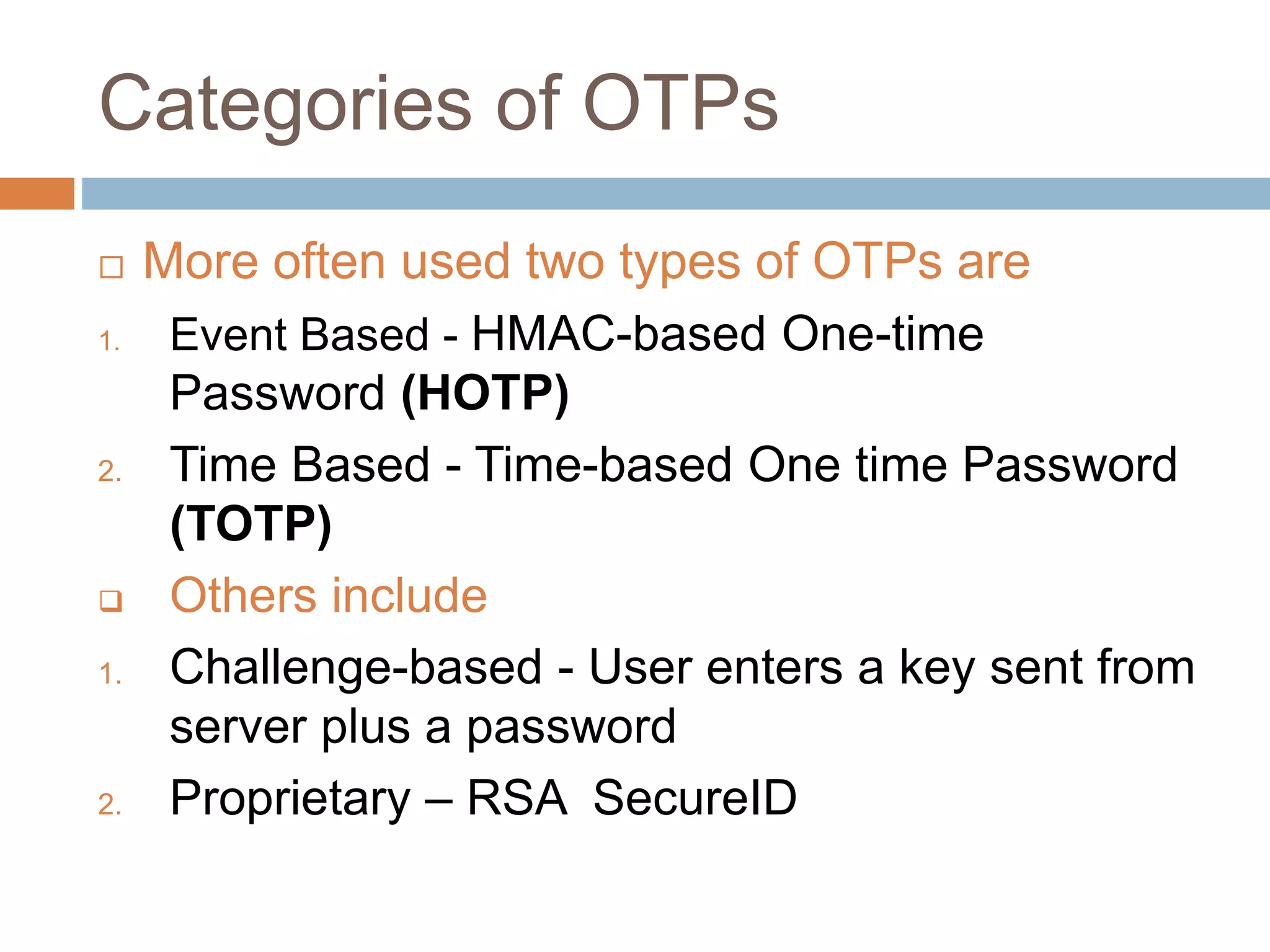
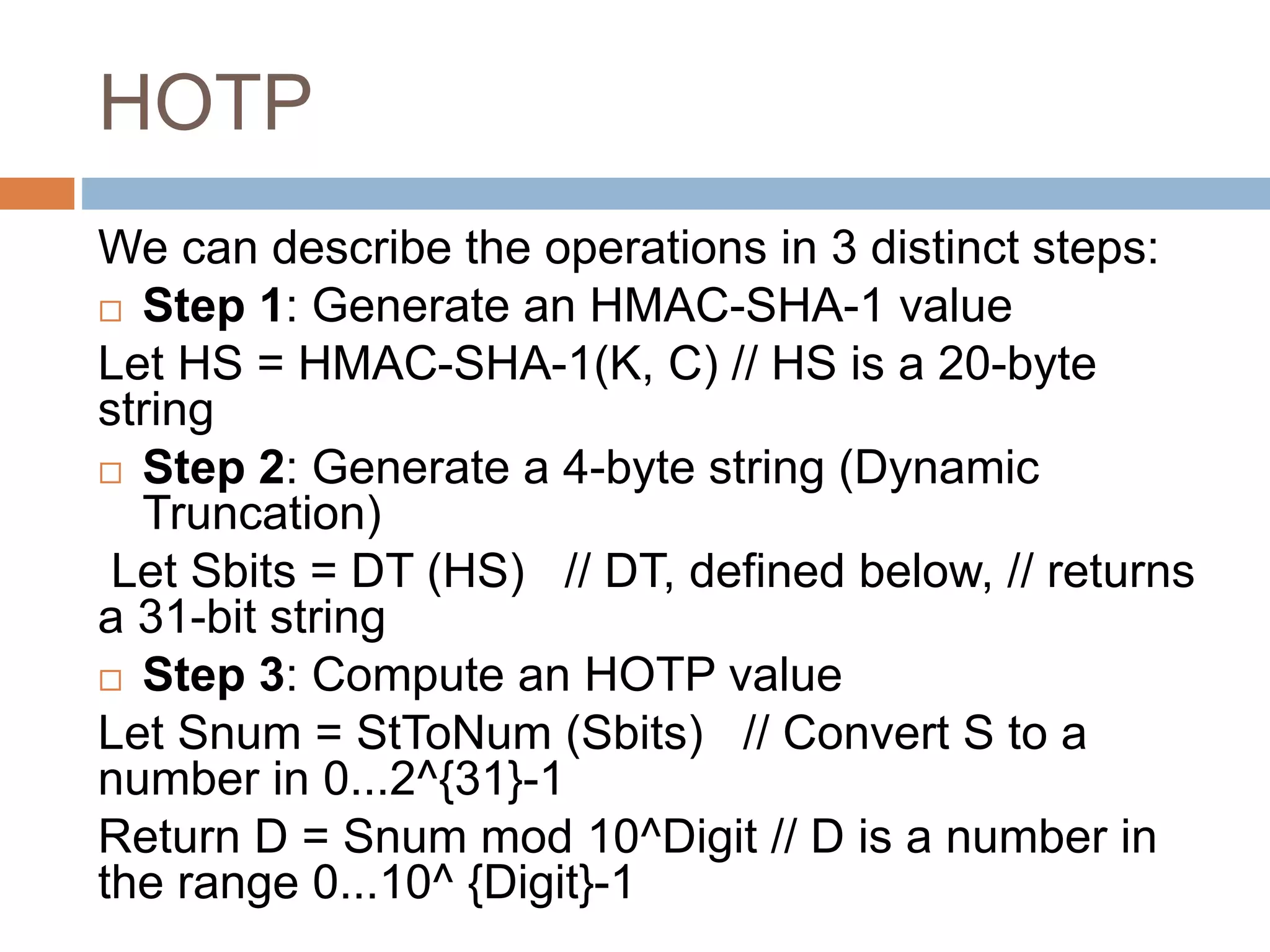
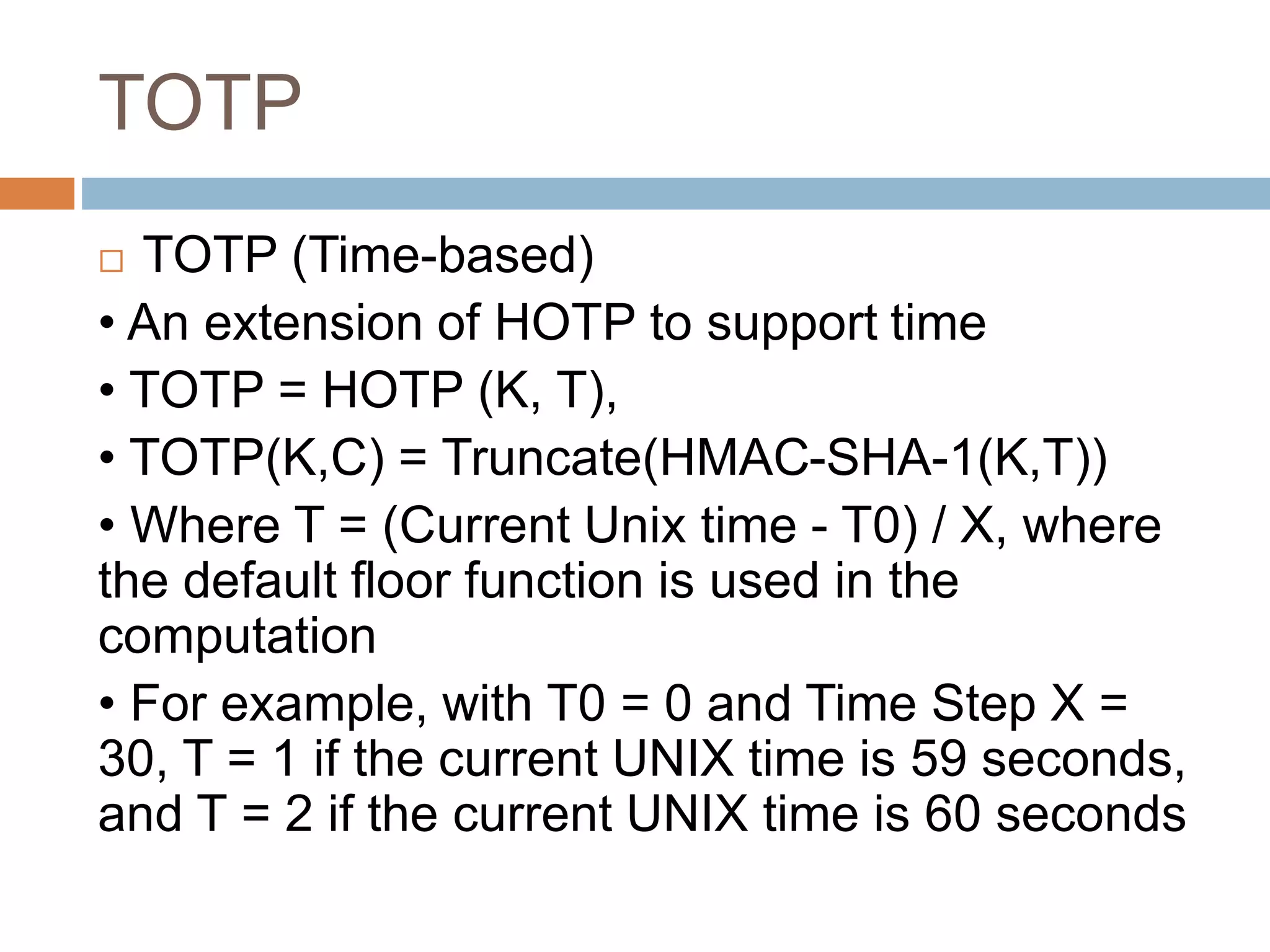
This document provides an overview of one-time passwords (OTP), including a brief history, benefits and costs, categories, generation methods like HOTP and TOTP, delivery methods, relevant RFCs and standards, potential attacks, and development libraries. It defines an OTP as a single-use password or code used to authenticate over untrusted channels, complementing a user password for two-factor authentication. Common OTP types are event-based HOTP, which uses a HMAC to generate codes based on a key and counter, and time-based TOTP, which extends HOTP to generate codes based on time.