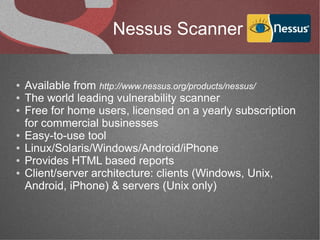
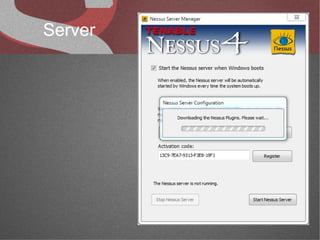
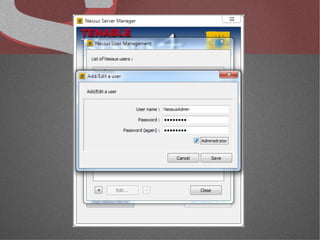
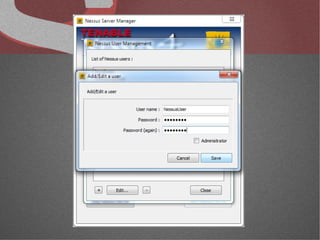
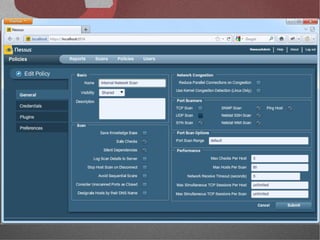
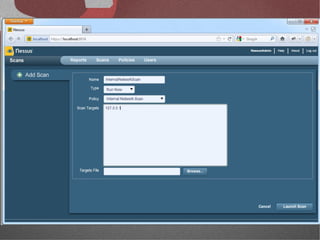
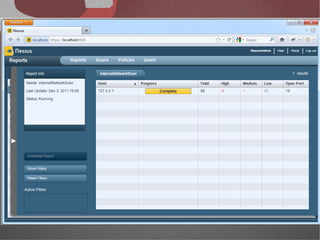
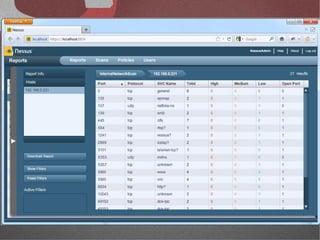
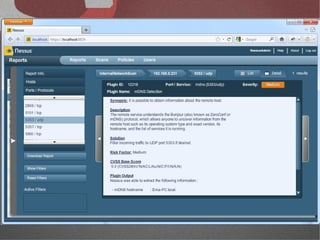
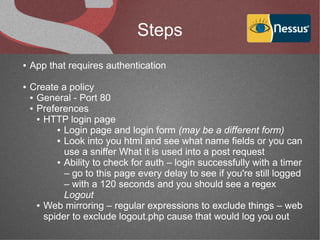
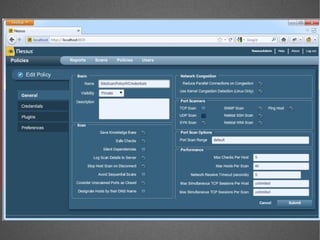
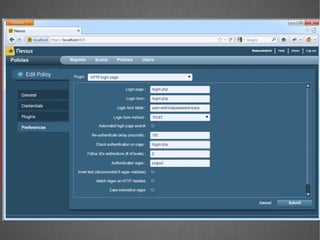
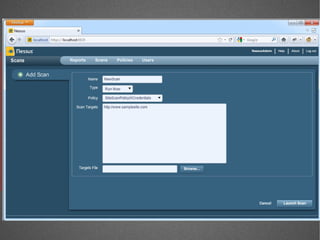
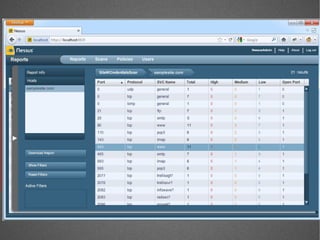
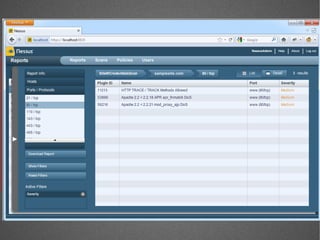
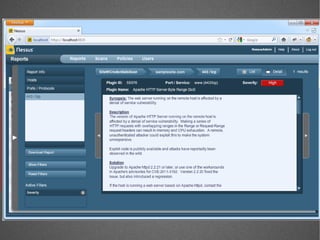
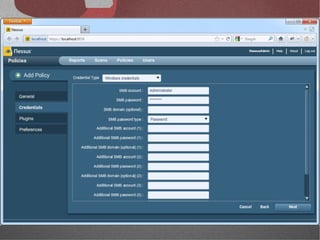
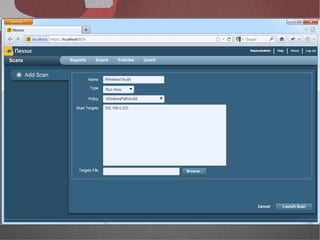
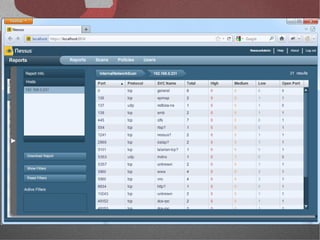
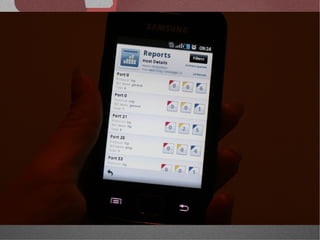
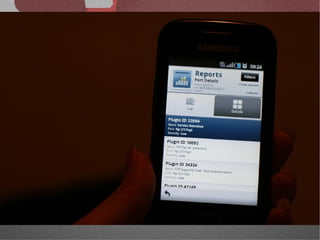
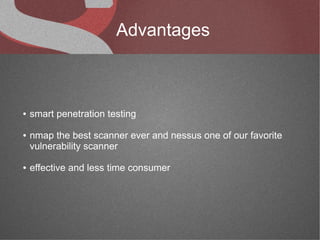
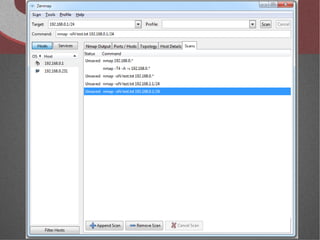
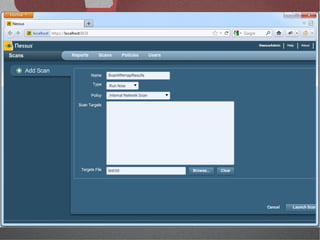
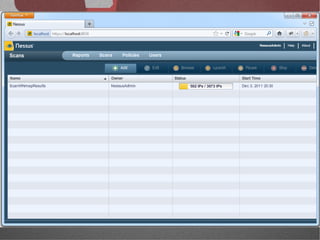
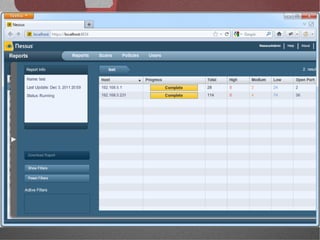
The document discusses various network security tools, focusing on Nessus and Nmap. Nessus is an open-source vulnerability scanner that scans for vulnerabilities on networks and hosts. It provides reports and has both free and commercial versions. Nmap is a port scanner used to discover hosts and services on a network. The document explains how Nessus and Nmap can be used together for penetration testing, with Nmap performing initial scans and Nessus following up with more detailed vulnerability assessments. Example uses of the tools for internal network scanning and web application testing are also provided.