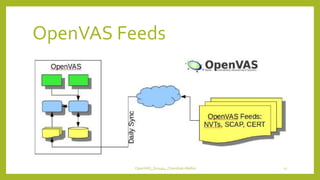
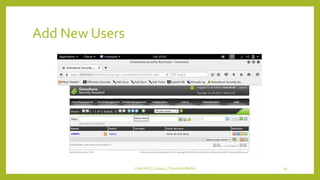
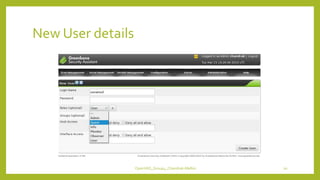
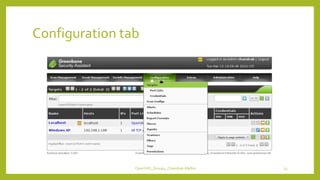
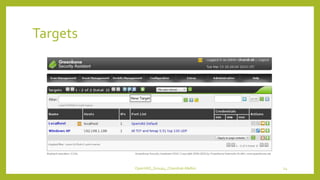
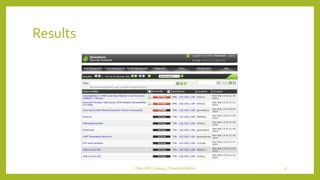
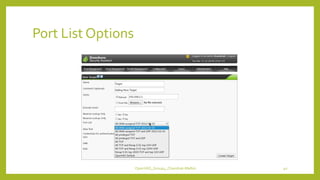
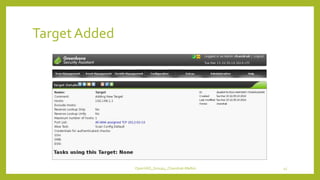
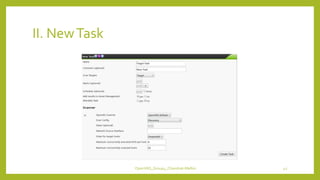
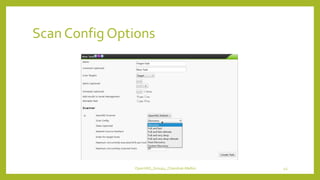
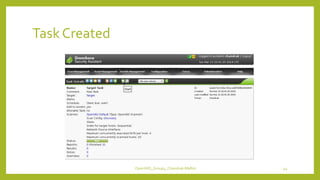
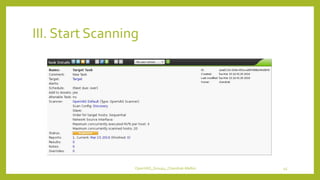
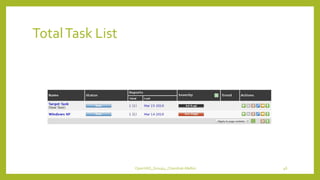
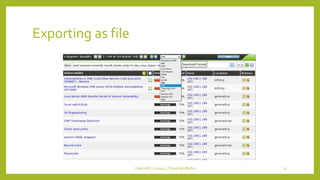
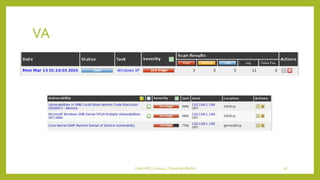
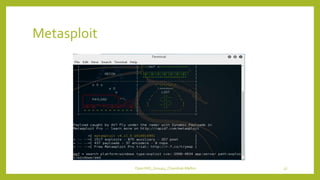
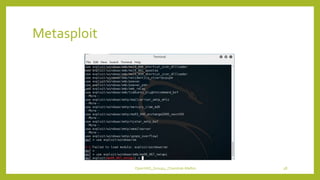
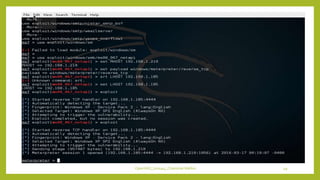
The document provides an overview of OpenVAS, a vulnerability assessment scanner that highlights its importance, architecture, and functionality. It explains how to conduct vulnerability assessments using OpenVAS, including setup, scanning targets, and exporting reports. The document also discusses the benefits and limitations of OpenVAS, along with steps for mitigating identified vulnerabilities.