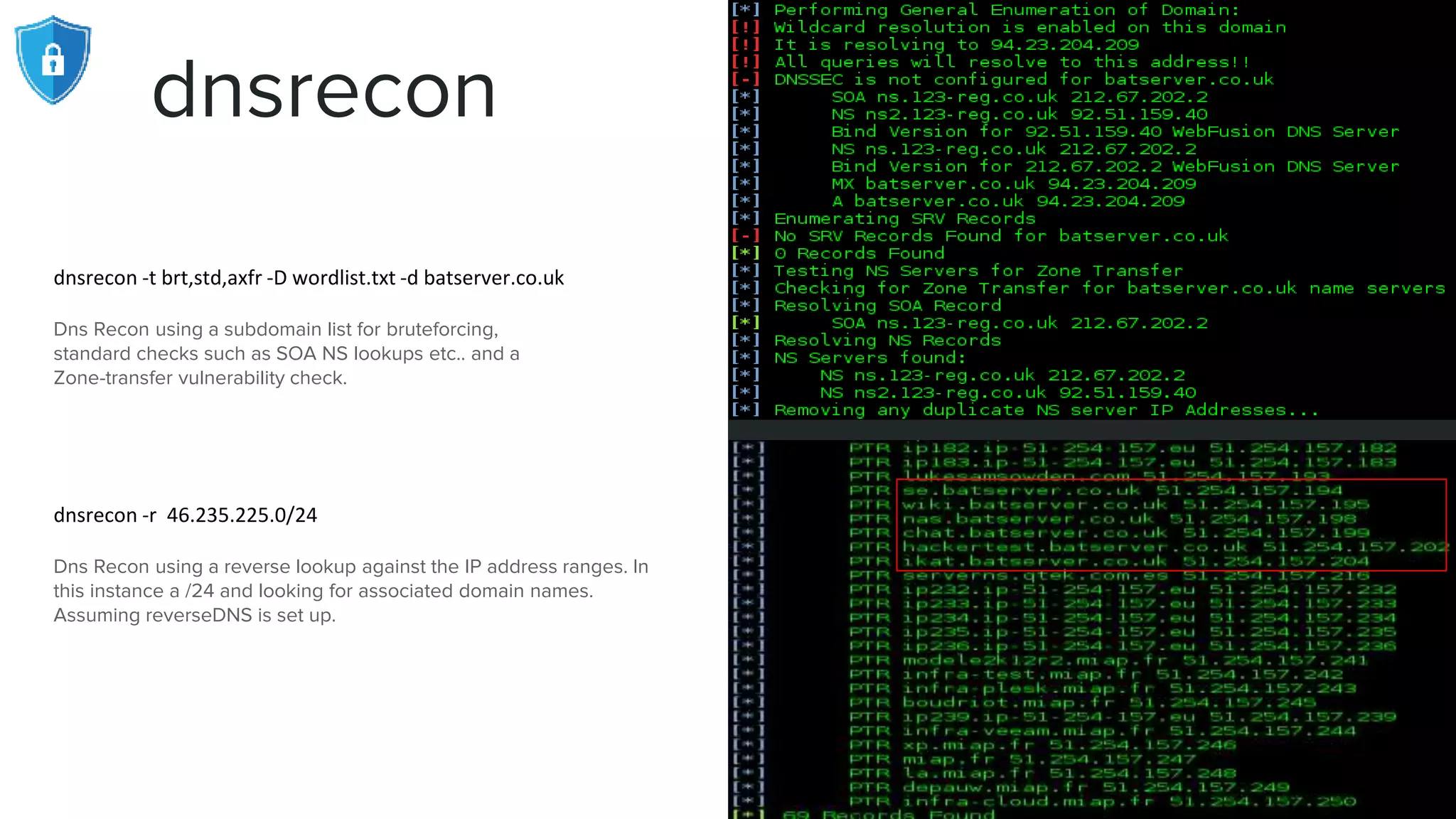
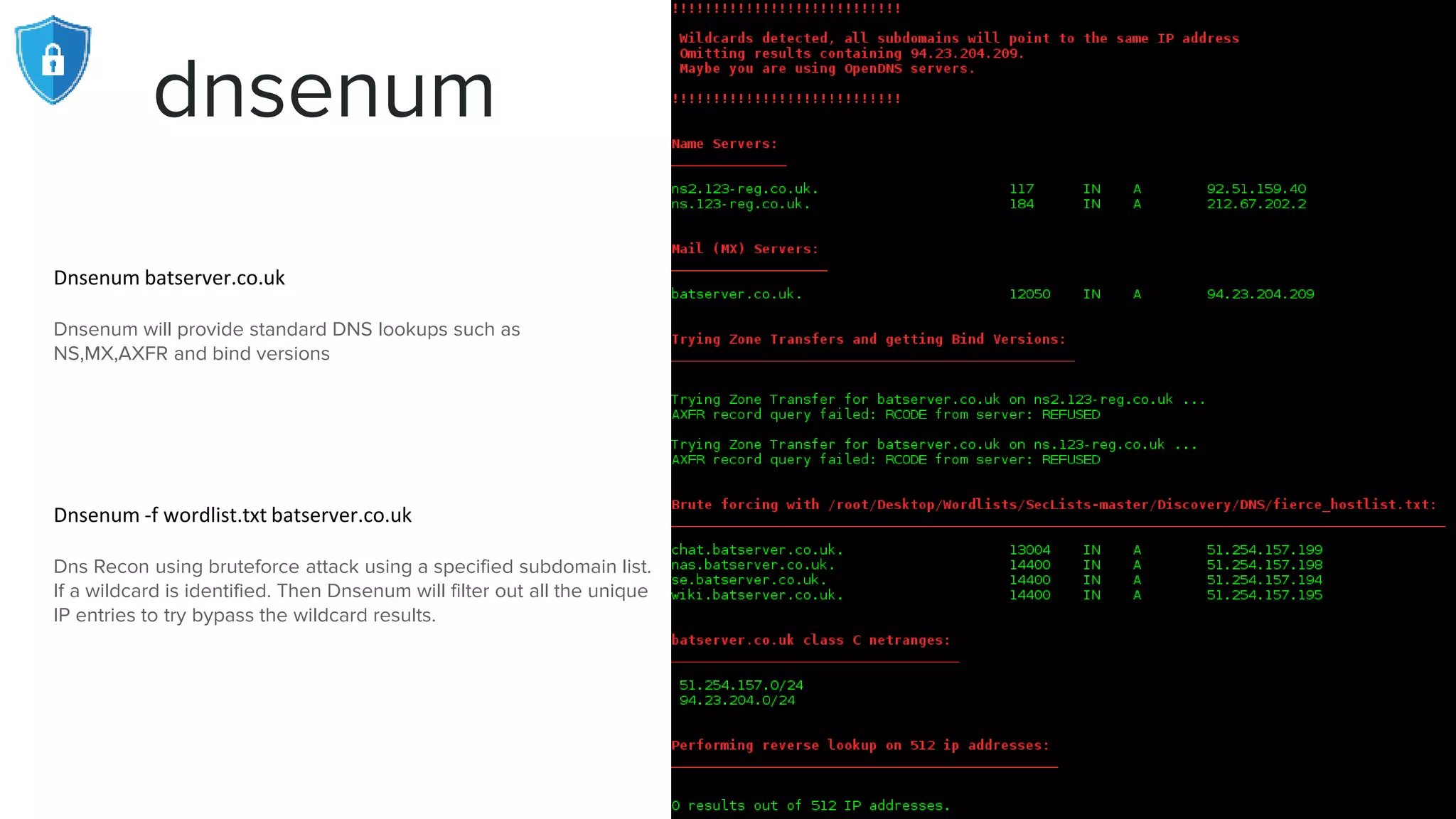
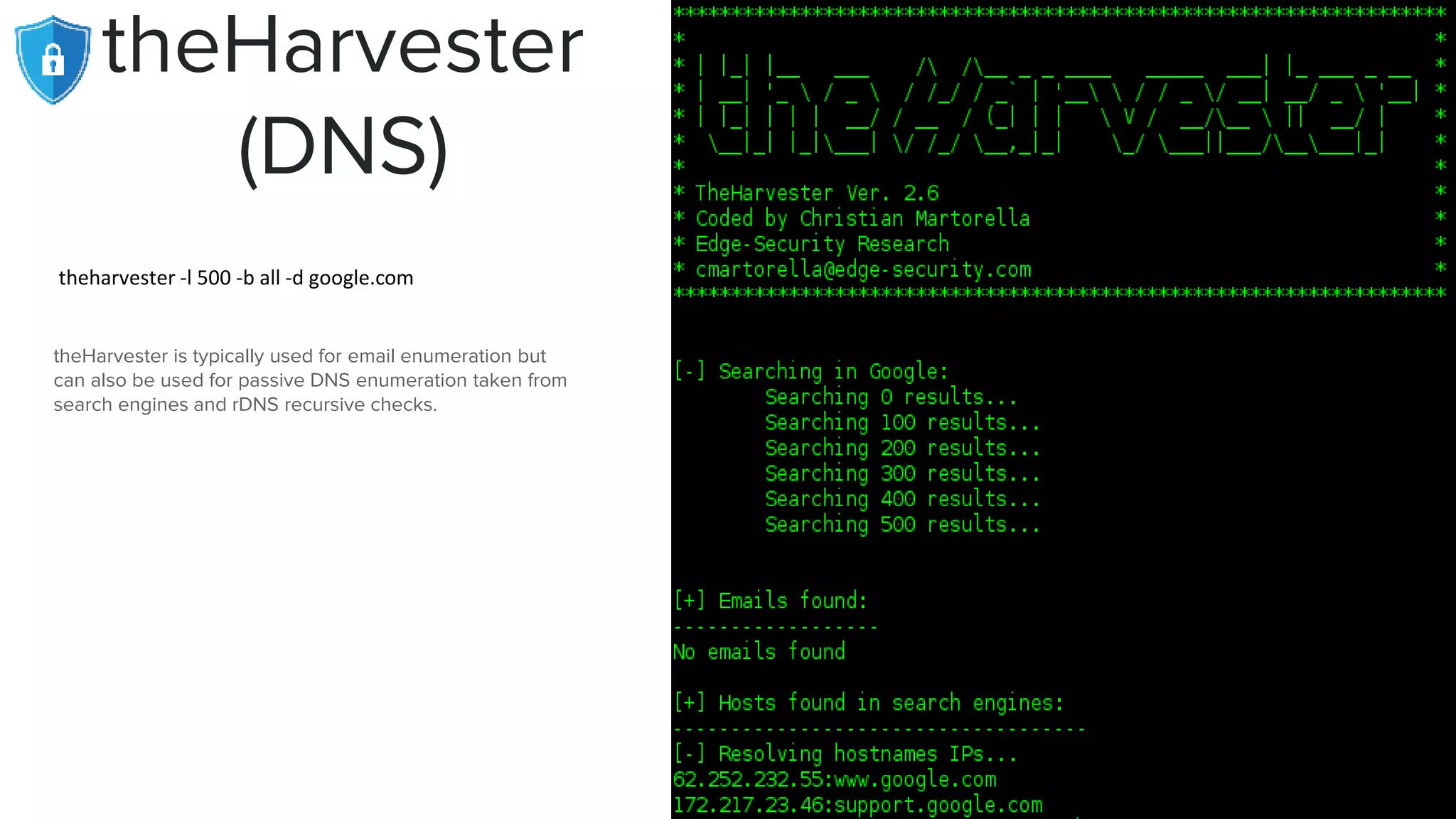
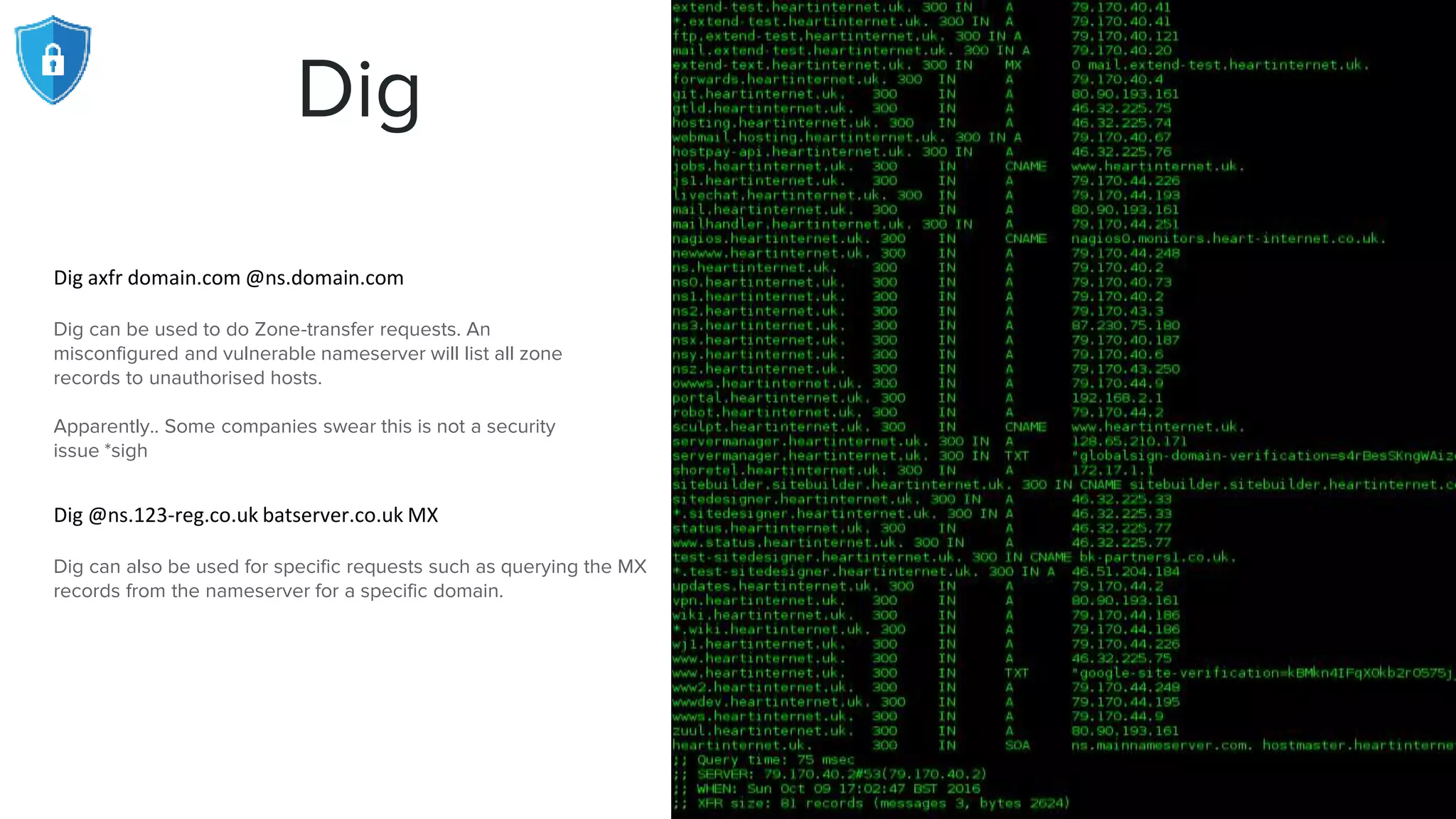
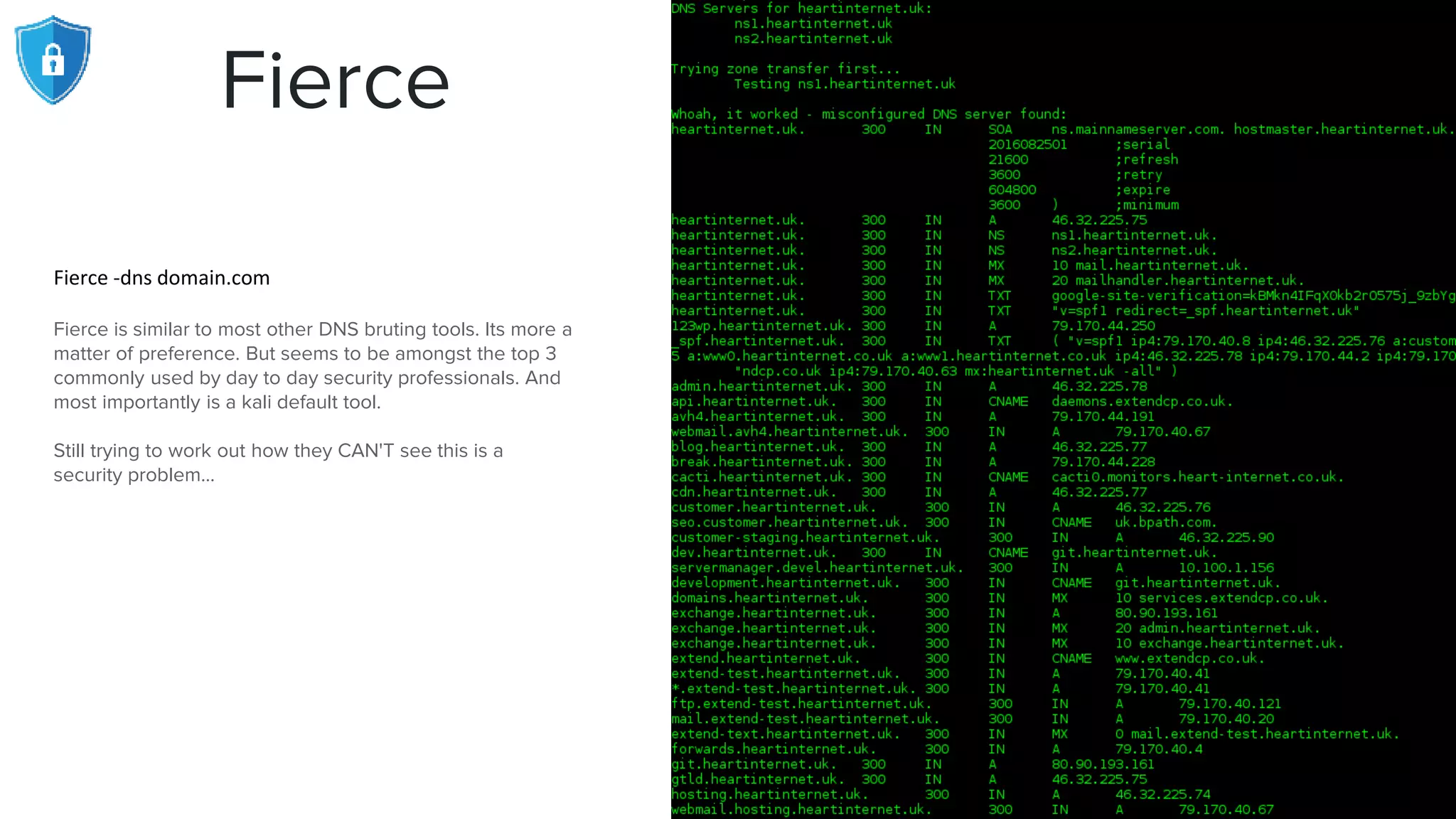
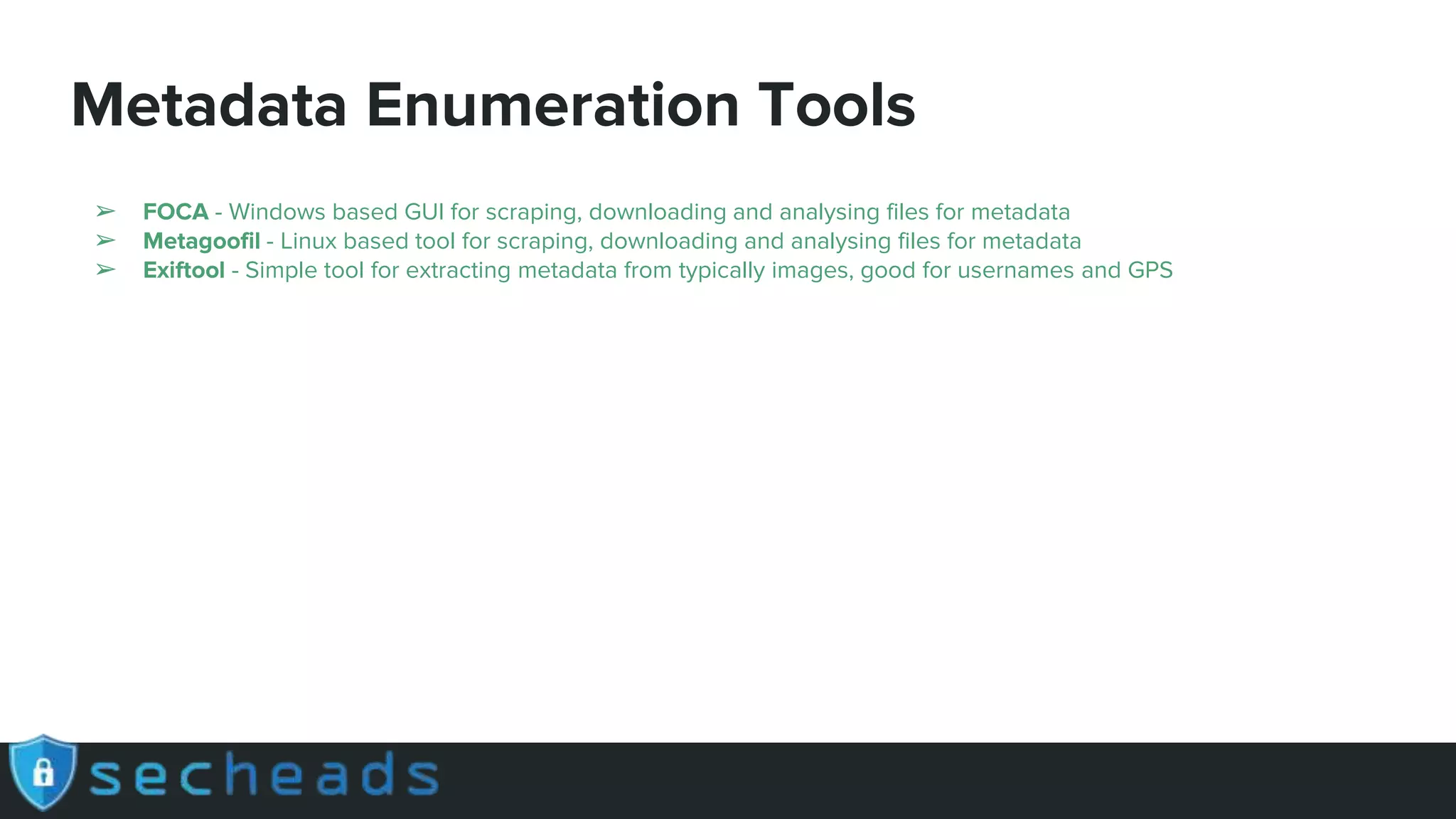
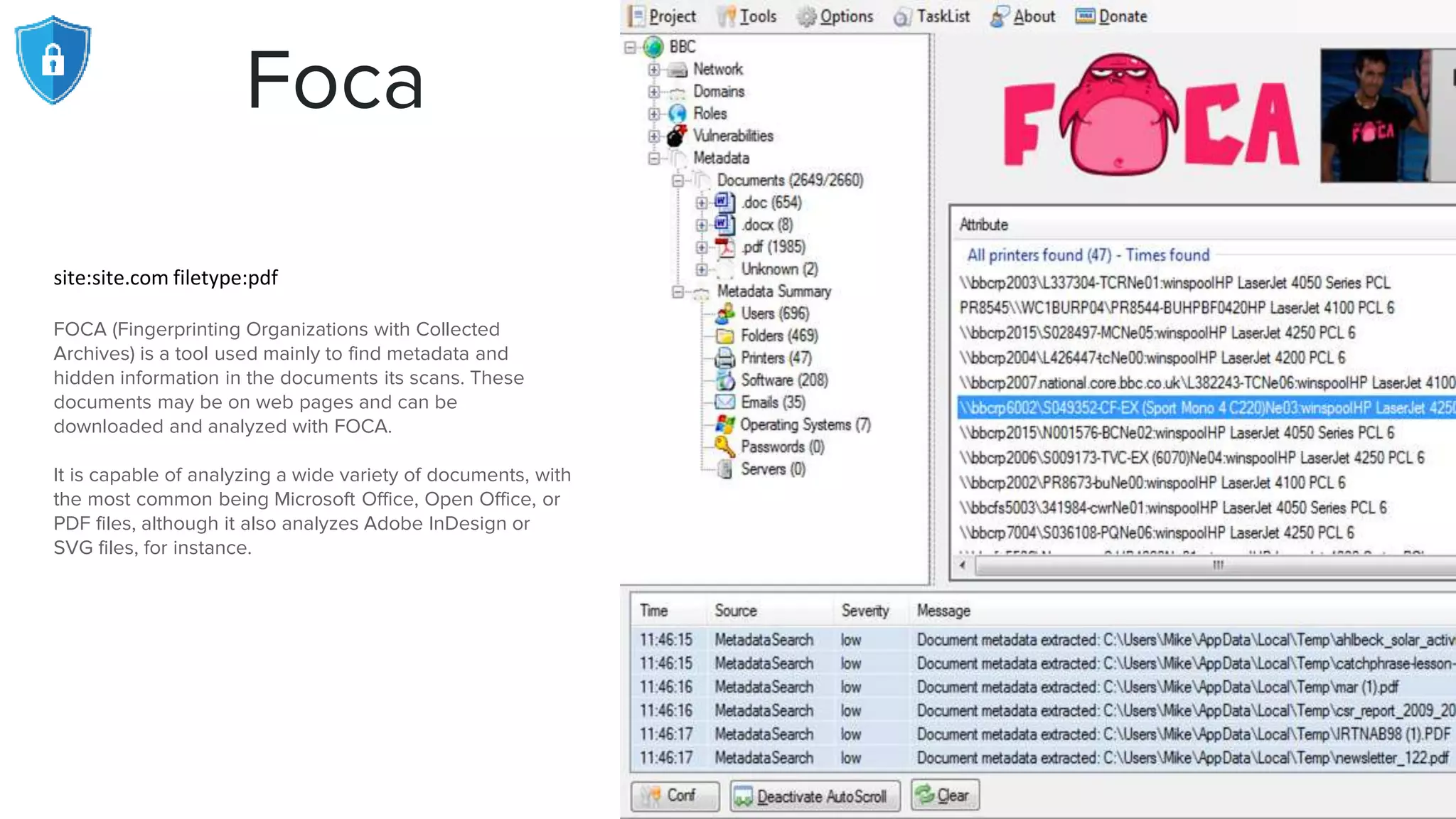
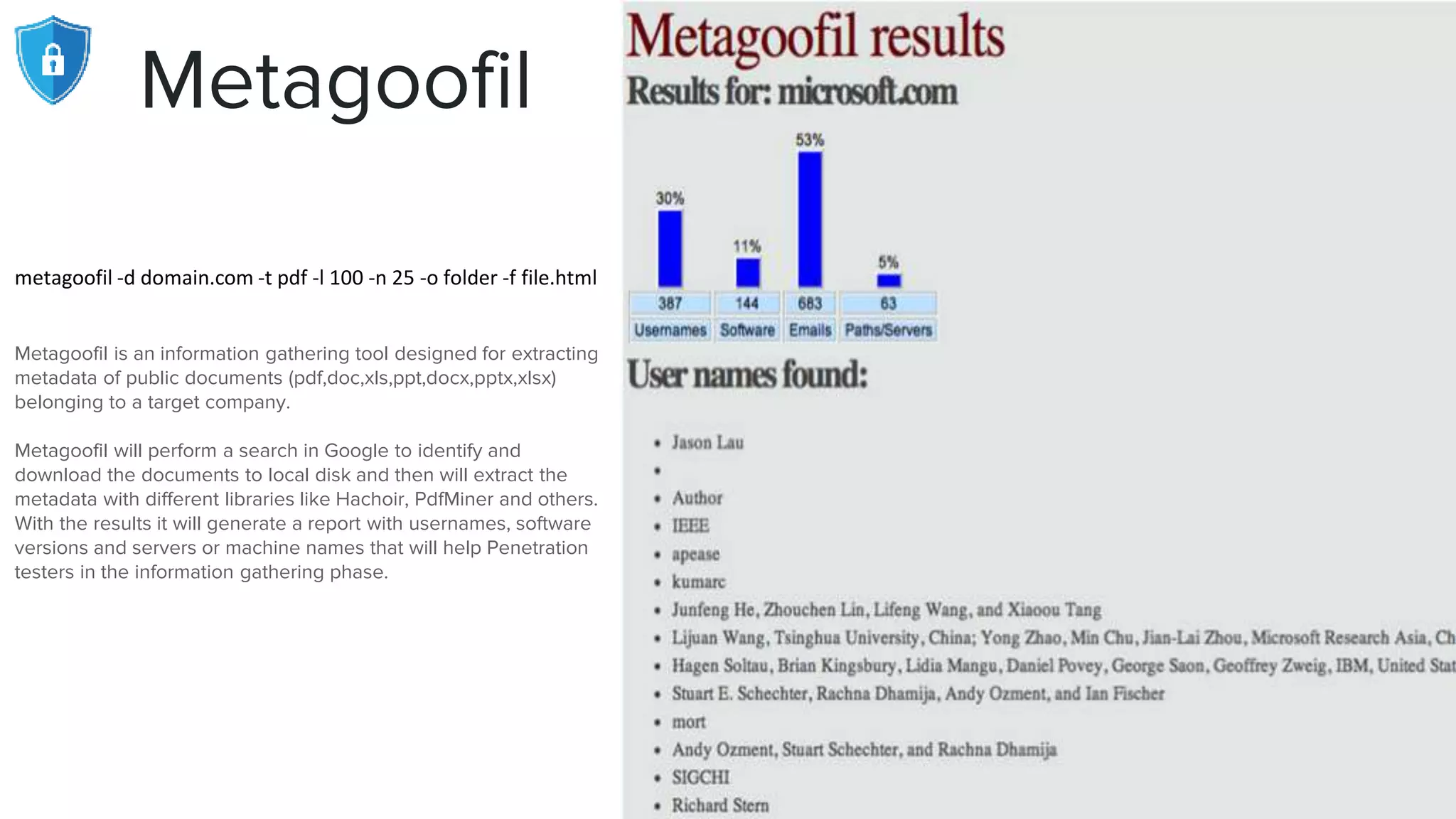
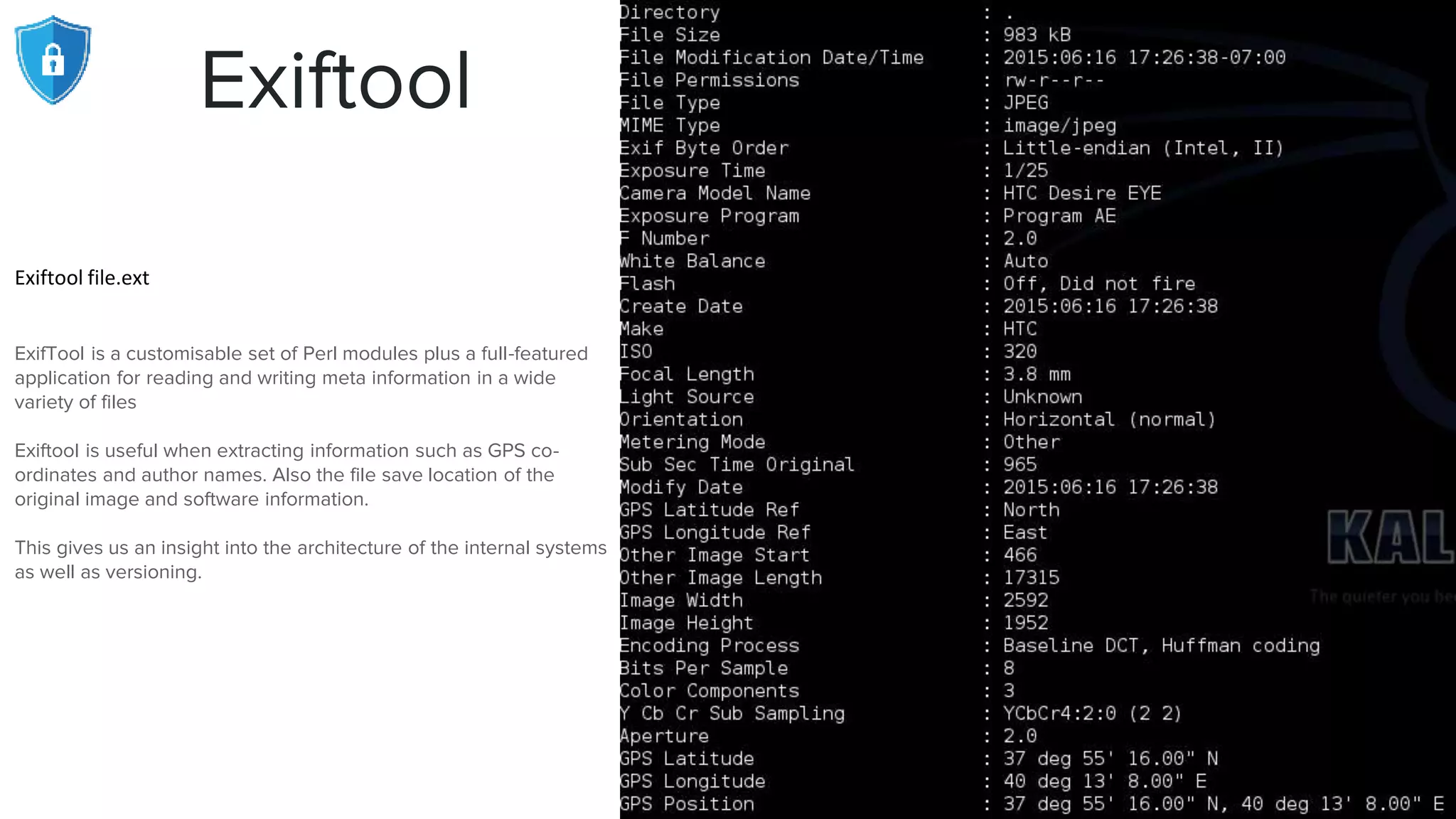
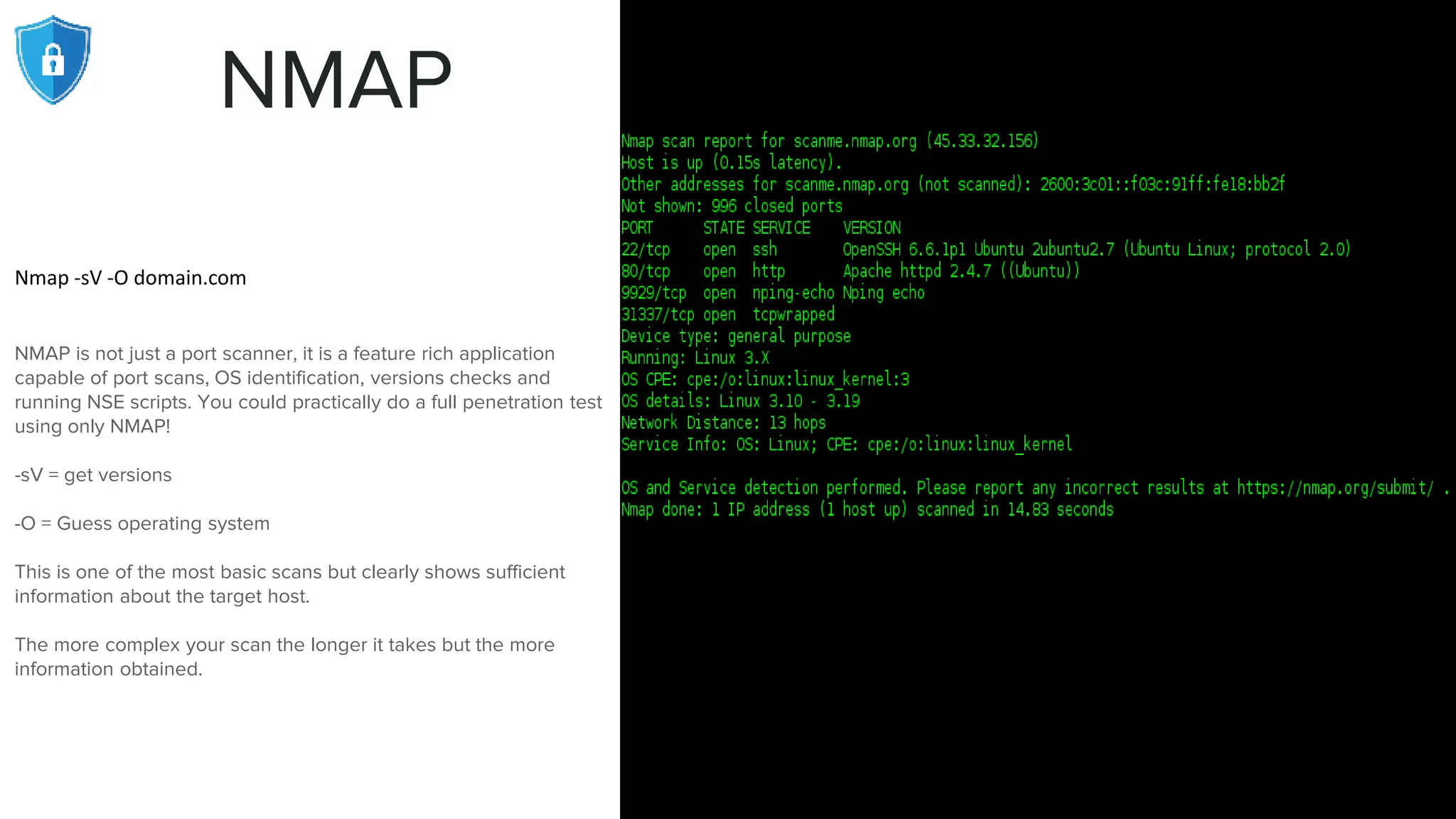
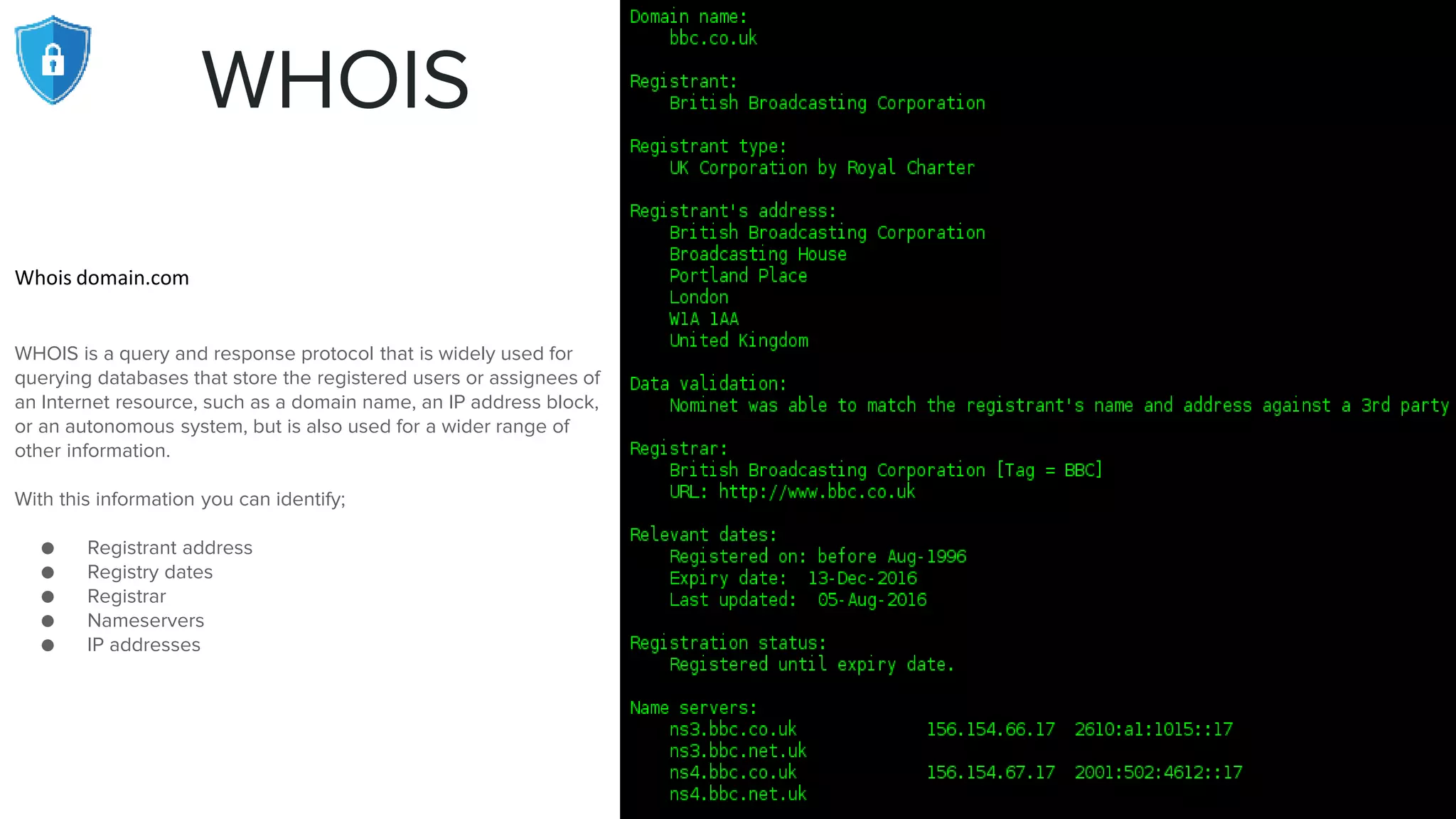
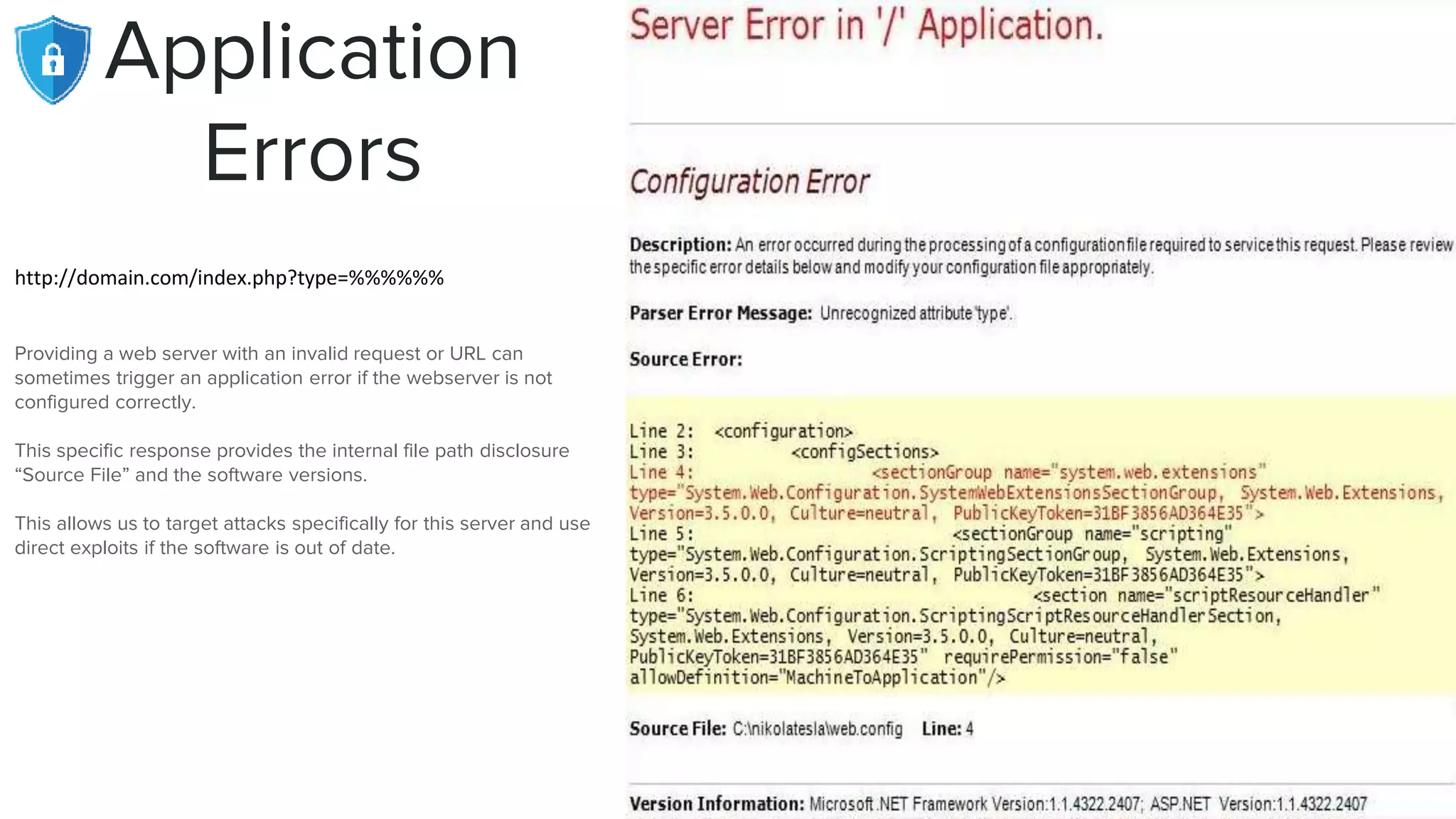
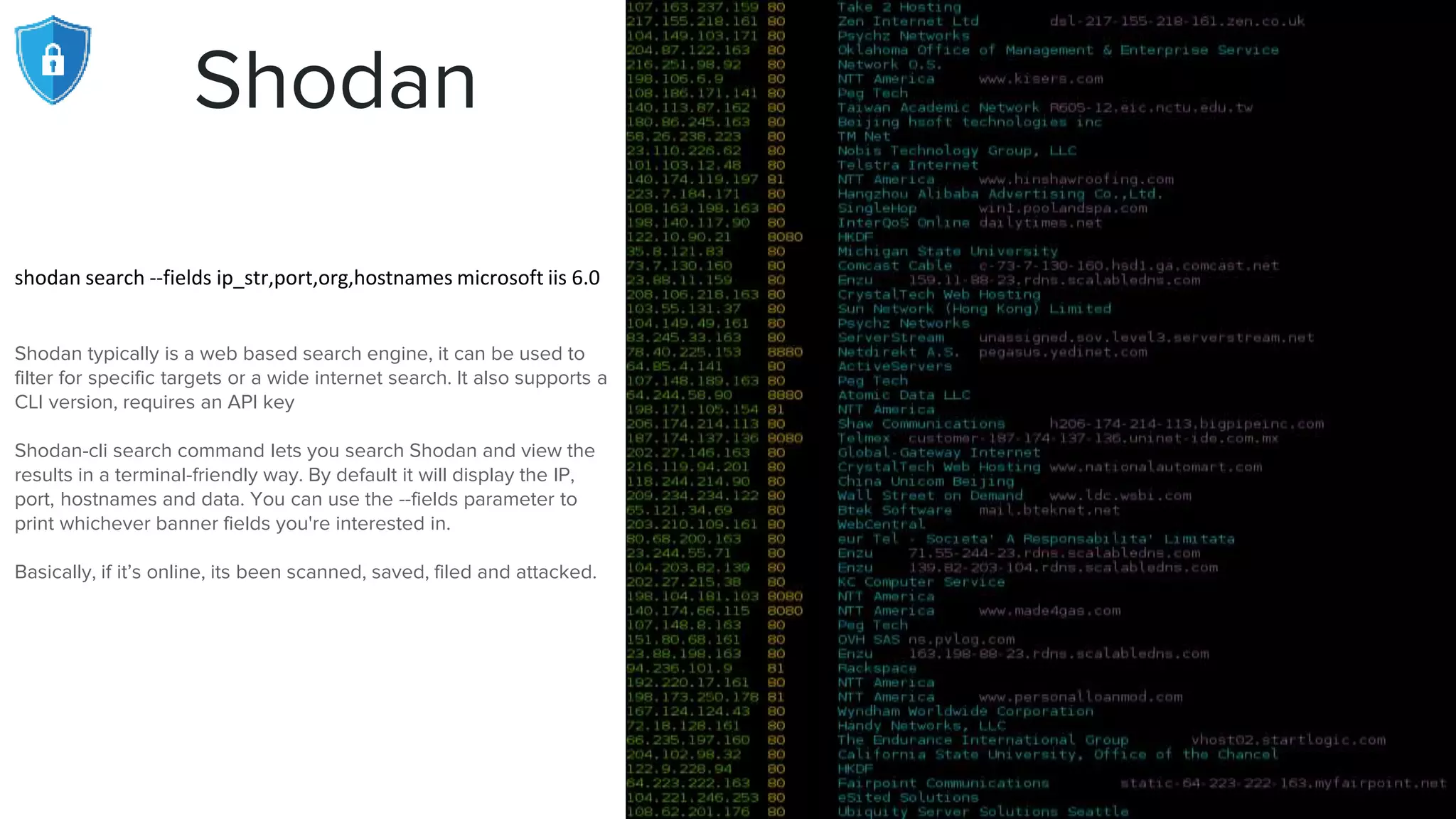
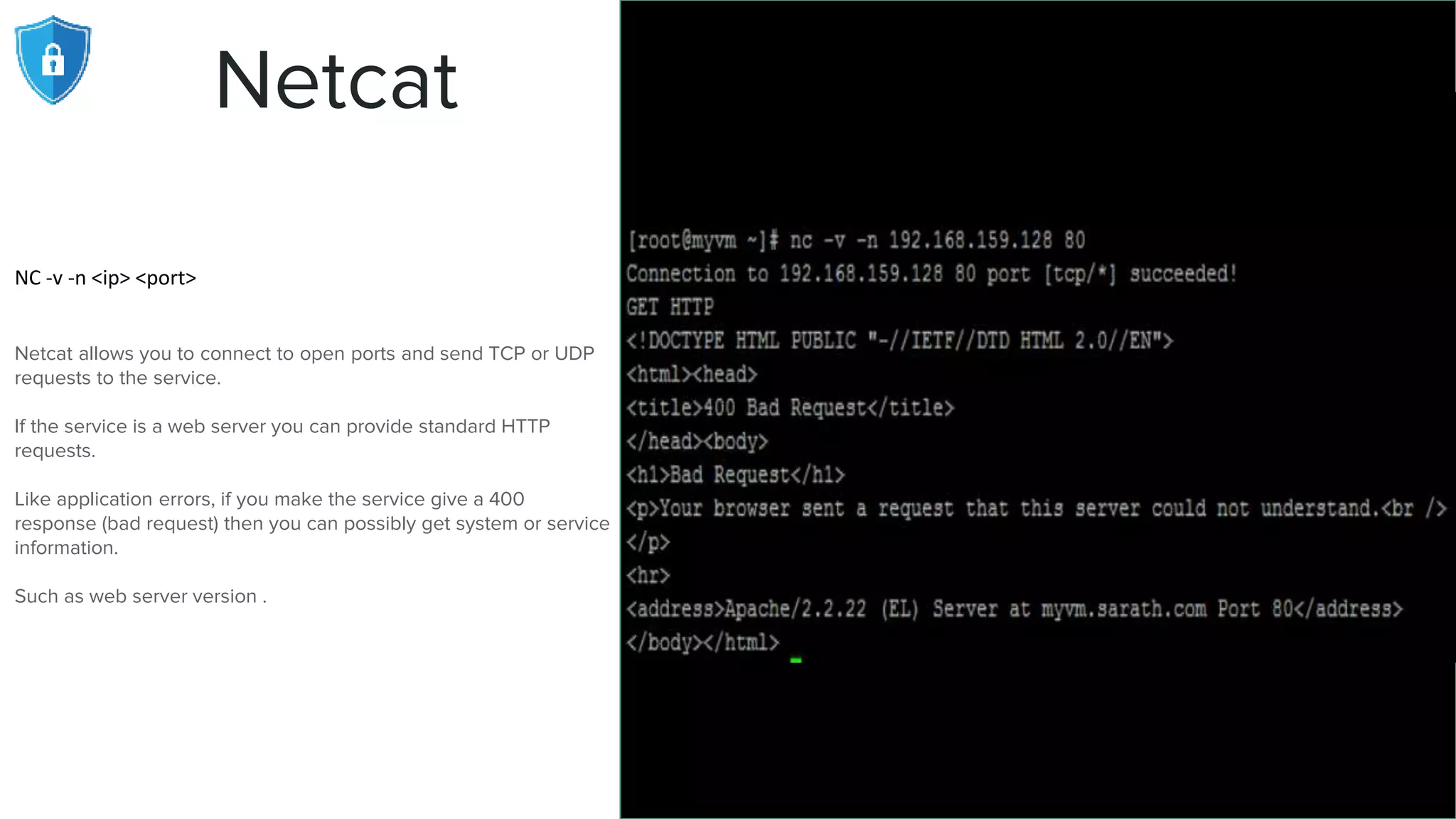
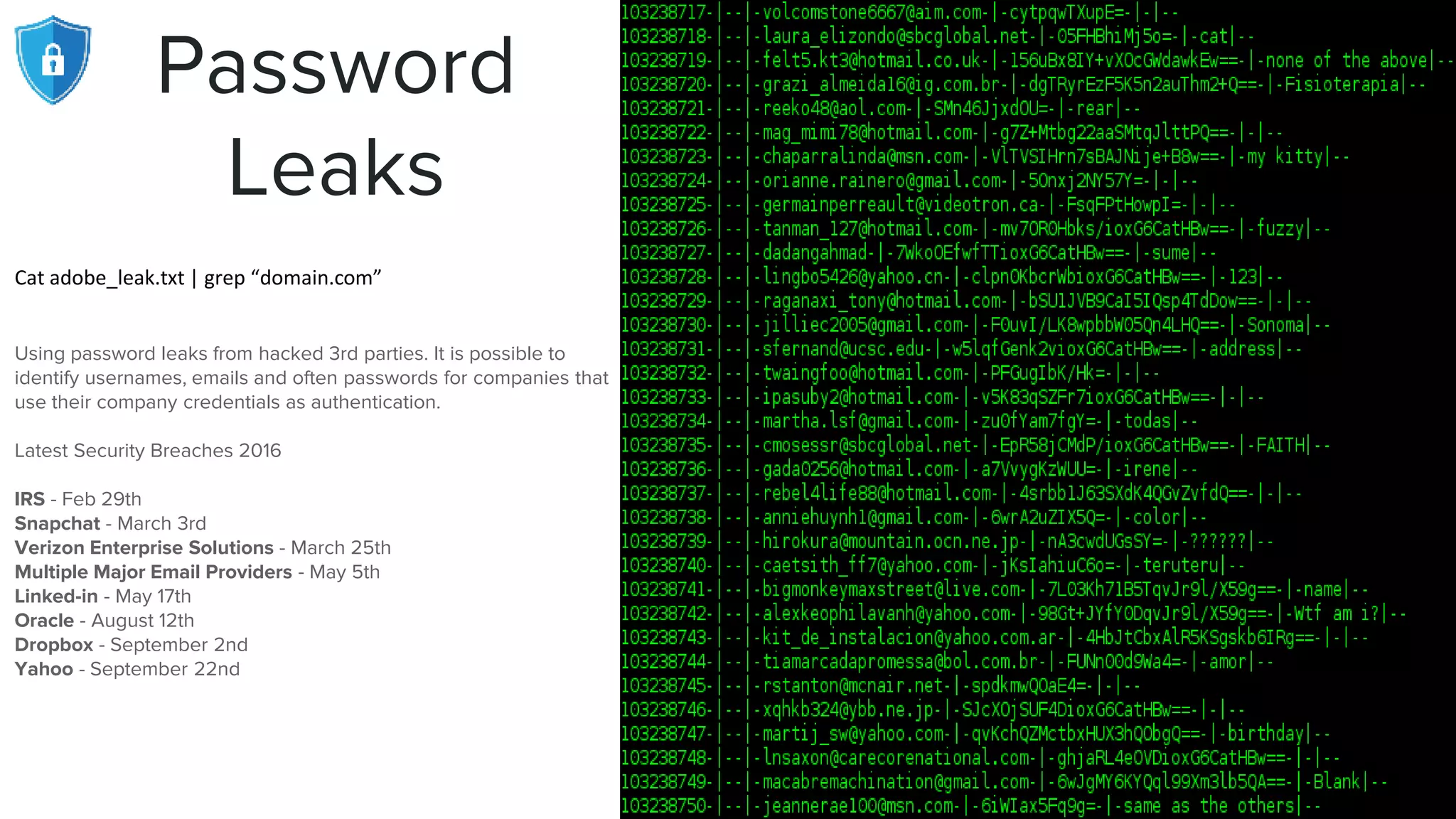
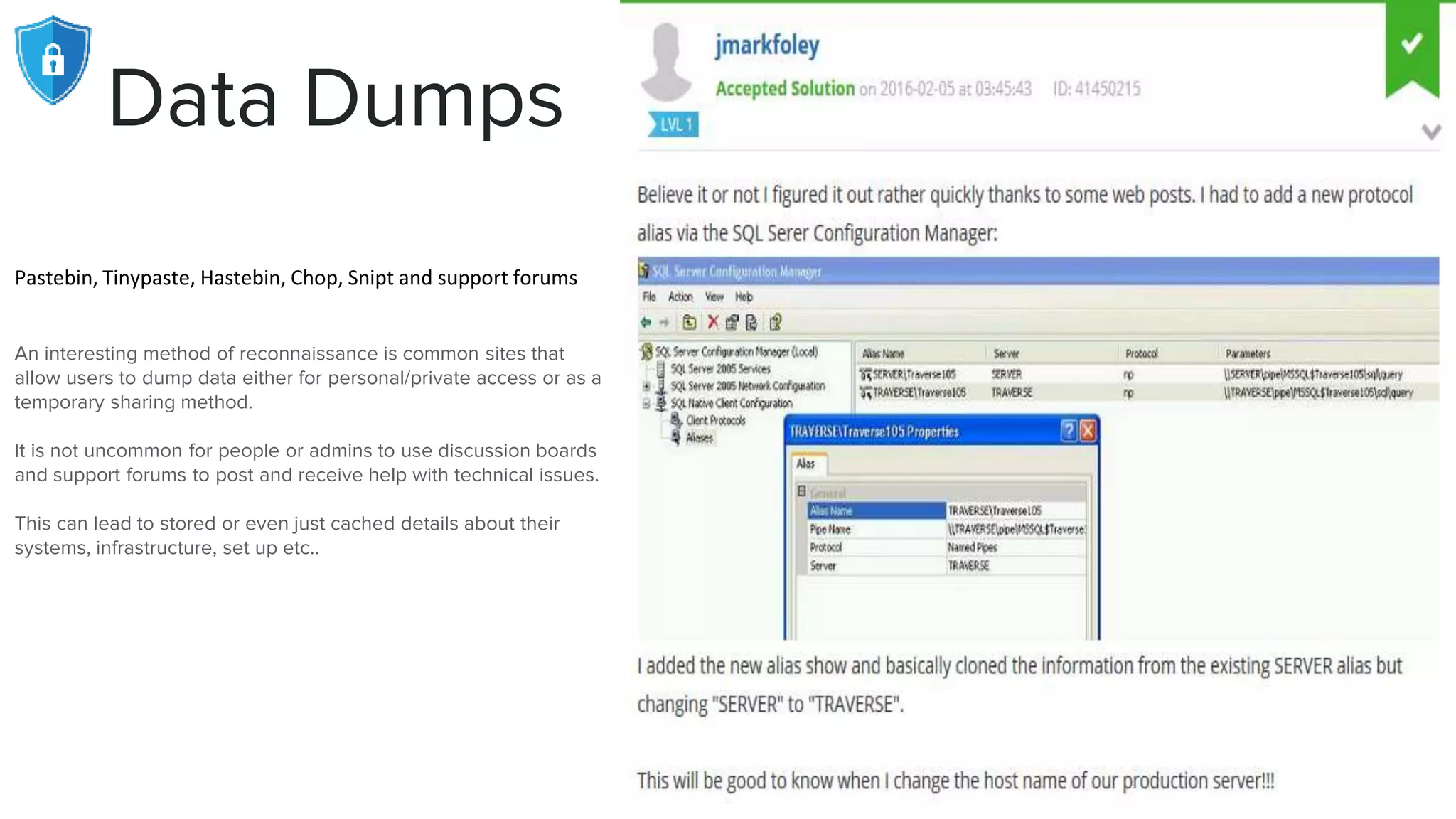
The document provides an extensive overview of reconnaissance and open-source intelligence techniques used in penetration testing, focusing on DNS enumeration, metadata collection, and server enumeration tools. It lists various tools available for gathering information about target systems, including functionalities and commands for each tool. The conclusion emphasizes the importance of operational security and thorough reconnaissance to effectively execute penetration testing strategies.