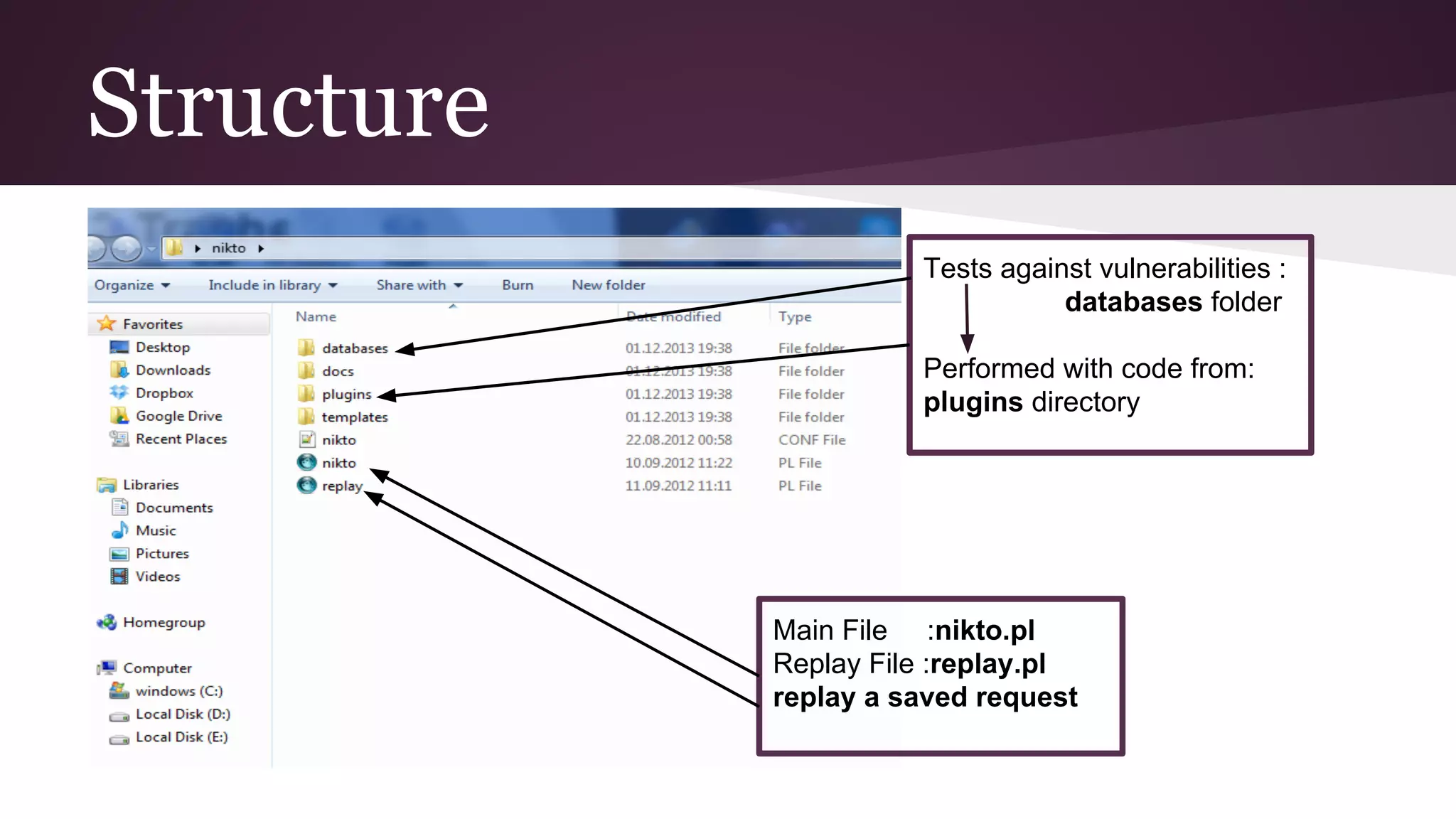
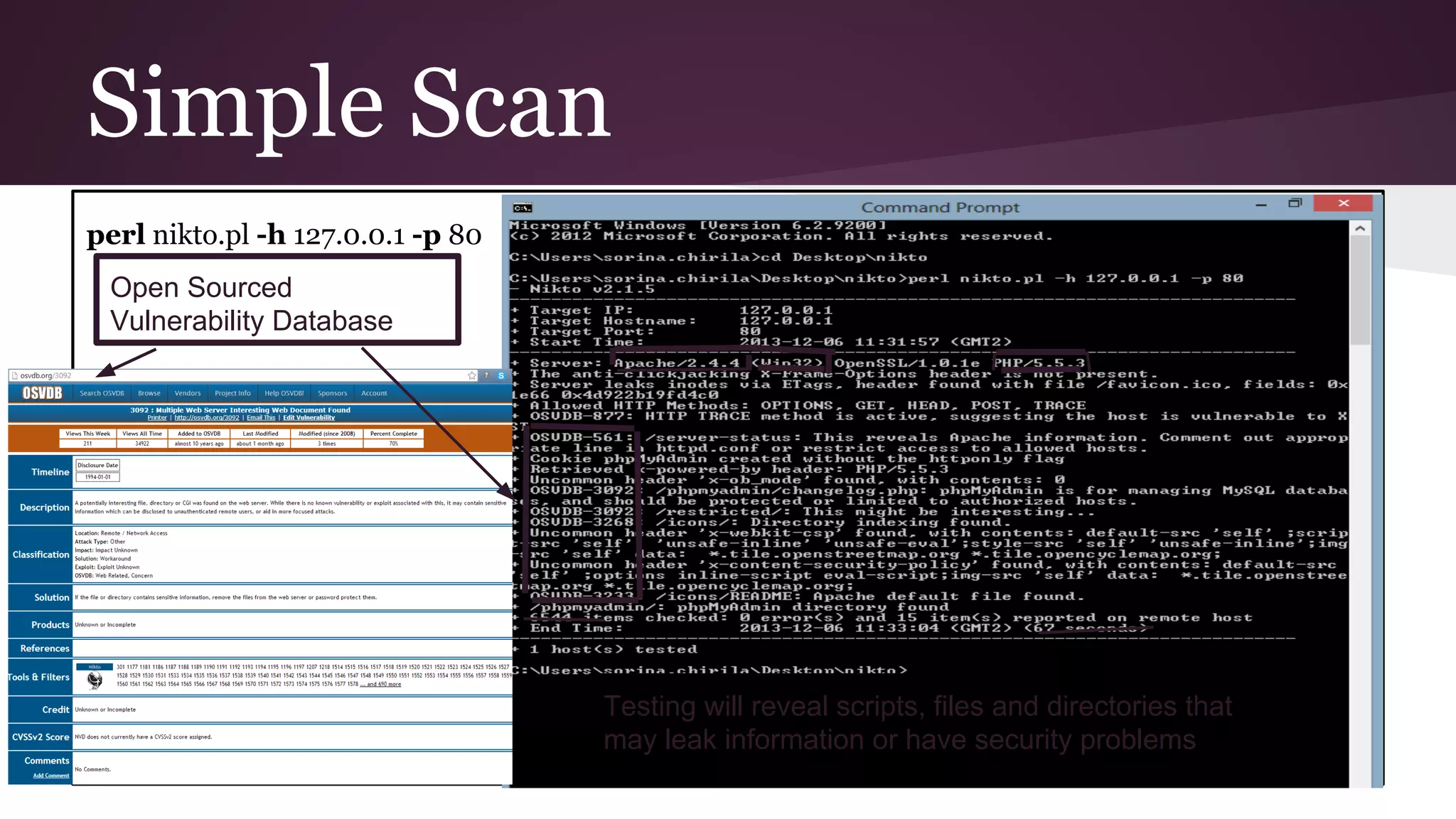
Nikto is a free and open source web server scanner used to identify vulnerabilities and help secure servers. It tests servers for over 6,500 dangerous files and scripts, outdated versions of software, and misconfigurations. Nikto scans target servers and outputs results that can help identify security problems. It has advantages like being fast, versatile, and open source, while its only disadvantage is needing to run via the command line.