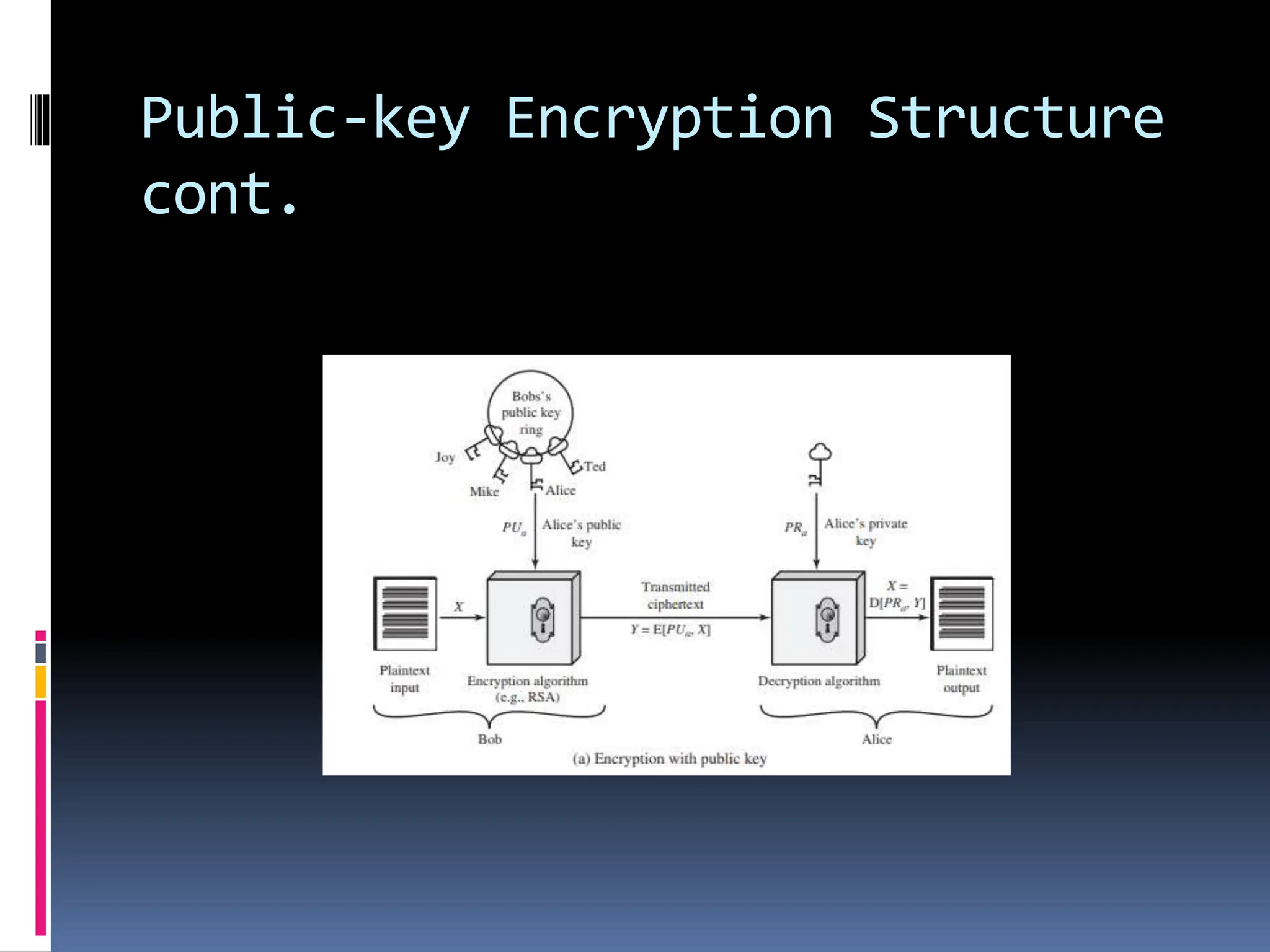
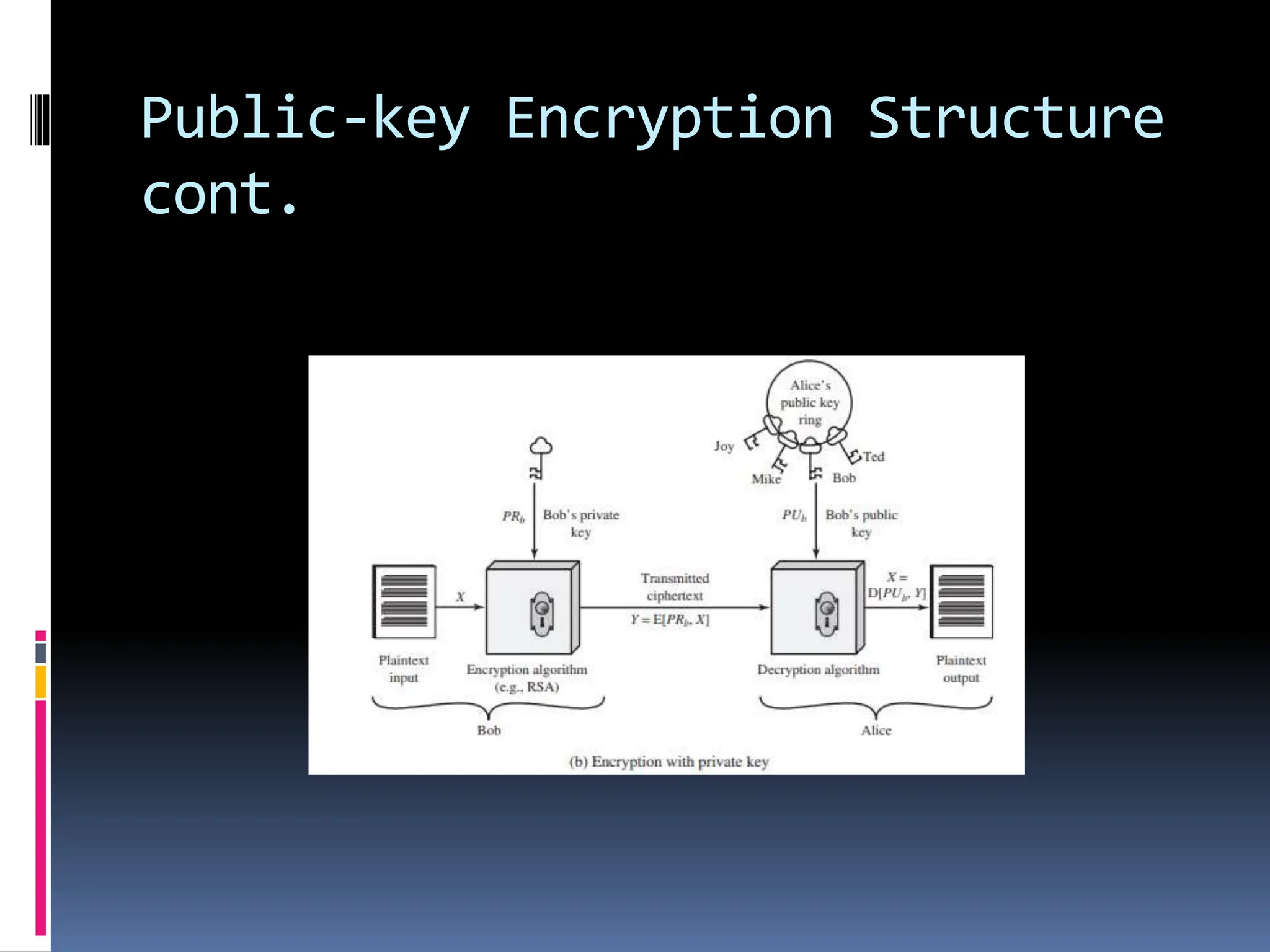
Public-key encryption, introduced by Diffie and Hellman in 1976, revolutionizes encryption by utilizing asymmetric algorithms based on mathematical functions rather than simple bit operations, distinguishing it from symmetric encryption. Key misconceptions include the belief that public-key encryption is inherently more secure, that it has made symmetric encryption obsolete, and that key distribution is simpler with public-key methods, while both encryption types have their own strengths and weaknesses. The public-key structure involves a pair of keys for encryption and decryption, with public keys shared openly and private keys kept secure, allowing for confidential communication as long as the private key remains protected.