Netcat is a versatile network utility tool that can be used for both legitimate network analysis and security issues identification. It allows creating inbound or outbound TCP or UDP connections to any ports and can be used for port scanning, data transfer, and performance testing. However, it also poses security risks if used maliciously by allowing execution of programs on listening ports, which could enable attacks like SYN flooding.




![How Do I use netcat ?
General form of usage is
nc [switches] [hostname] [portnumber]
Simplest Usage would be
nc –v www.msn.com 80
Use GET method GET / HTTP/1.0
Hostname can be a name or IP
Address](https://image.slidesharecdn.com/8c21da14-1c9c-44ee-8e24-9a1ddd64ca82-150211062639-conversion-gate02/85/Netcat-6-320.jpg)
![ Use of –n switch
If not specified performs forward and reverse
DNS look up
Reports the problem of mismatched names in
DNS
D:toolsnc>nc -v www.hotmail.com 80
DNS fwd/rev mismatch: www.hotmail.com != hotmail.se
DNS fwd/rev mismatch: www.hotmail.com !=
ld.cb.msn.com
DNS fwd/rev mismatch: www.hotmail.com !=
ld.cb.msn.com
www.hotmail.com [207.68.171.233] 80 (http) open
IF specified will take only IPAddress as hostname
argument](https://image.slidesharecdn.com/8c21da14-1c9c-44ee-8e24-9a1ddd64ca82-150211062639-conversion-gate02/85/Netcat-7-320.jpg)



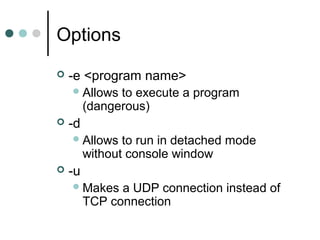
![Options
-L
Listen harder
-r
Randomize port numbers
-z
Zero – I/O mode [used in scanning]](https://image.slidesharecdn.com/8c21da14-1c9c-44ee-8e24-9a1ddd64ca82-150211062639-conversion-gate02/85/Netcat-11-320.jpg)



![D:toolsnc>nc -v -w 5 -r davinci.newcs.uwindsor.ca 20-30
davinci.newcs.uwindsor.ca [137.207.76.3] 22 (?) open
SSH-2.0-Sun_SSH_1.0
davinci.newcs.uwindsor.ca [137.207.76.3] 28 (?) open
davinci.newcs.uwindsor.ca [137.207.76.3] 20 (ftp-data) open
davinci.newcs.uwindsor.ca [137.207.76.3] 23 (telnet) open
internet2 proxy-telnet [v3.1] ready
√☺Please enter your userid: davinci.newcs.uwindsor.ca [137.207.76.3] 24 (?)
open
davinci.newcs.uwindsor.ca [137.207.76.3] 30 (?) open
davinci.newcs.uwindsor.ca [137.207.76.3] 25 (smtp) open
220-Sendmail 8.6.12/8.6.12 ready on internet2
220 ESMTP spoken here
davinci.newcs.uwindsor.ca [137.207.76.3] 26 (?) open
davinci.newcs.uwindsor.ca [137.207.76.3] 29 (?) open
davinci.newcs.uwindsor.ca [137.207.76.3] 27 (?) open
davinci.newcs.uwindsor.ca [137.207.76.3] 21 (ftp) open
220- internet2 proxy-ftp [v3.1] ready
220 Please enter your userid
D:toolsnc>](https://image.slidesharecdn.com/8c21da14-1c9c-44ee-8e24-9a1ddd64ca82-150211062639-conversion-gate02/85/Netcat-16-320.jpg)




![RESULT
D:toolsnc>nc -l -p 21 -e cmd.exe
LISTENER
C:Documents and SettingsRAJAT>ftp 192.168.0.100
Connected to 192.168.0.100.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
D:toolsnc>
Request](https://image.slidesharecdn.com/8c21da14-1c9c-44ee-8e24-9a1ddd64ca82-150211062639-conversion-gate02/85/Netcat-21-320.jpg)