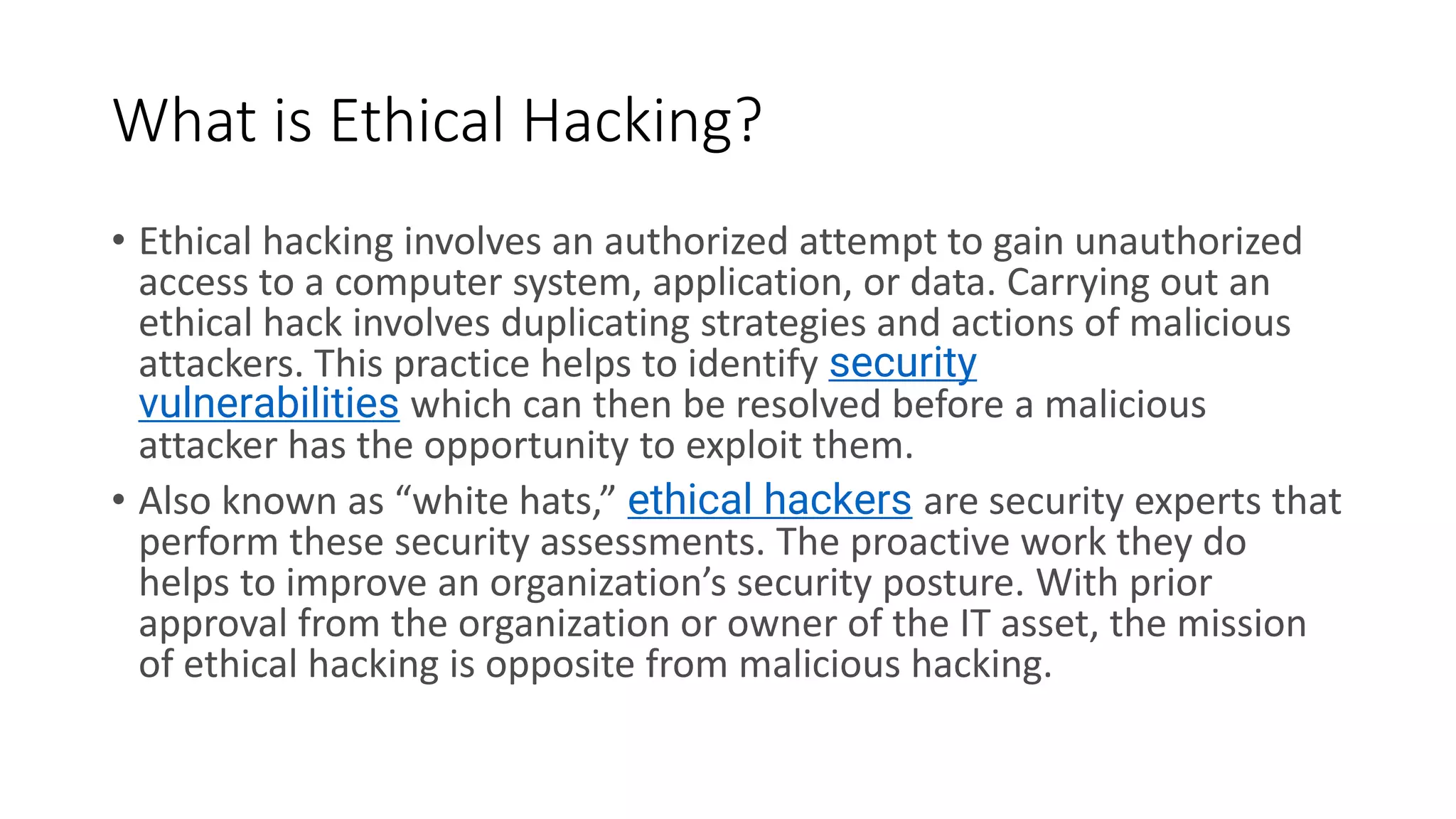
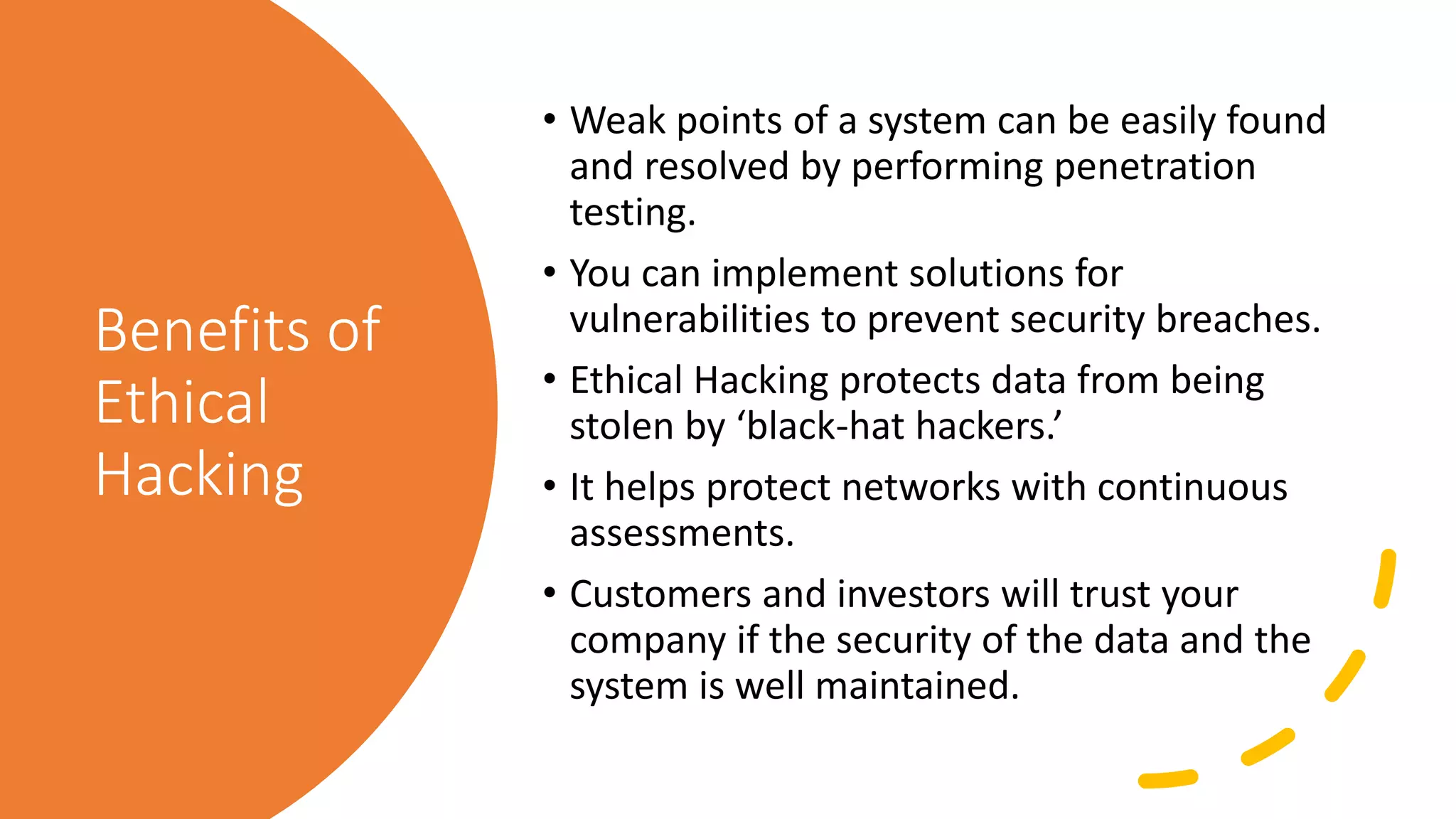
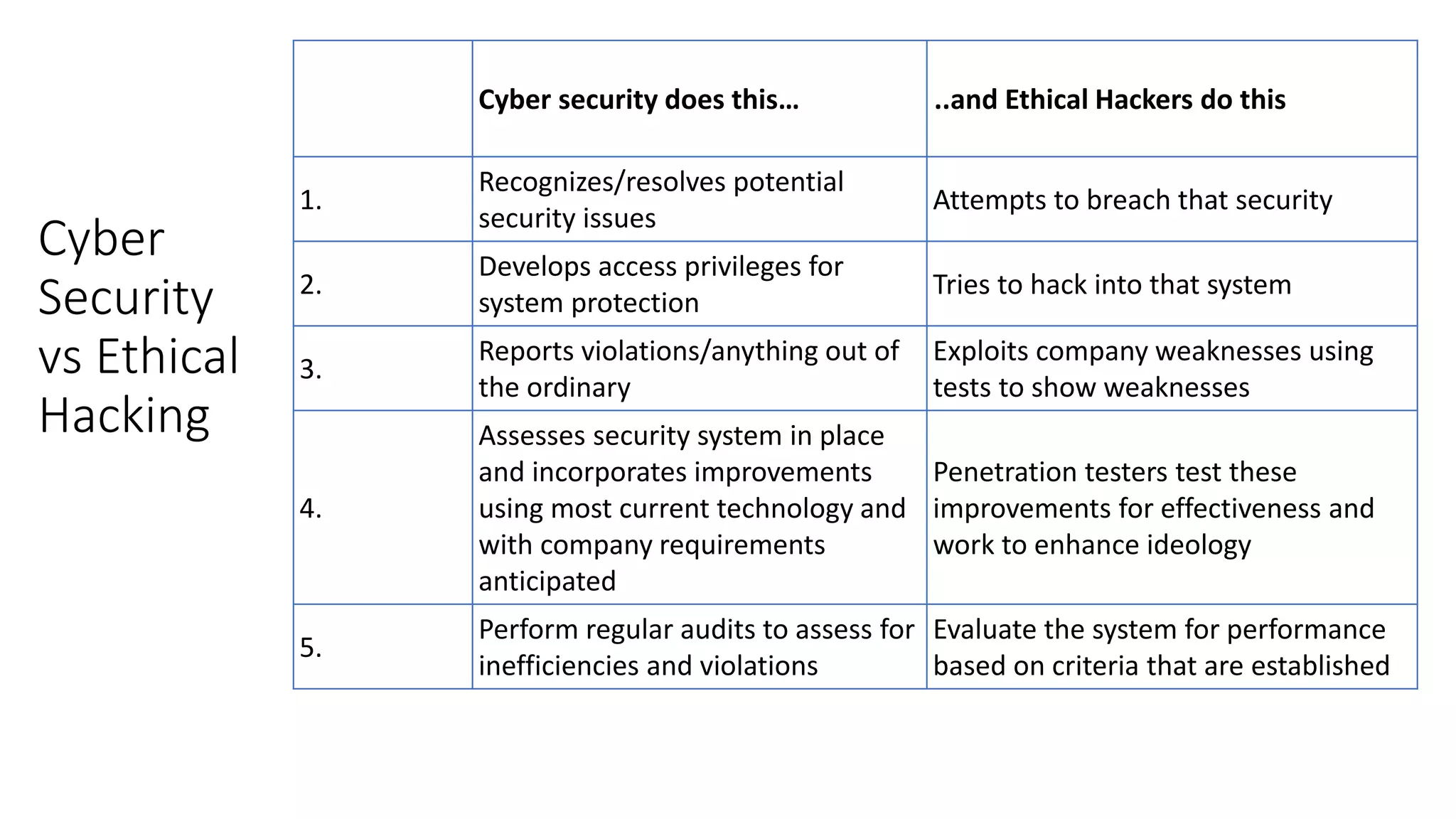
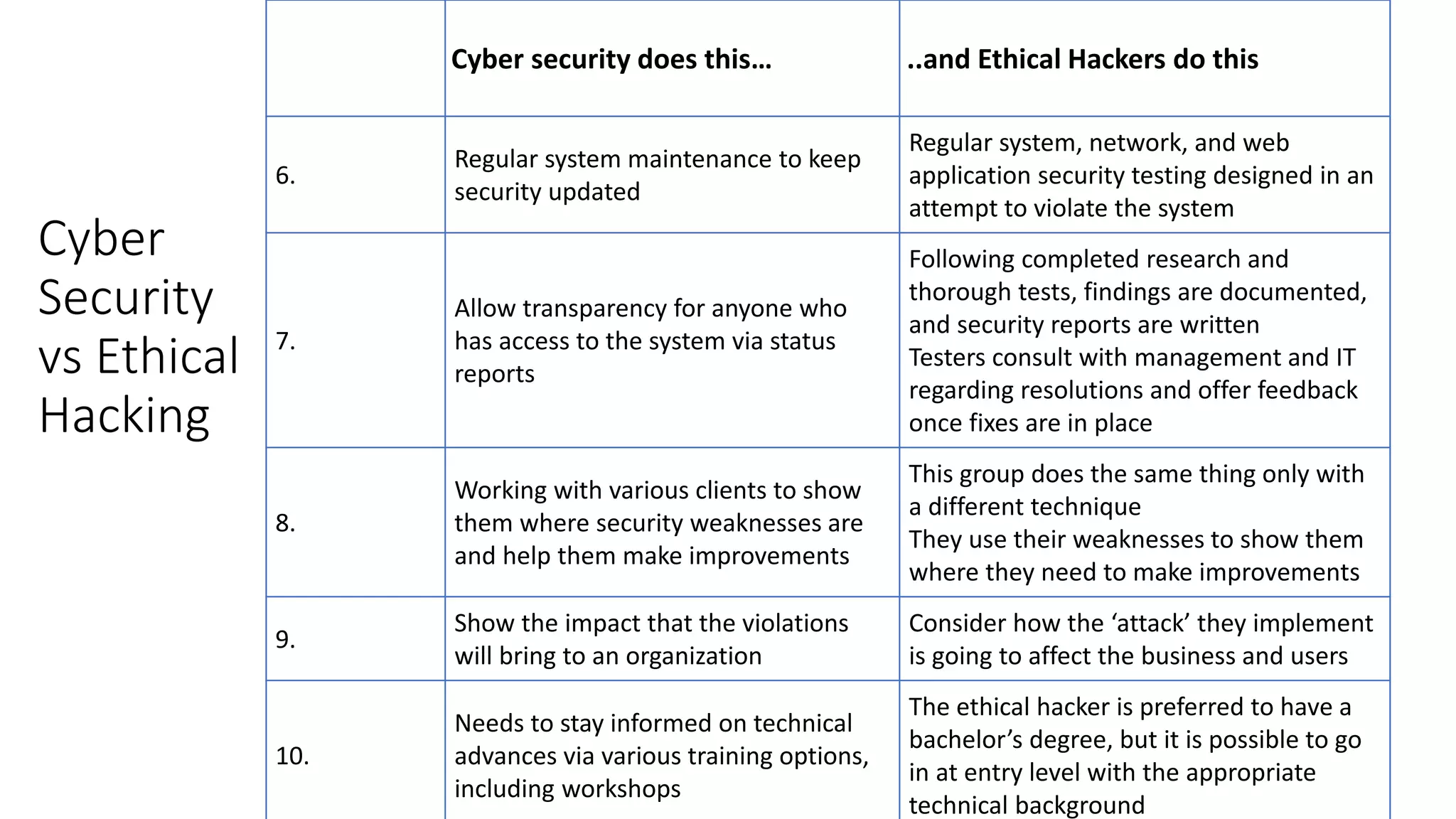
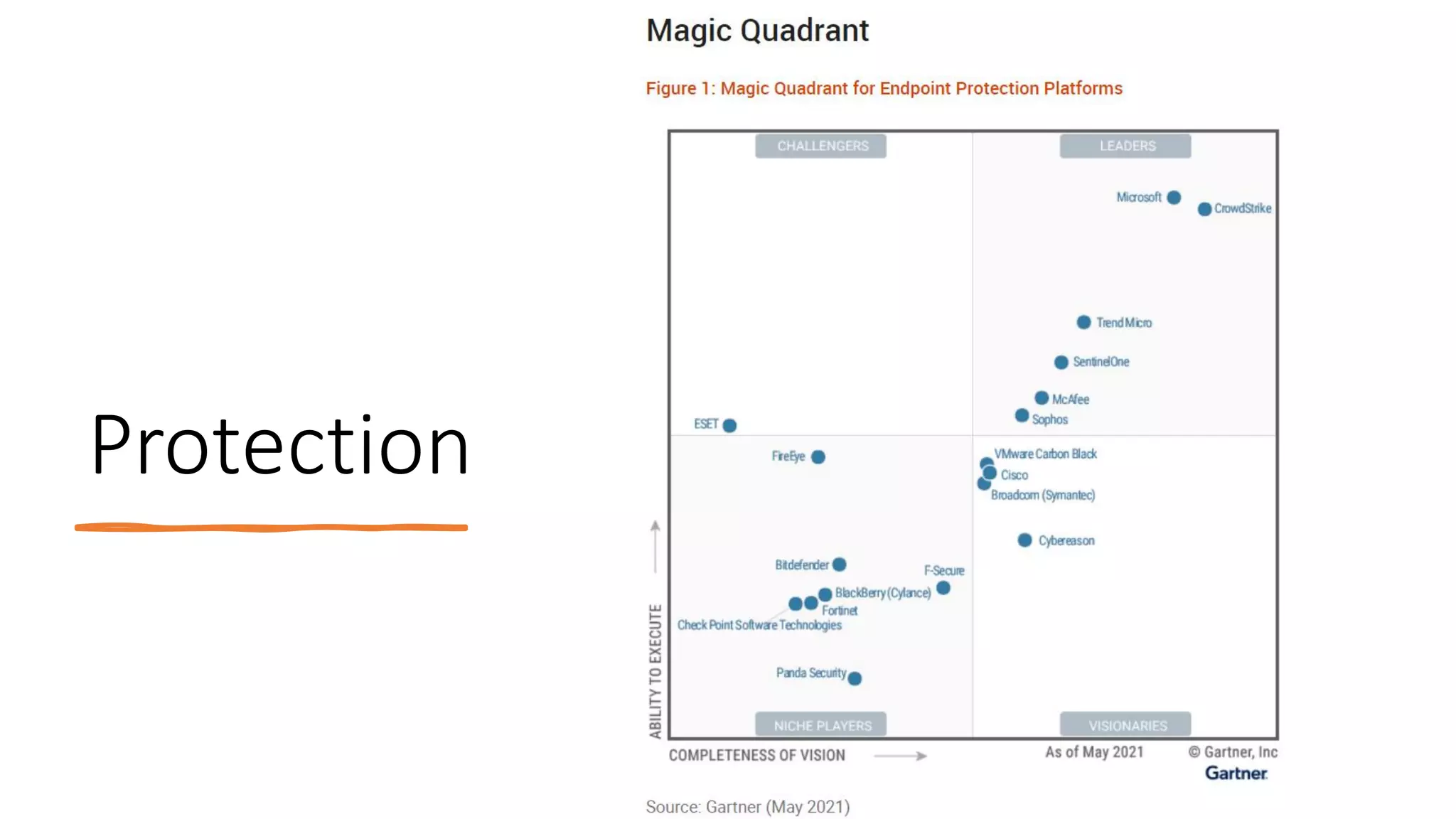
Cyber security involves protecting systems from attacks by implementing security measures and resolving issues. Ethical hacking takes an authorized approach to attempt gaining unauthorized access to systems to identify vulnerabilities. It involves duplicating hacker strategies with permission to find weaknesses before exploits. Both cyber security and ethical hacking work to improve security, but cyber security recognizes, resolves, and reports issues, while ethical hacking tries to breach security for testing to provide feedback on weaknesses.