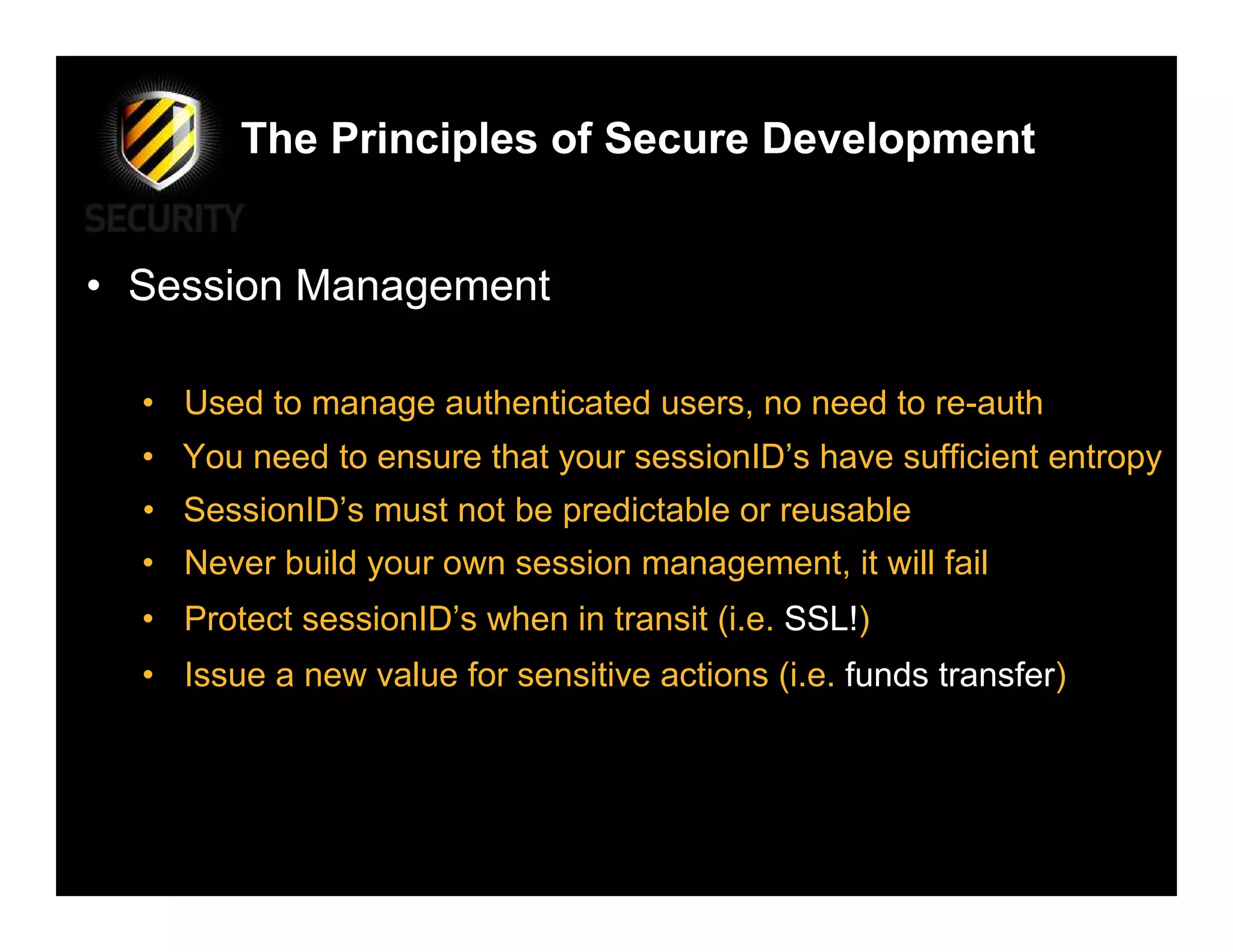
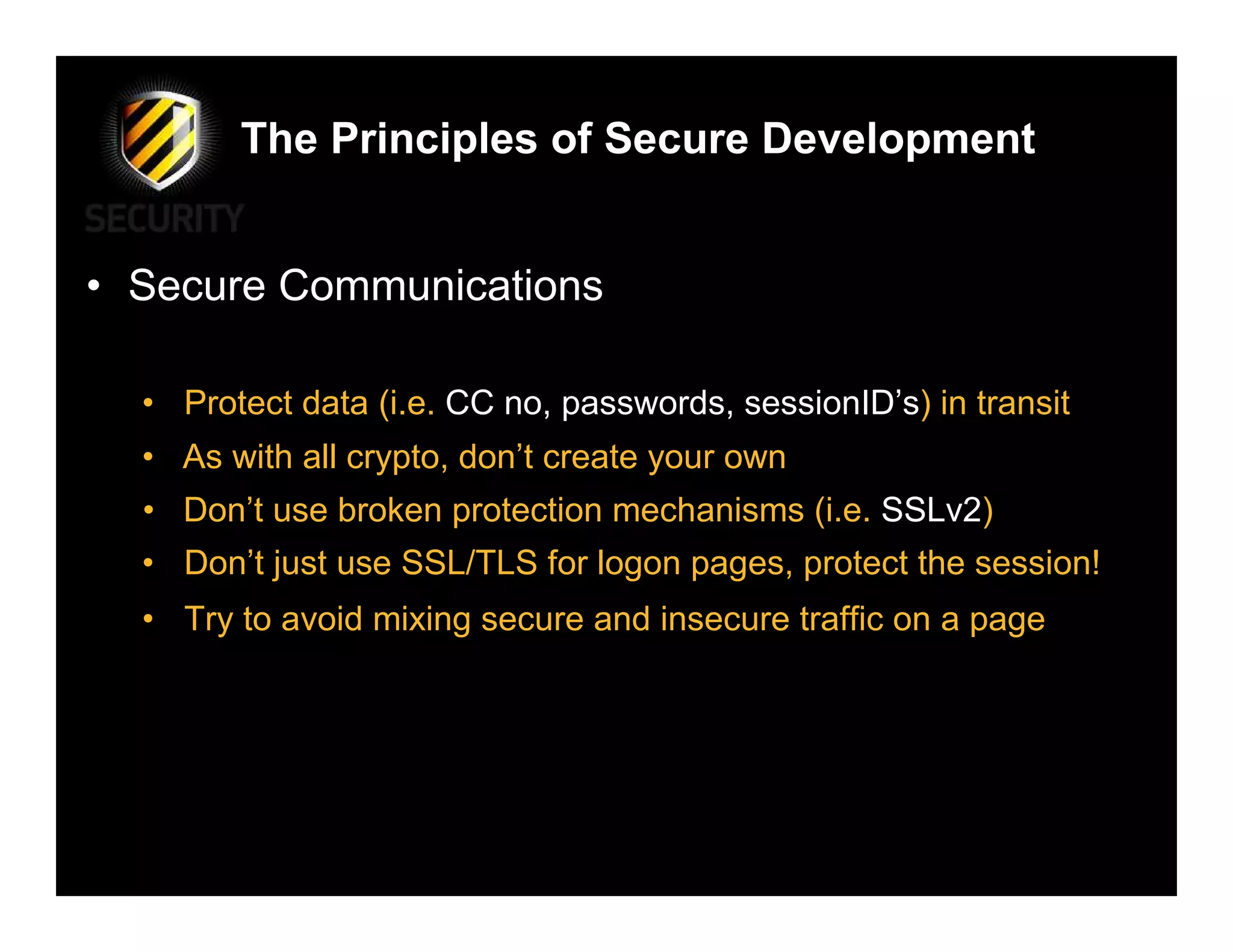
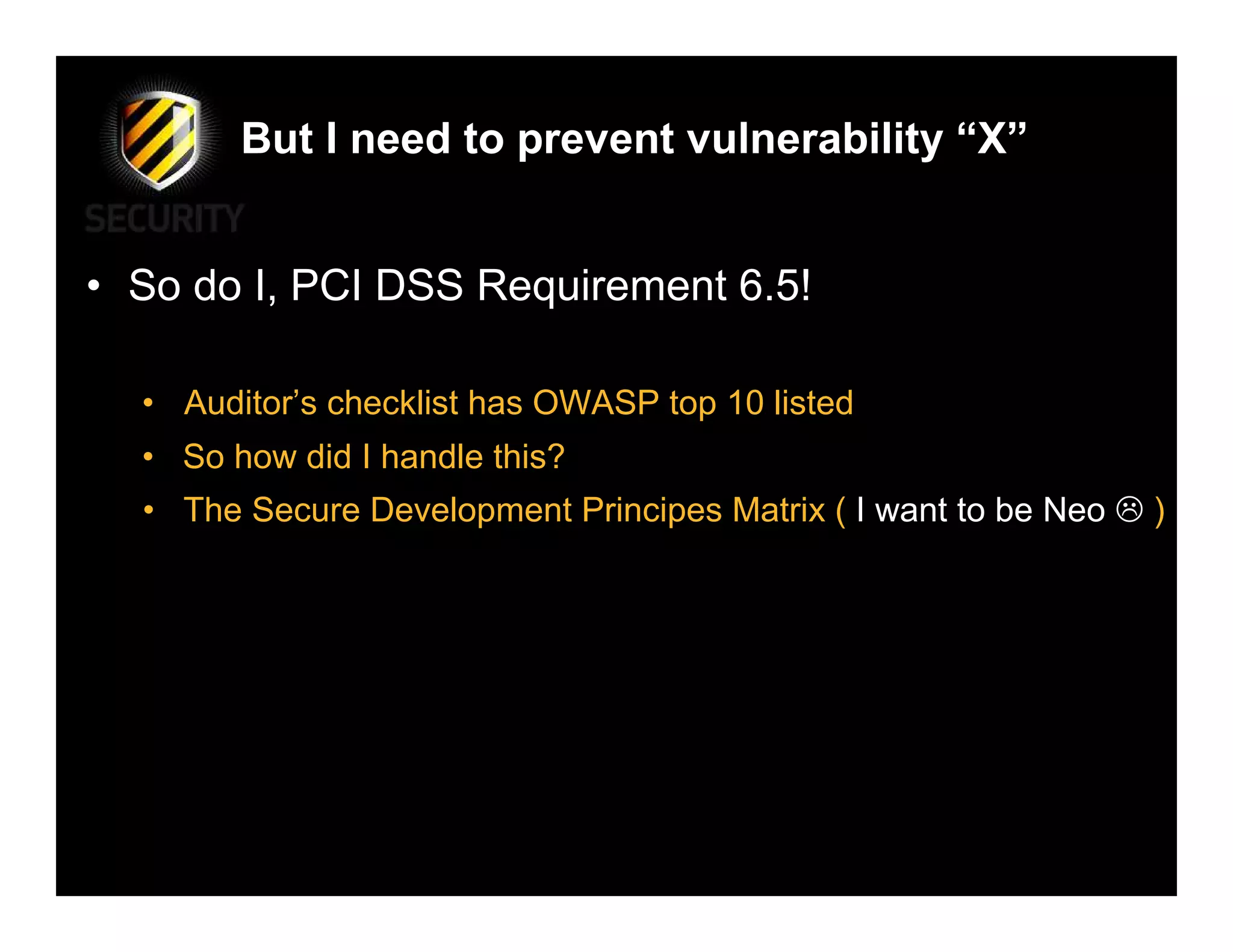
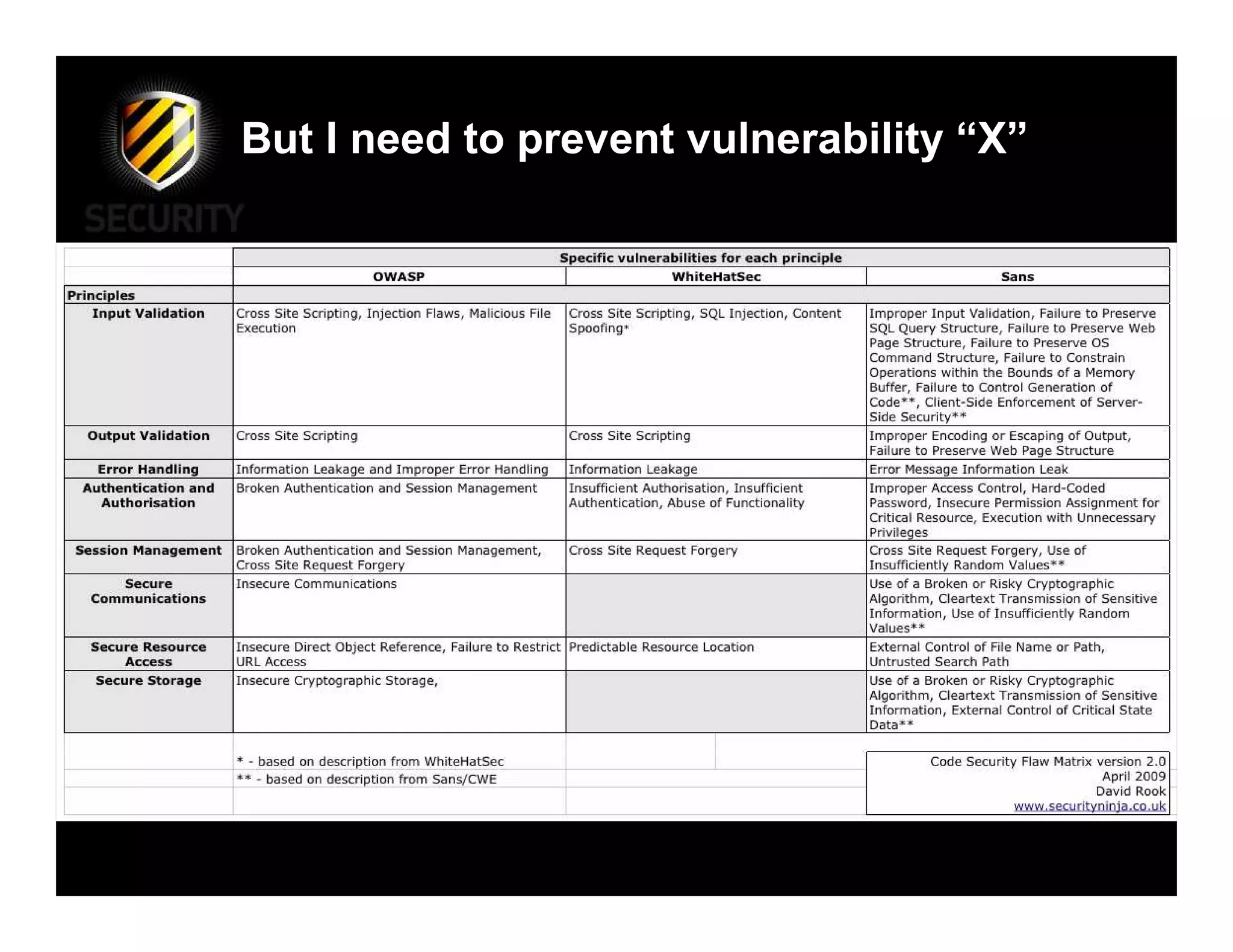
David Rook discusses the principles of secure development in software, highlighting the need for a proactive approach to prevent vulnerabilities by teaching developers secure coding practices rather than just informing them of specific vulnerabilities. He emphasizes essential principles such as input validation, error handling, and secure communications, while critiquing the current methods that often lead to security flaws in applications. Rook advocates for integrating security throughout the development process to ensure robust applications against threats.










![The Principles of Secure Development
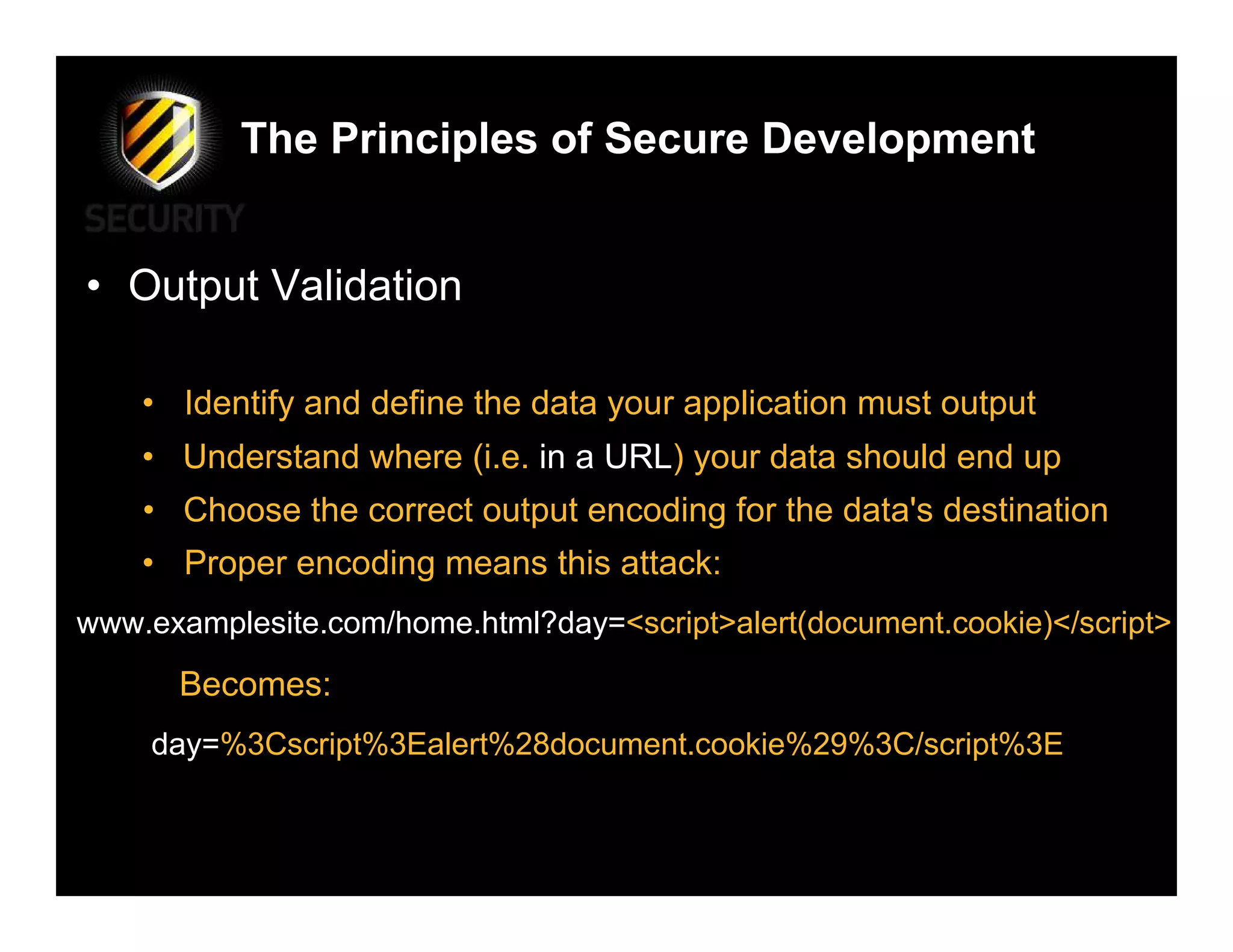
• Error Handling
• Even the best apps will crash at some point, be prepared!
• Crashes/errors can help an attacker if you don’t handle them
• Handle error conditions securely, sanitise the message sent
• No error handling = information leakage
Microsoft OLE DB Provider for ODBC
Drivers(0x80040E14)
[Microsoft][ODBC SQL Server Driver][SQL
Server]Invalid column name
/examplesite/login.asp, line 10](https://image.slidesharecdn.com/securitybsides-david-rook-110322061329-phpapp01/75/The-Principles-of-Secure-Development-BSides-Las-Vegas-2009-15-2048.jpg)