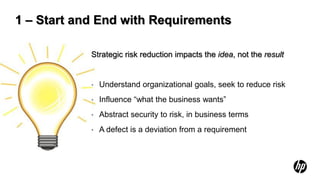
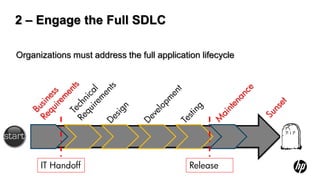
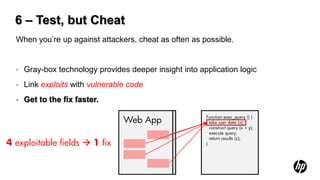
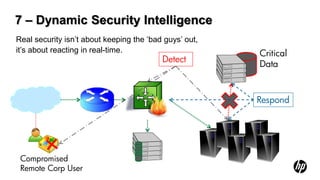
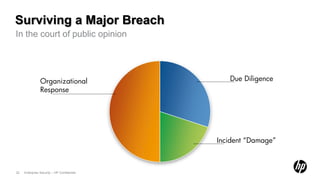
The document outlines the future of software security assurance, highlighting the necessity for modernized security practices in response to outdated applications and the challenges posed by cloud adoption. It identifies five key catalysts for change and proposes eight evolutions in software security strategies, emphasizing risk-based defense and the need for organizations to engage in the full application lifecycle. The overarching message is that proactive measures and adapting to emerging security challenges are critical to mitigating risks effectively.