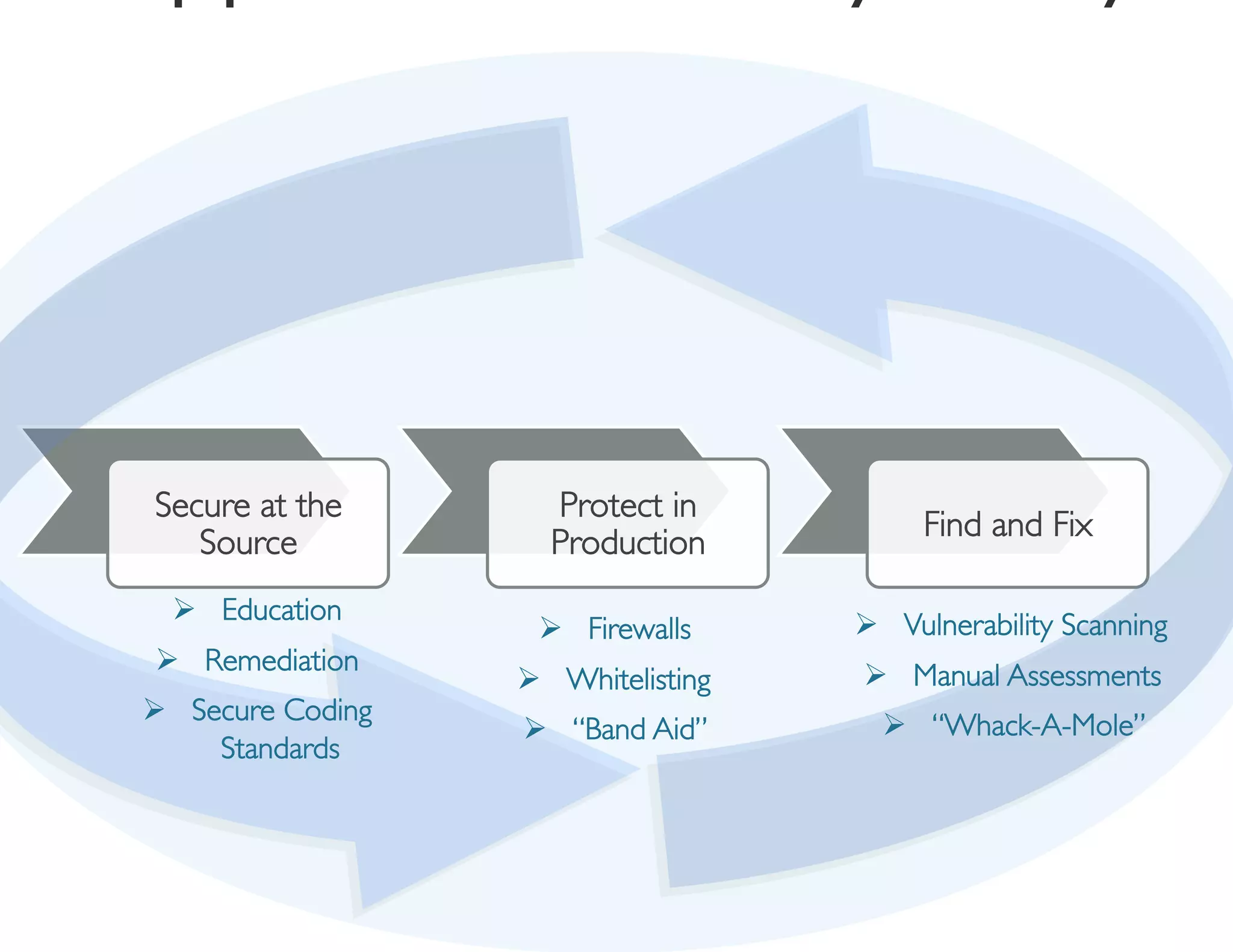
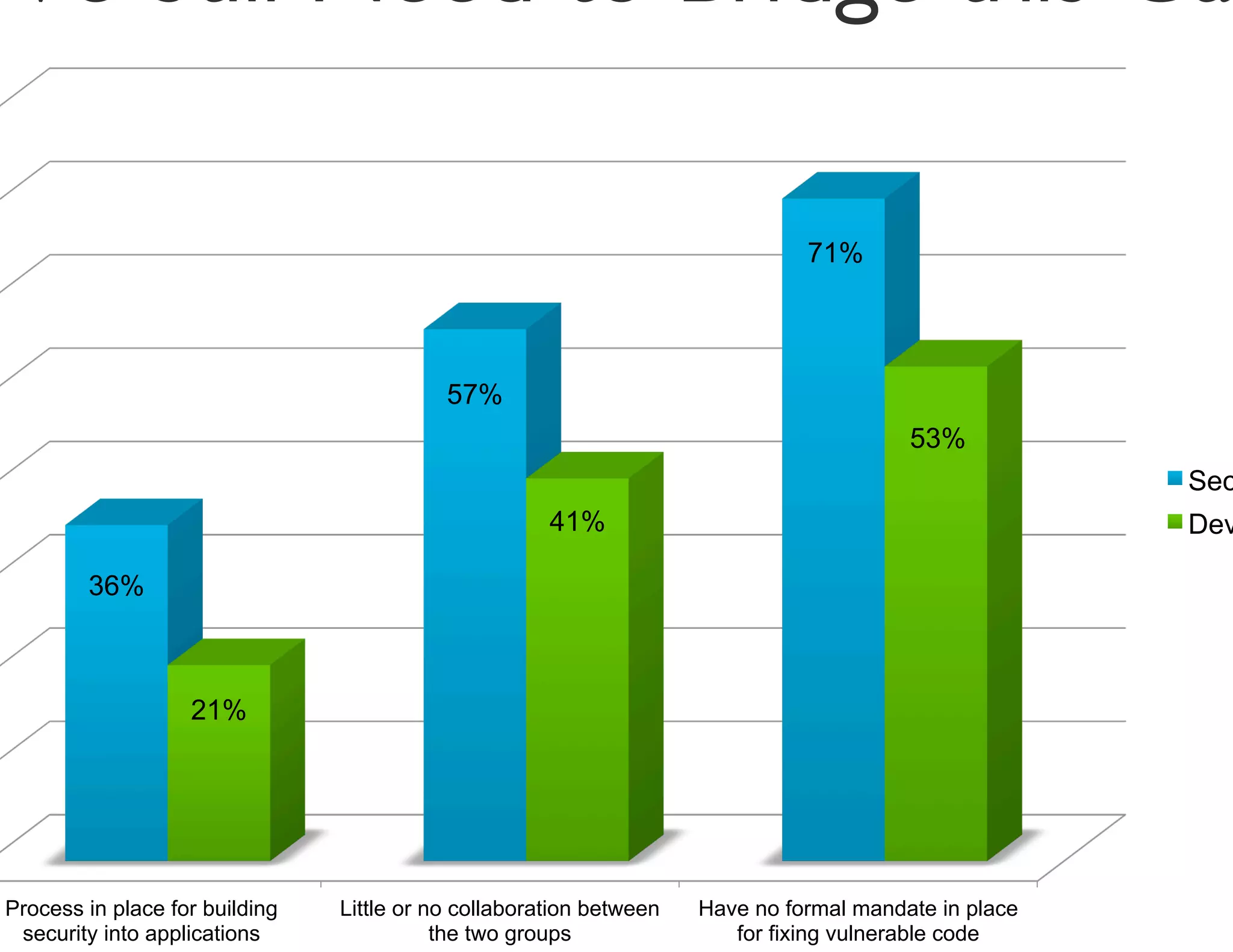
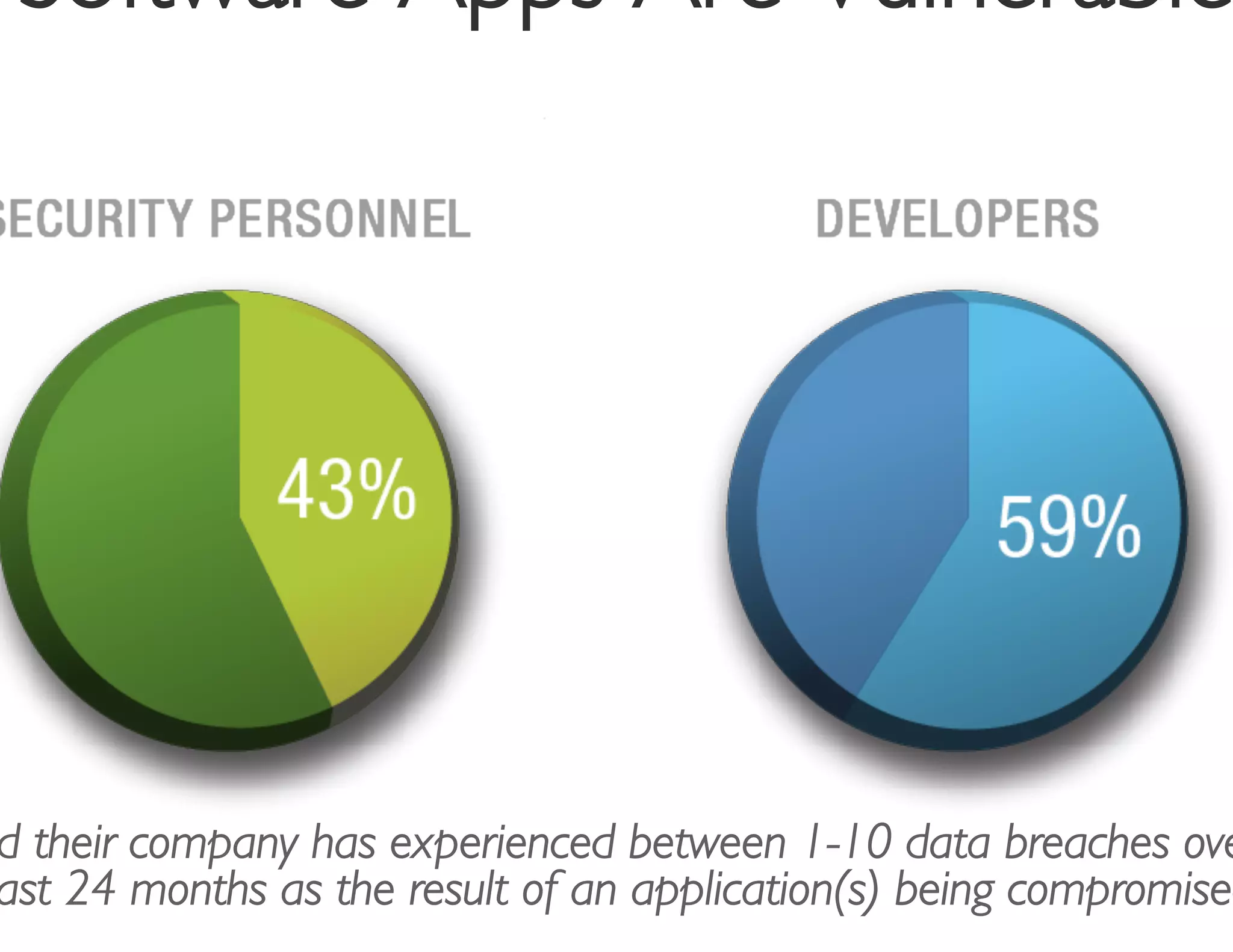
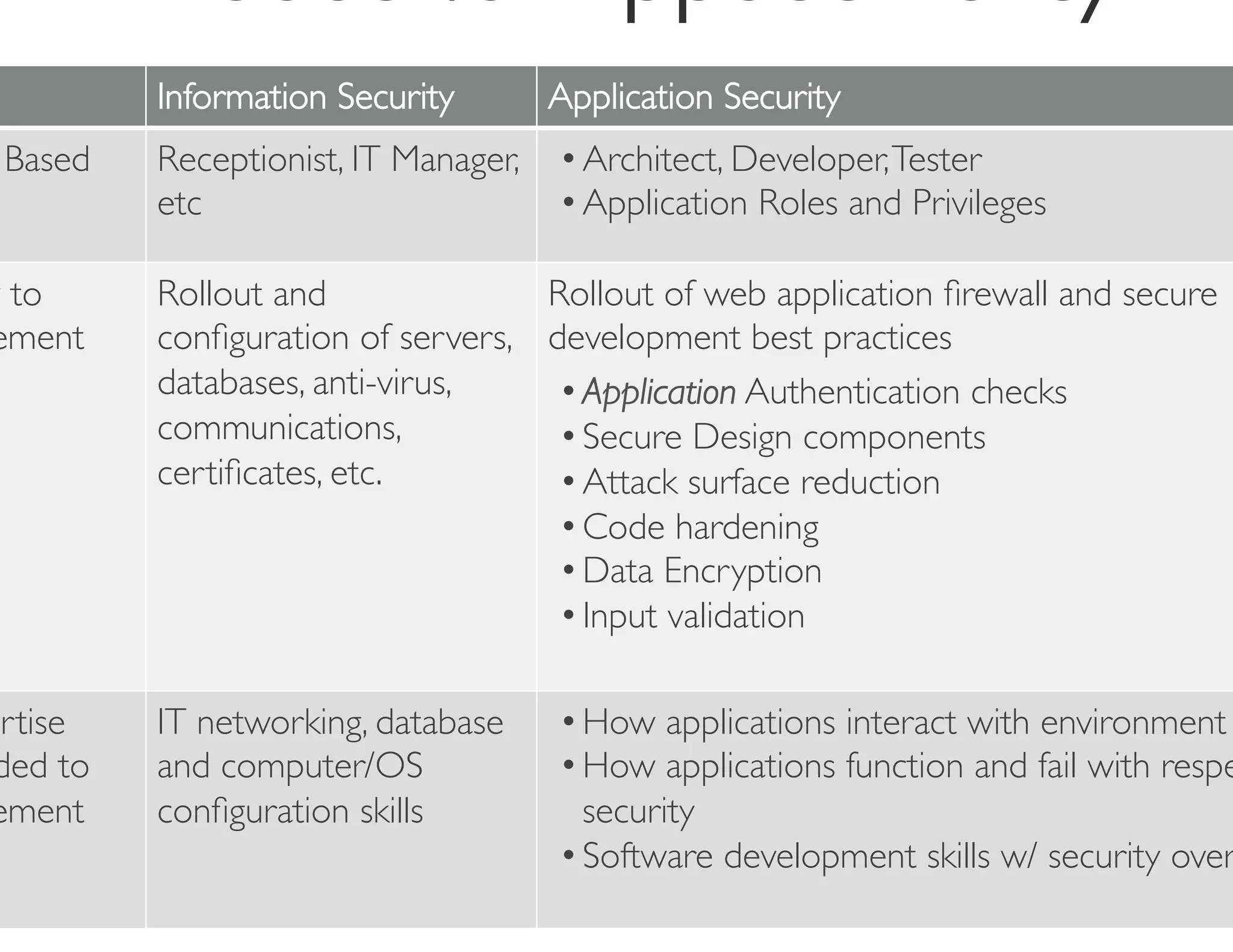
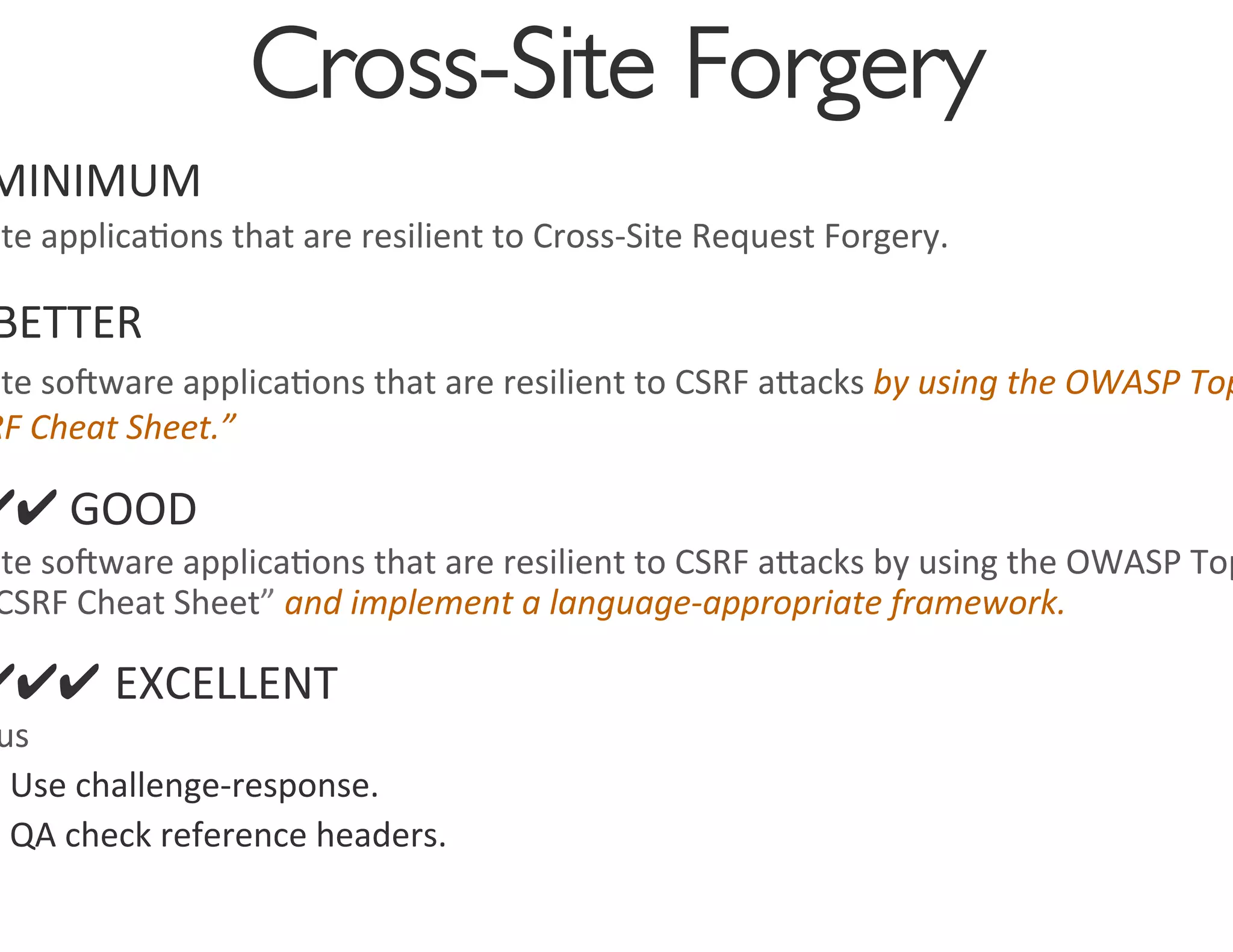
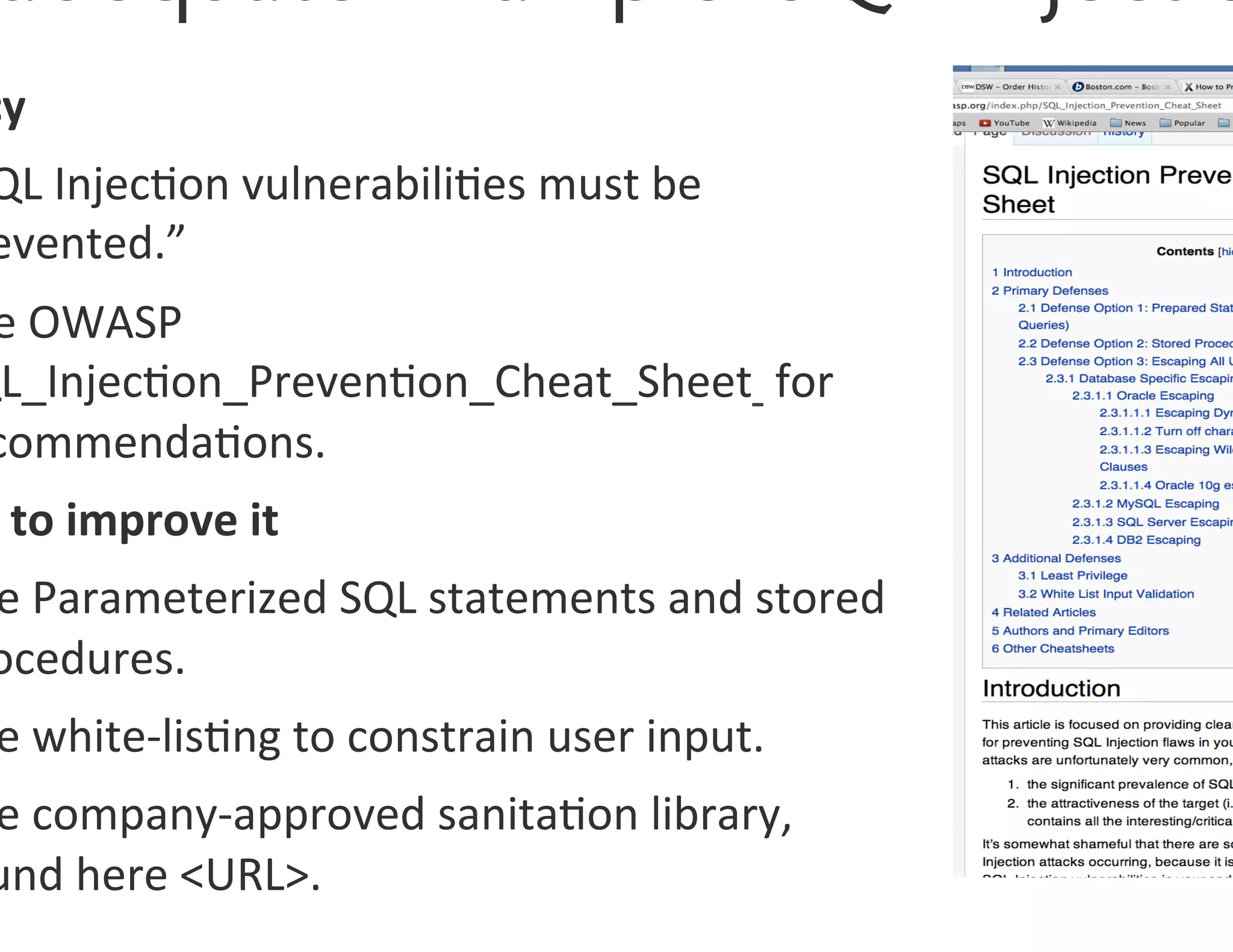
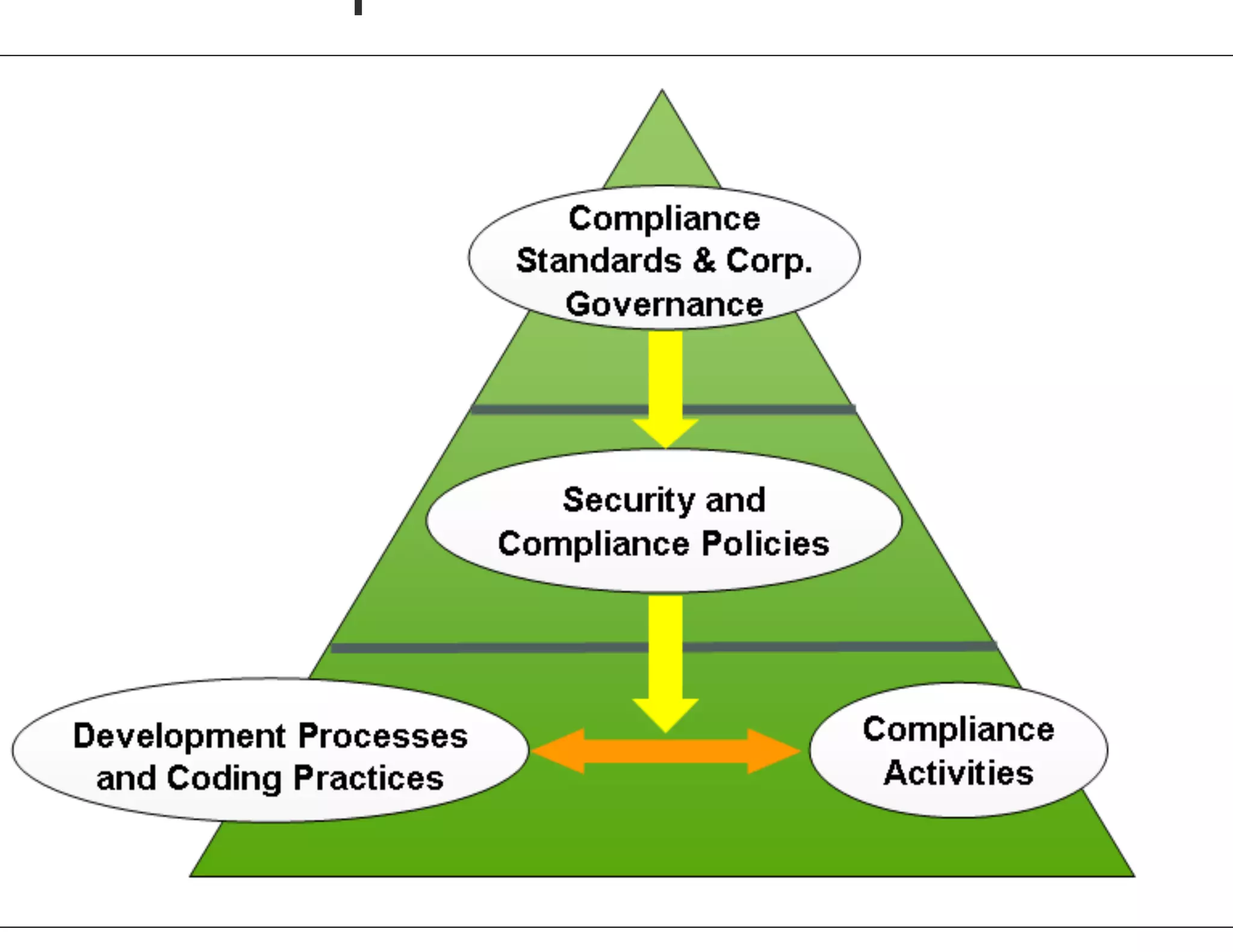
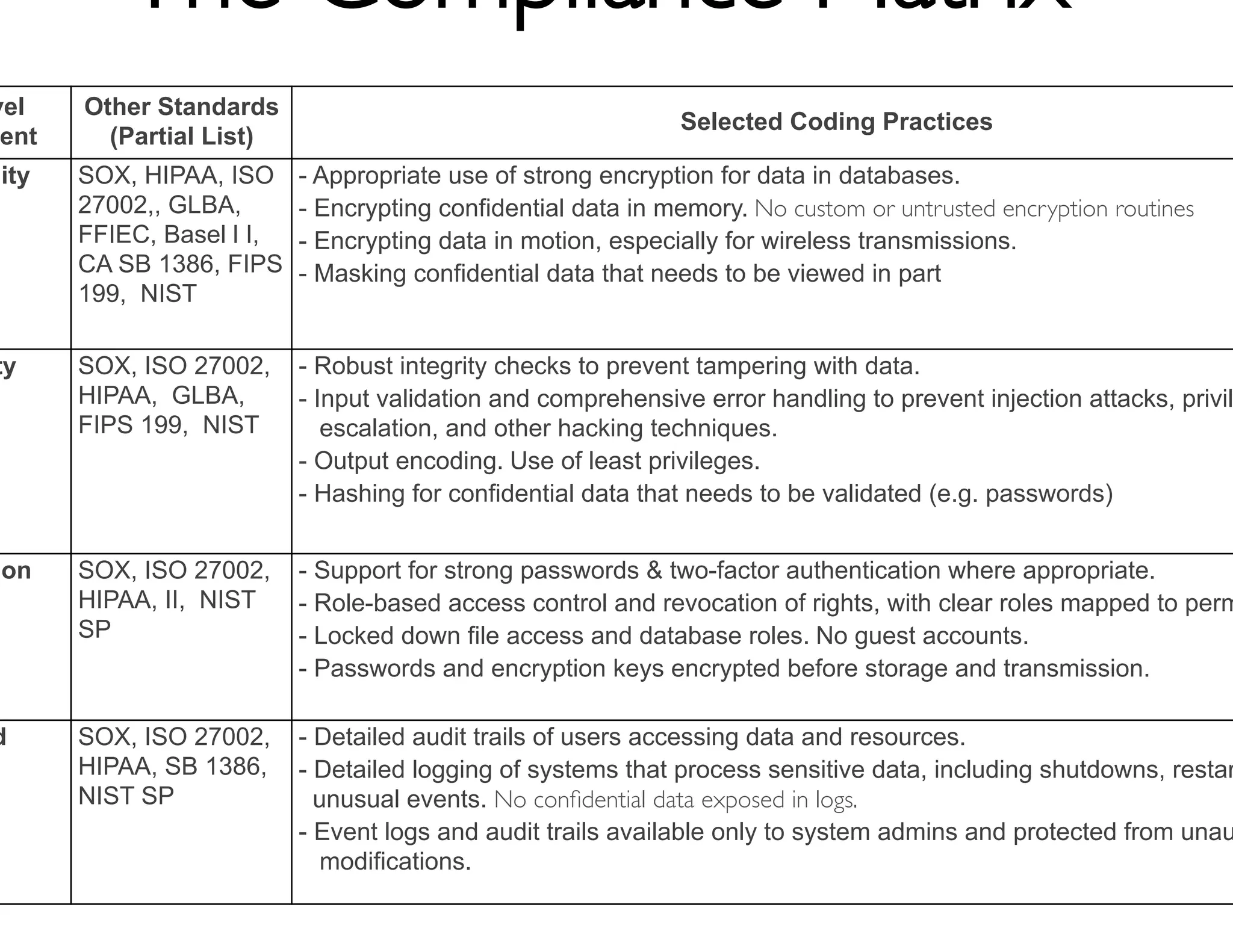
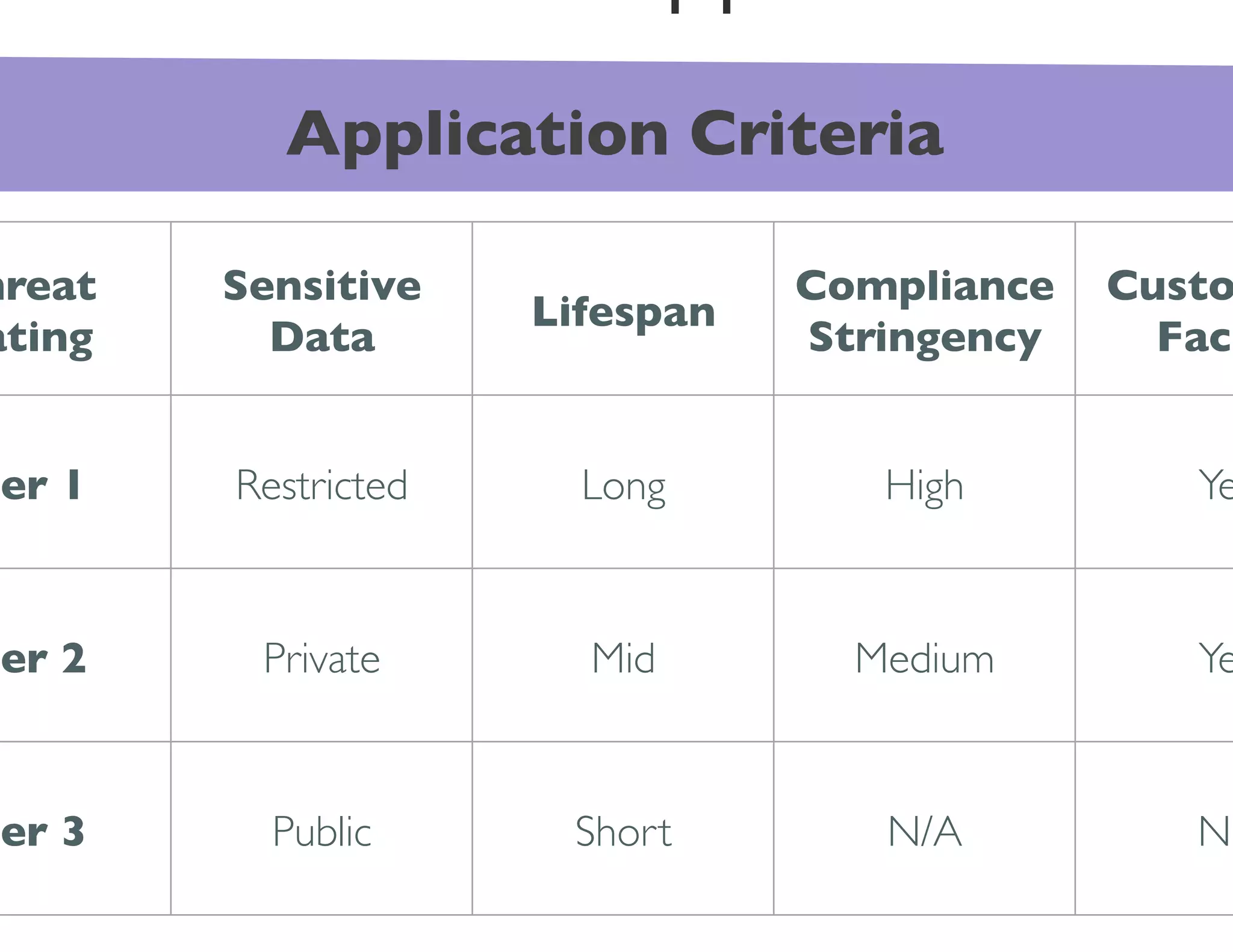
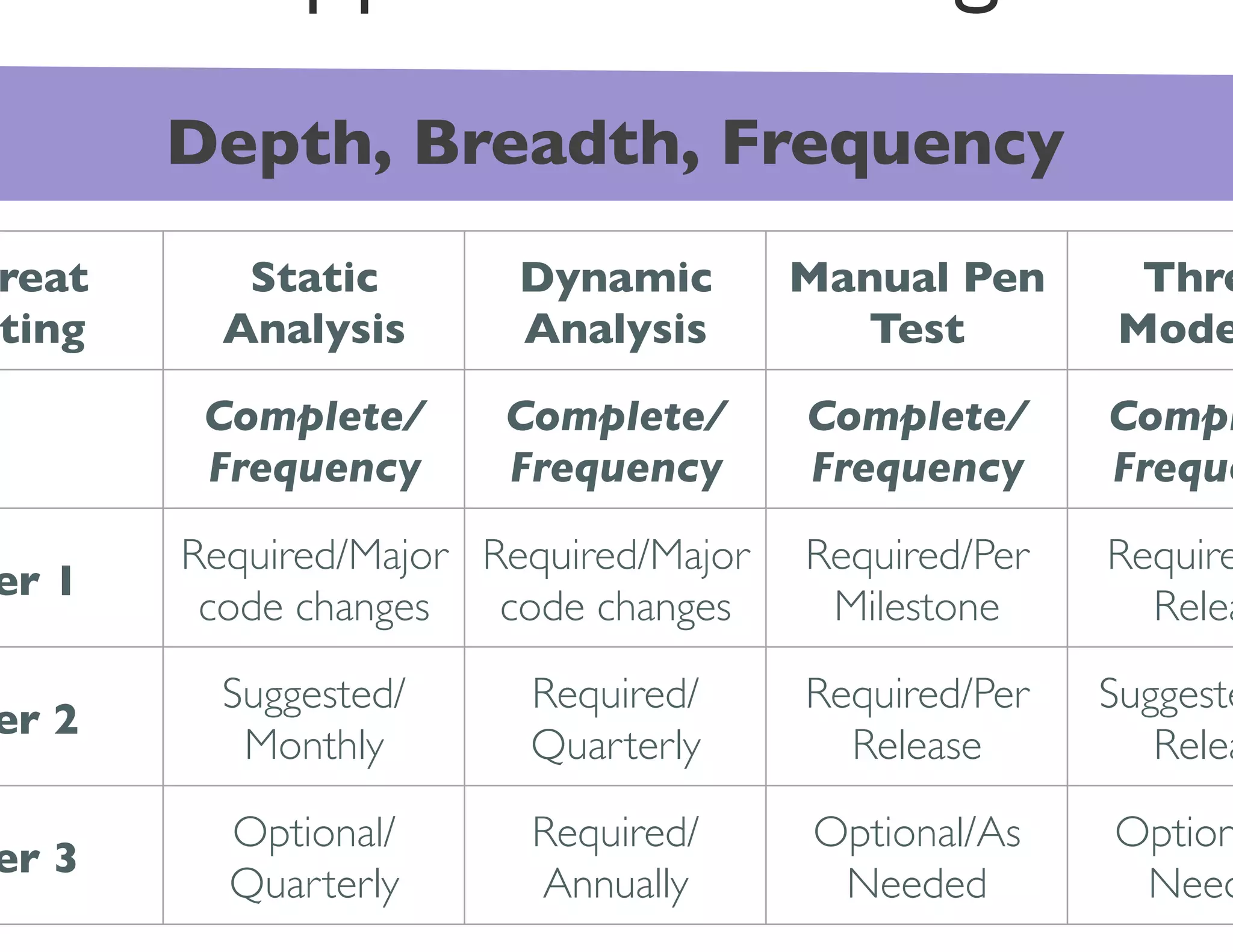
The document discusses strategies for managing software security risk and streamlining application security policy for organizations, emphasizing the need for collaboration between security and development teams. It outlines best practices for application security, the importance of compliance with legal and industry standards, and methods for integrating security into the software development lifecycle. Additionally, it addresses the challenges posed by Bring Your Own Device (BYOD) policies and the necessity for continuous education and training to enhance security awareness among employees.