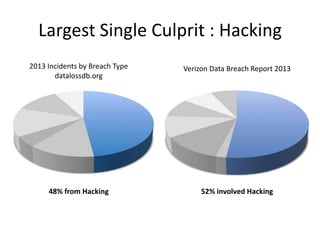
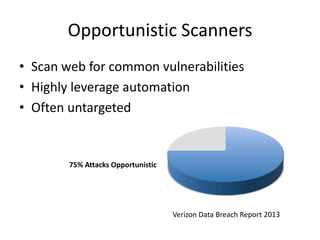
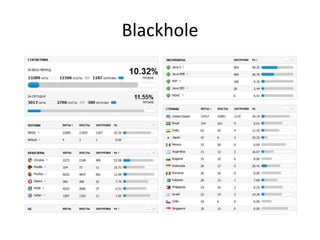
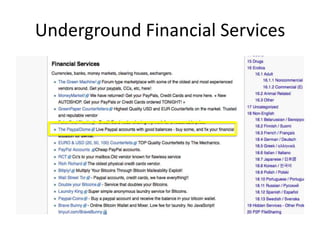
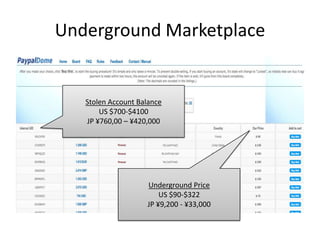
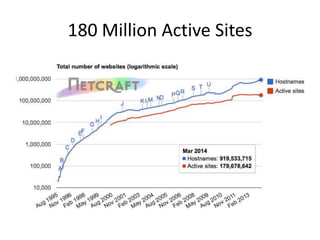
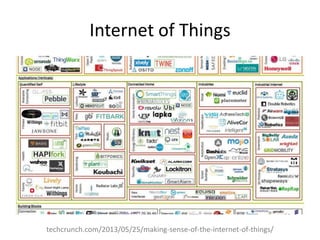
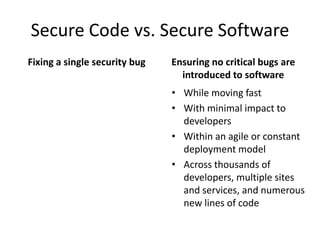
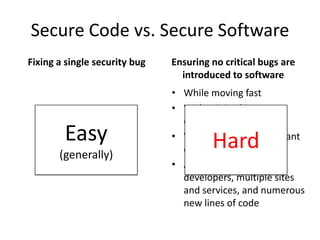
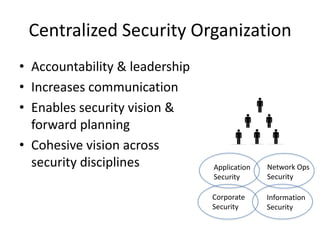
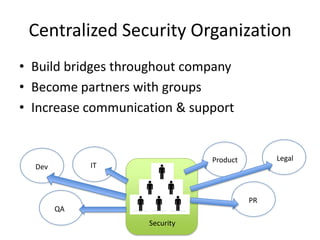
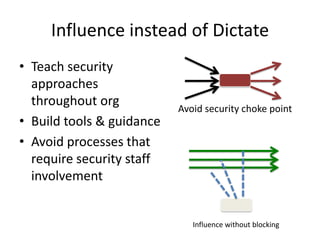
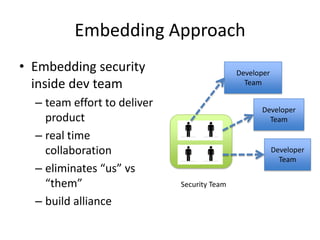
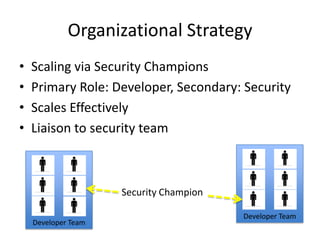
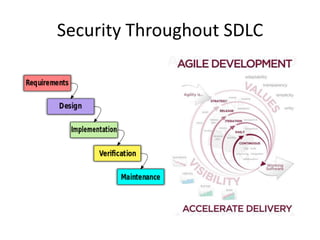
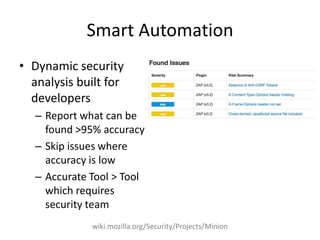
Michael Coates discusses security challenges in today's complex software world. Cybercrime costs over $100 billion annually. Most data breaches are caused by hacking rather than accidents. The security landscape is evolving with new technologies like cloud computing and the internet of things. Traditional security approaches like standards and hiring more people do not scale well. Instead, security needs to be integrated throughout the entire software development lifecycle and automated where possible to effectively secure systems at the speed and scale of modern development.