This document discusses key concepts in mobile computing including:
- People and devices can be mobile between different locations, networks, communication devices, and applications.
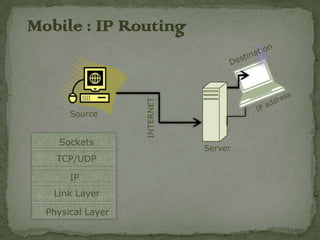
- Research issues in mobile computing include wireless communications challenges like bandwidth limitations and quality of connectivity, as well as mobility challenges like location transparency and dependency.
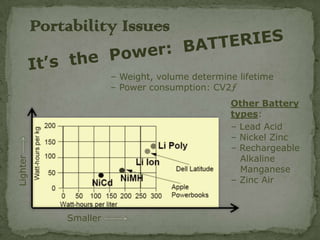
- Mobile devices can be display-only, laptop computers, or personal digital assistants, each with their own power, processing, storage and portability tradeoffs.
- Mobility introduces challenges for addressing, location-dependent services, and portability due to limitations of power, storage, user interfaces and local processing for mobile devices.