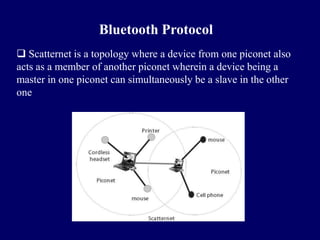
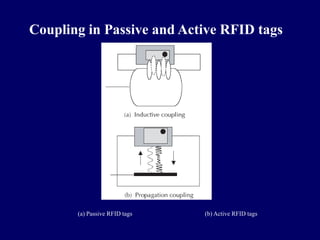
This document discusses emerging mobile computing technologies including Bluetooth, RFID, WiMAX, and mobile IP. It provides details on Bluetooth protocols and how Bluetooth allows wireless connections between various devices. It also describes RFID technologies including active and passive RFID tags and how RFID systems work. It outlines the IEEE 802.16 standard for WiMAX and its use for wireless broadband access. Key layers and aspects of the physical layer are summarized.