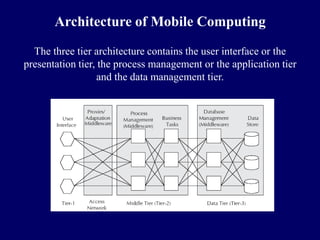
The document provides an overview of mobile computing architecture. It describes a three-tier architecture with a presentation tier (user interface), application tier (process management), and data management tier. It discusses various types of middleware that can be used in the application tier, including message-oriented middleware and transaction processing middleware. It also covers managing context in mobile computing, including user context, device context, network context, and others. The Client Context Manager maintains information about the mobile device, user, location, and environment to provide context awareness.