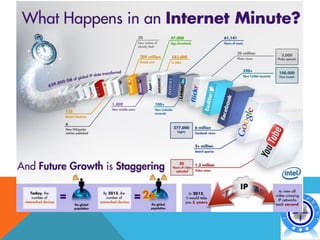
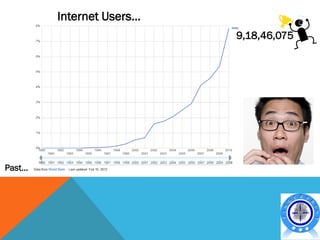
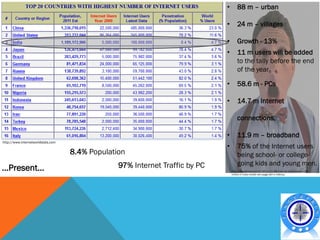
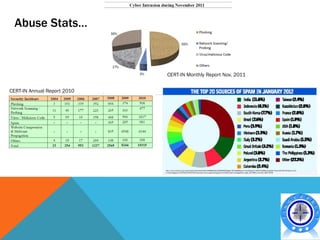
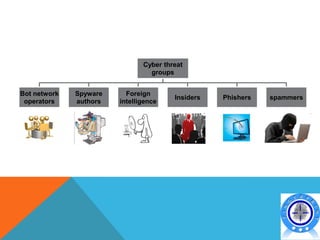
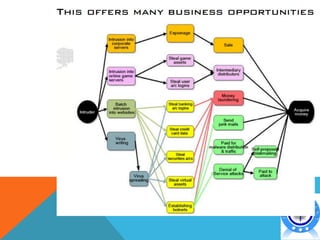
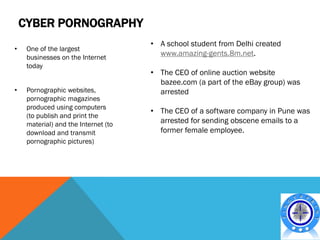
This document discusses various topics related to cyber crime including:
- The evolution of cyber crime and how internet usage has increased opportunities for cyber threats.
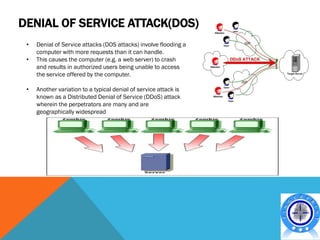
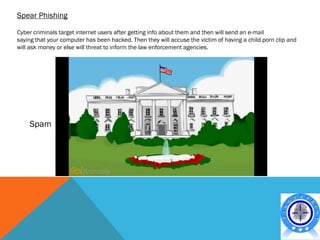
- Different types of cyber crimes such as financial crimes, intellectual property crimes, cyber bullying, and web defacement.
- Common targets of cyber crimes like individuals, businesses, and governments.
- Trends showing India has a significant problem with cyber crimes and ranks high globally in areas like spam generation.
- The document emphasizes that cyber crime prevention is important as internet usage continues to grow rapidly around the world.