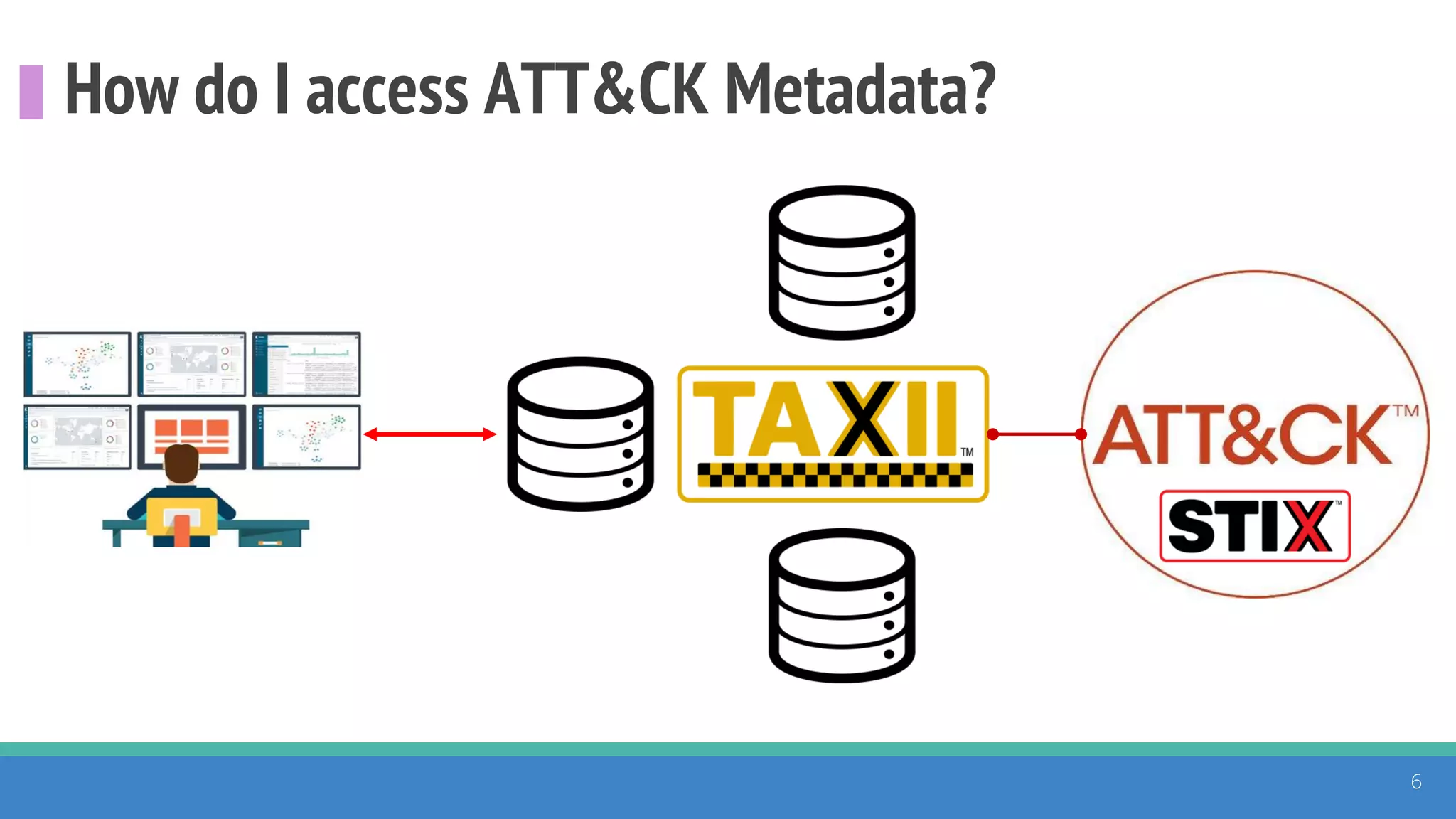
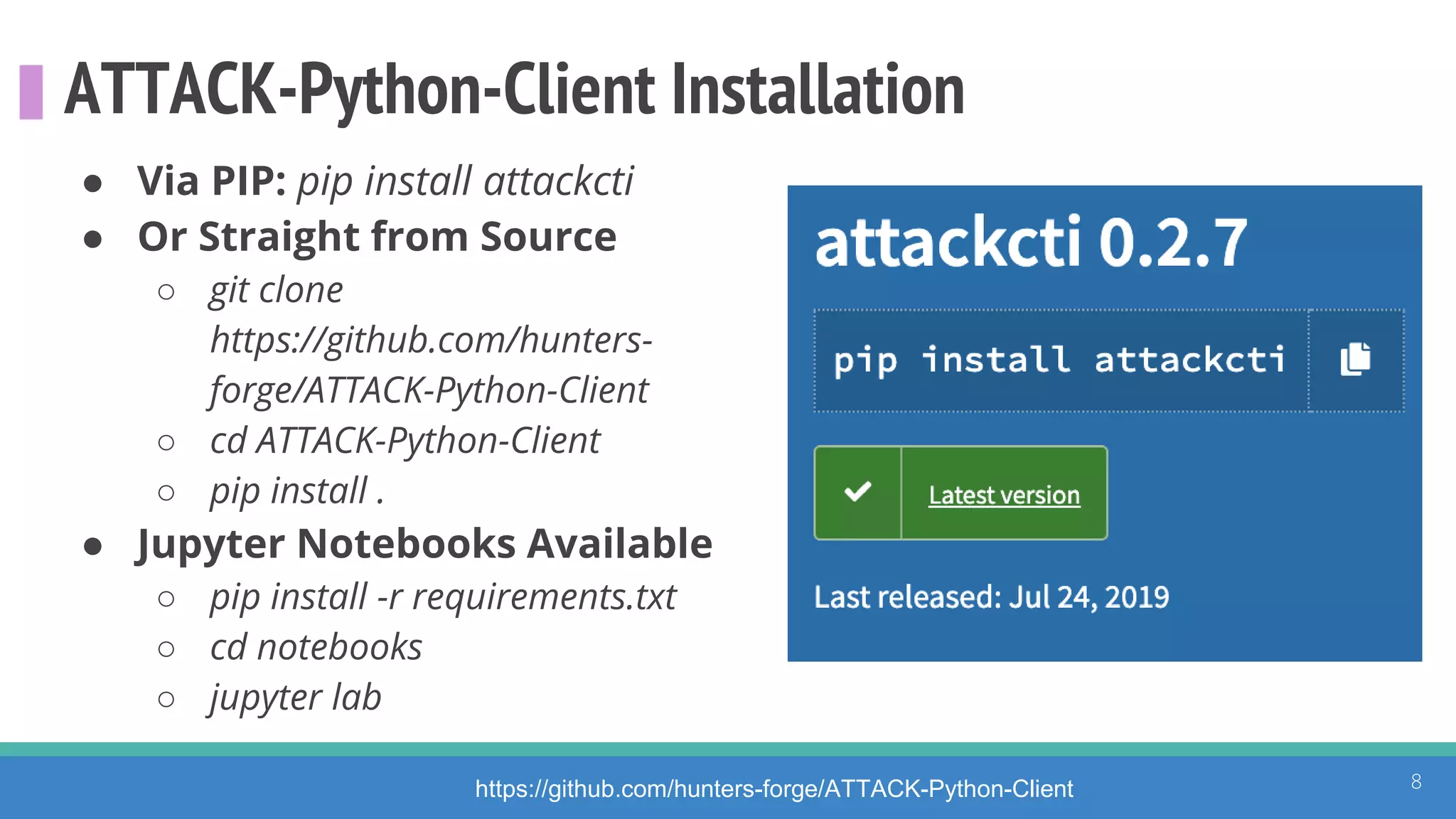
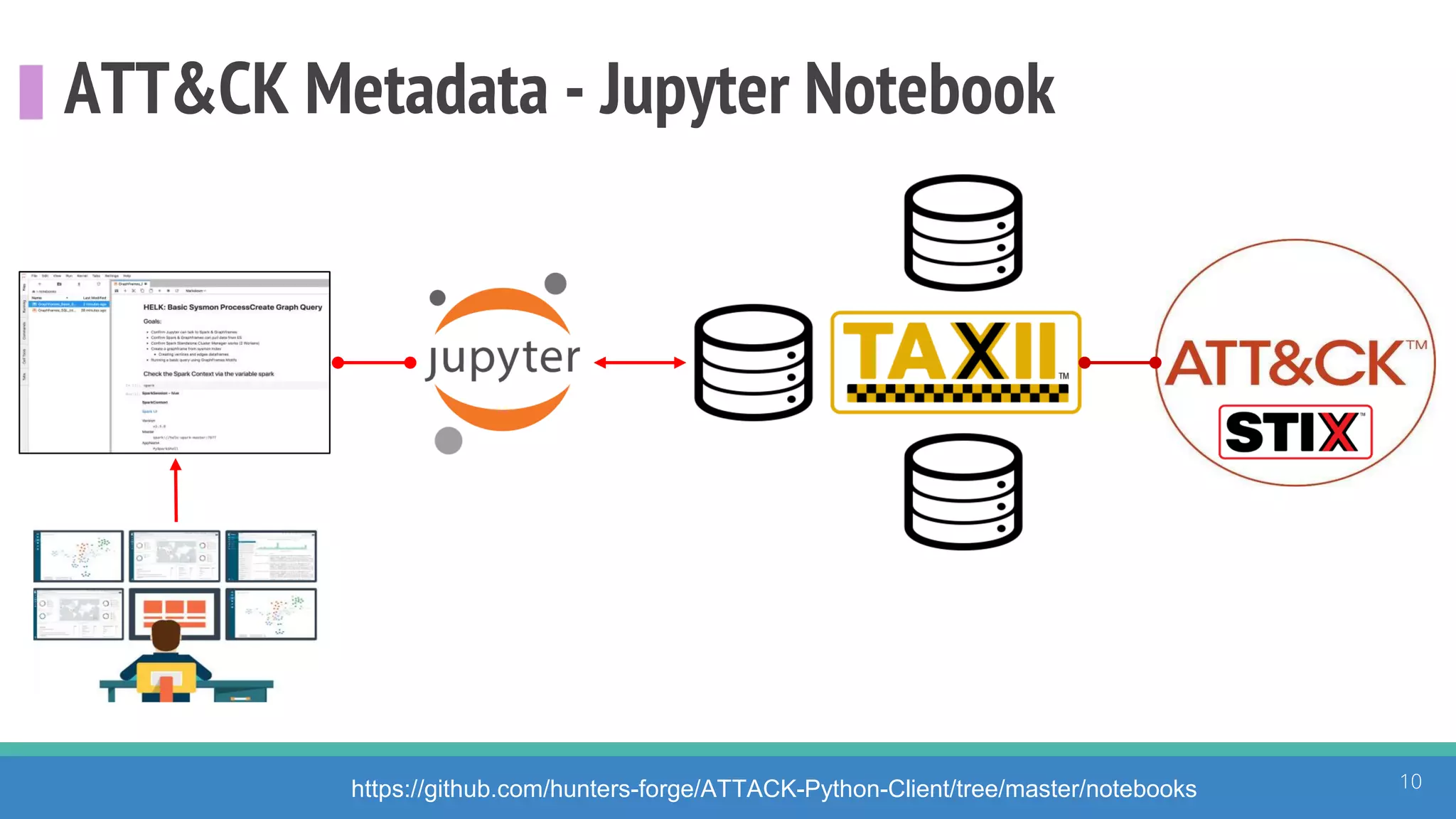
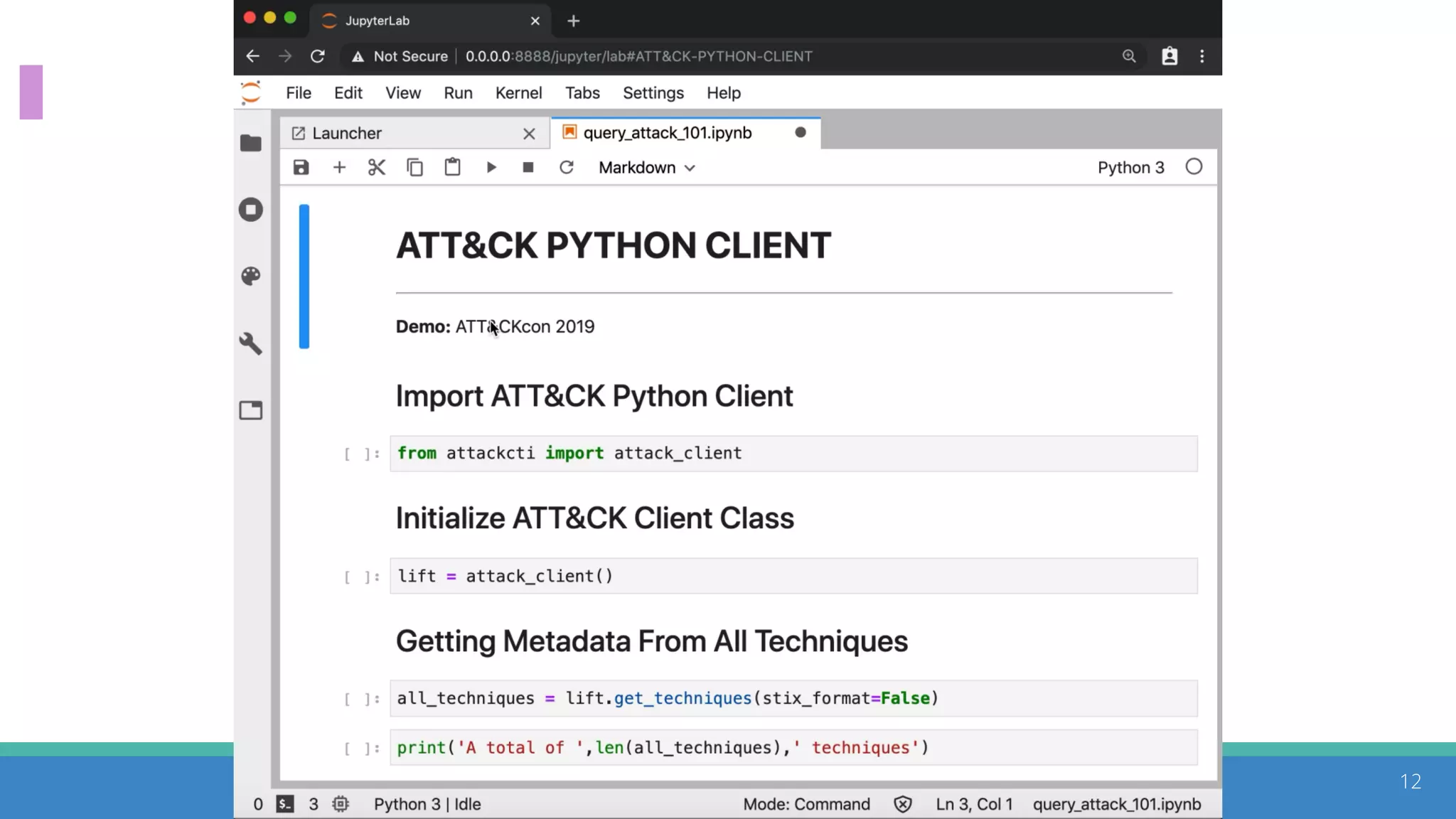
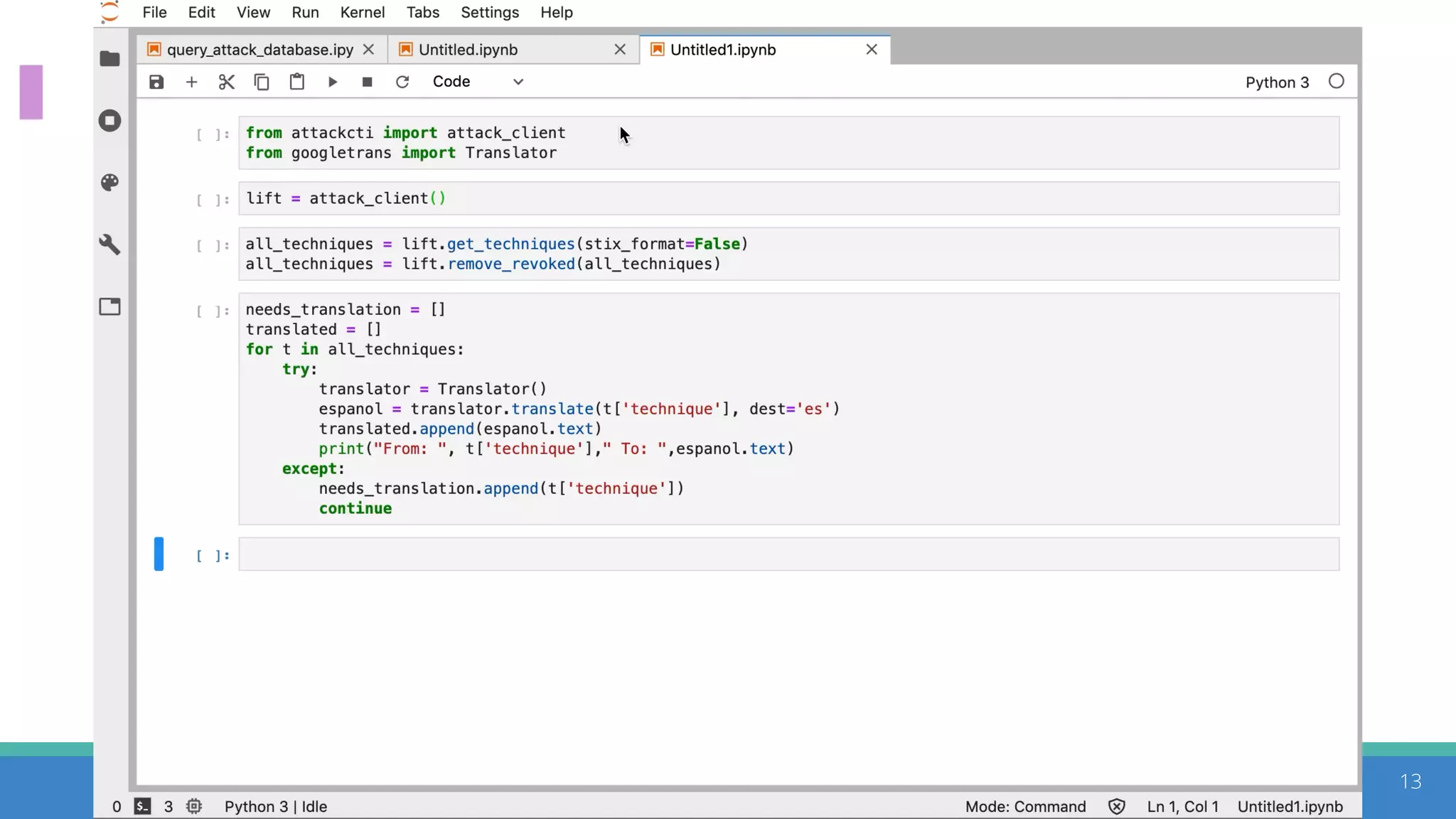
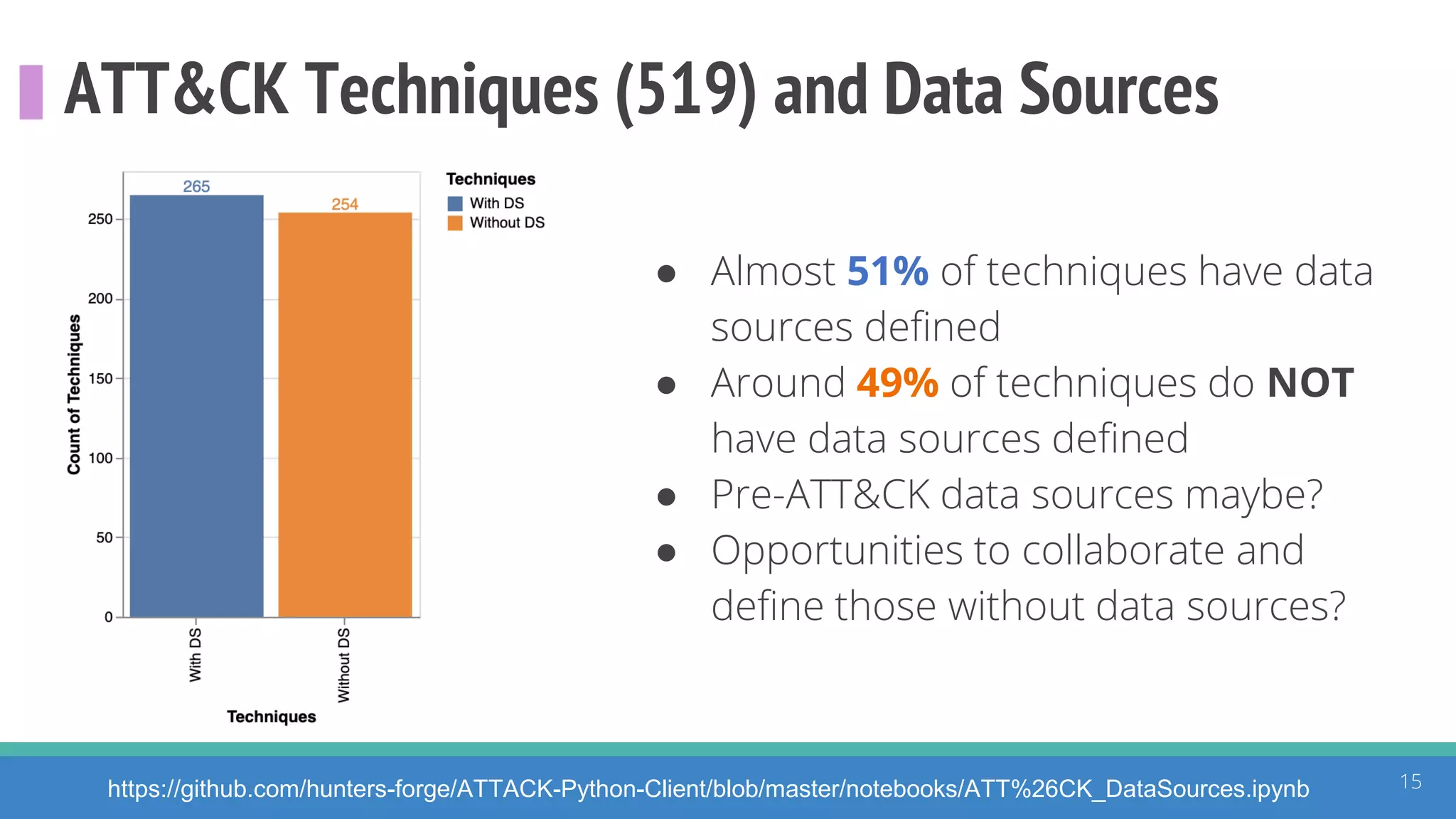
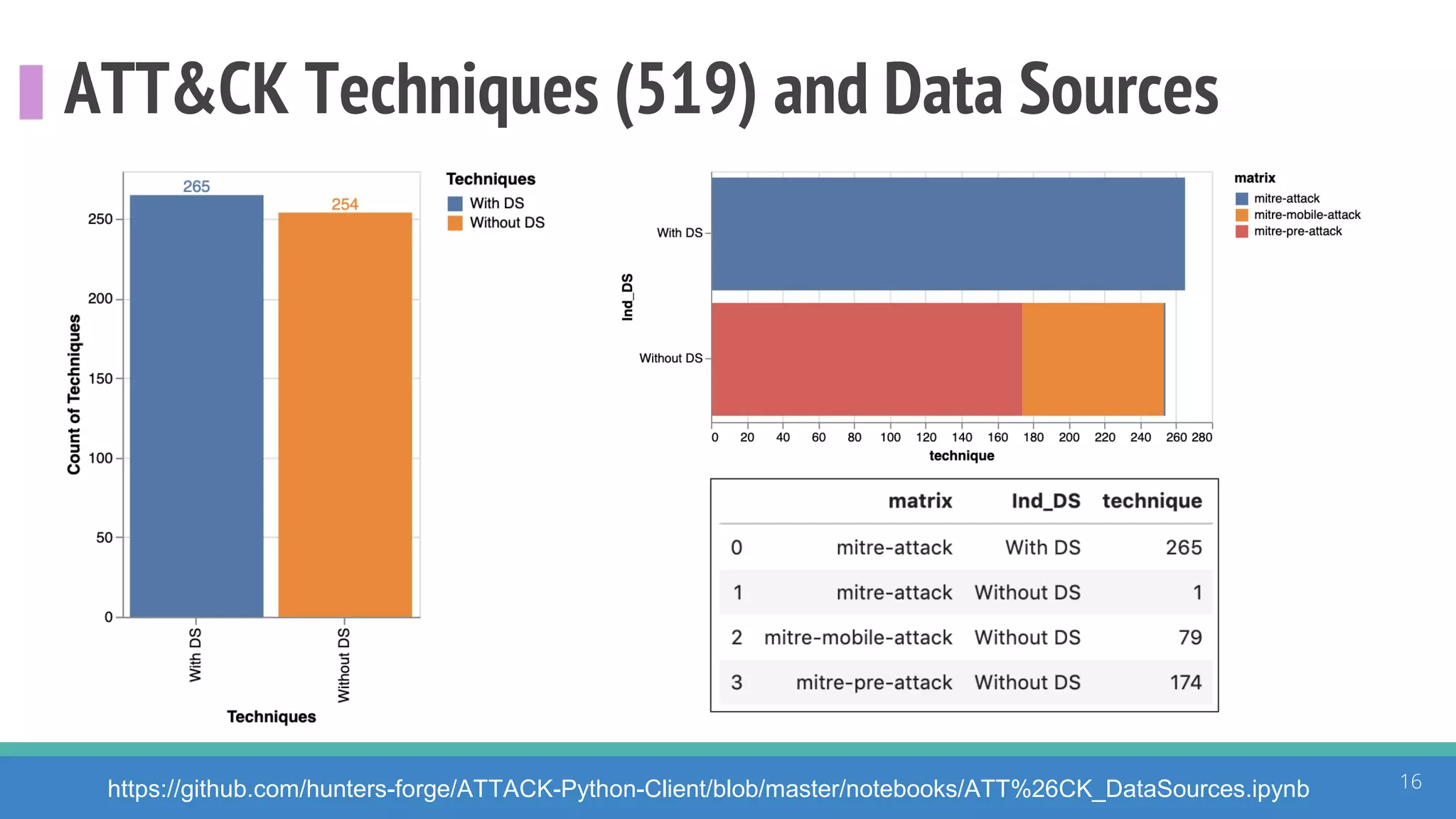
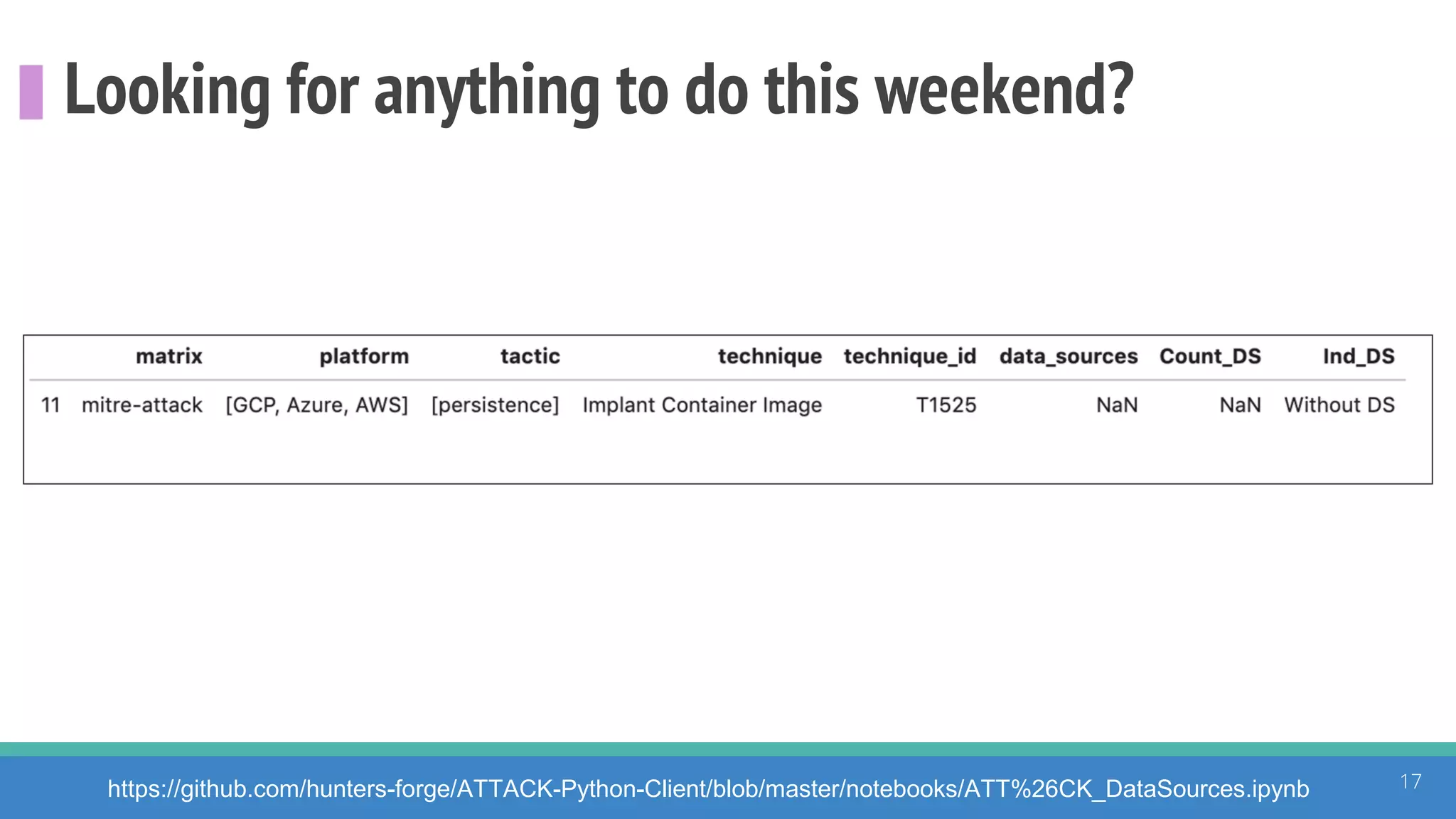
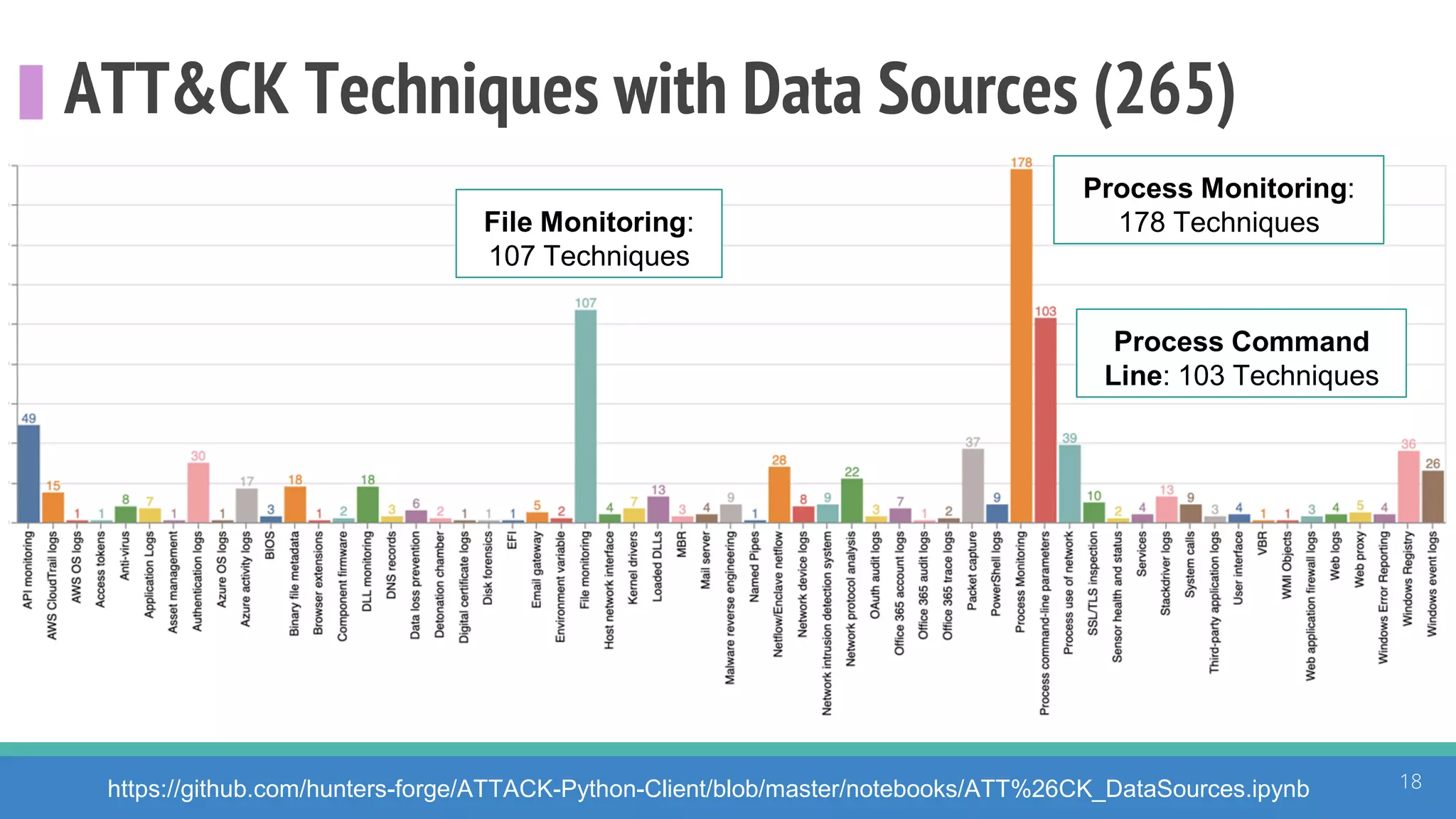
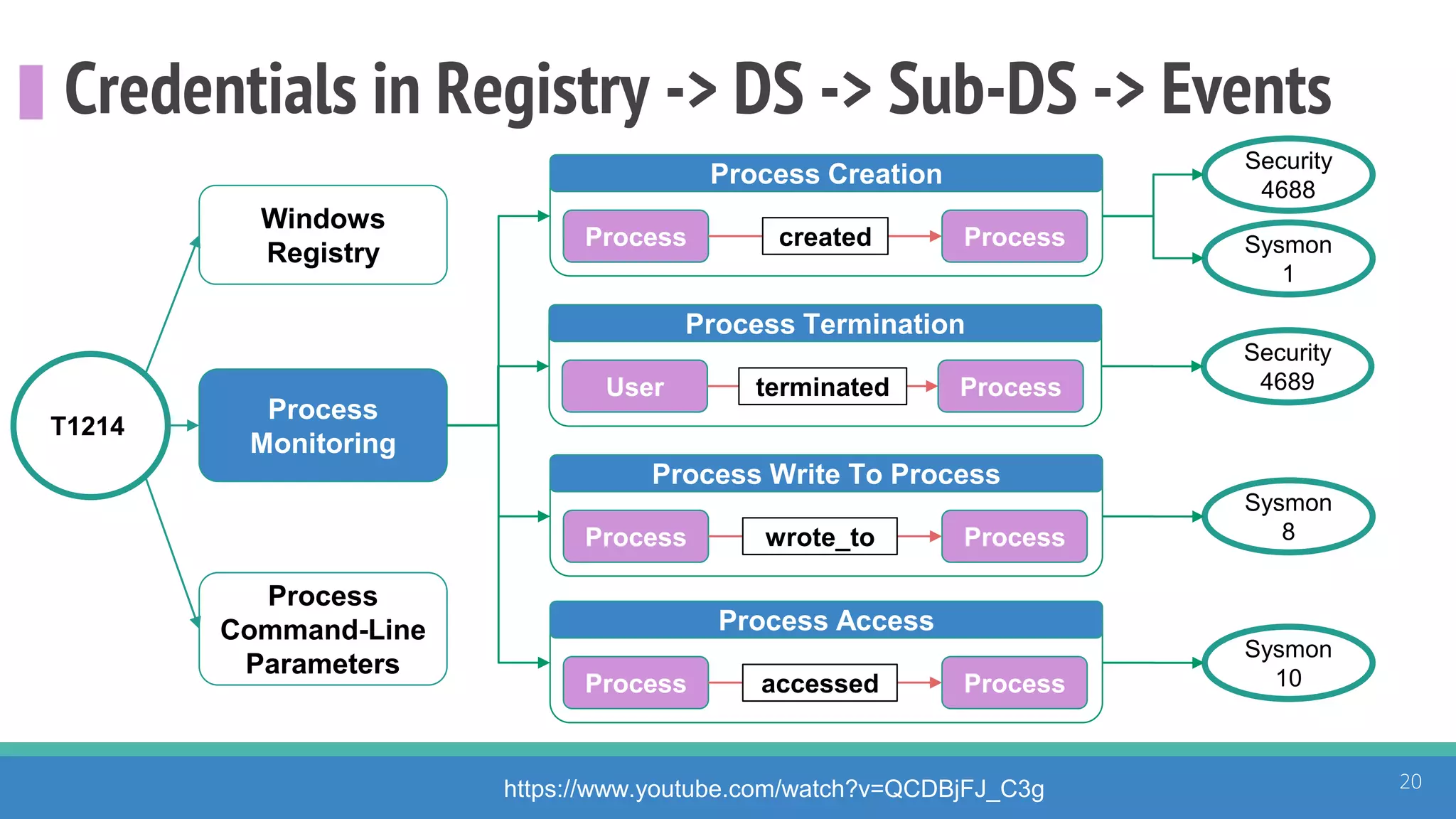
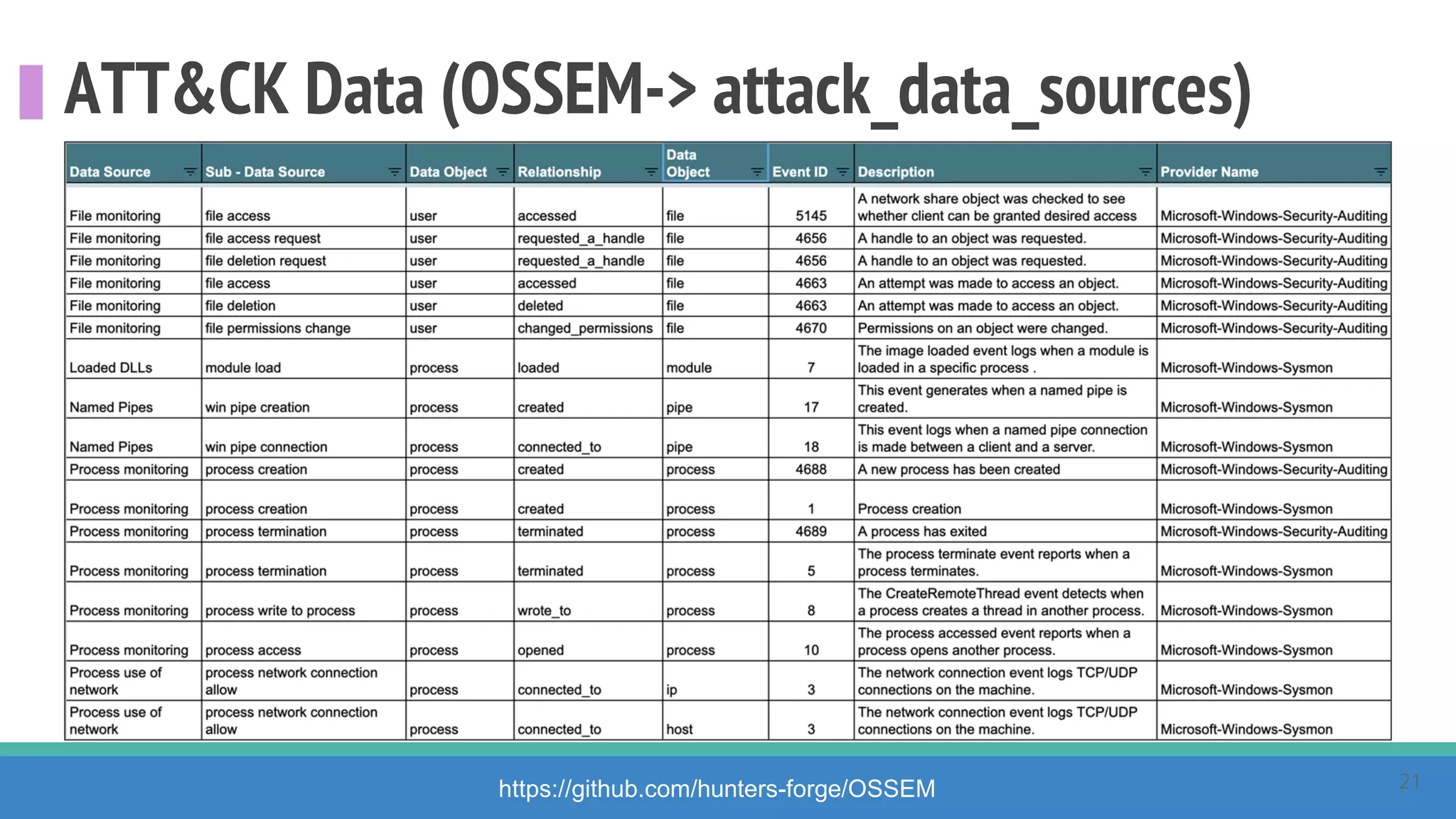
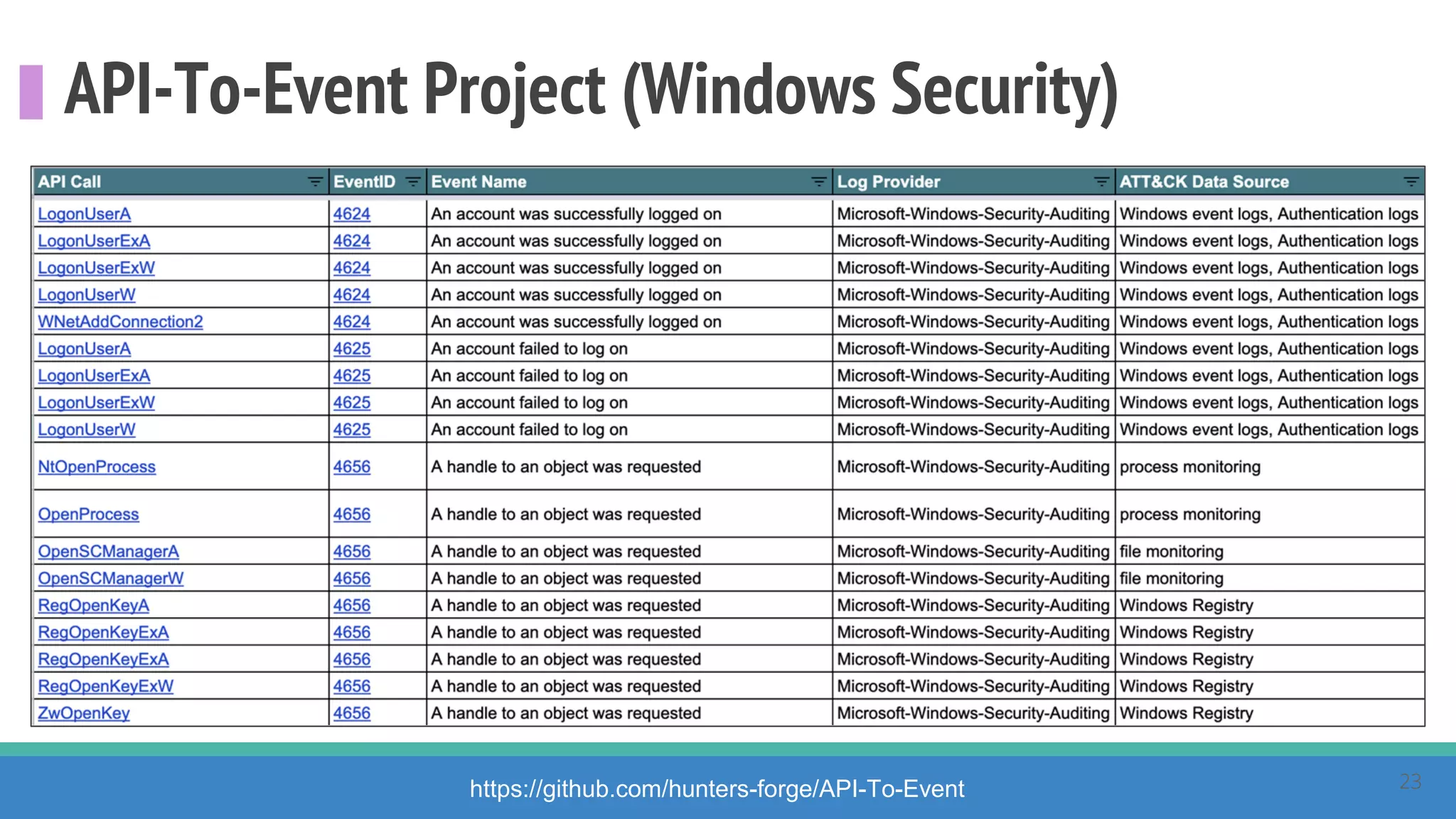
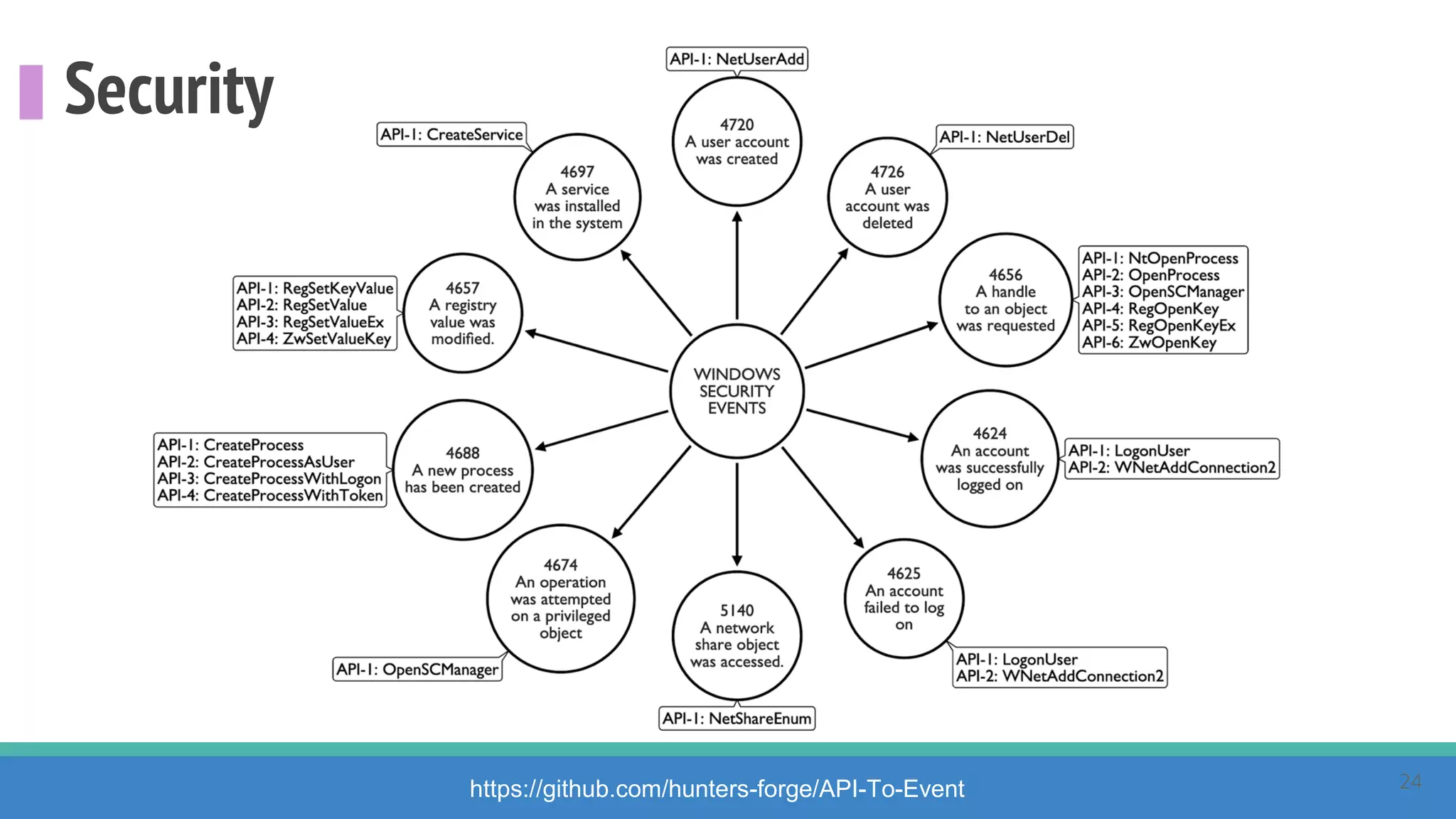
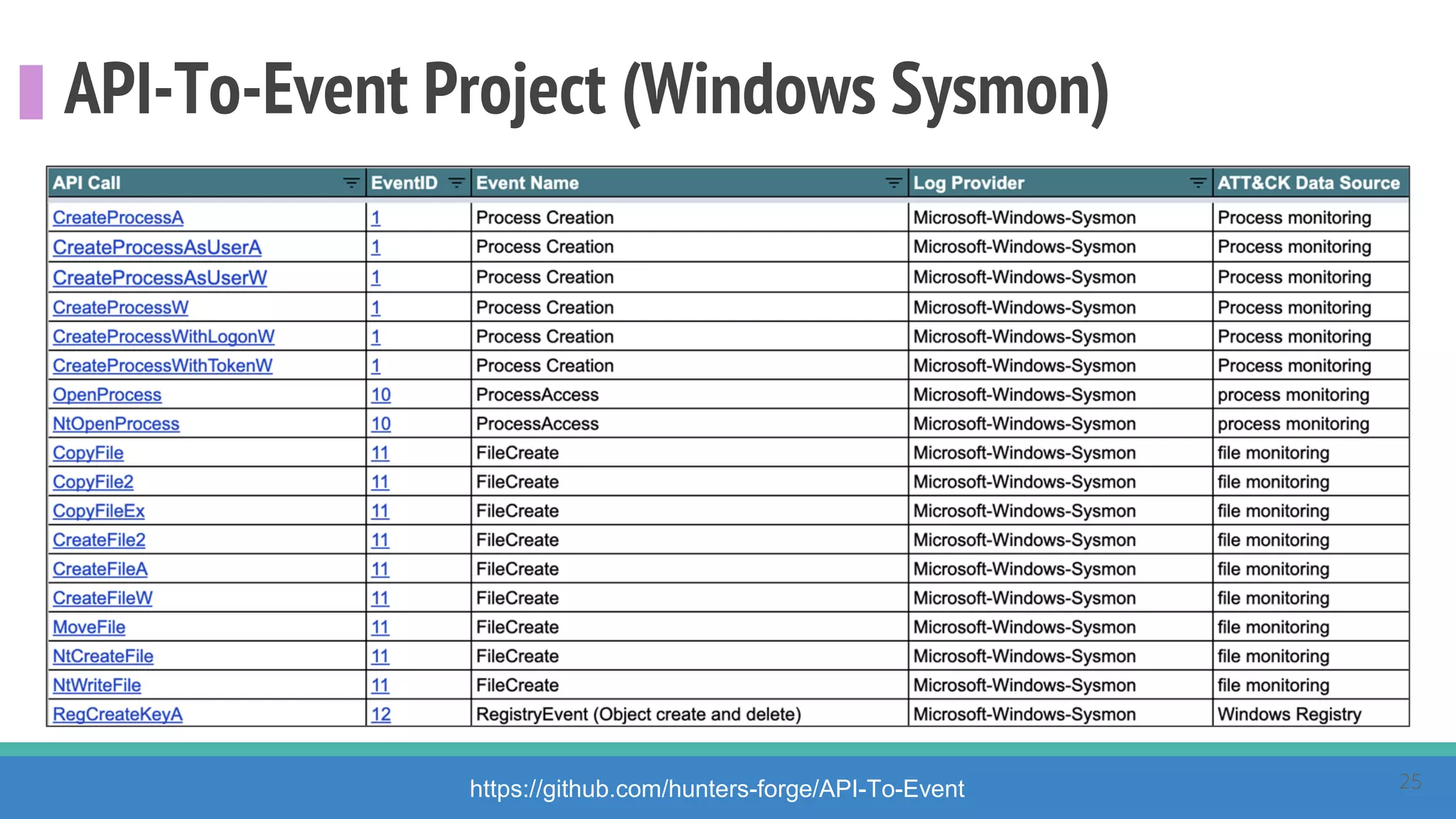
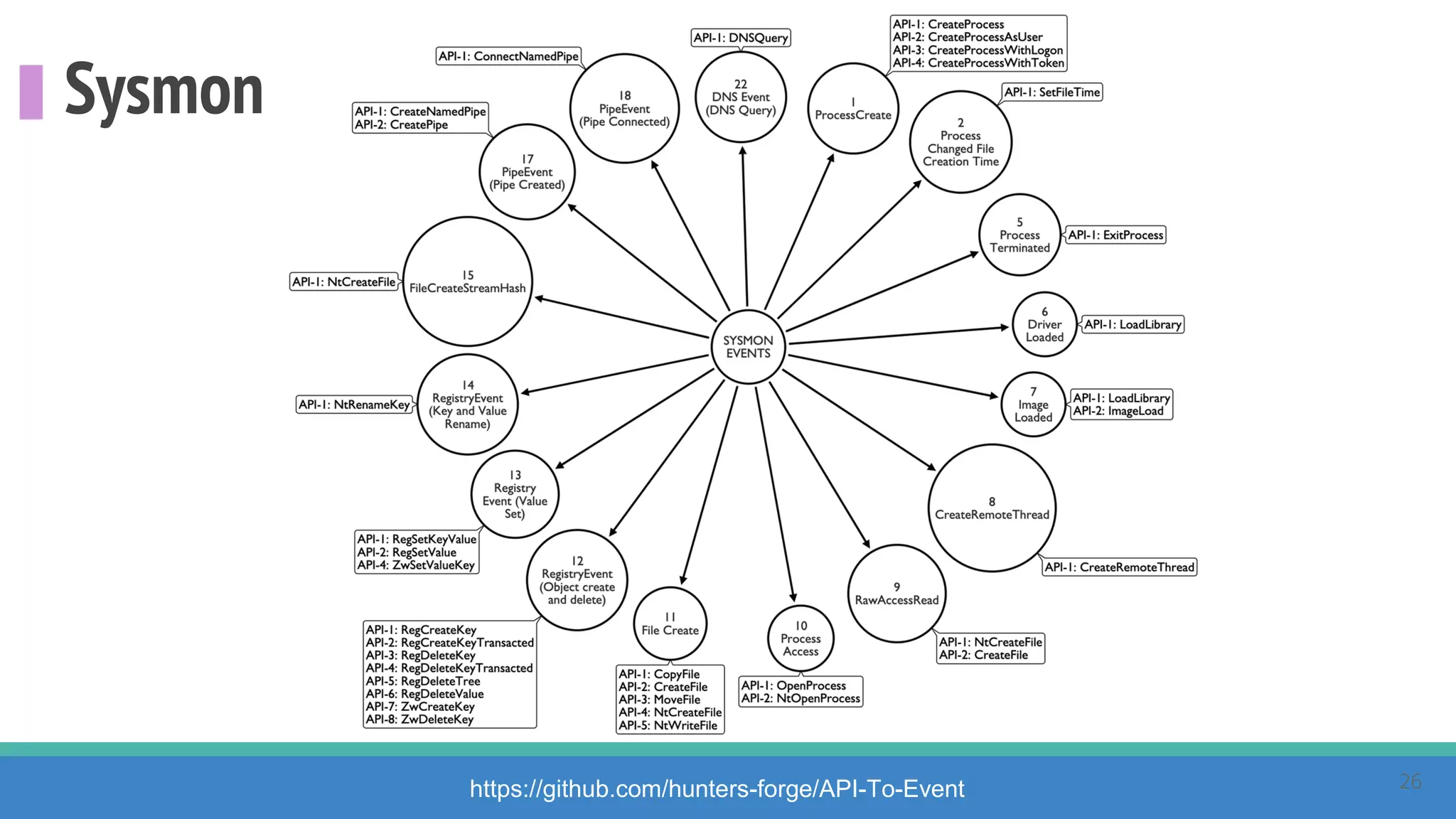
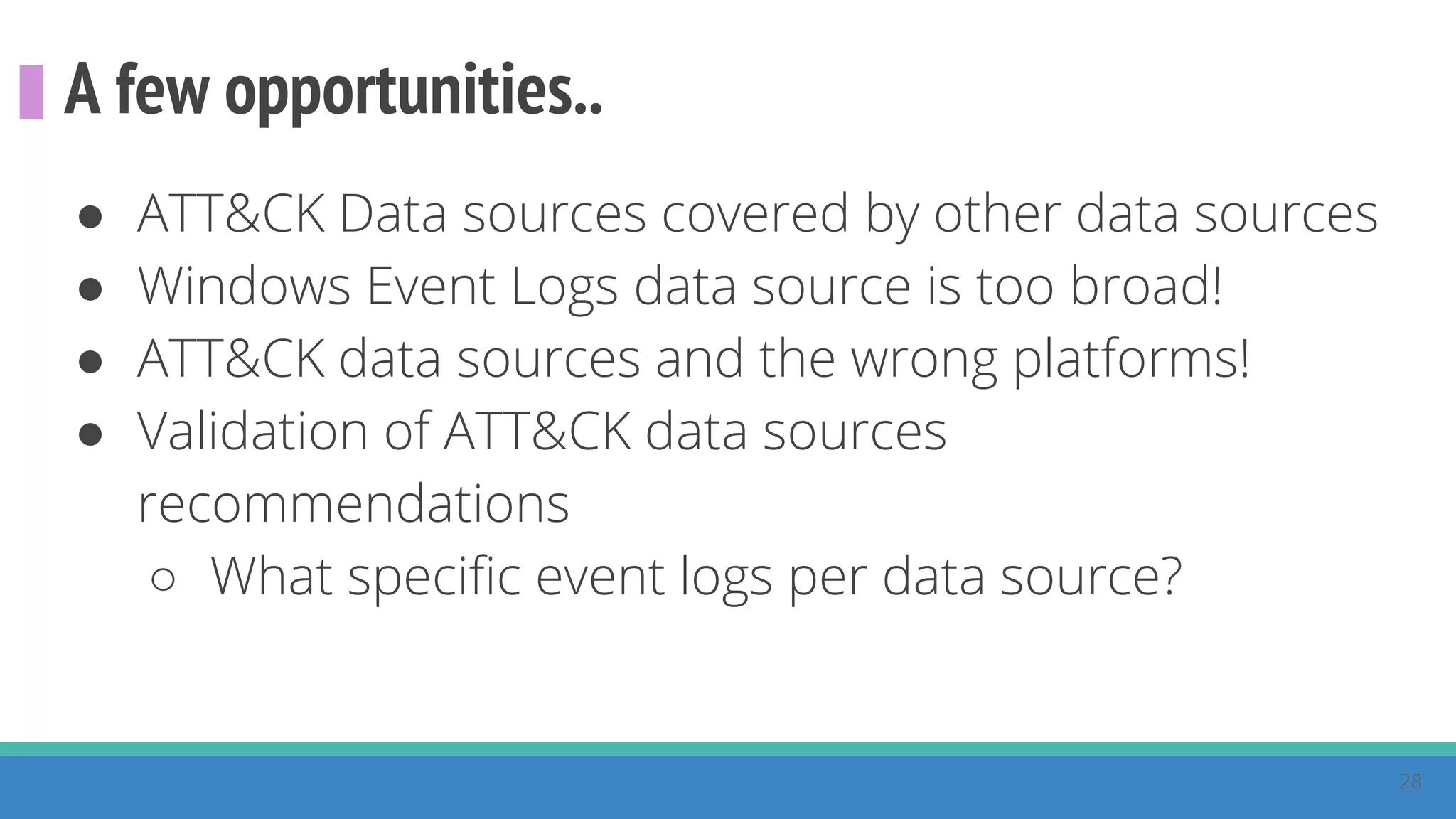
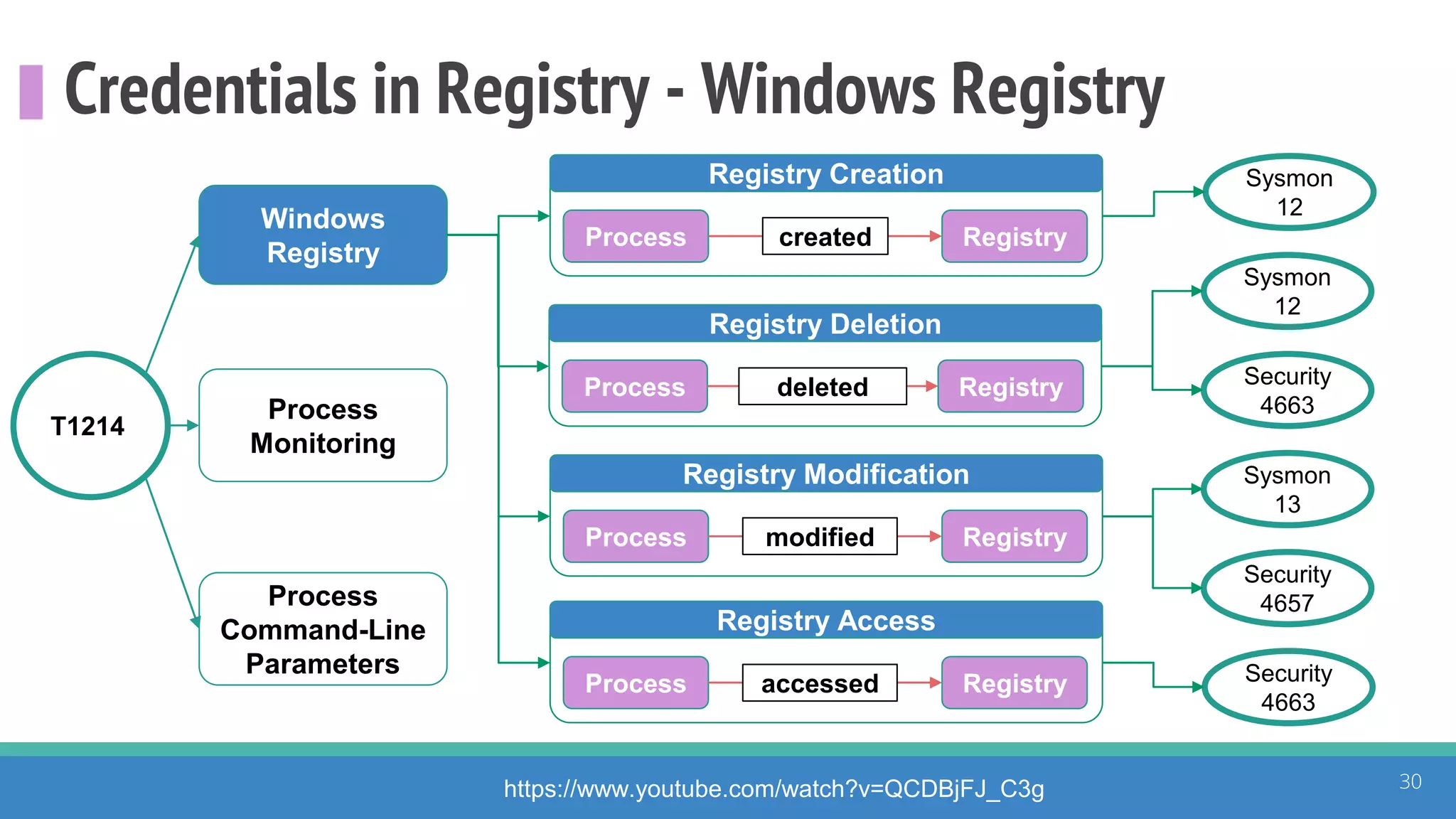
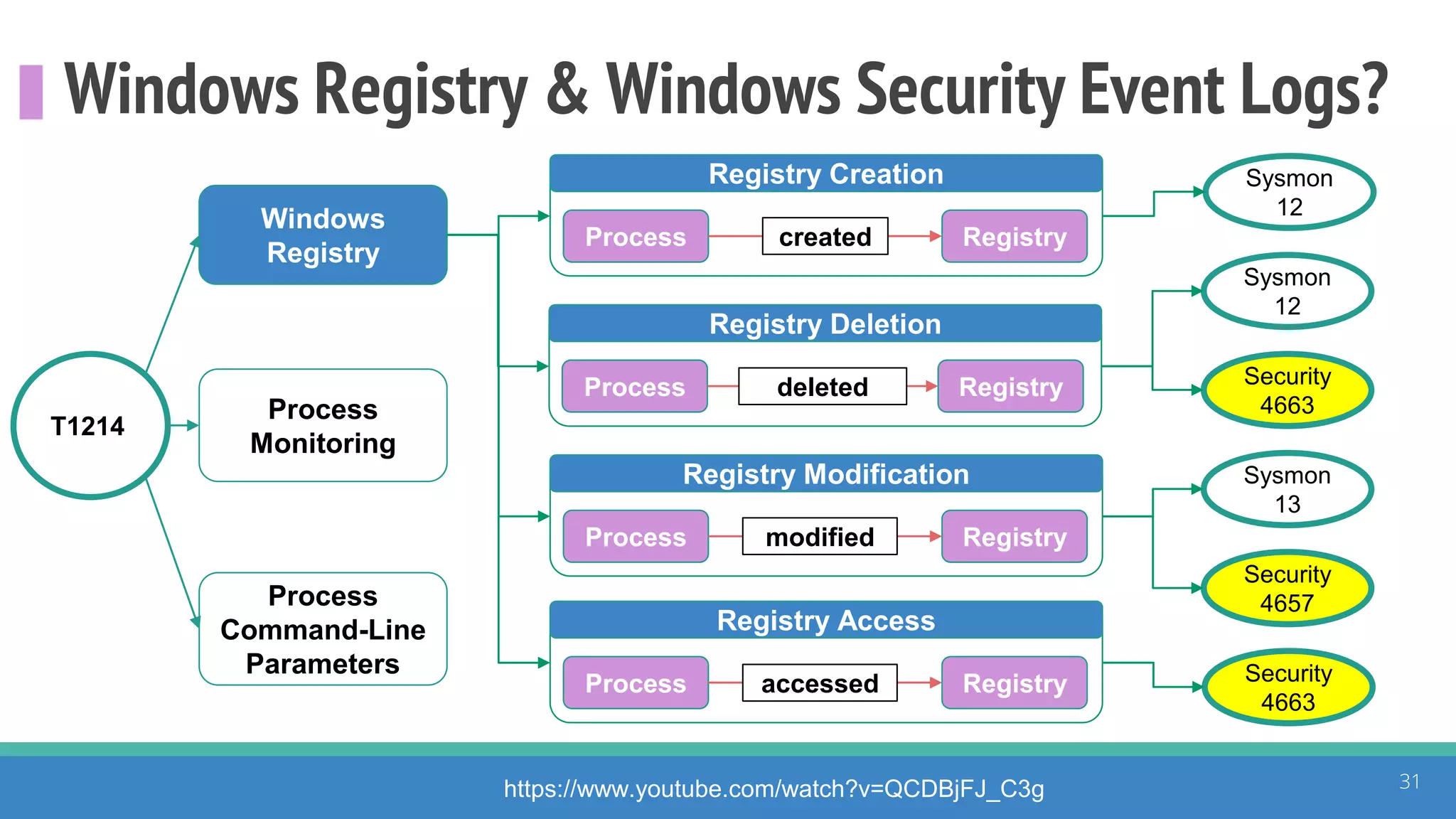
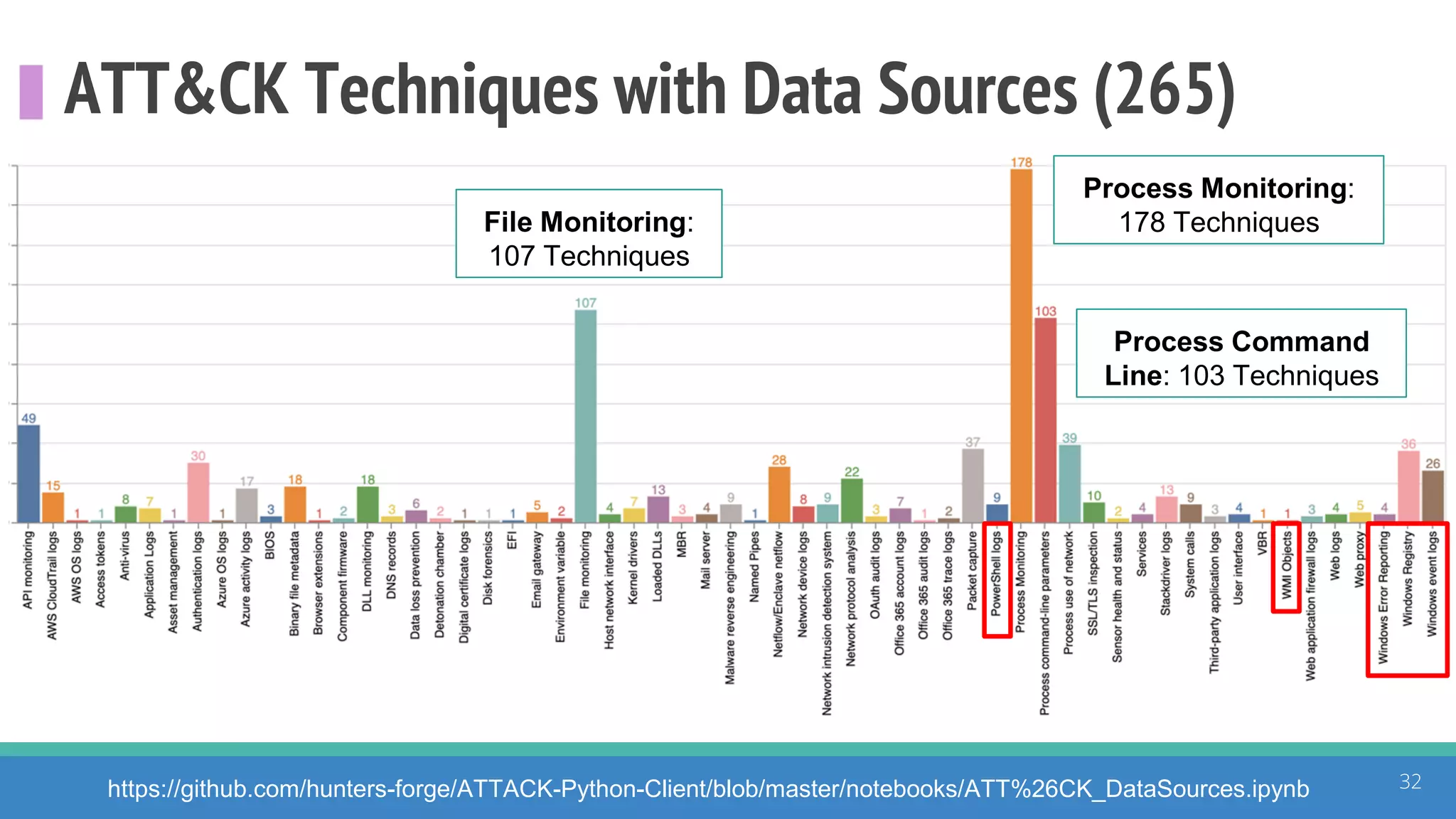
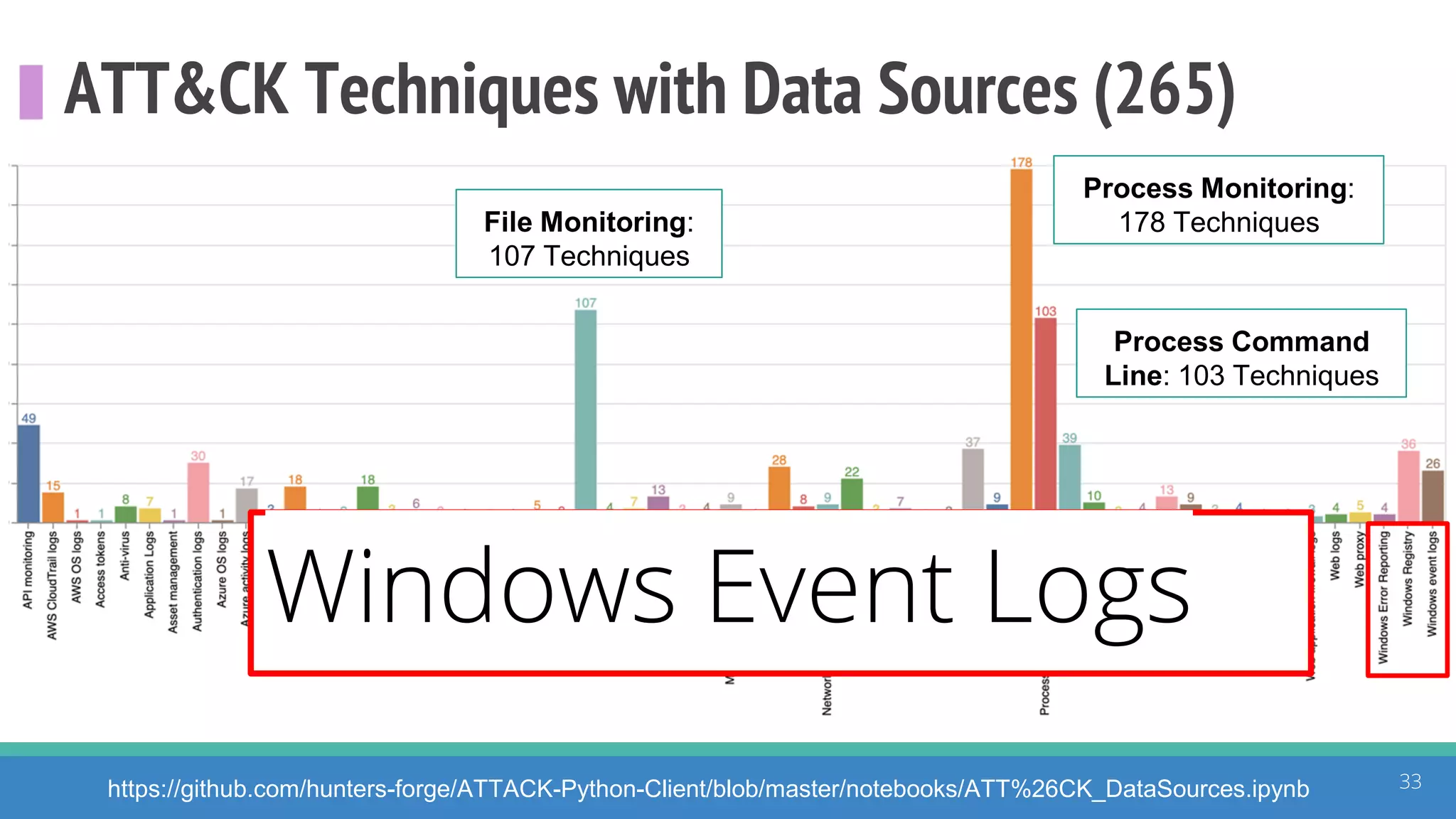
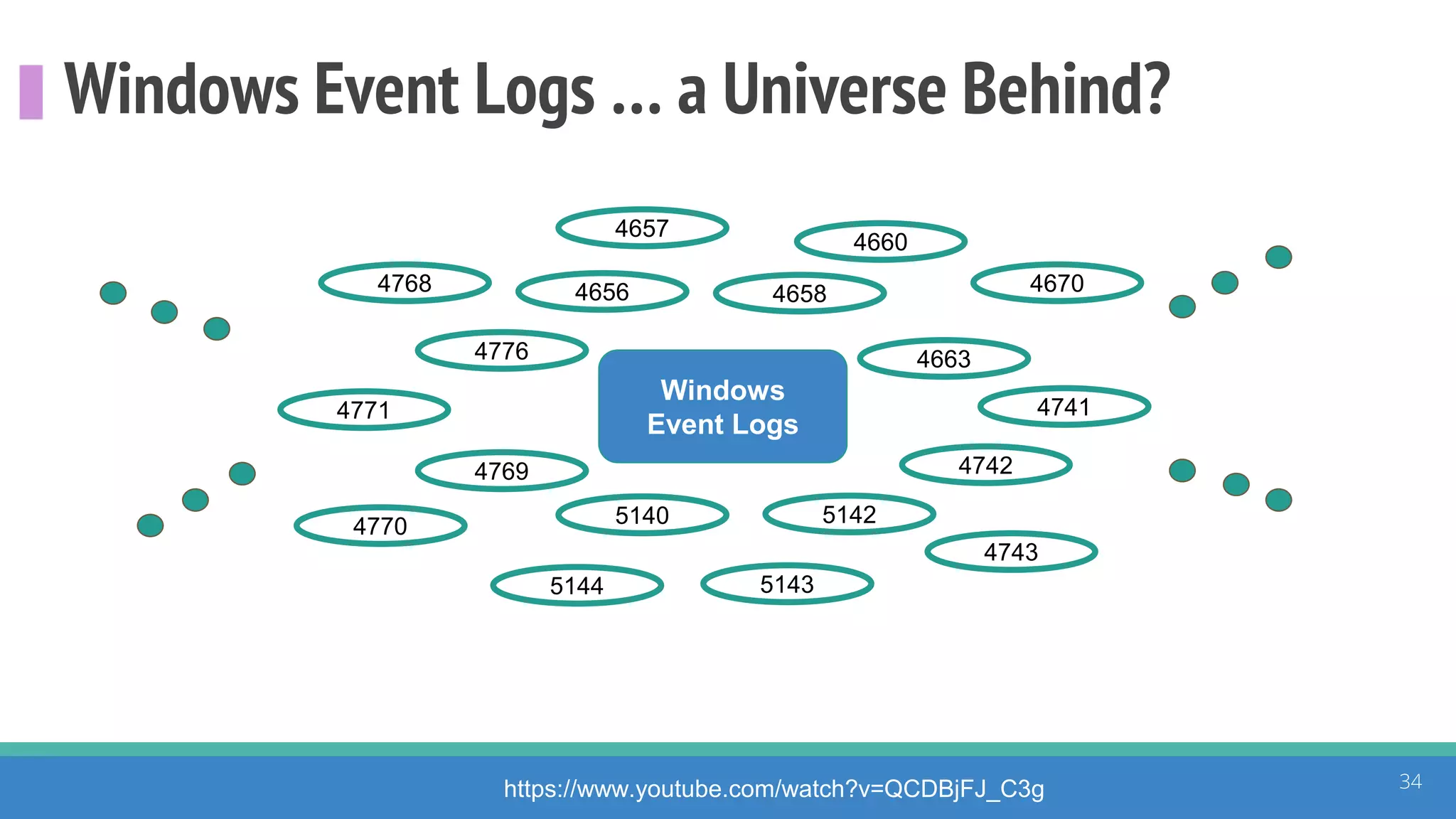
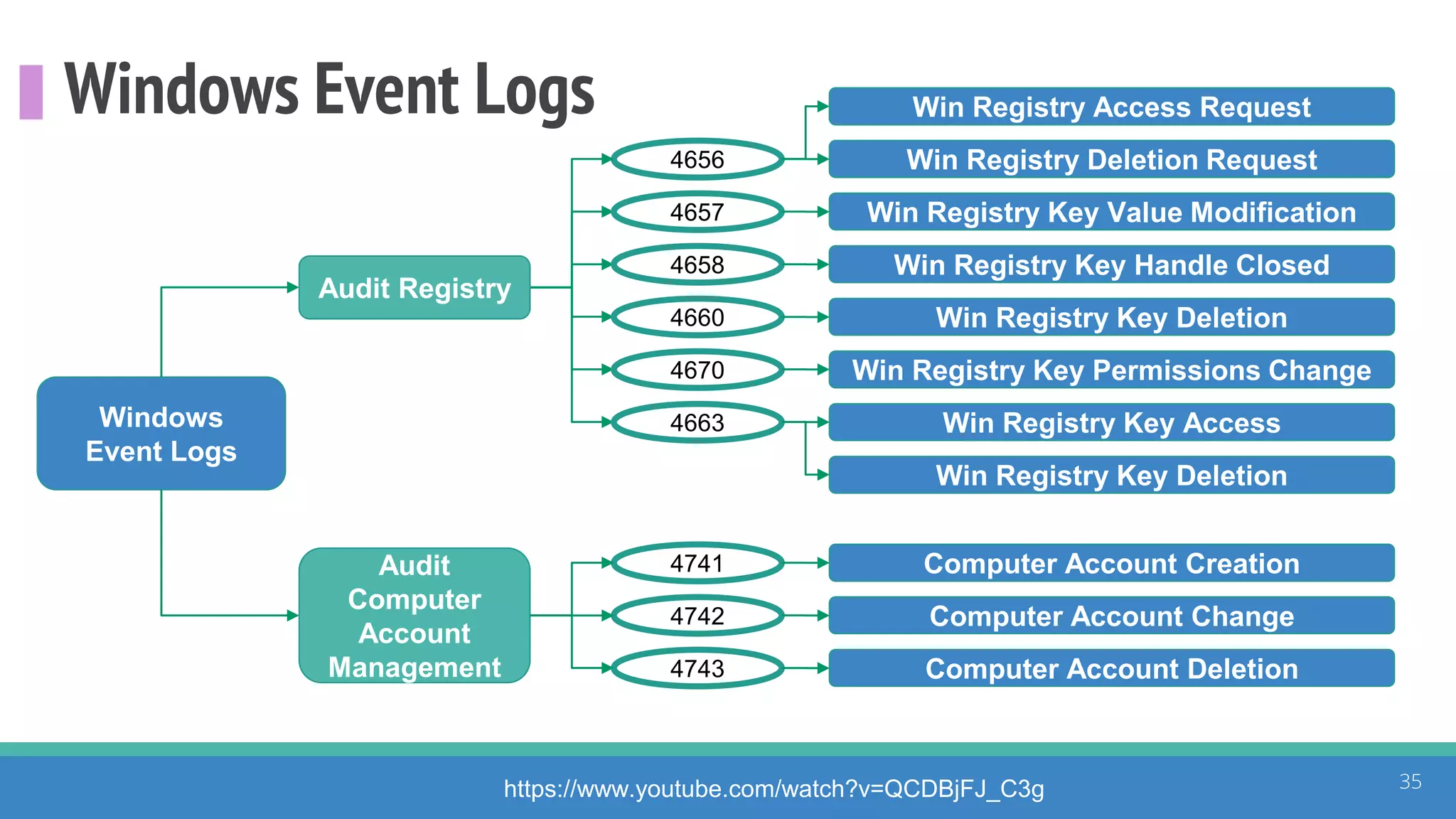
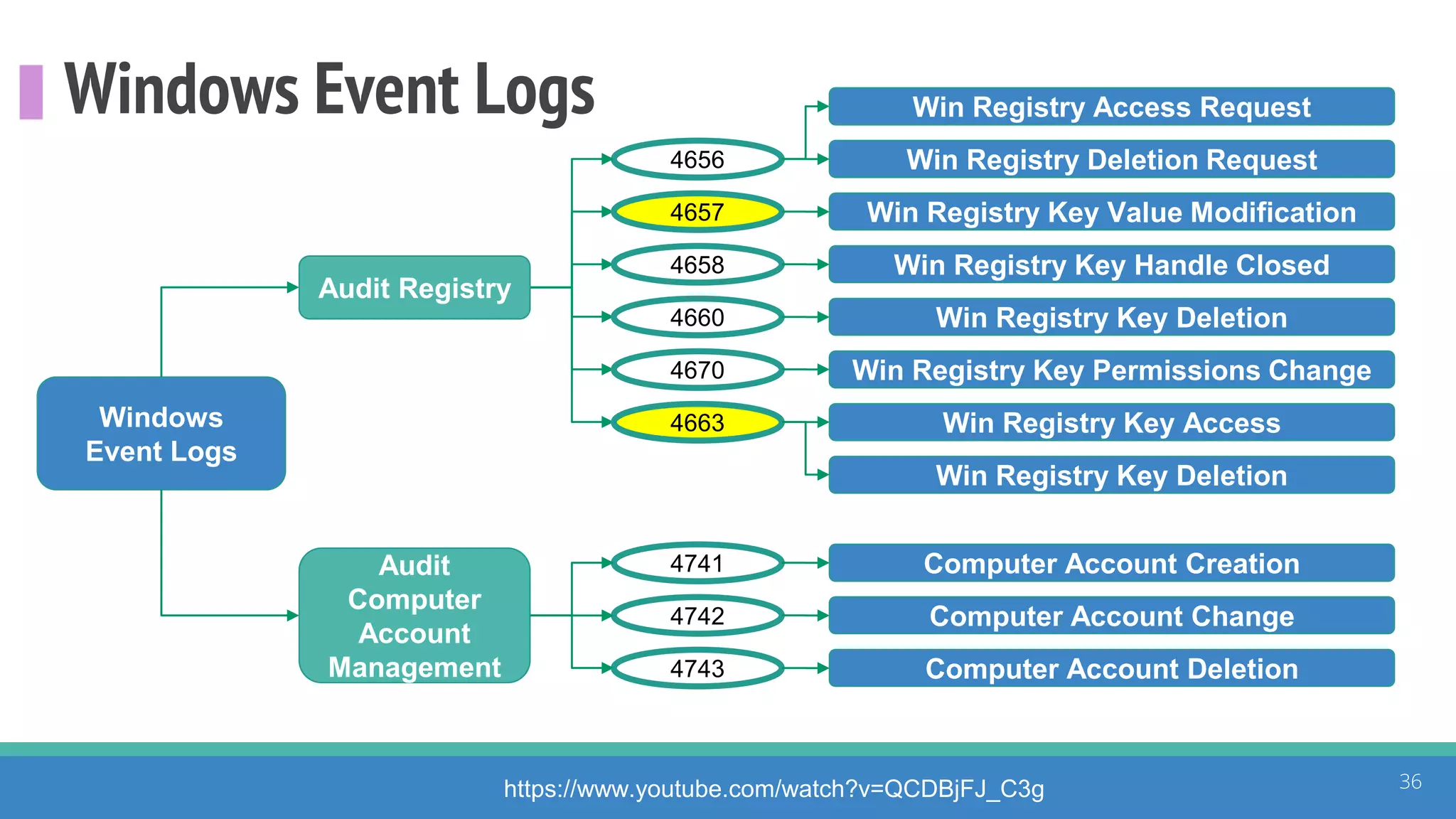
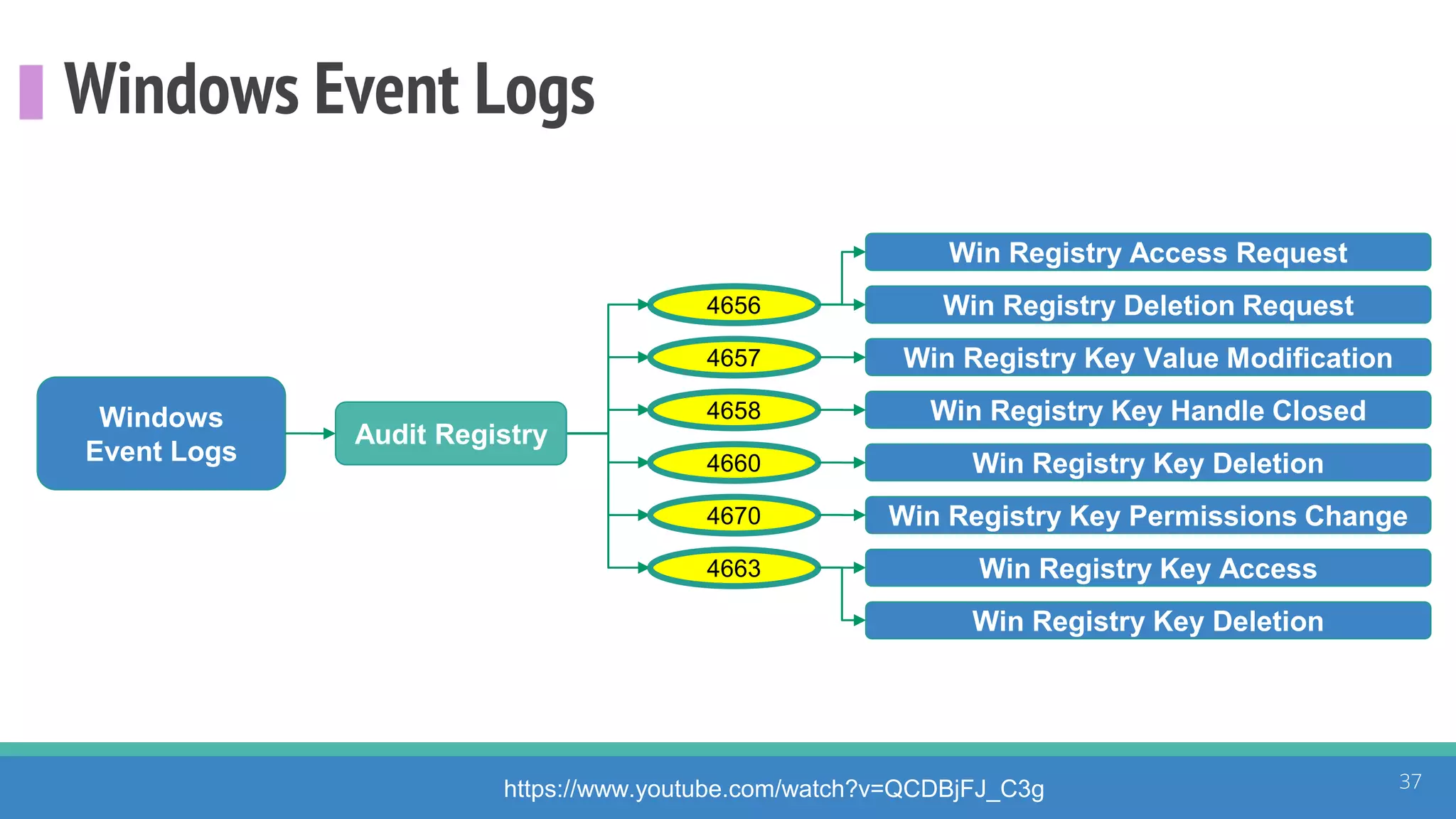
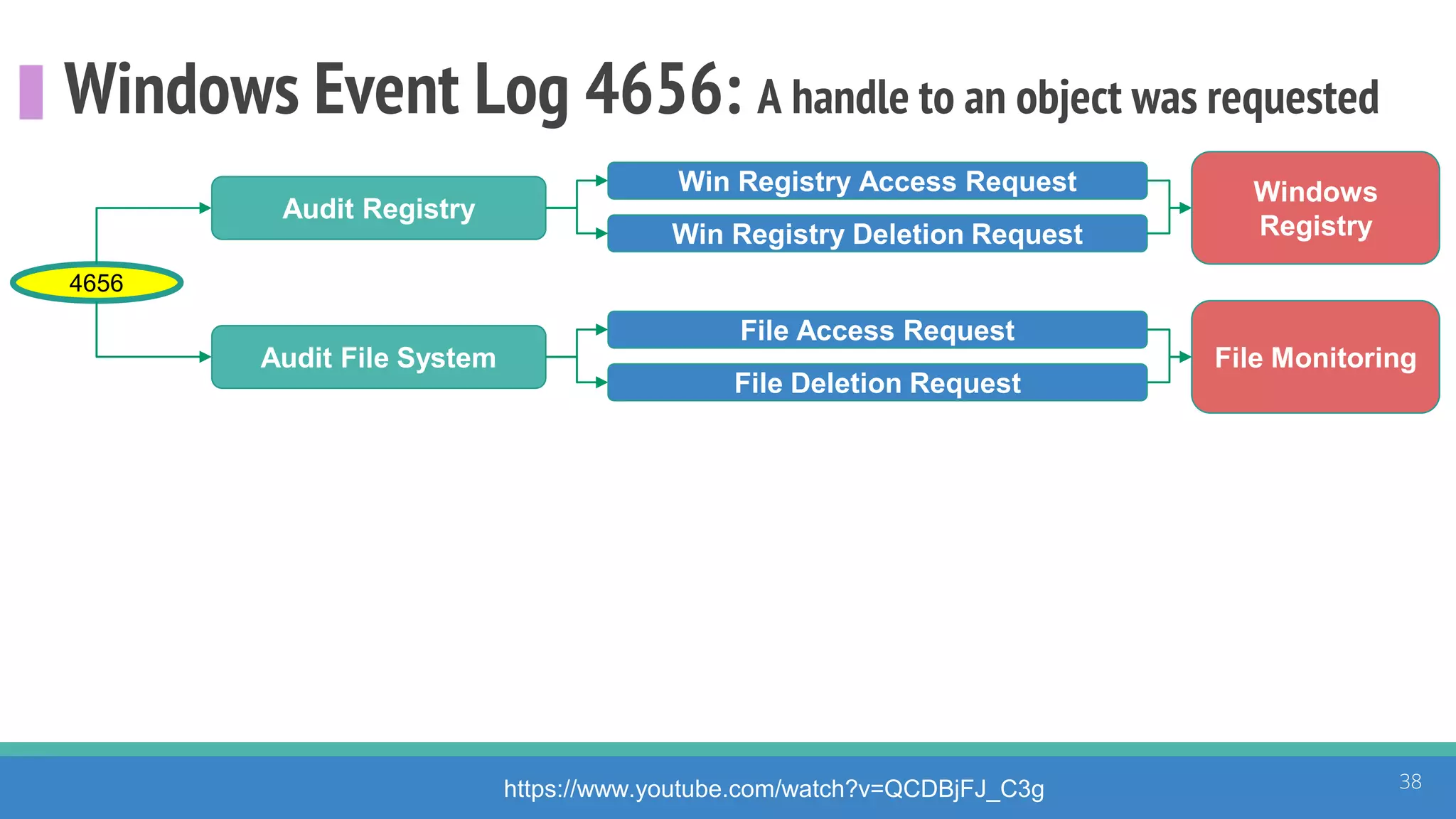
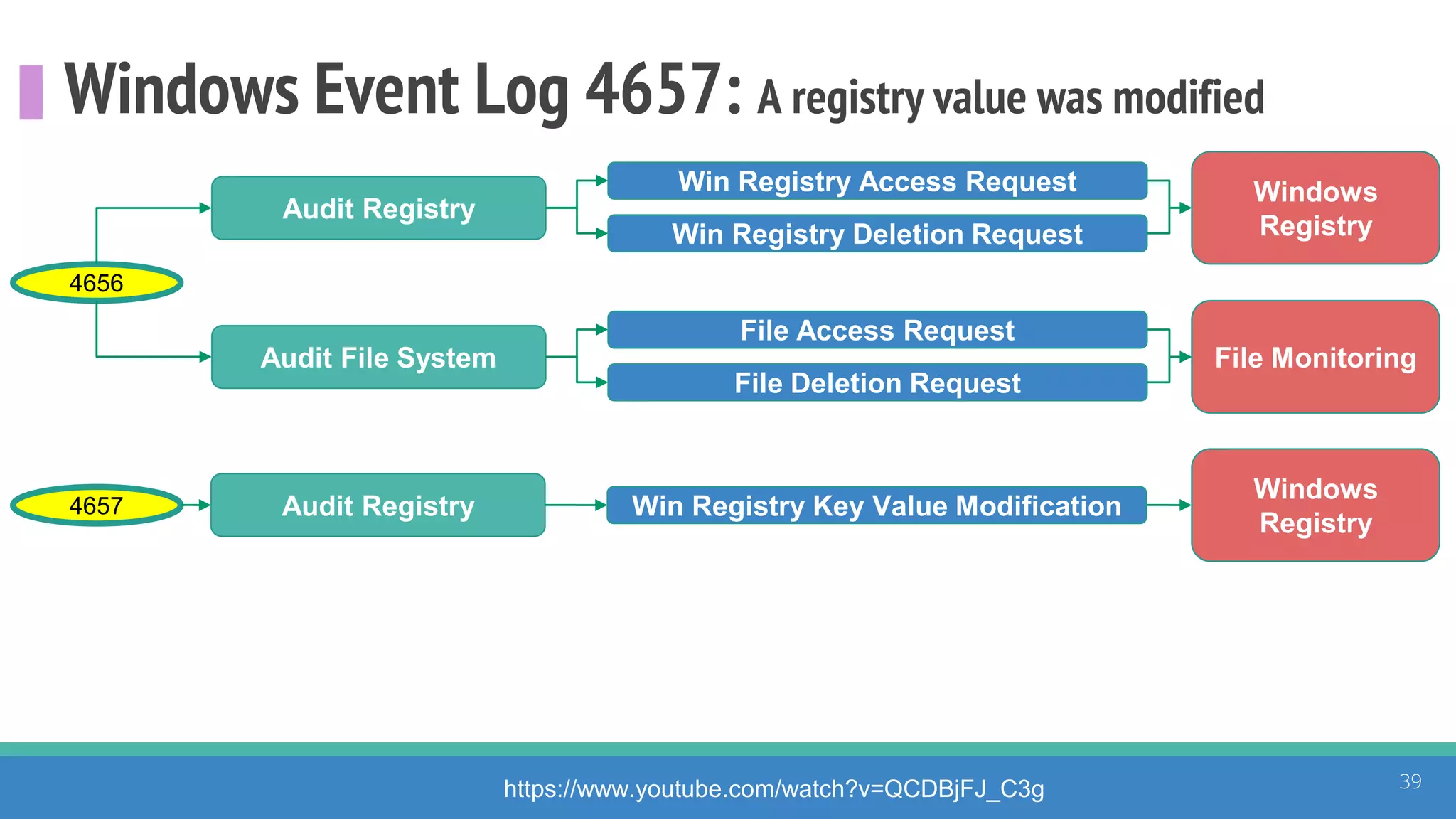
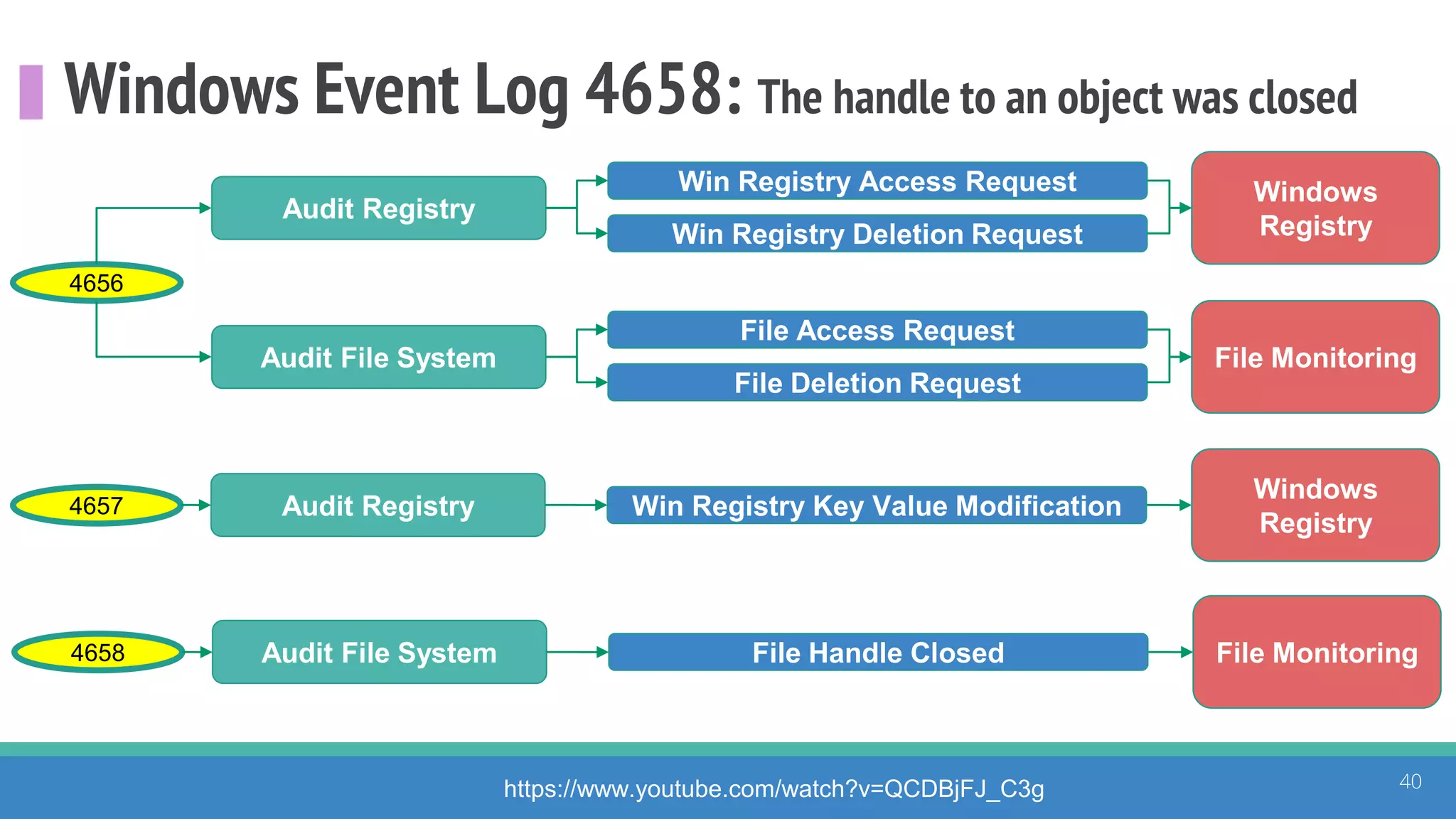
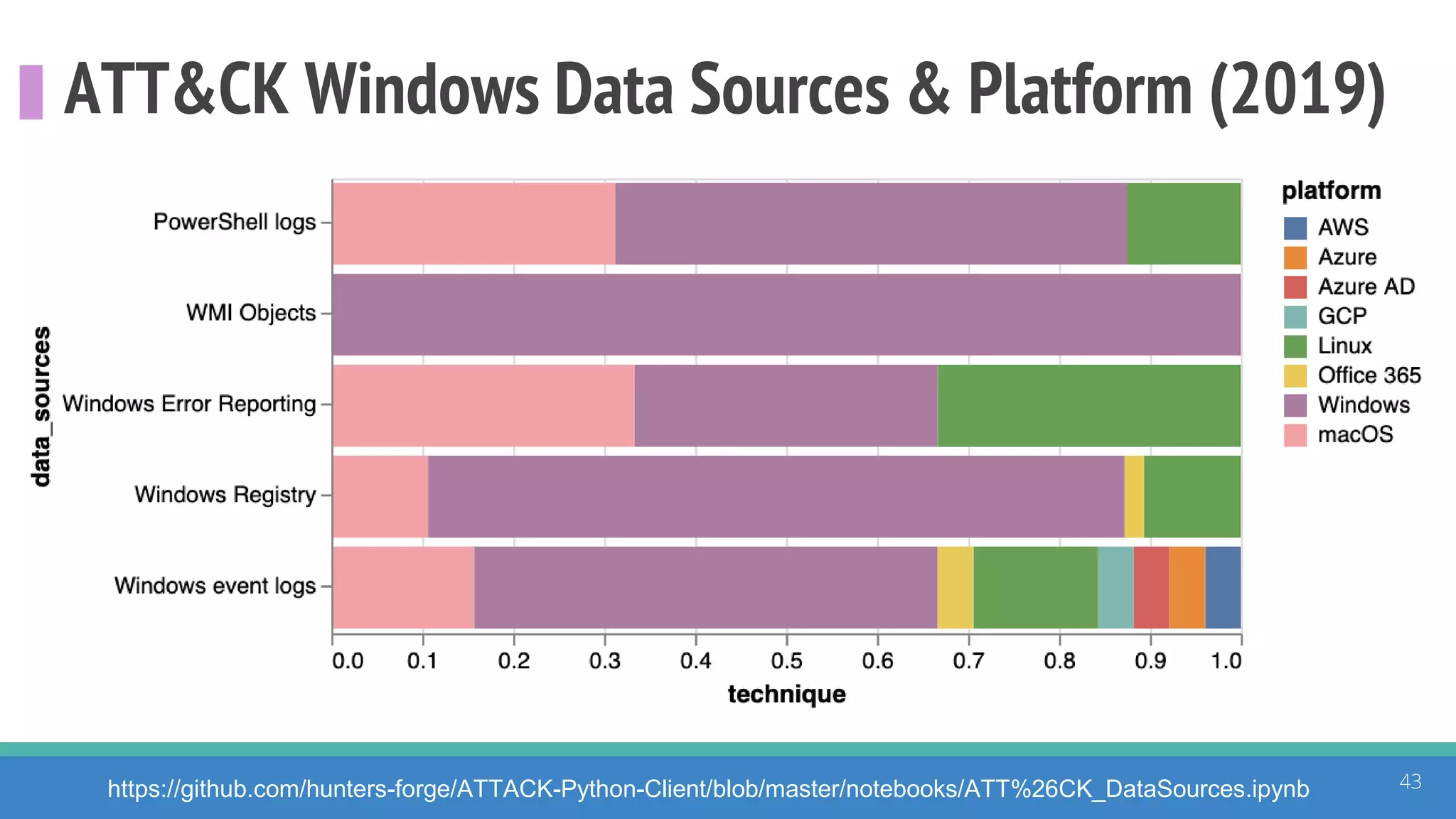
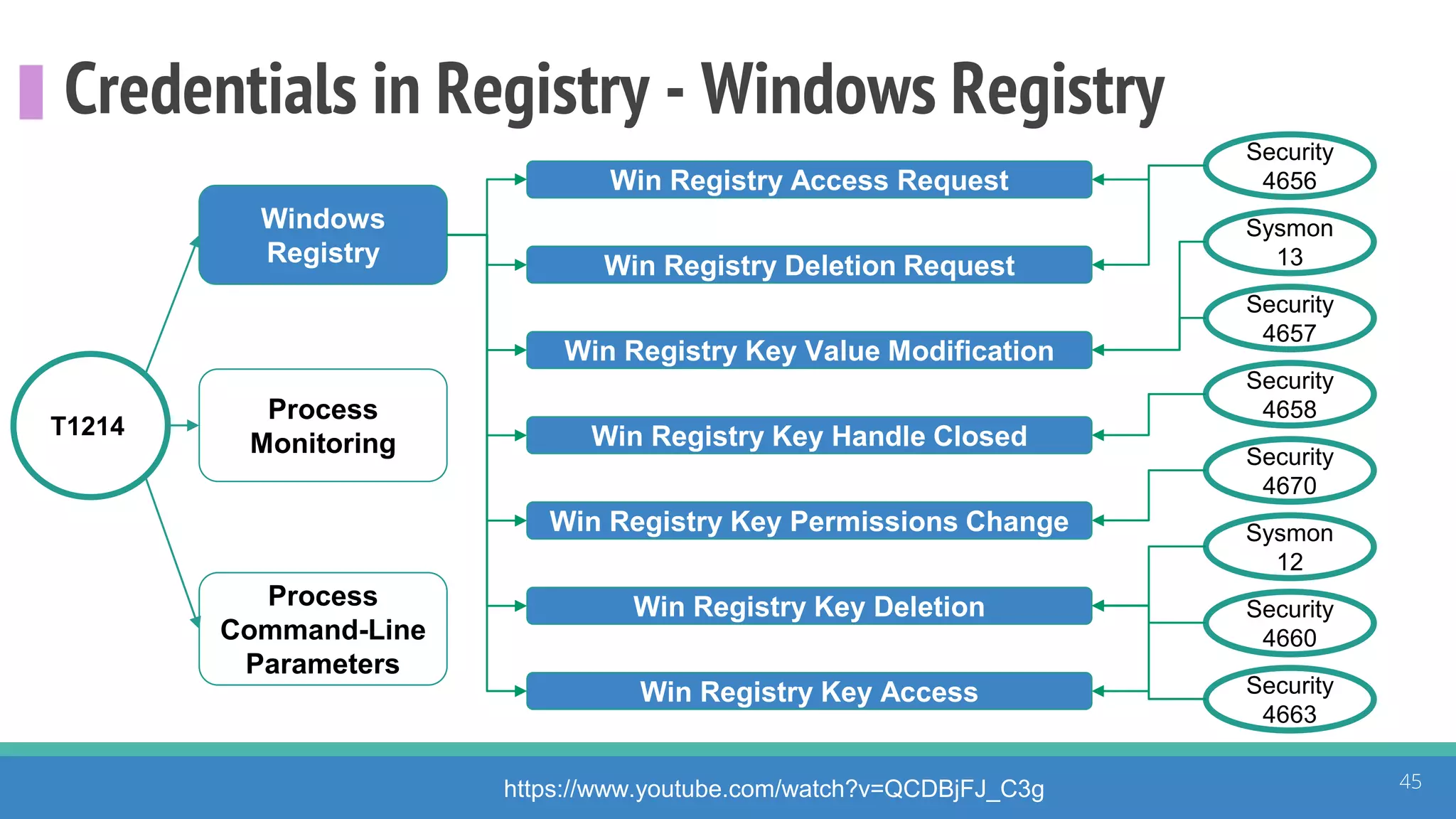
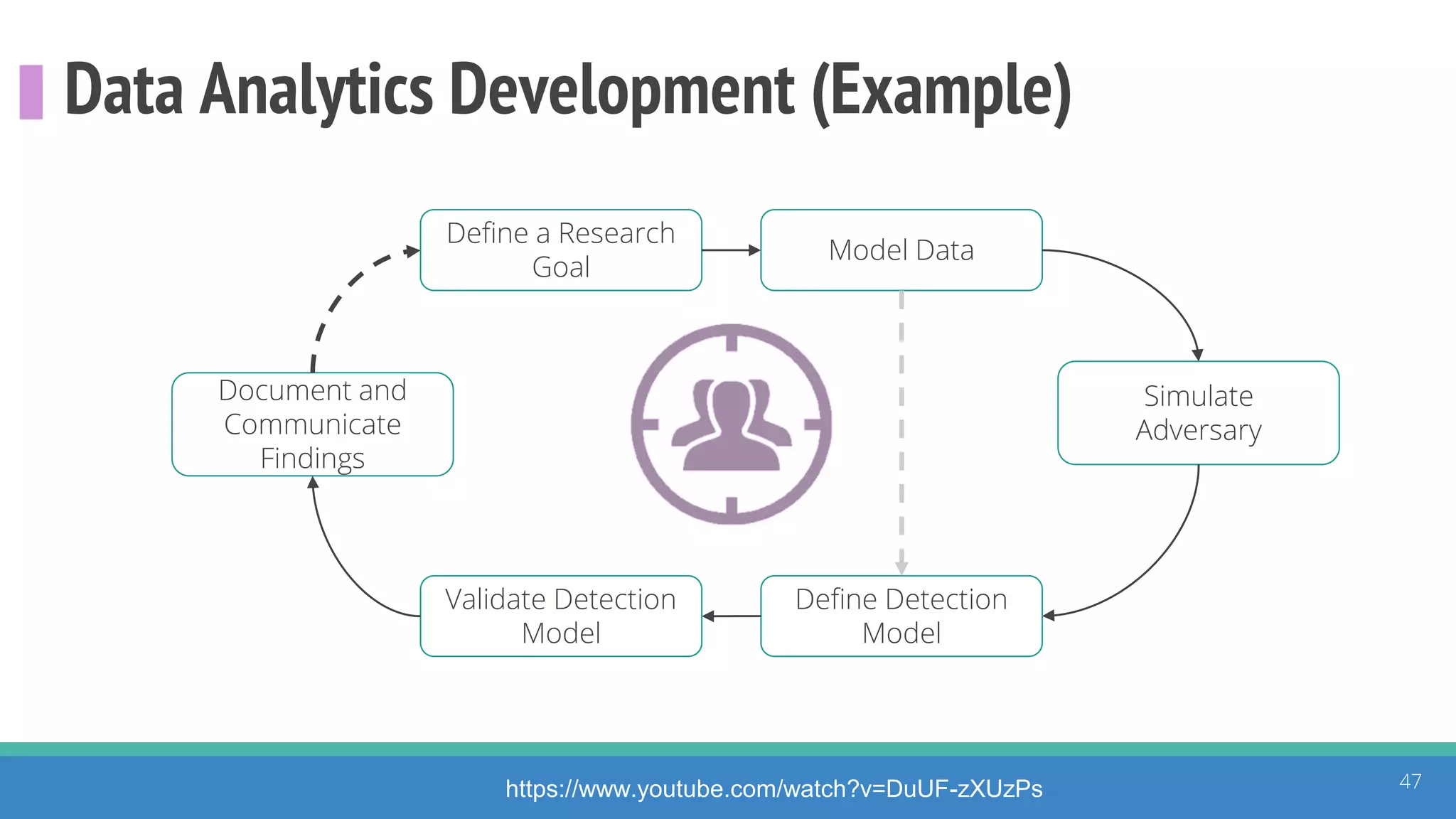
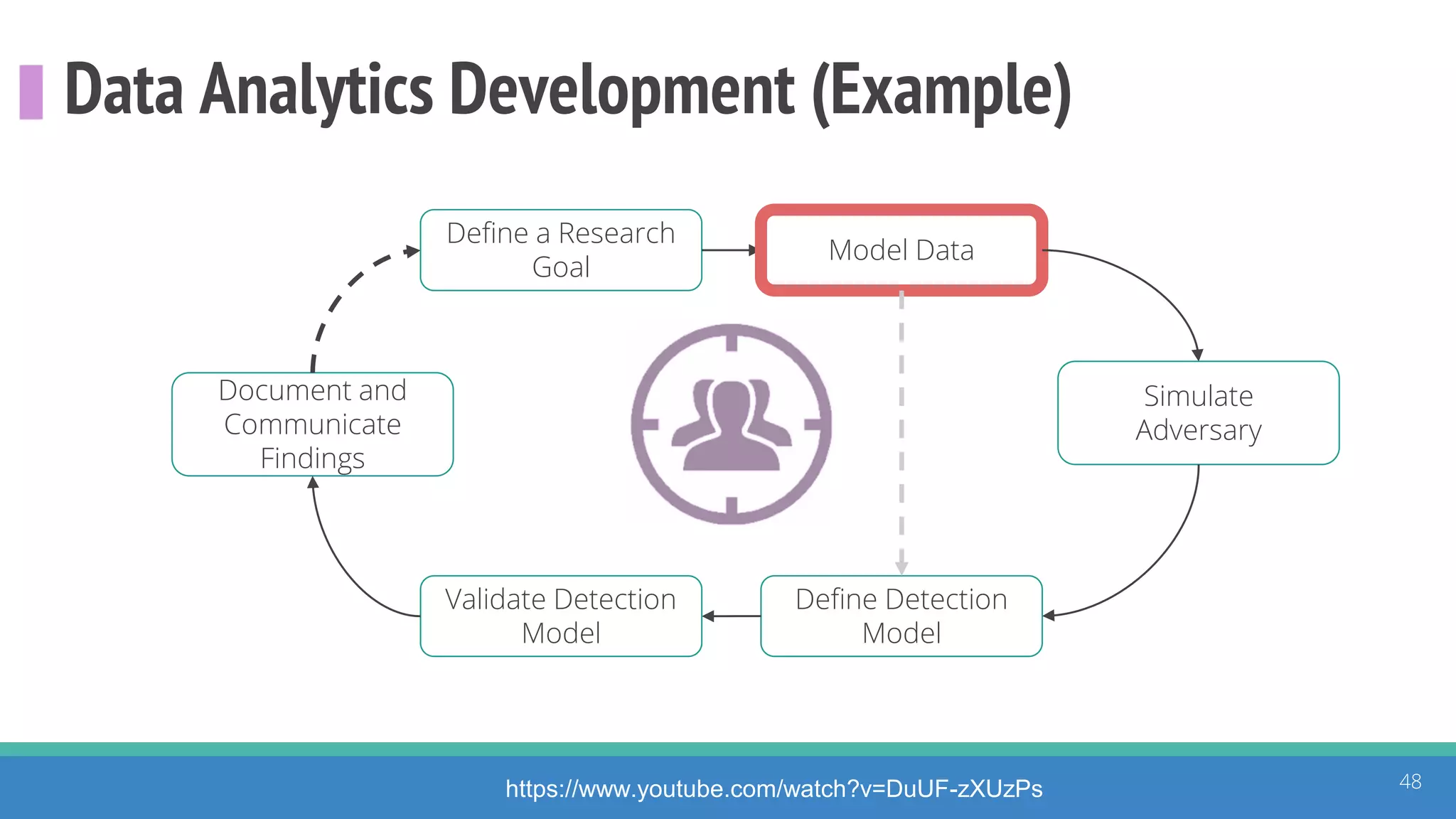
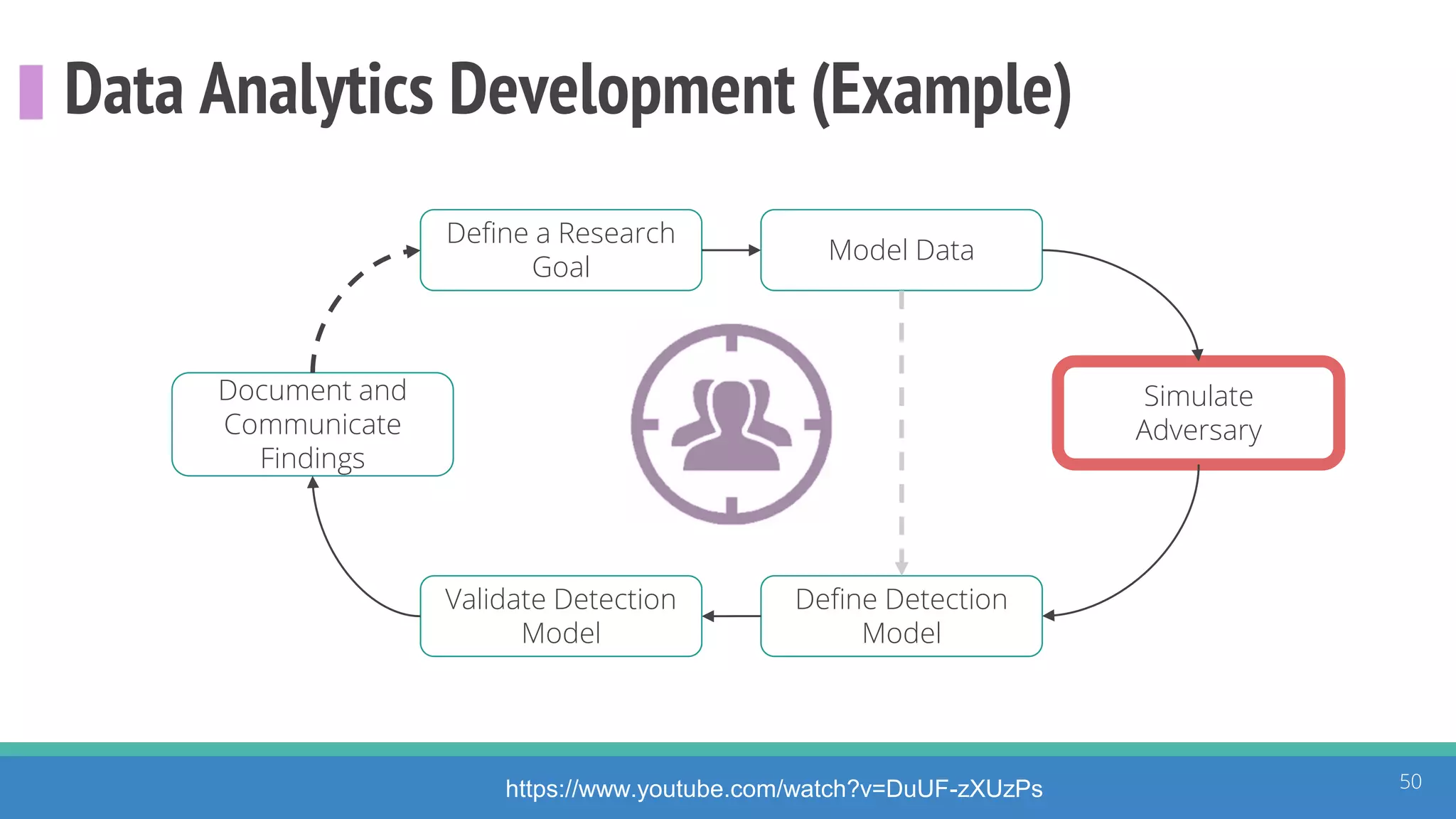
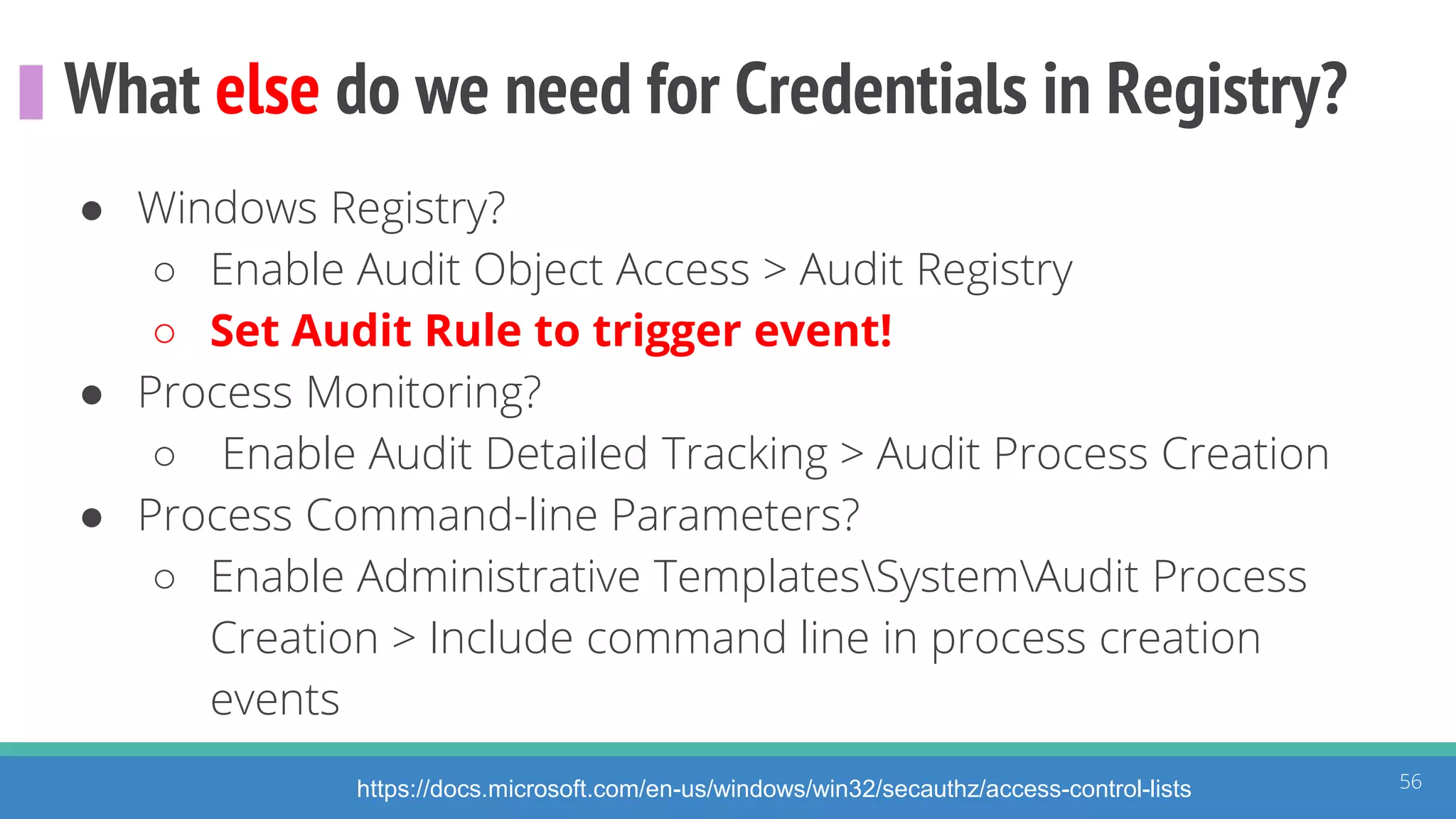
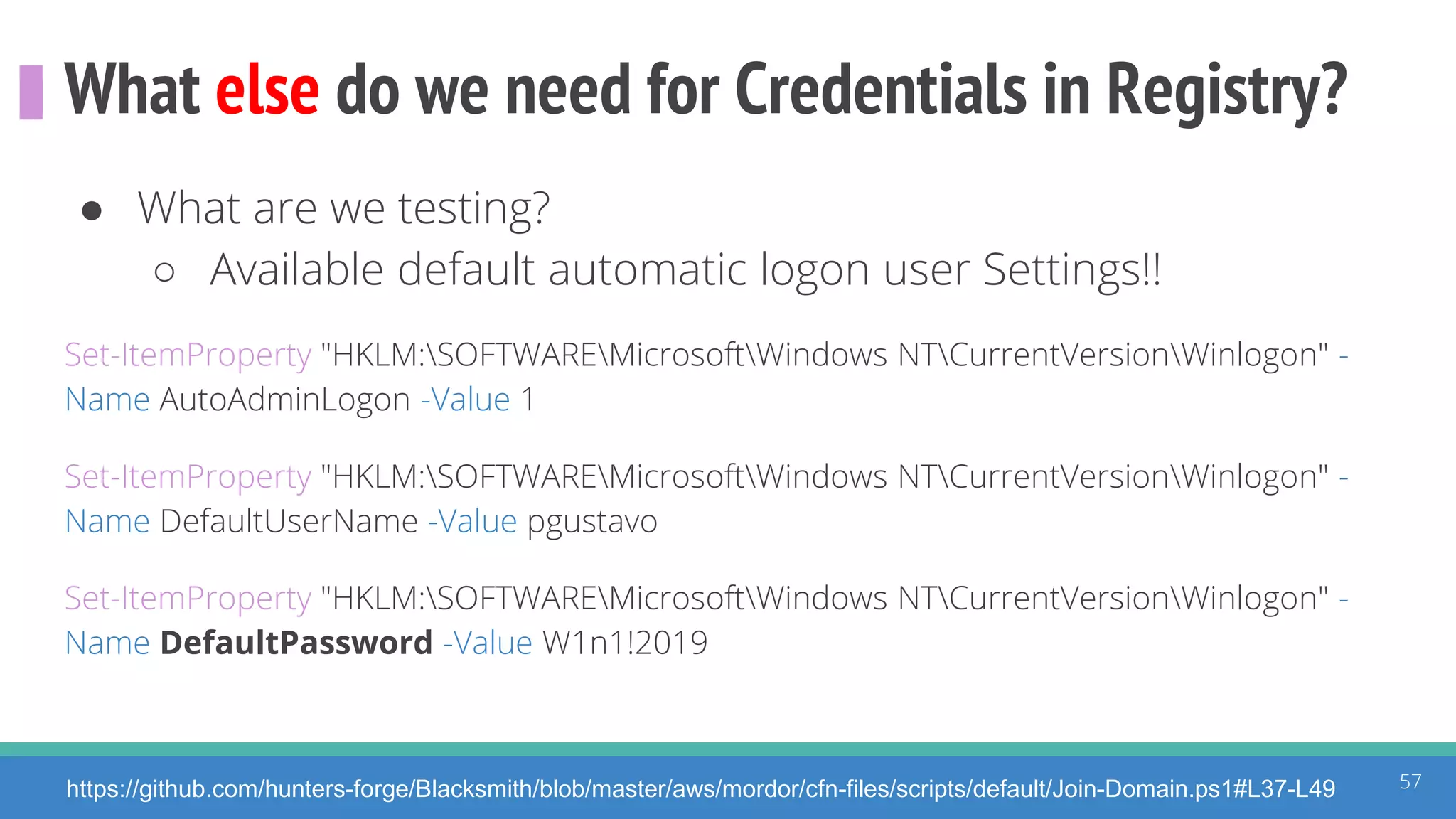
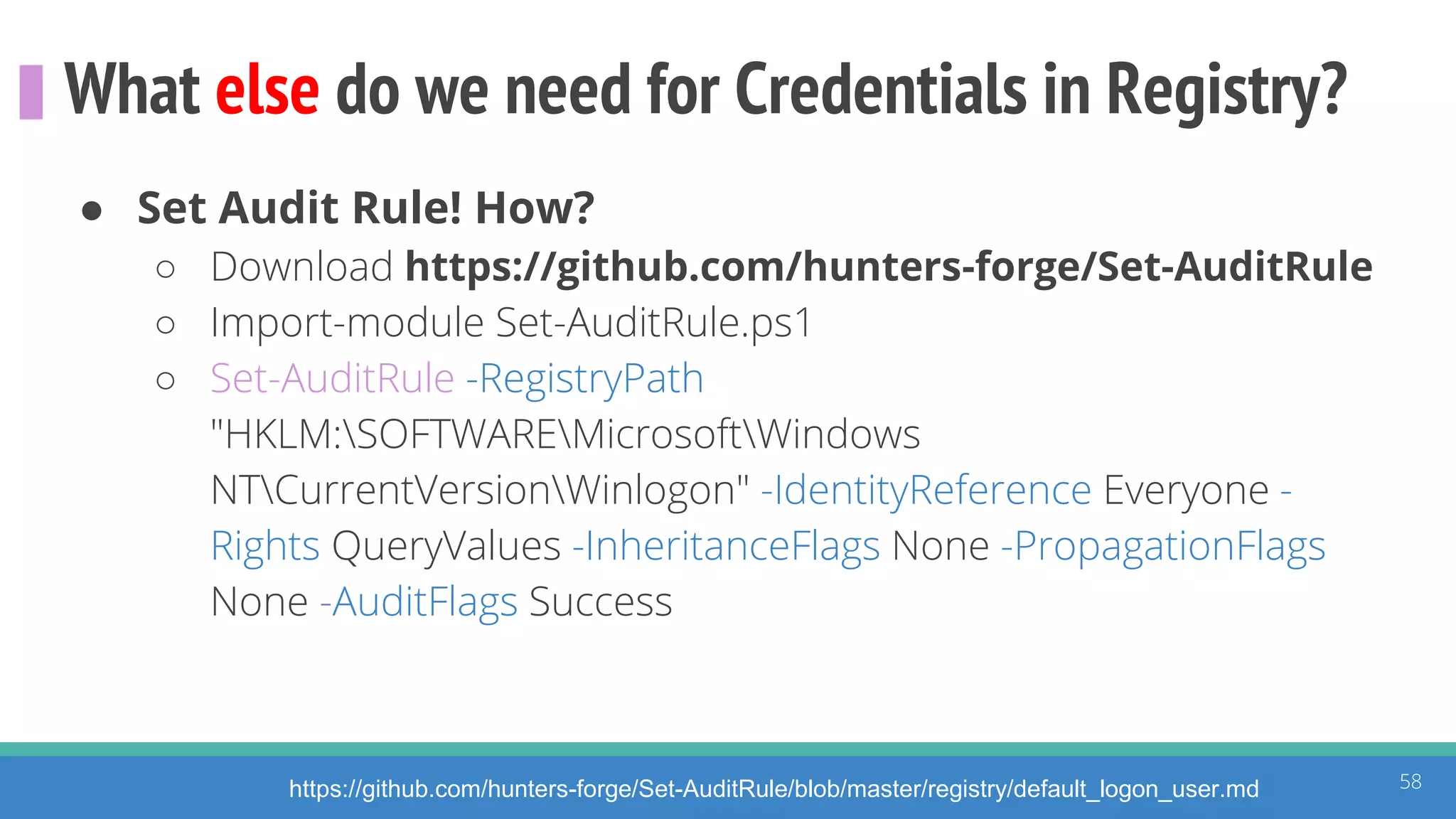
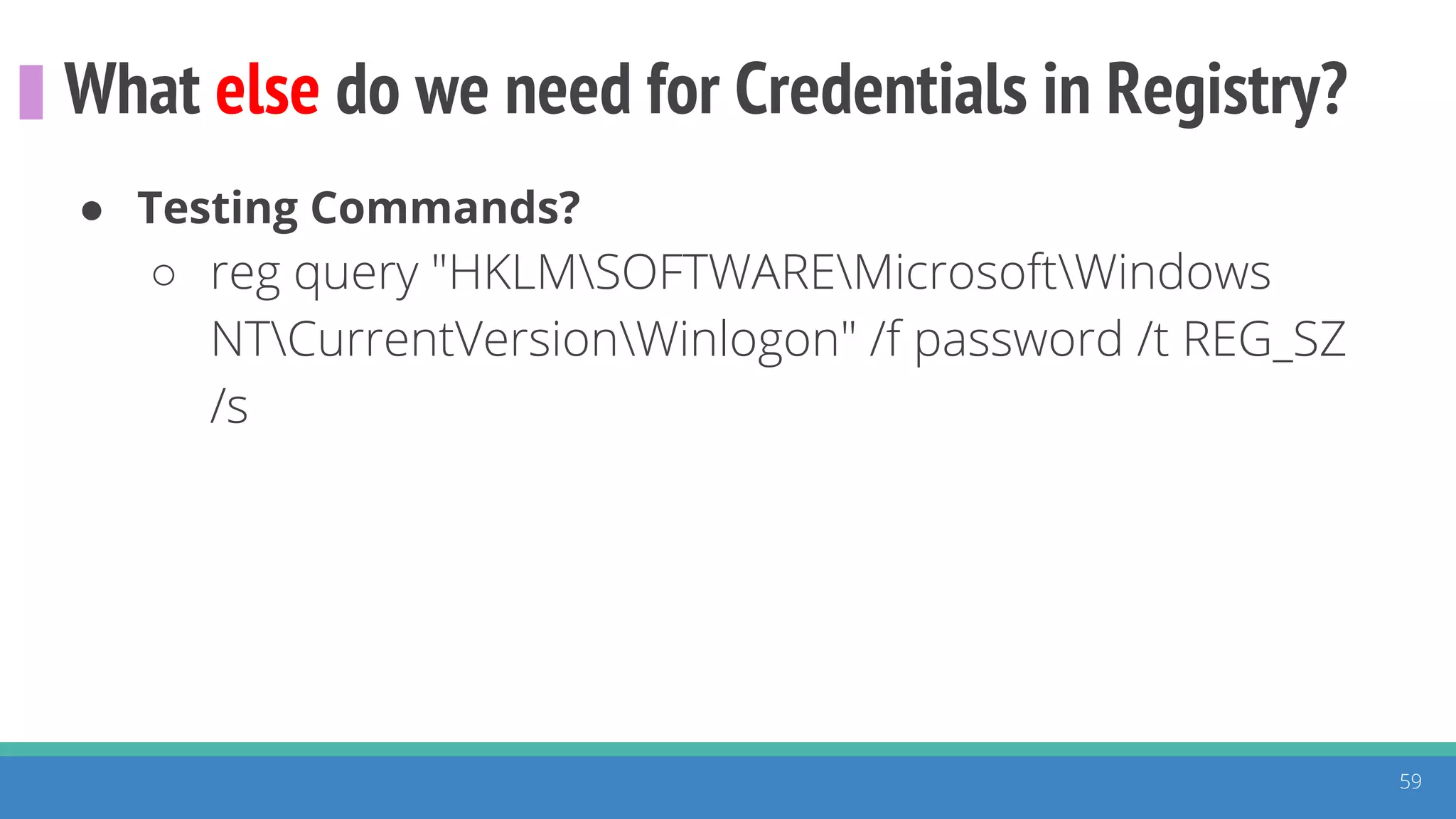
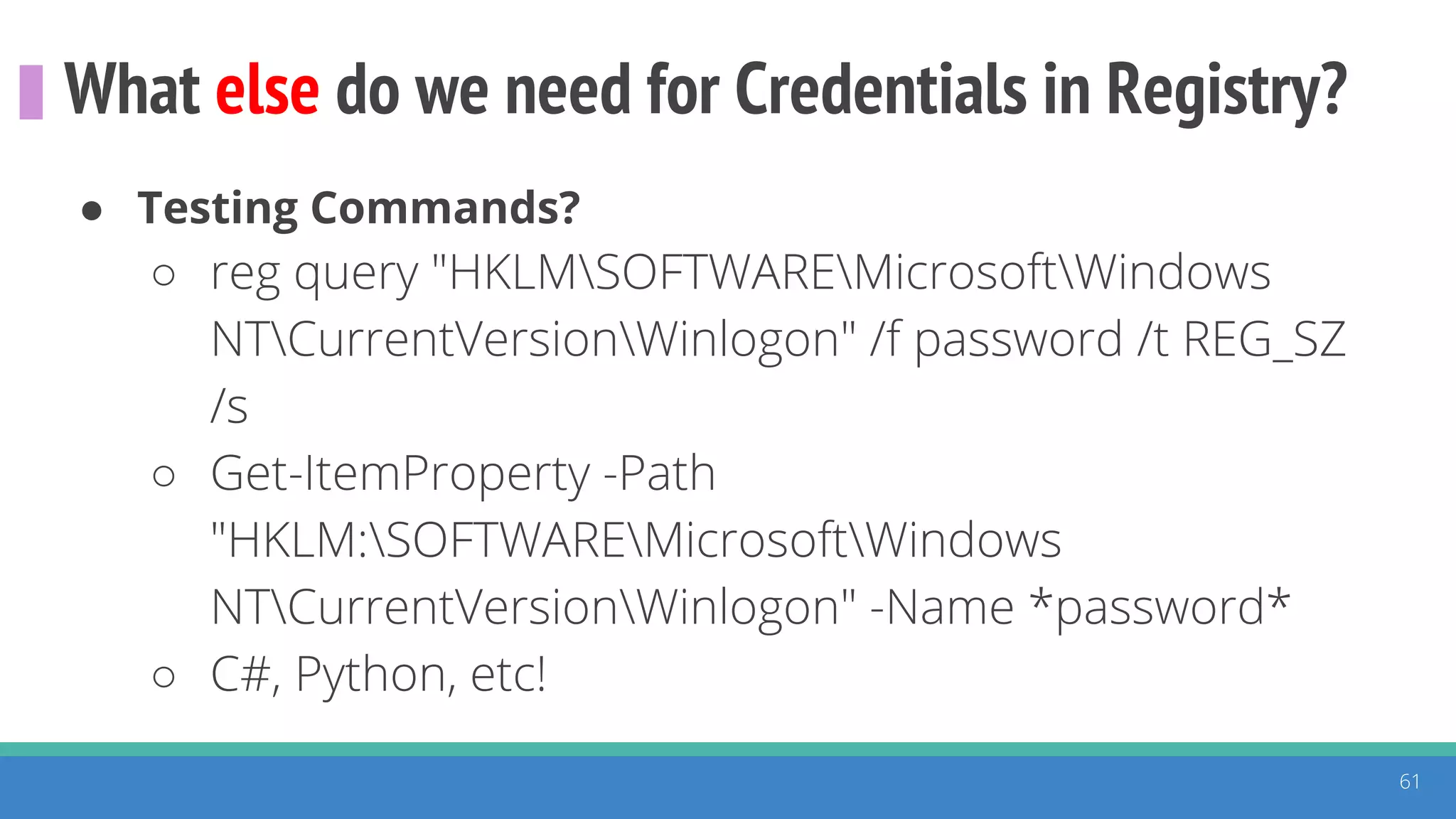
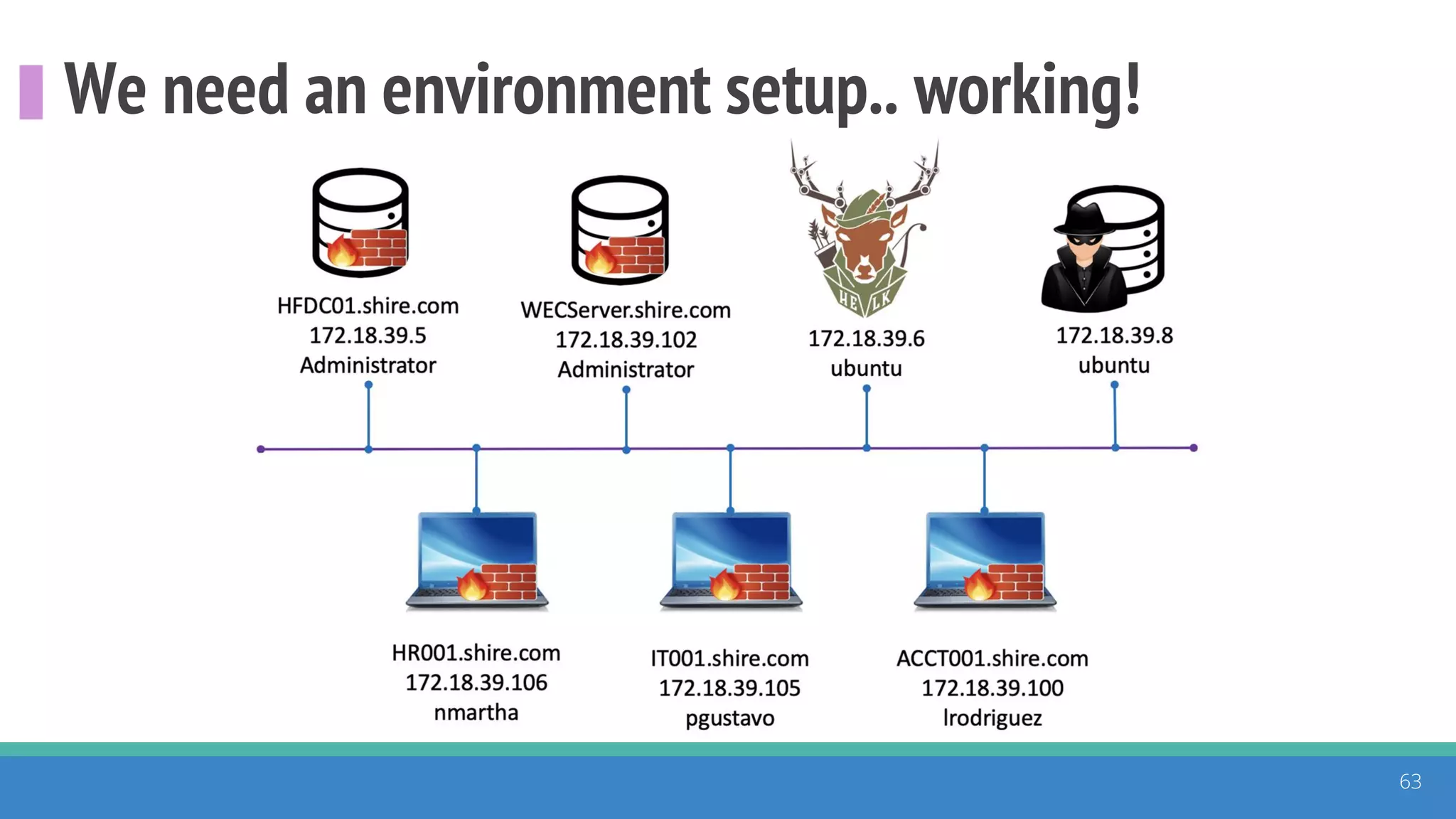
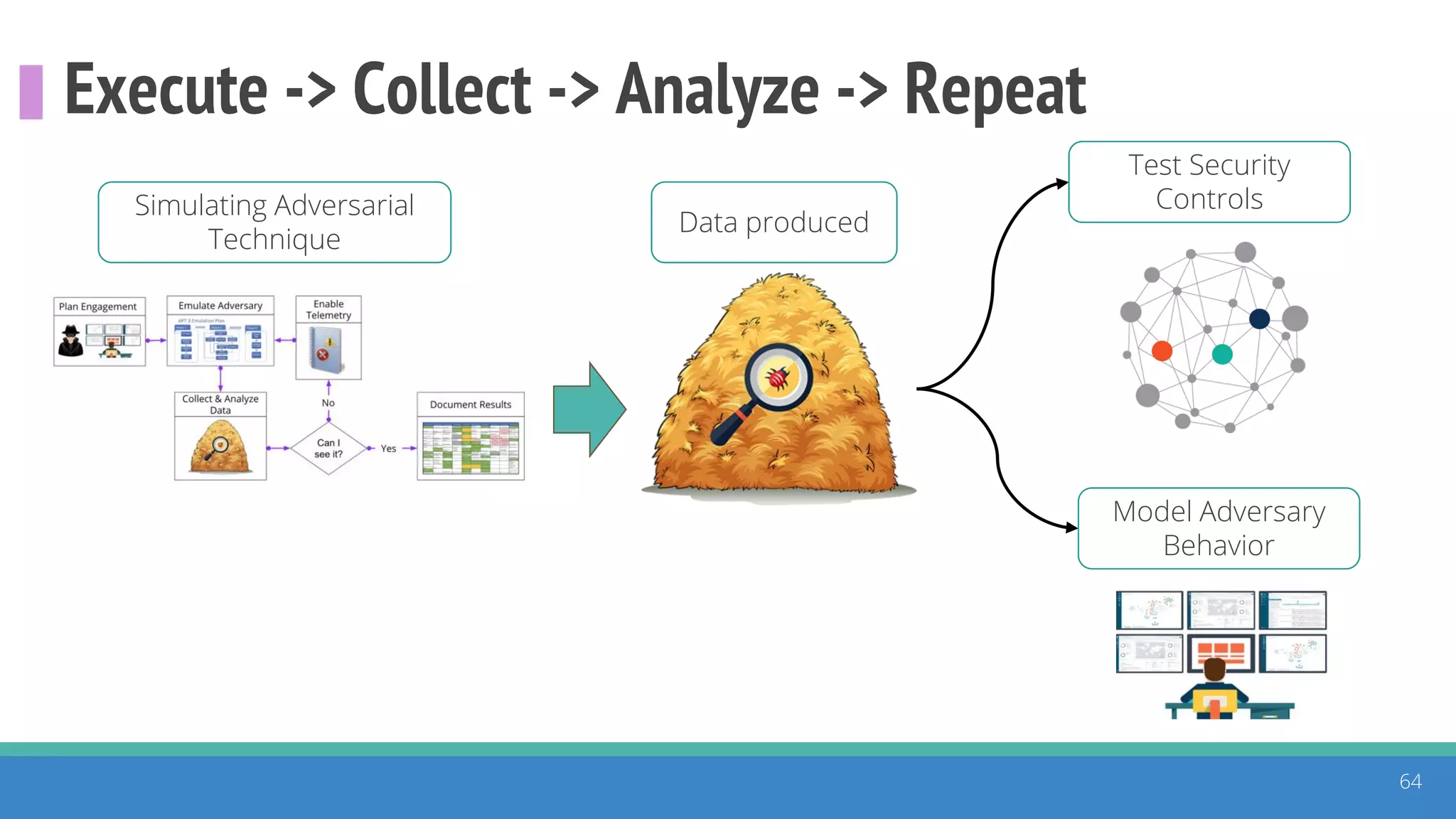
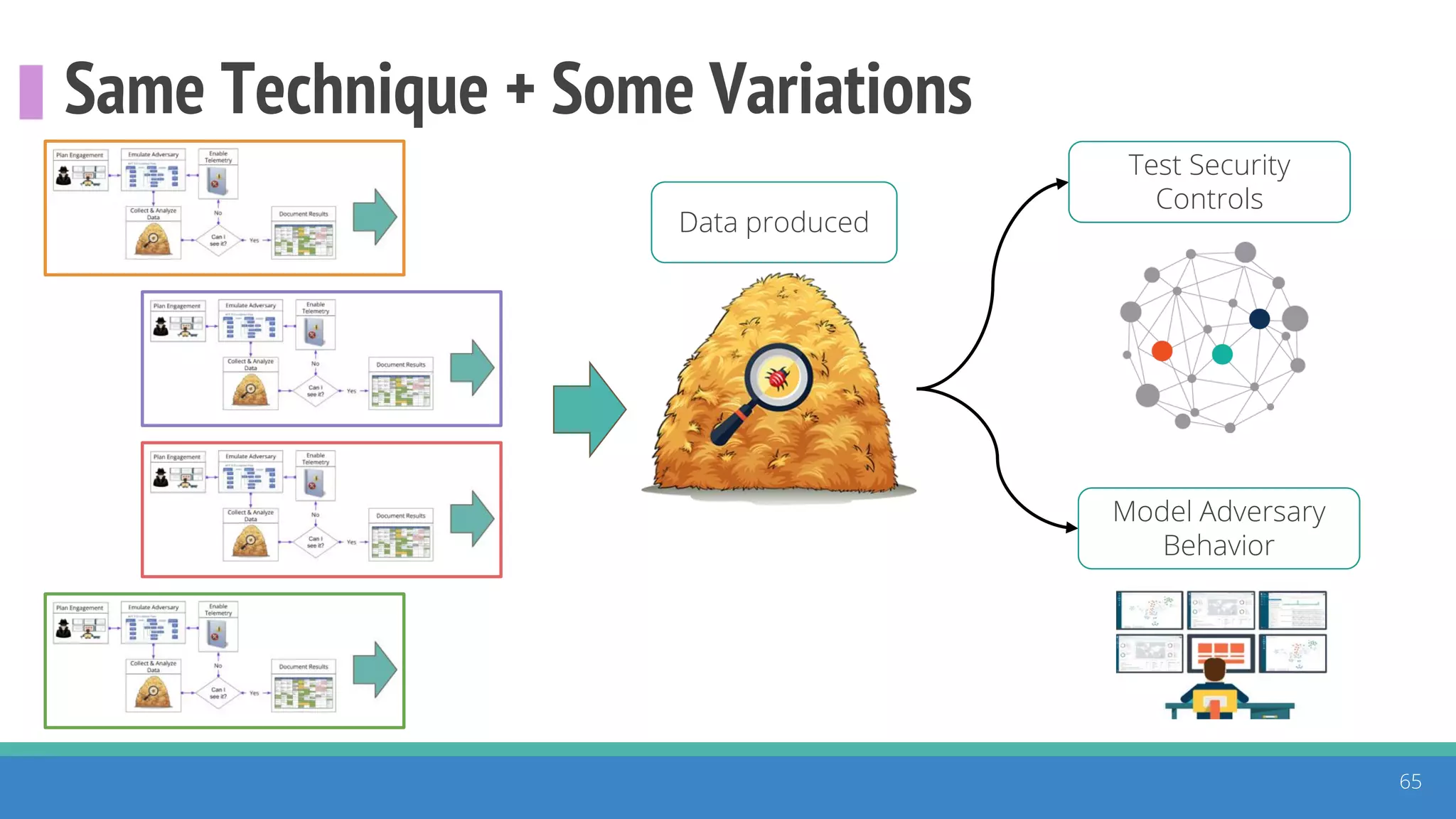
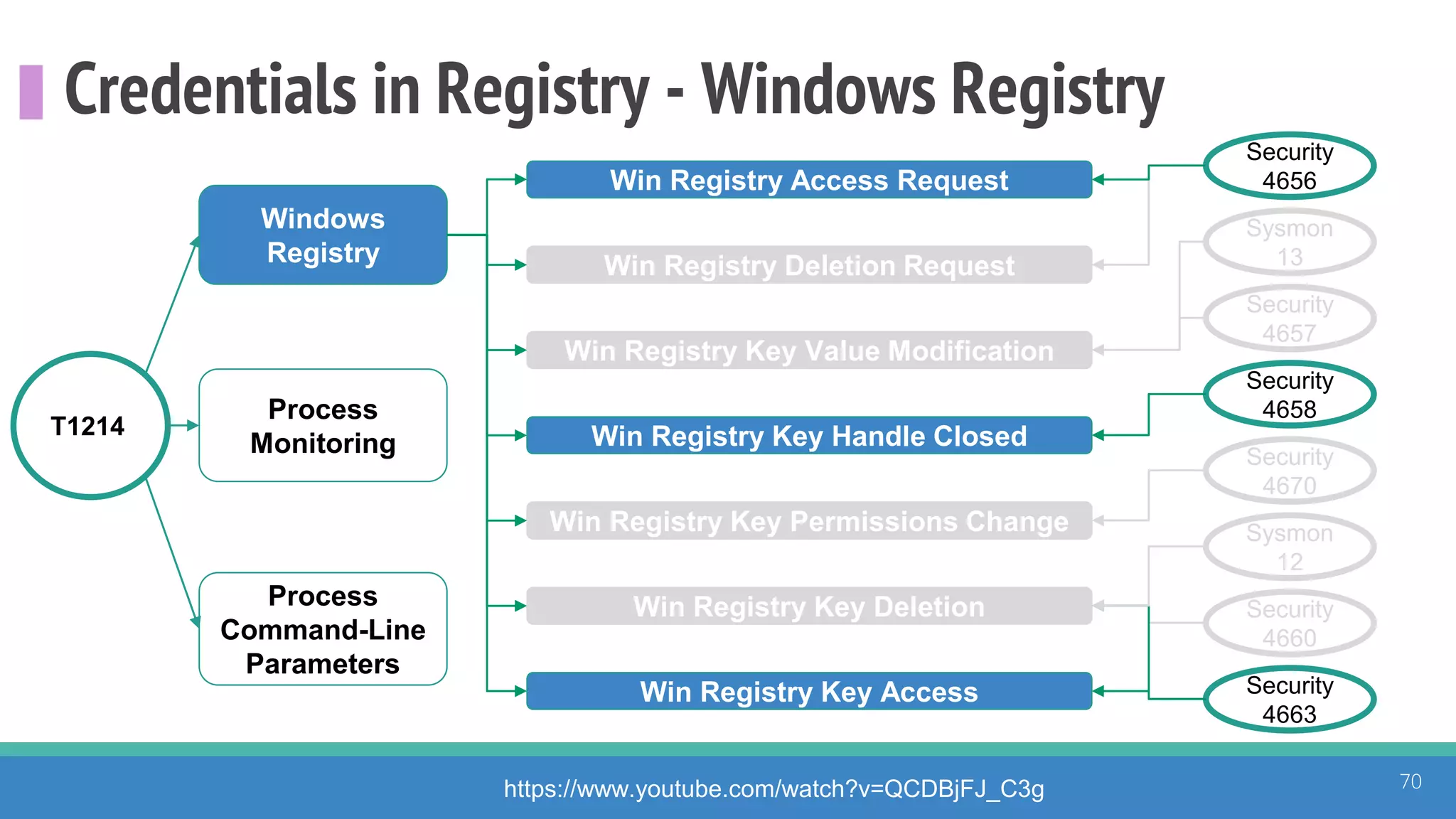
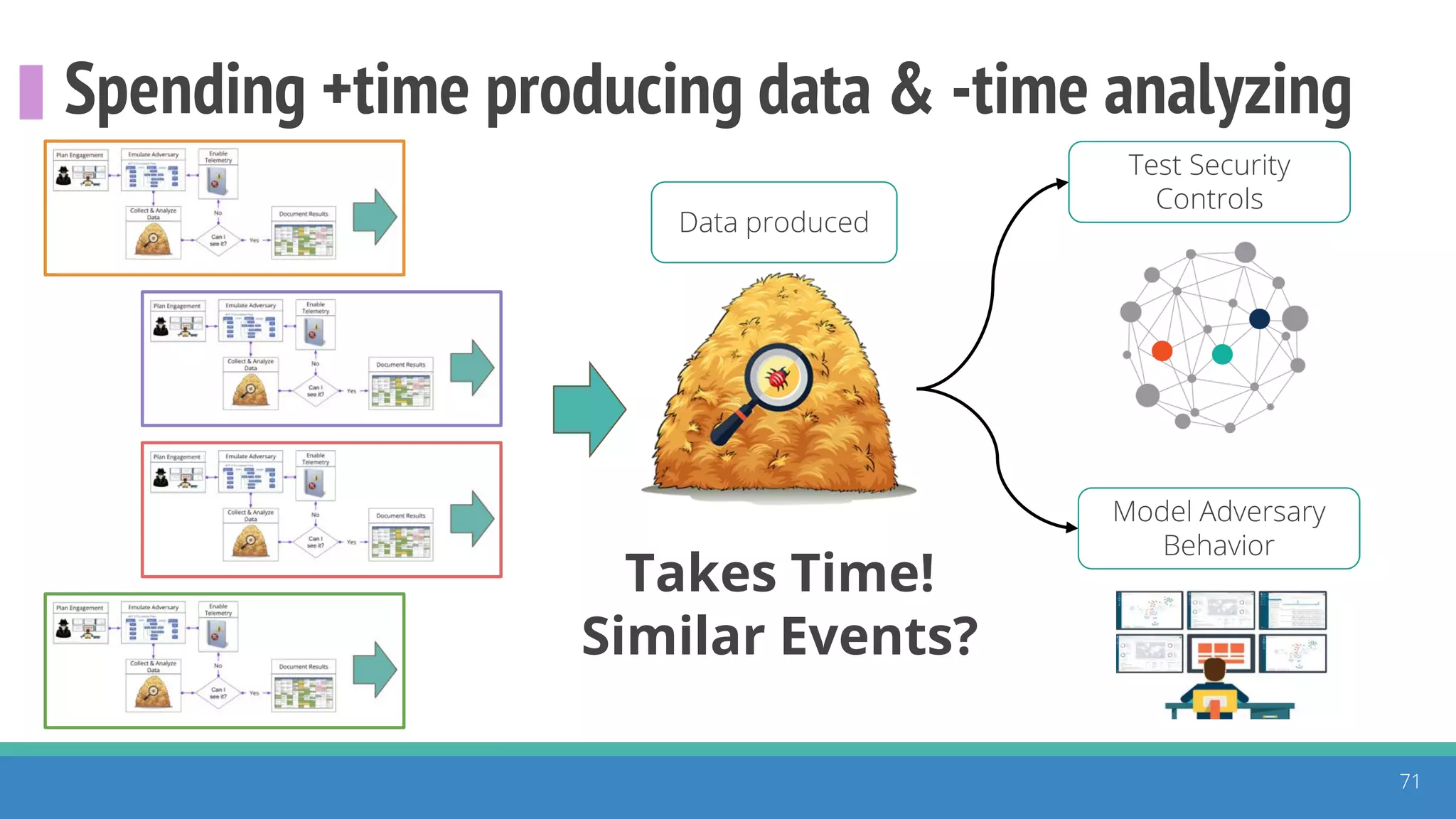
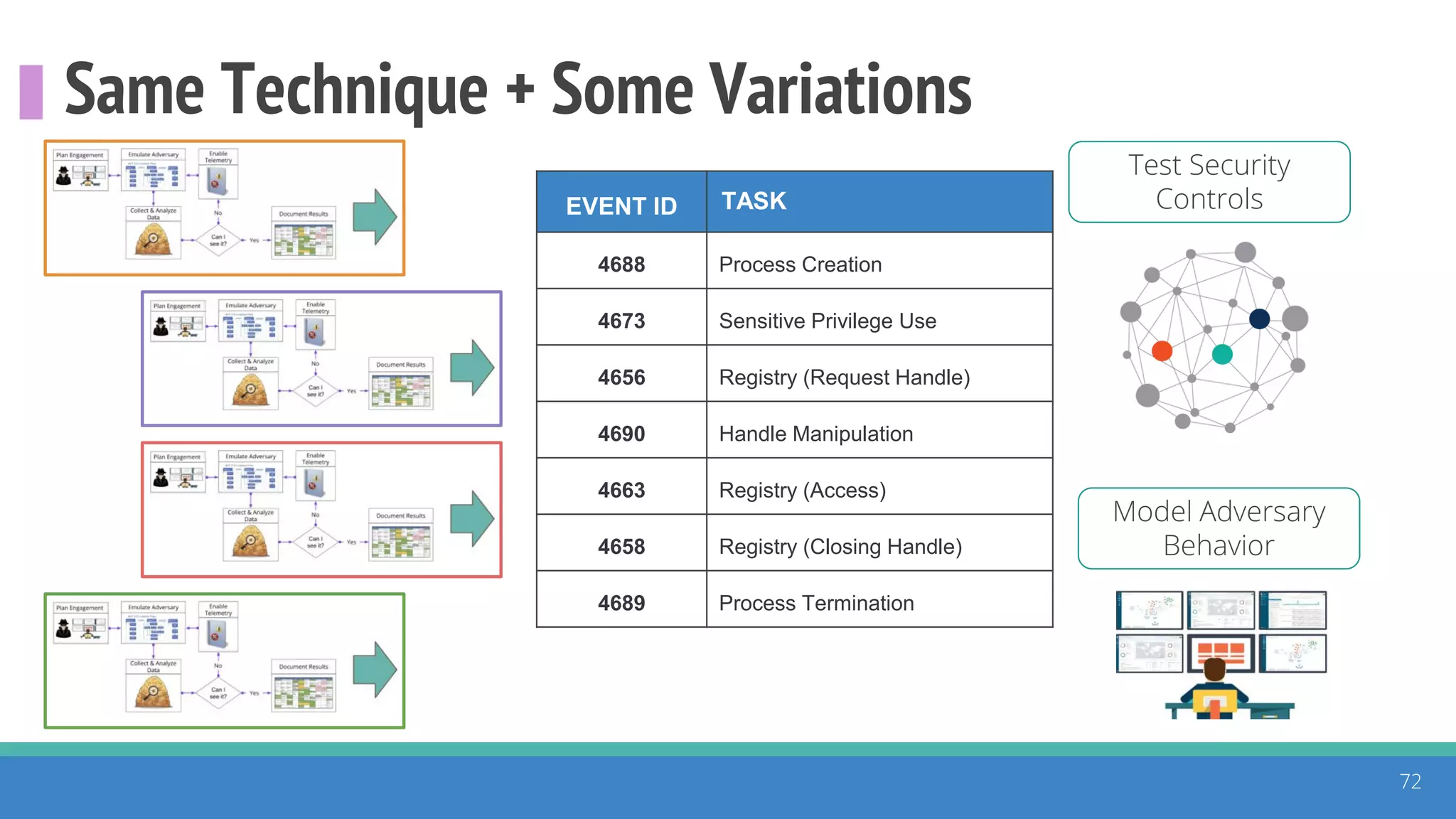
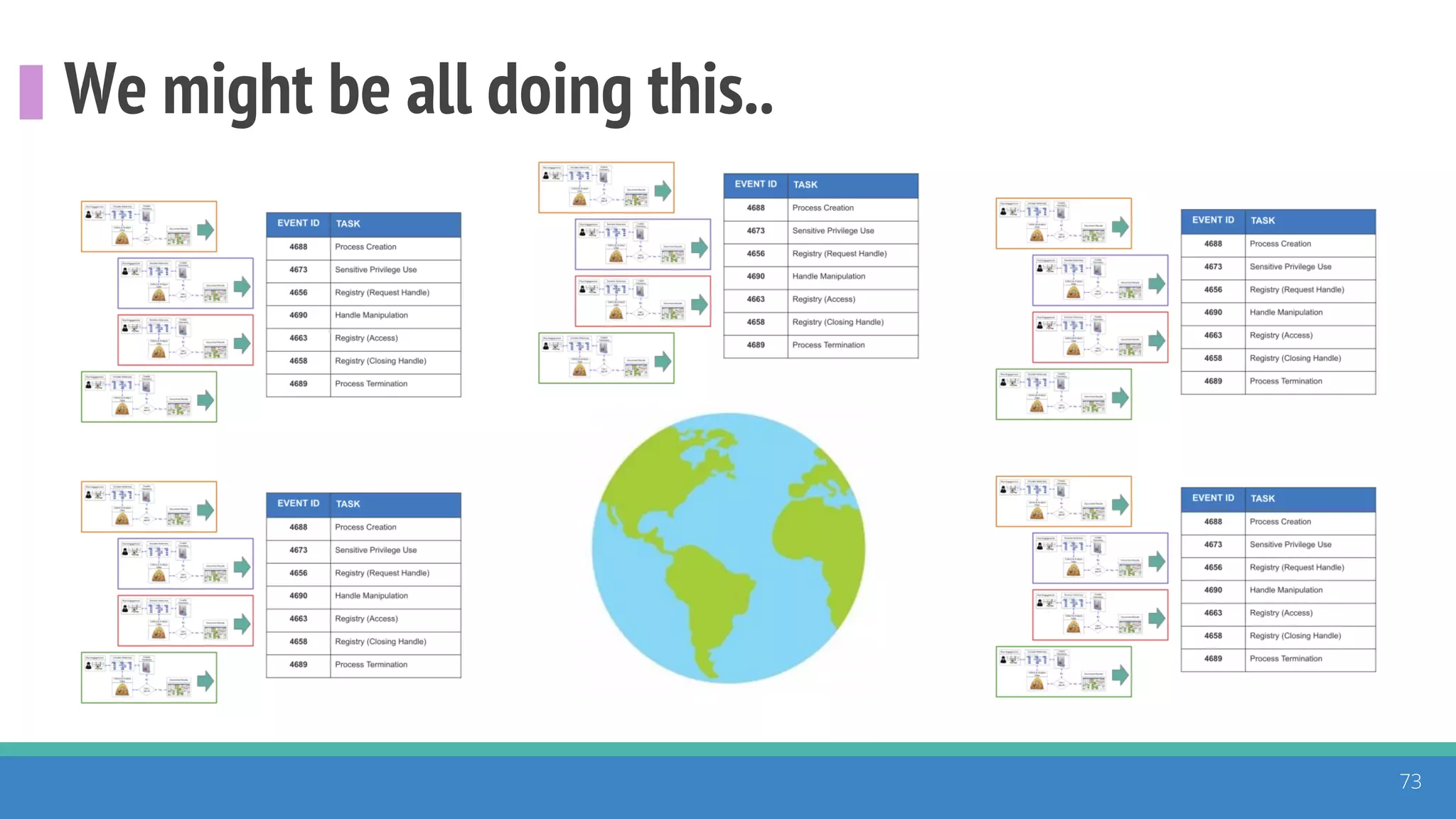
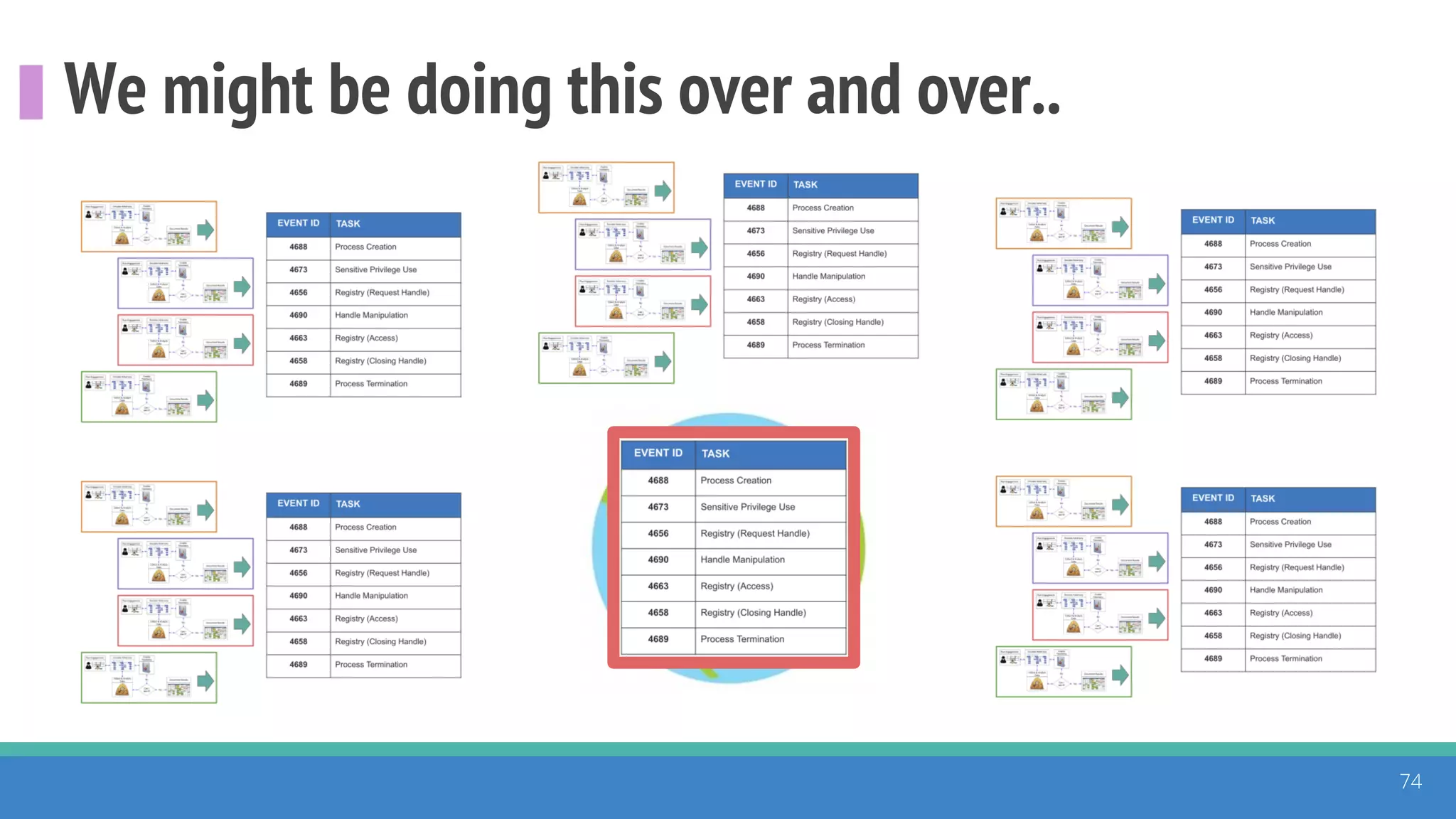
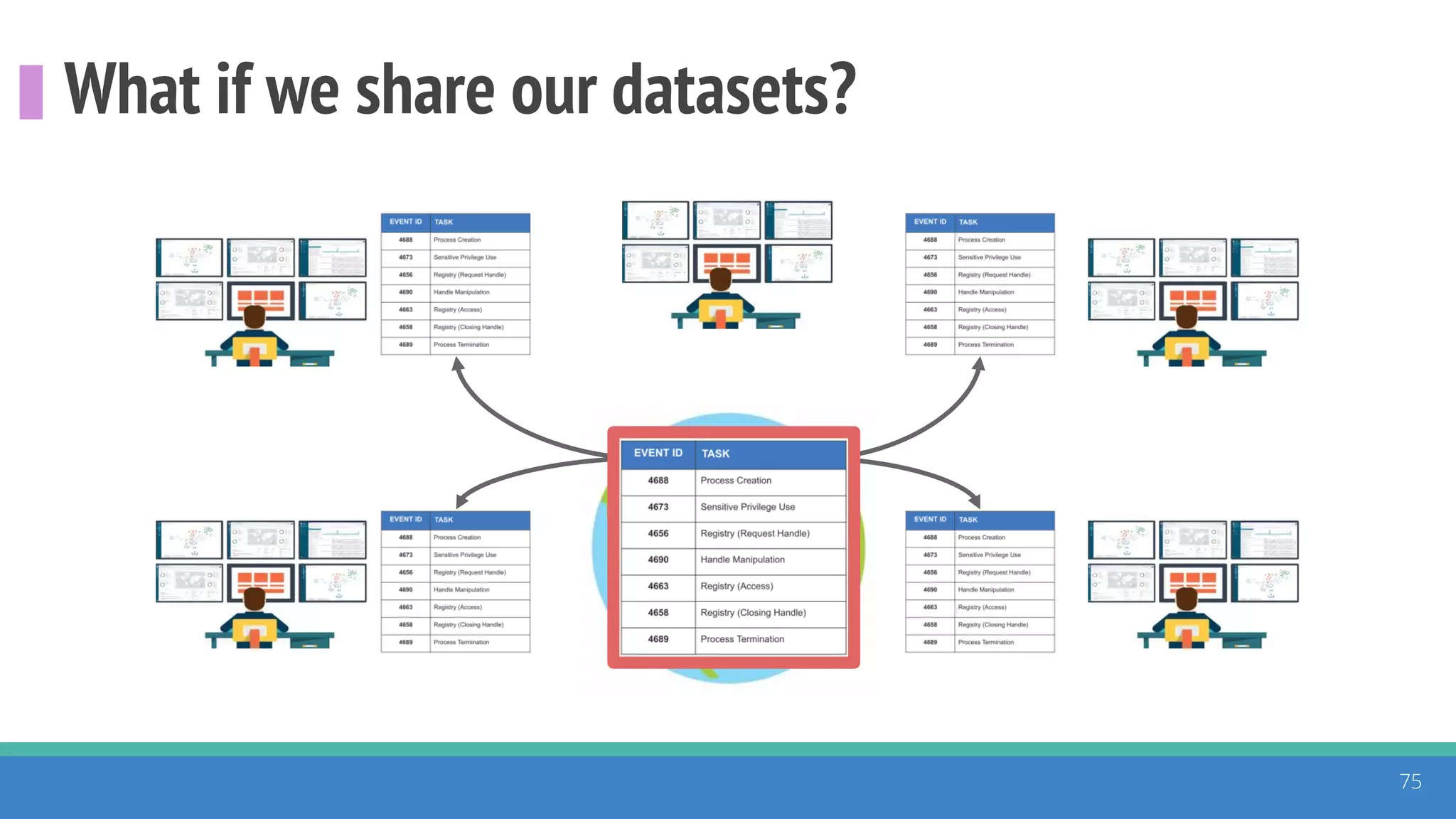
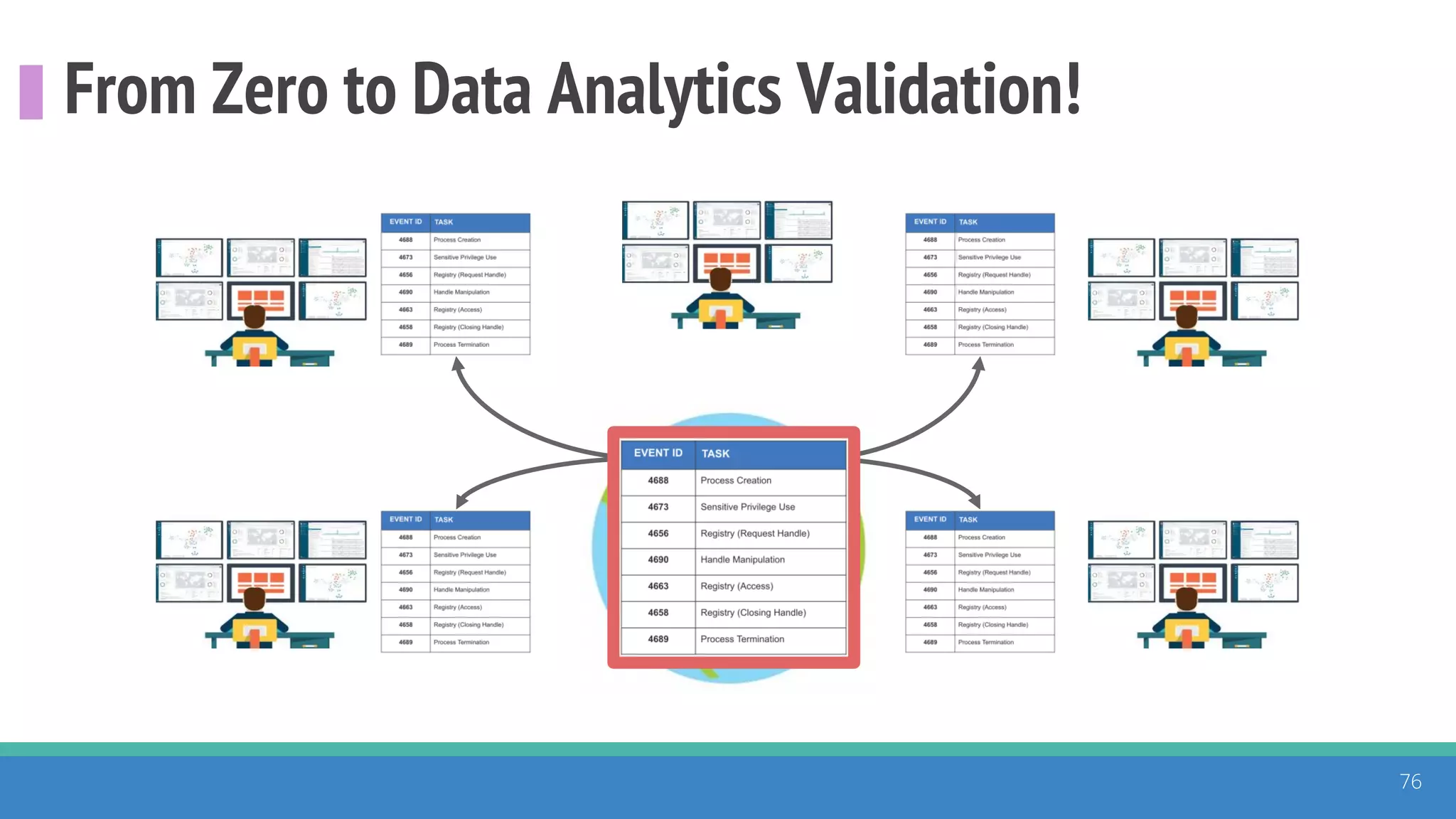
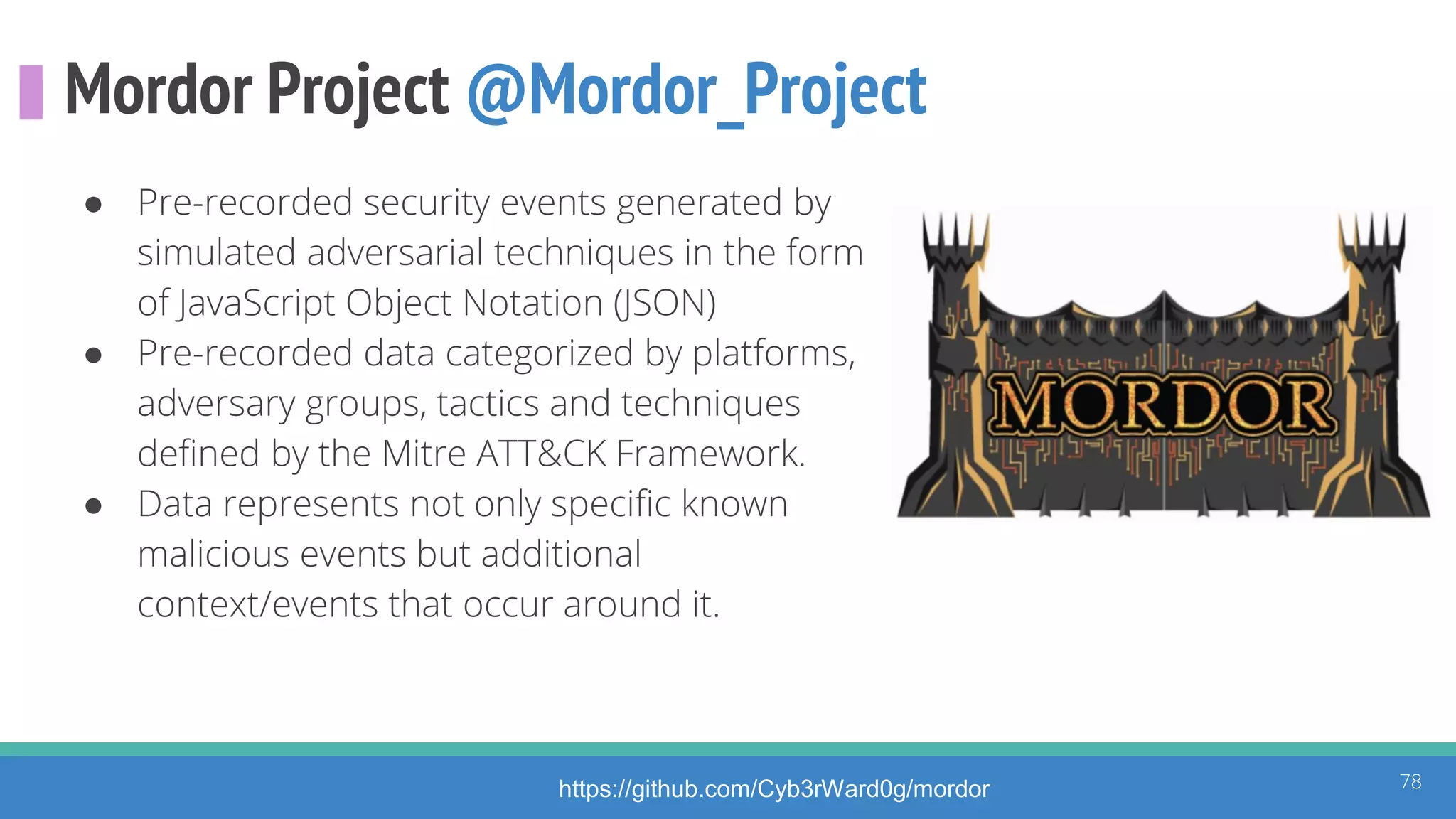
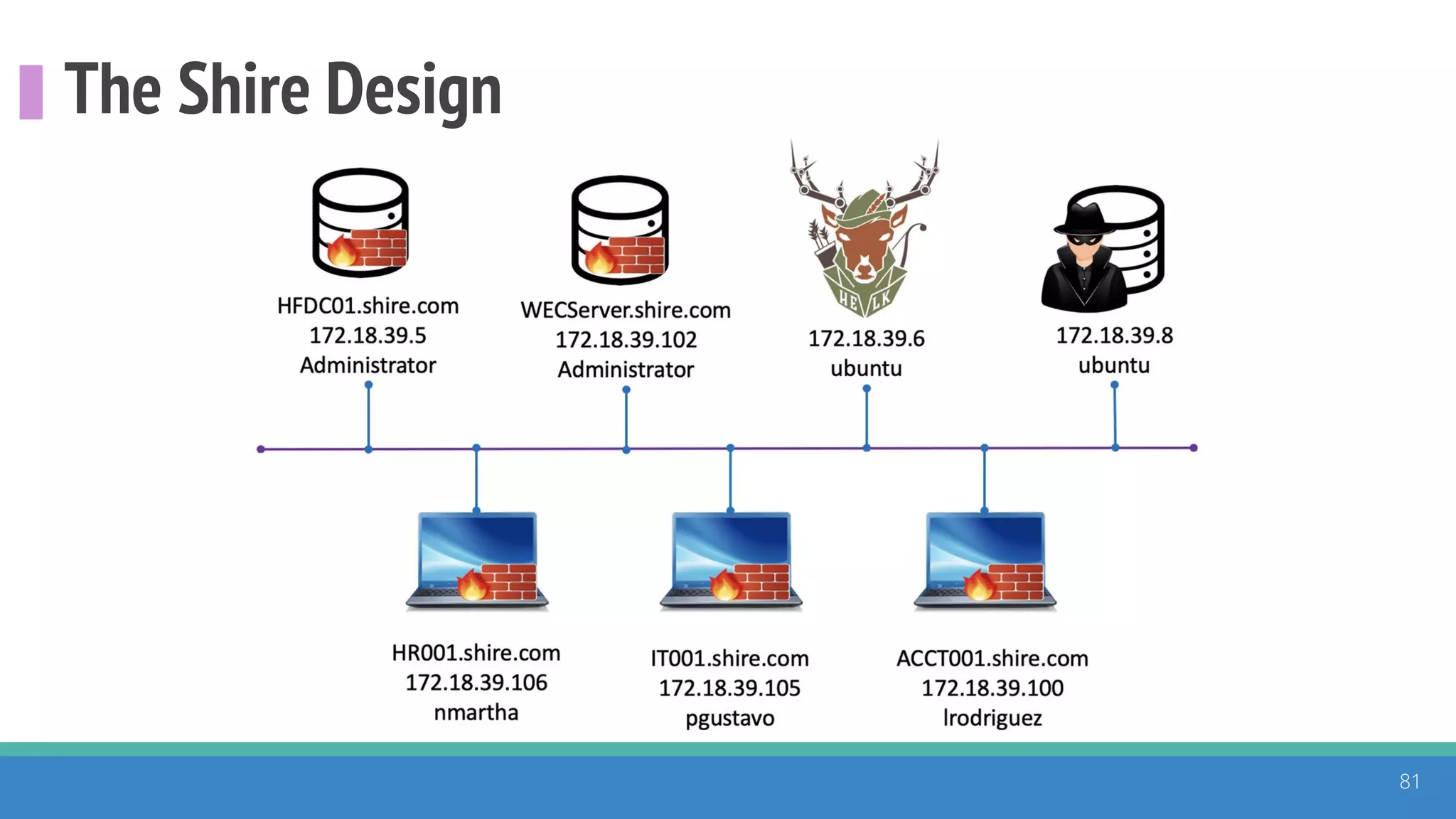
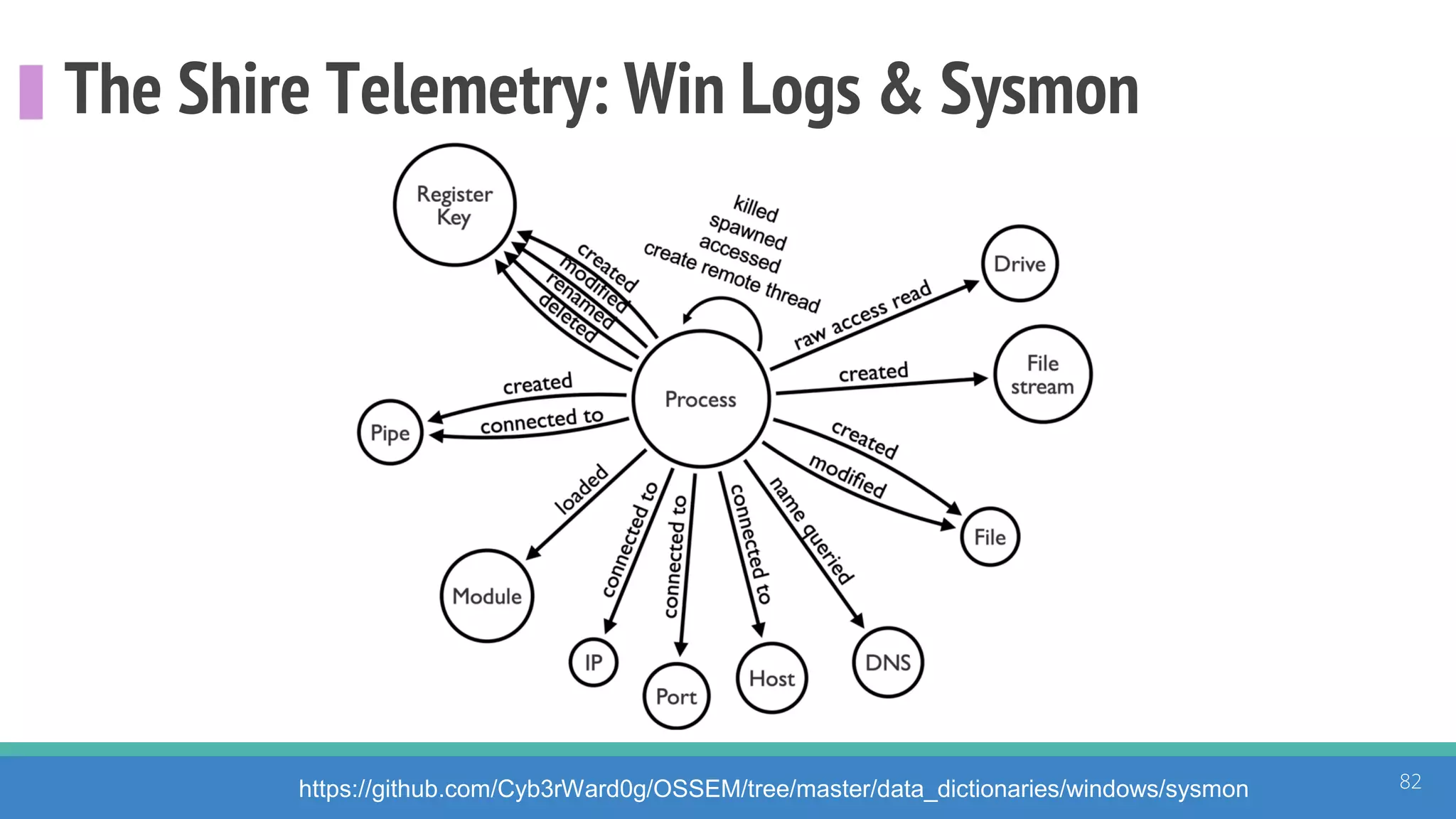
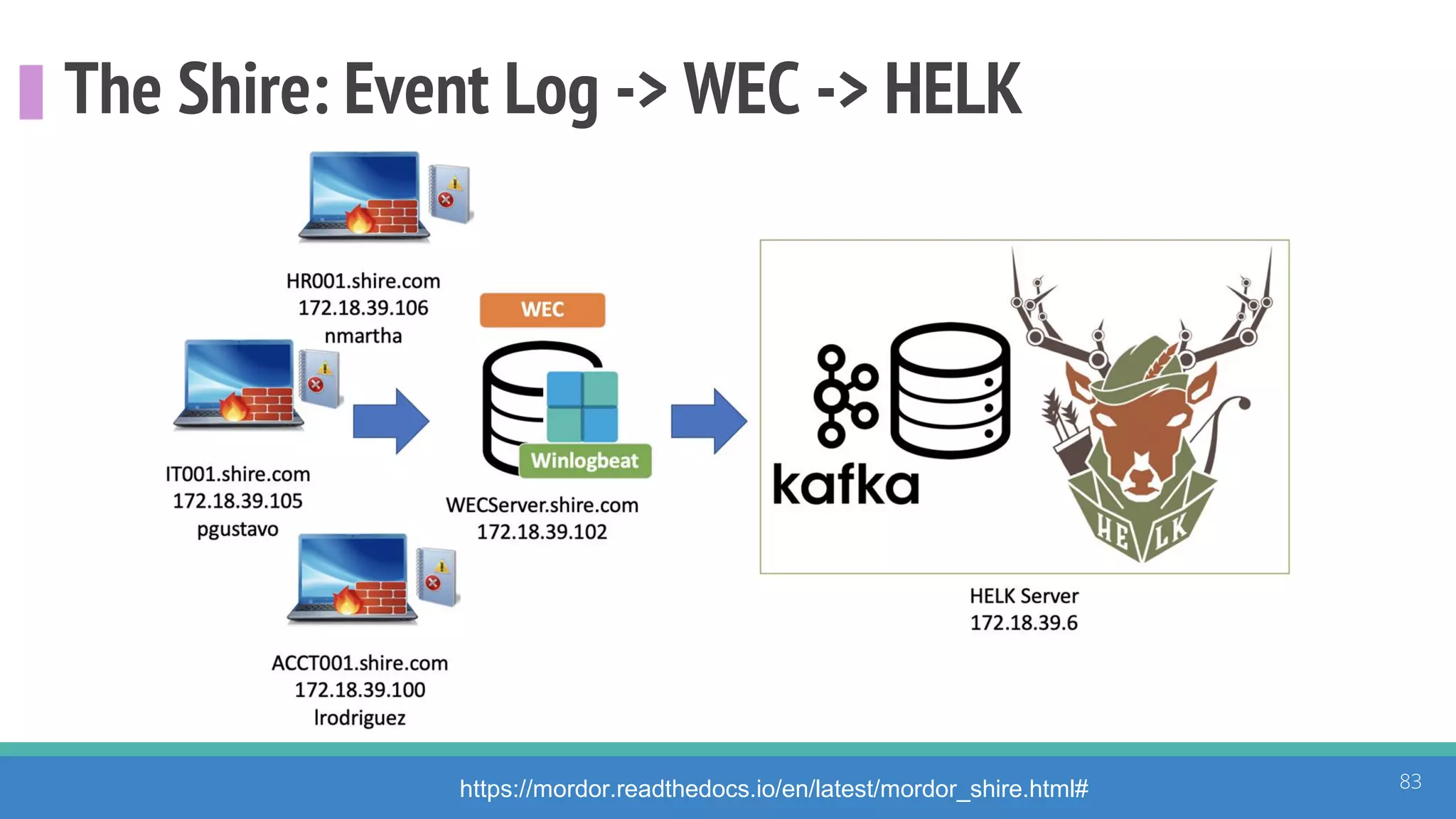
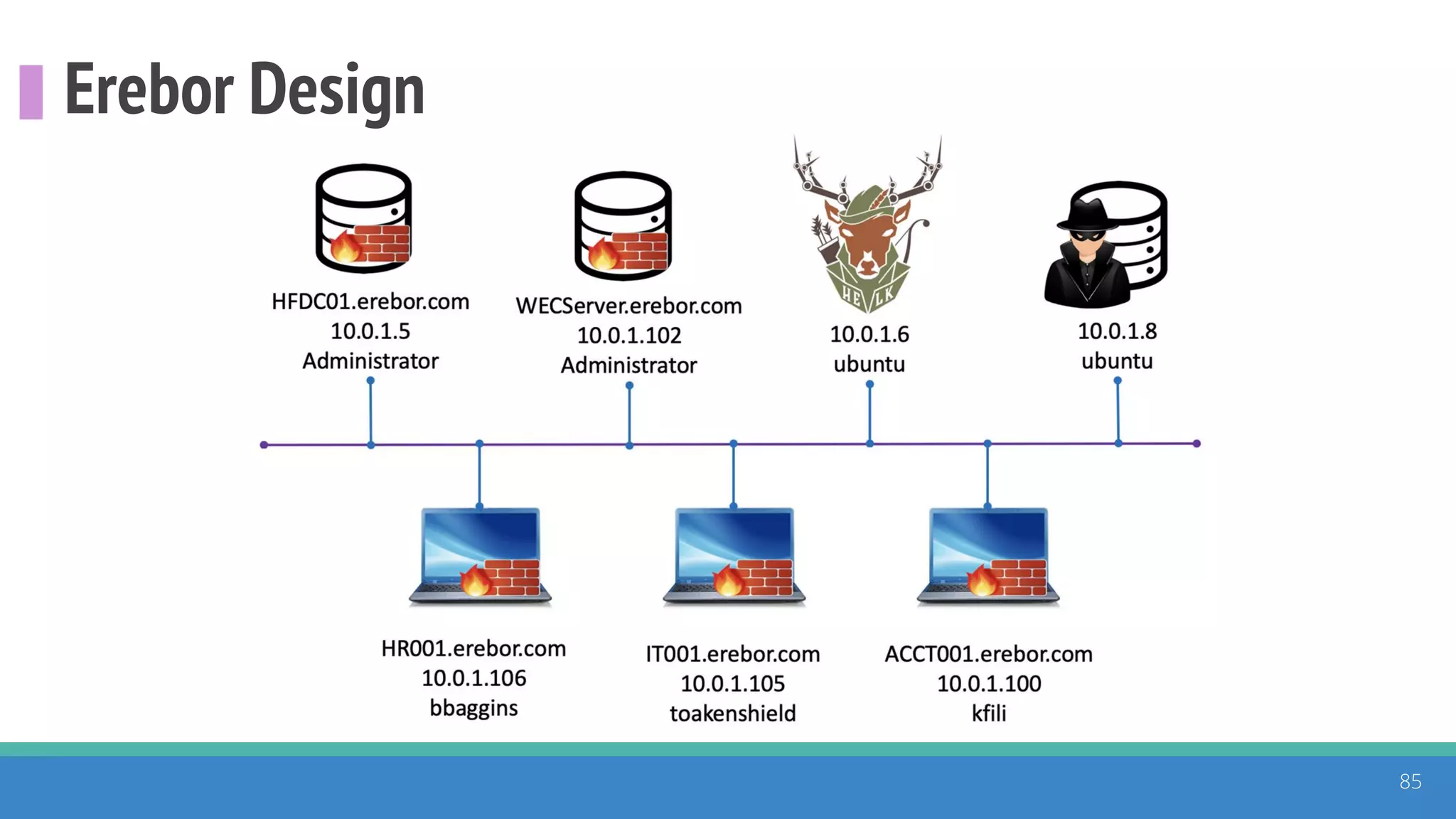
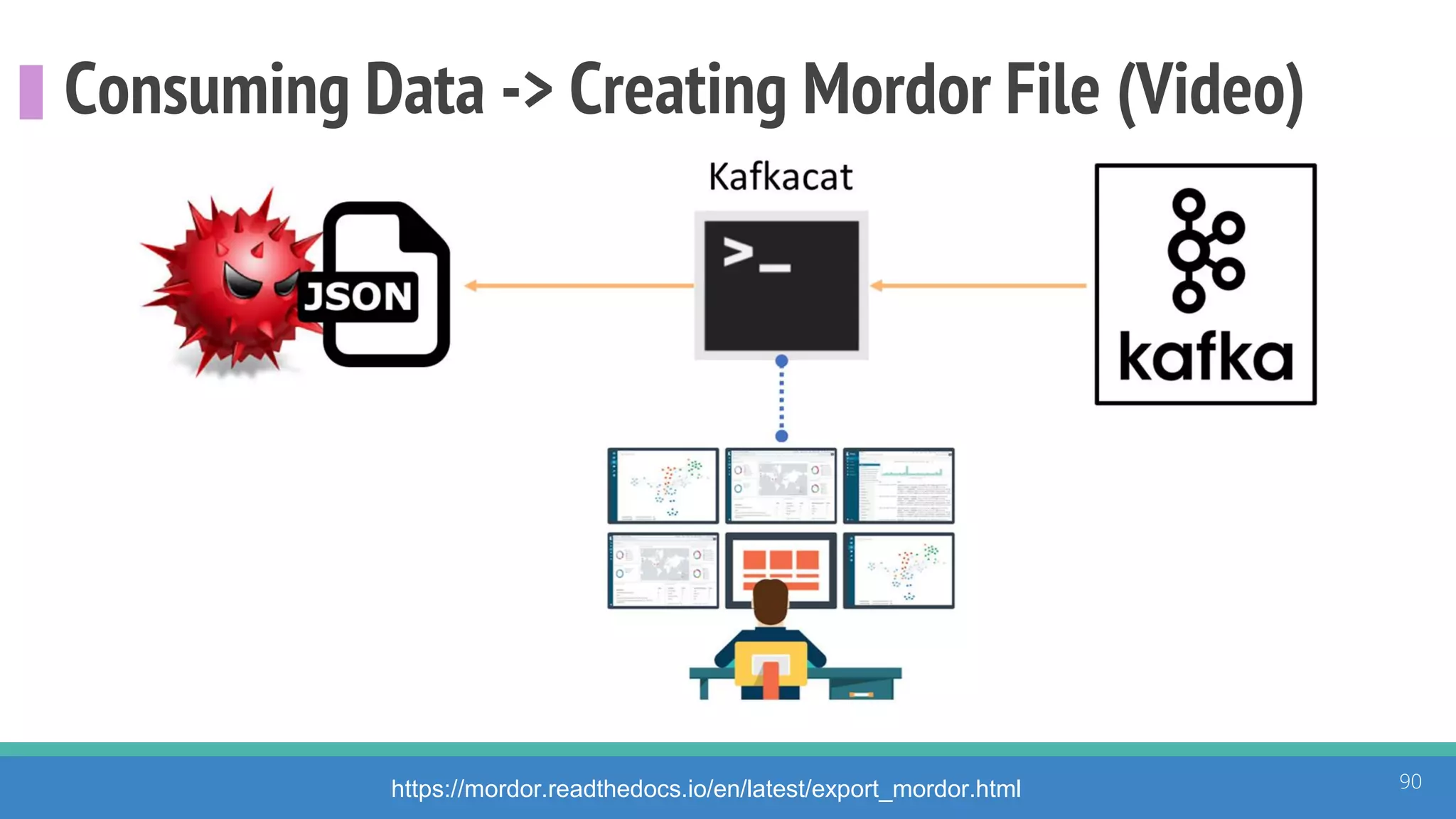
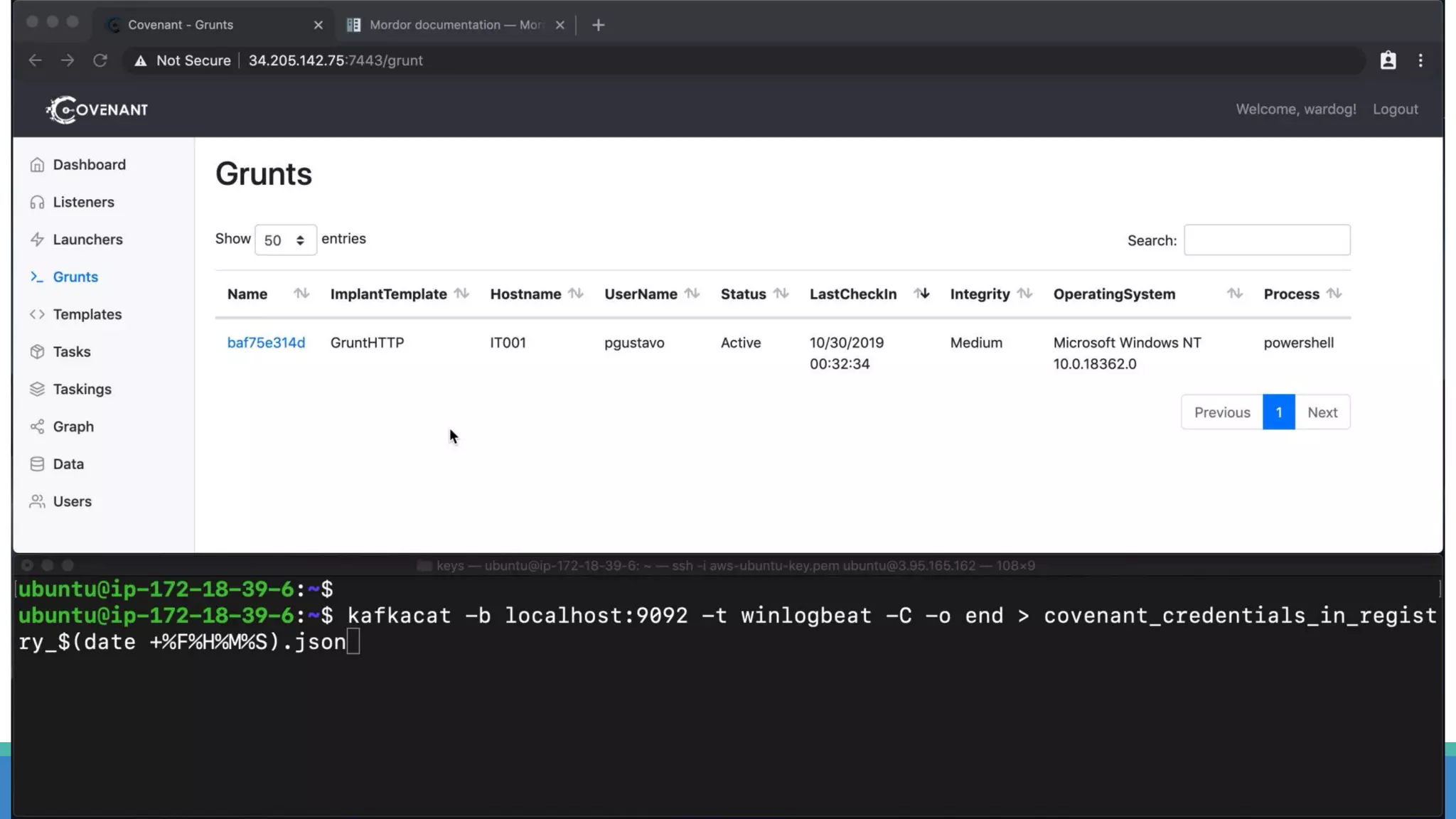
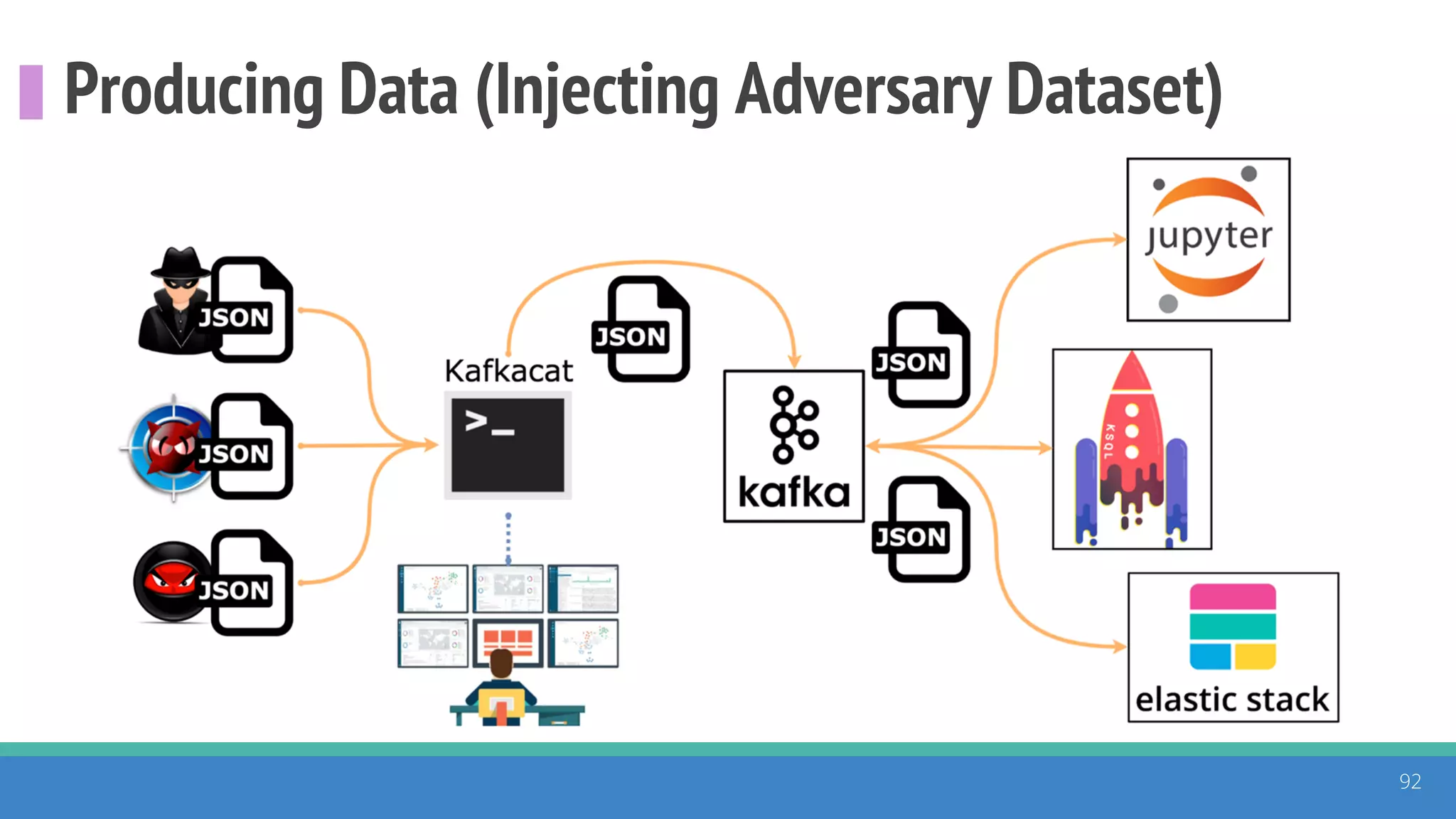
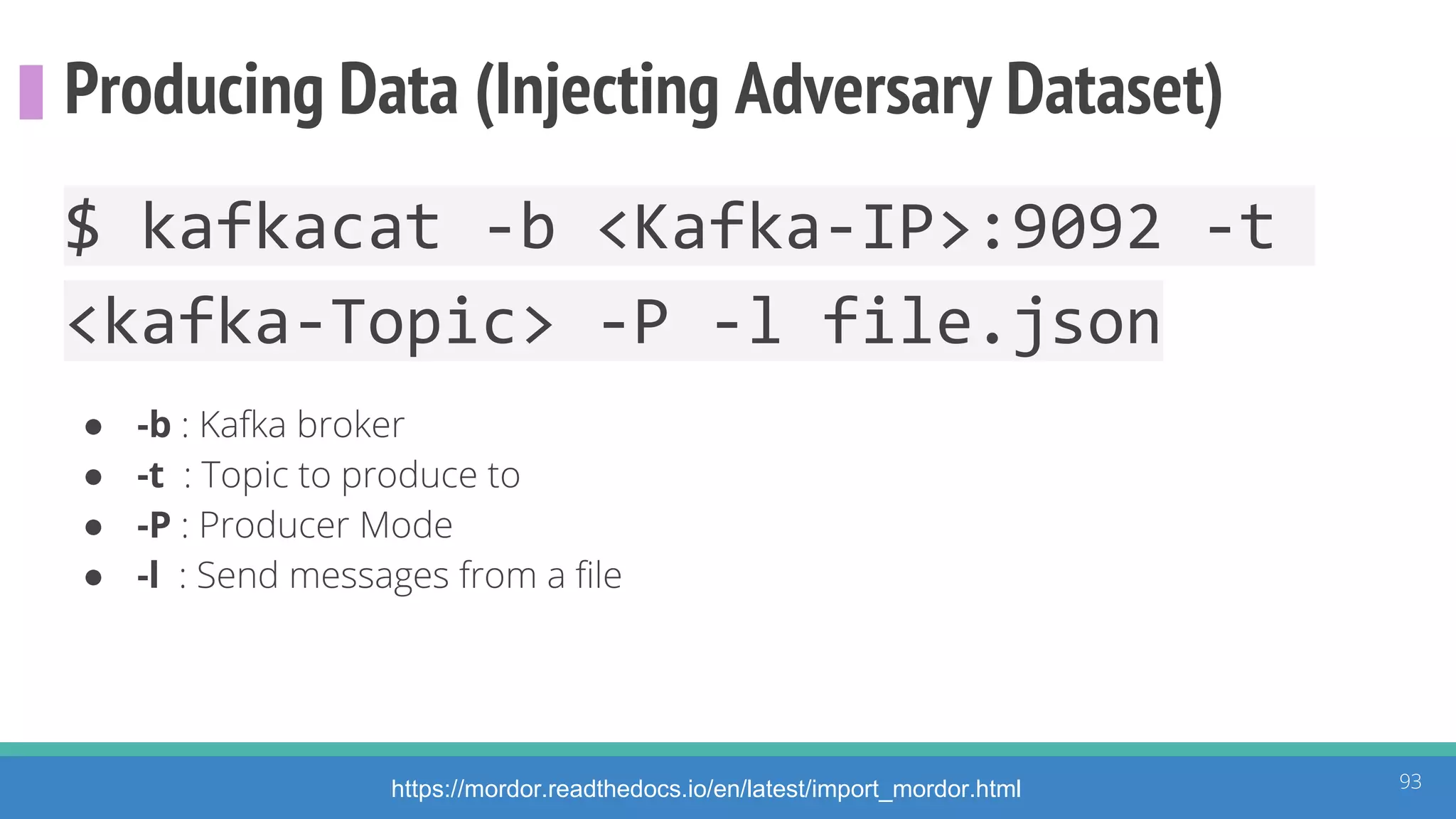
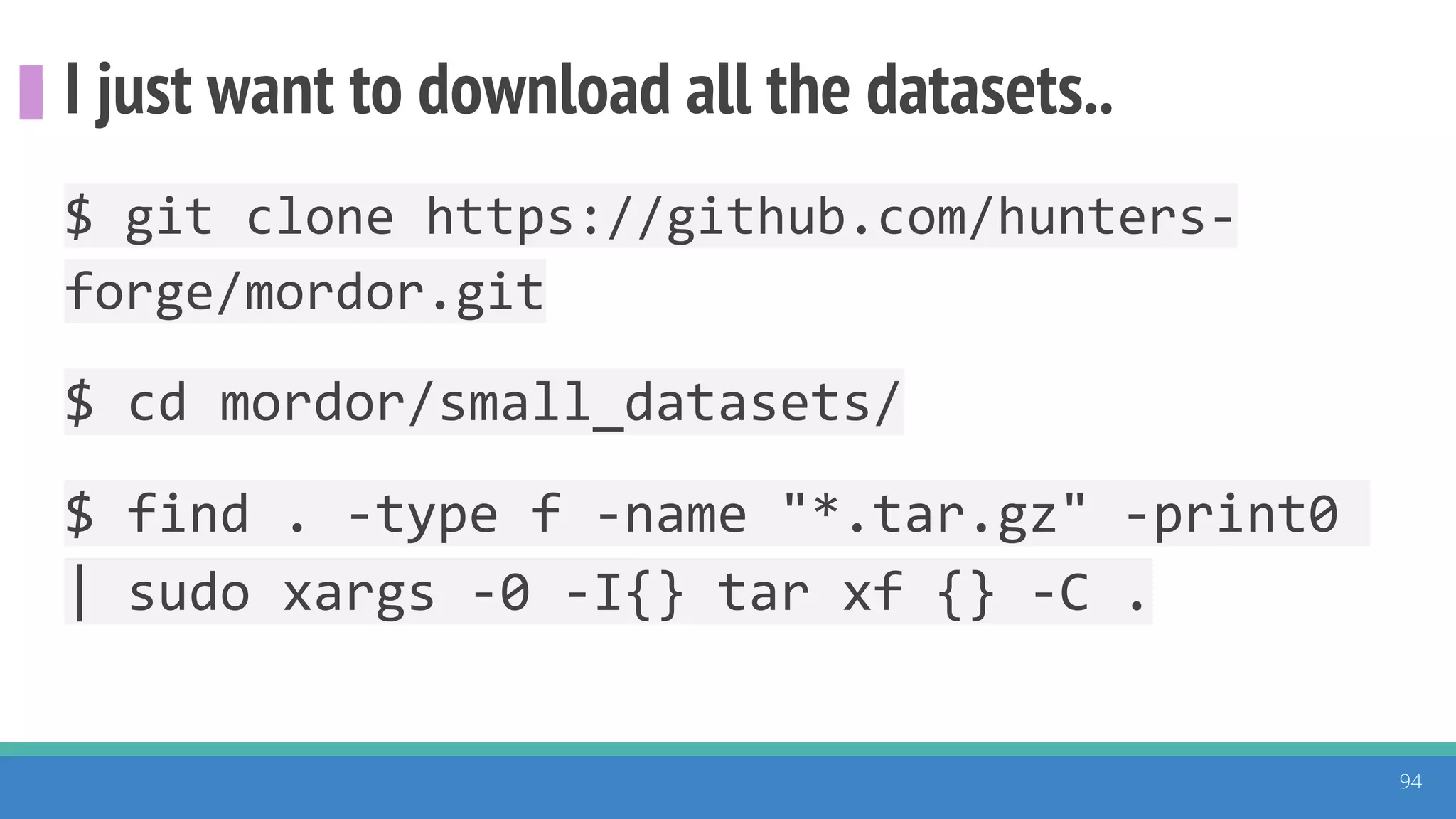
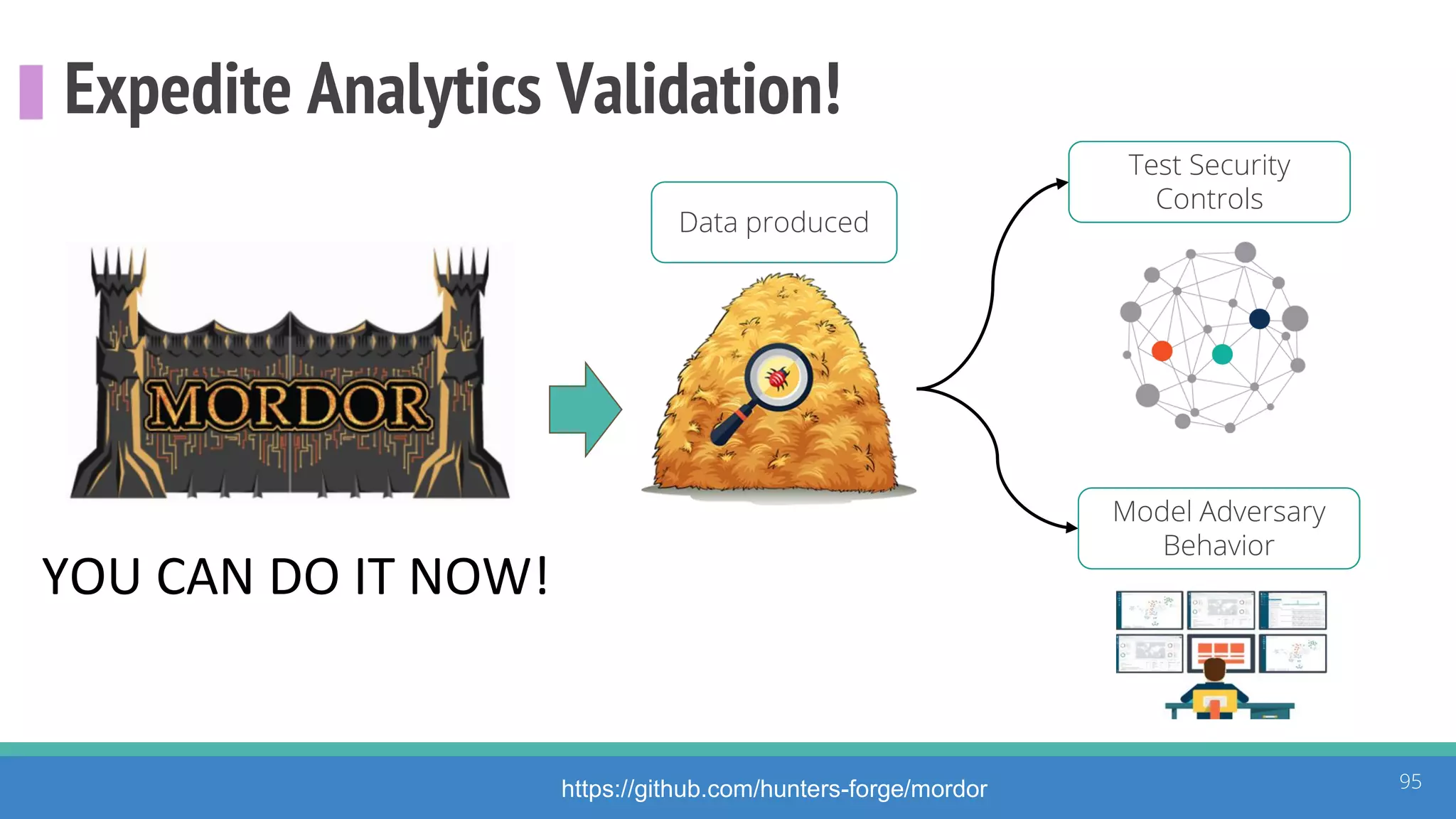
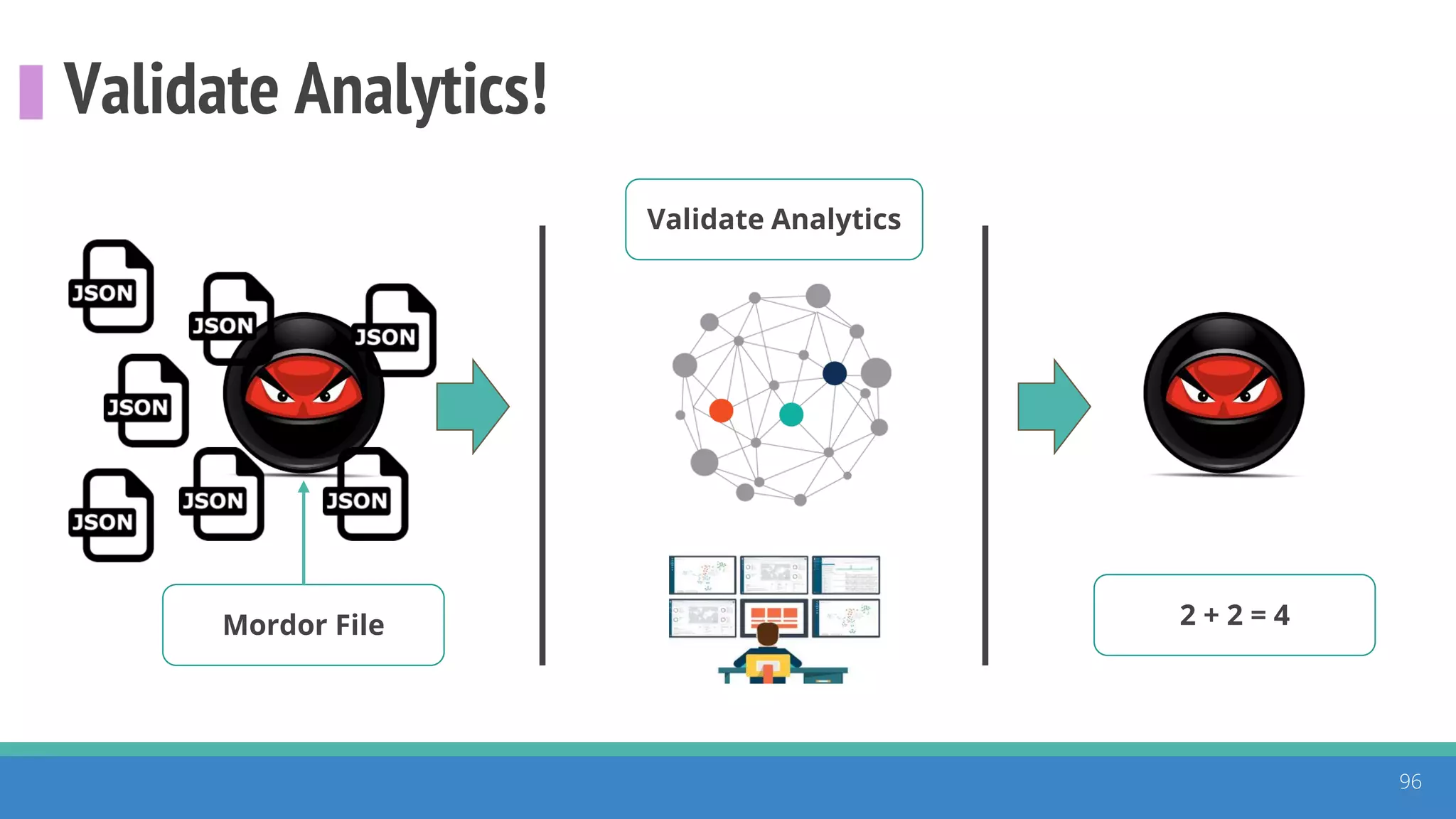
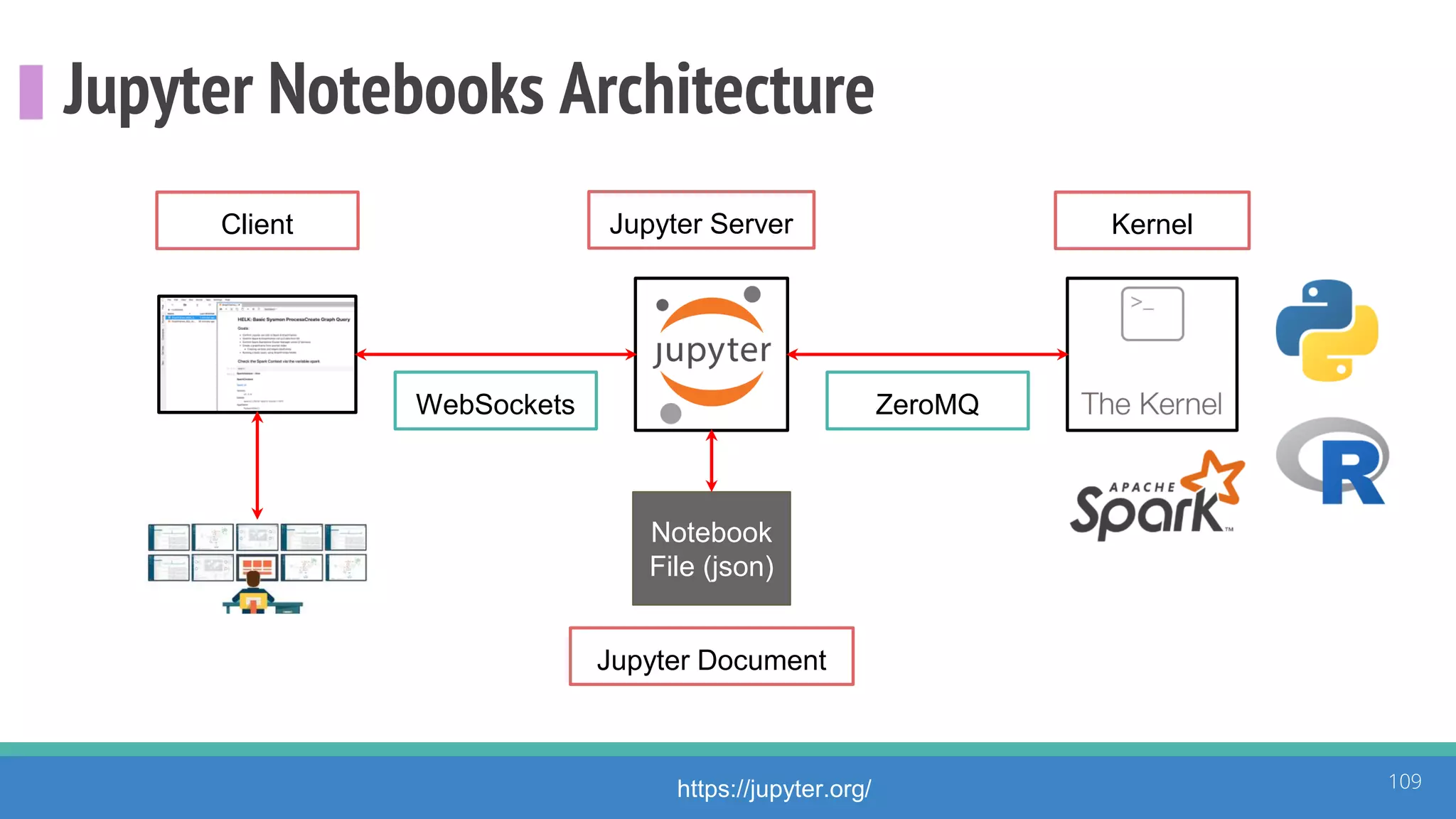
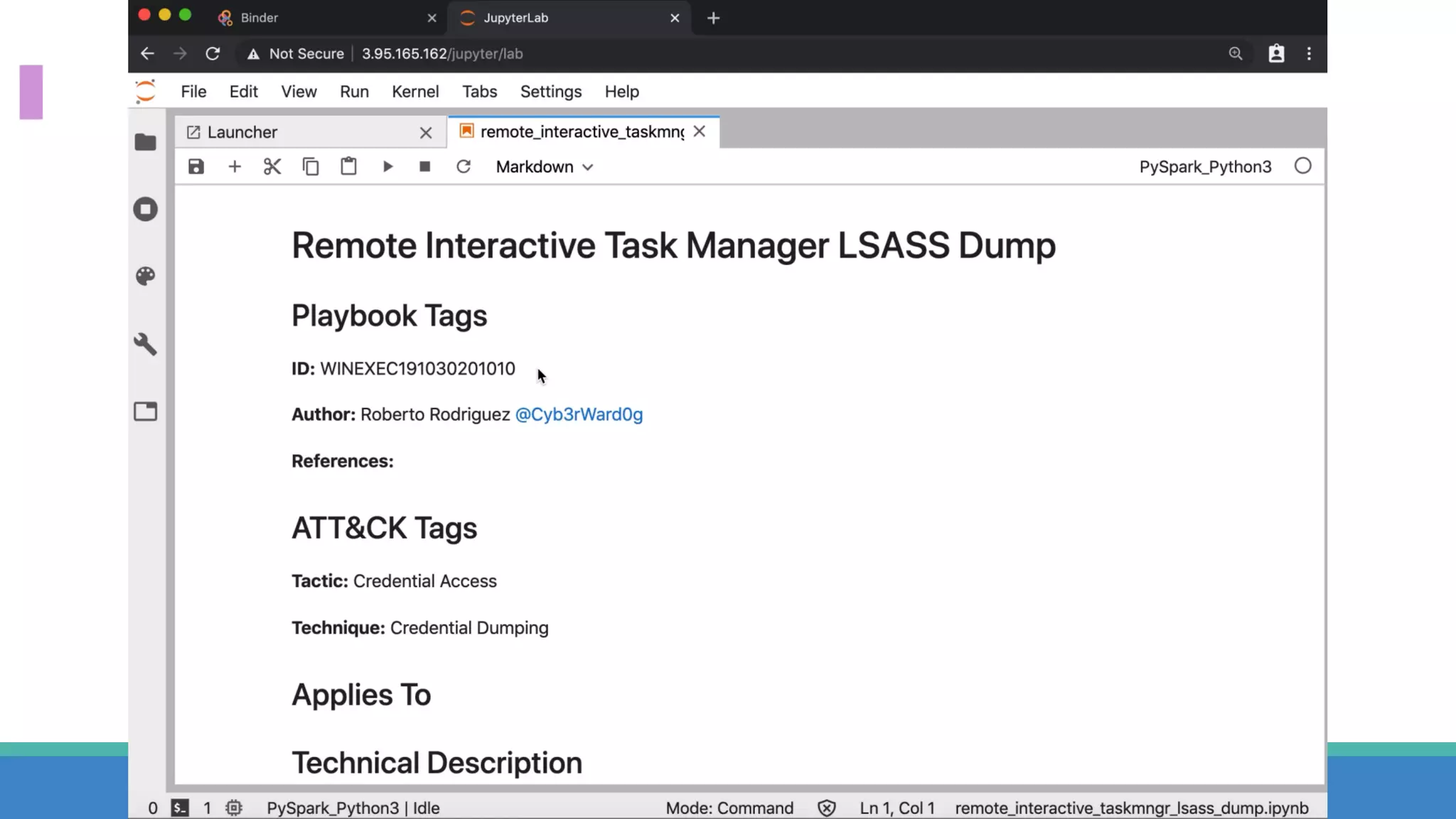
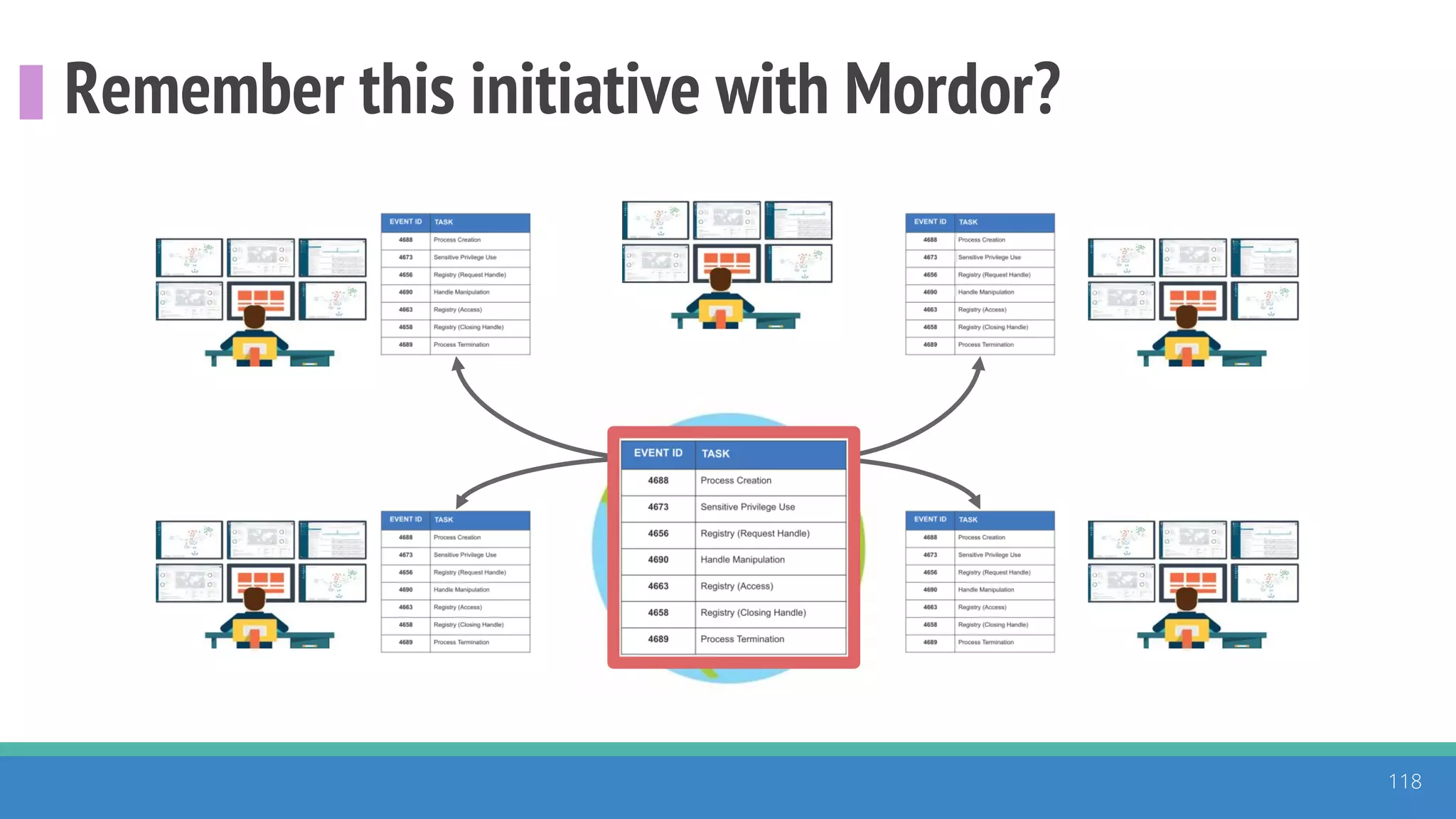
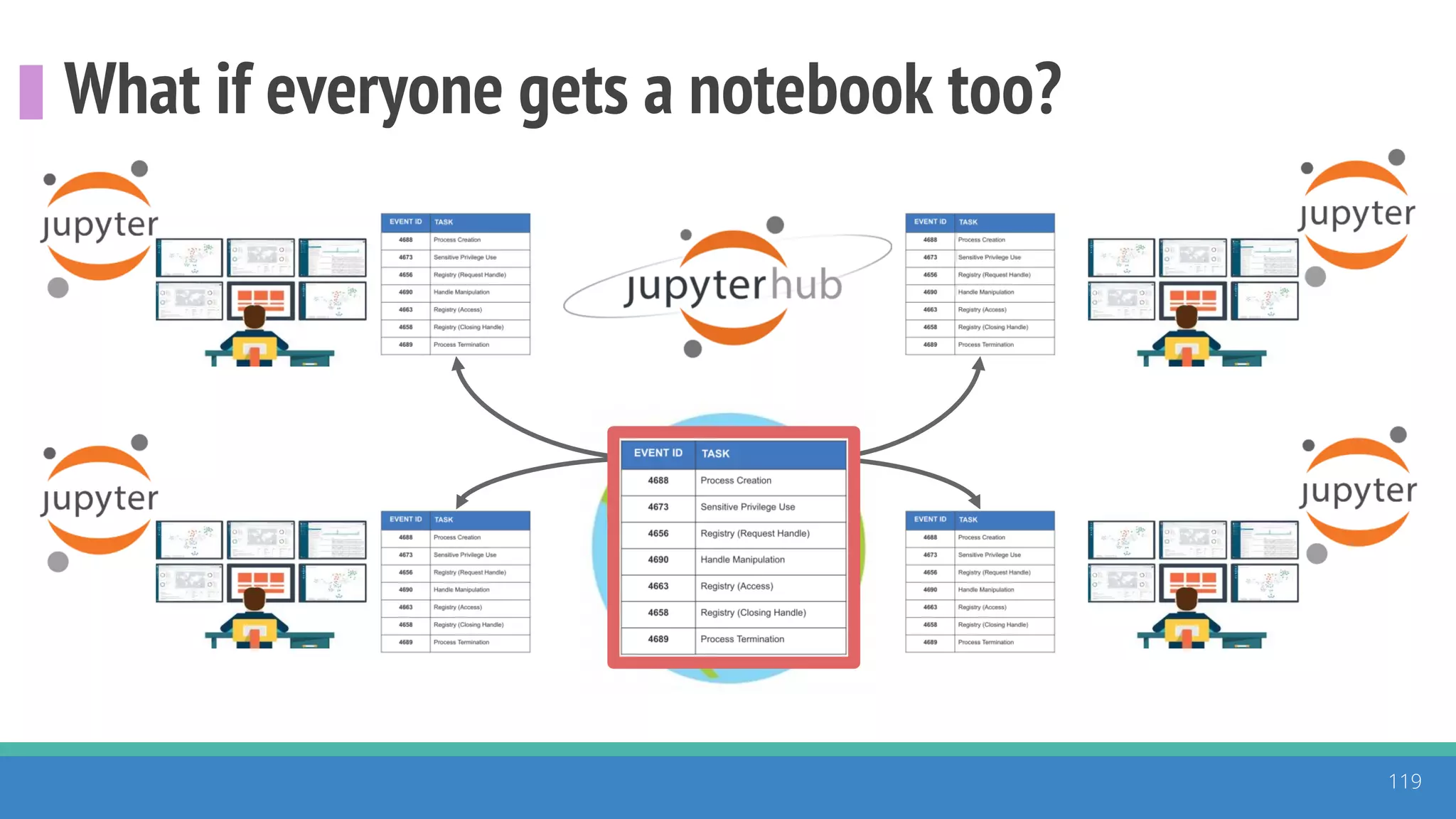
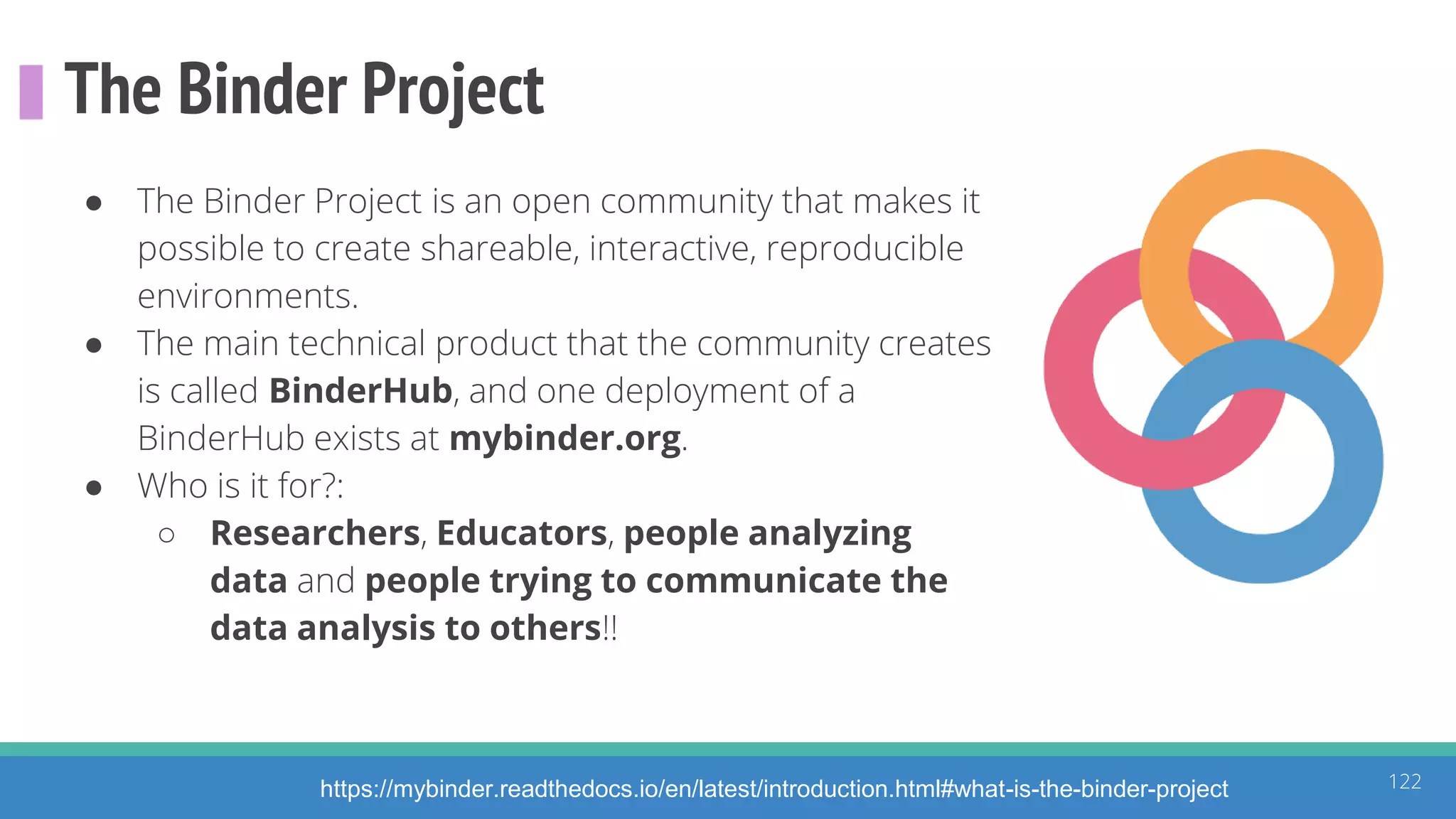
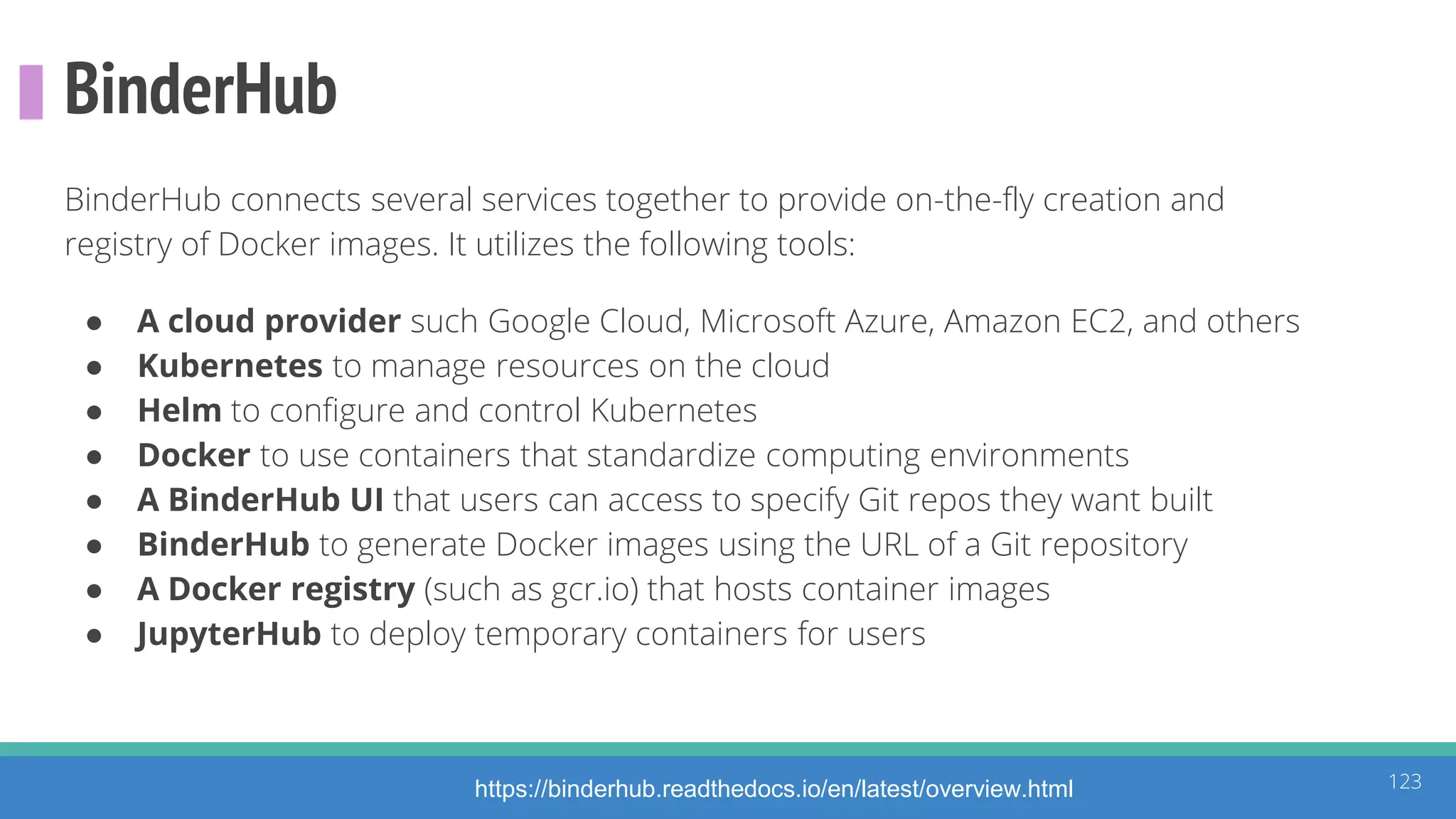
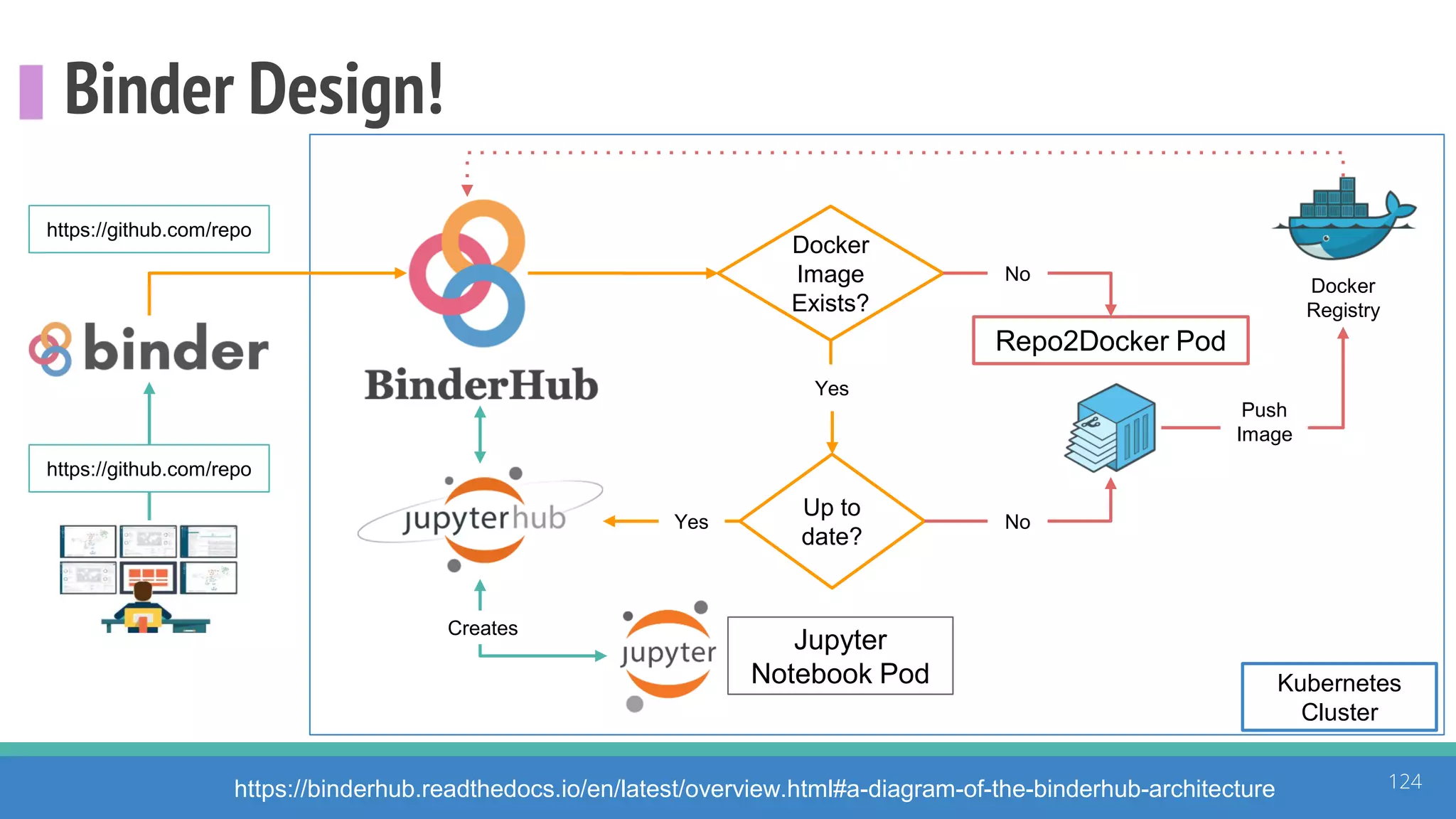
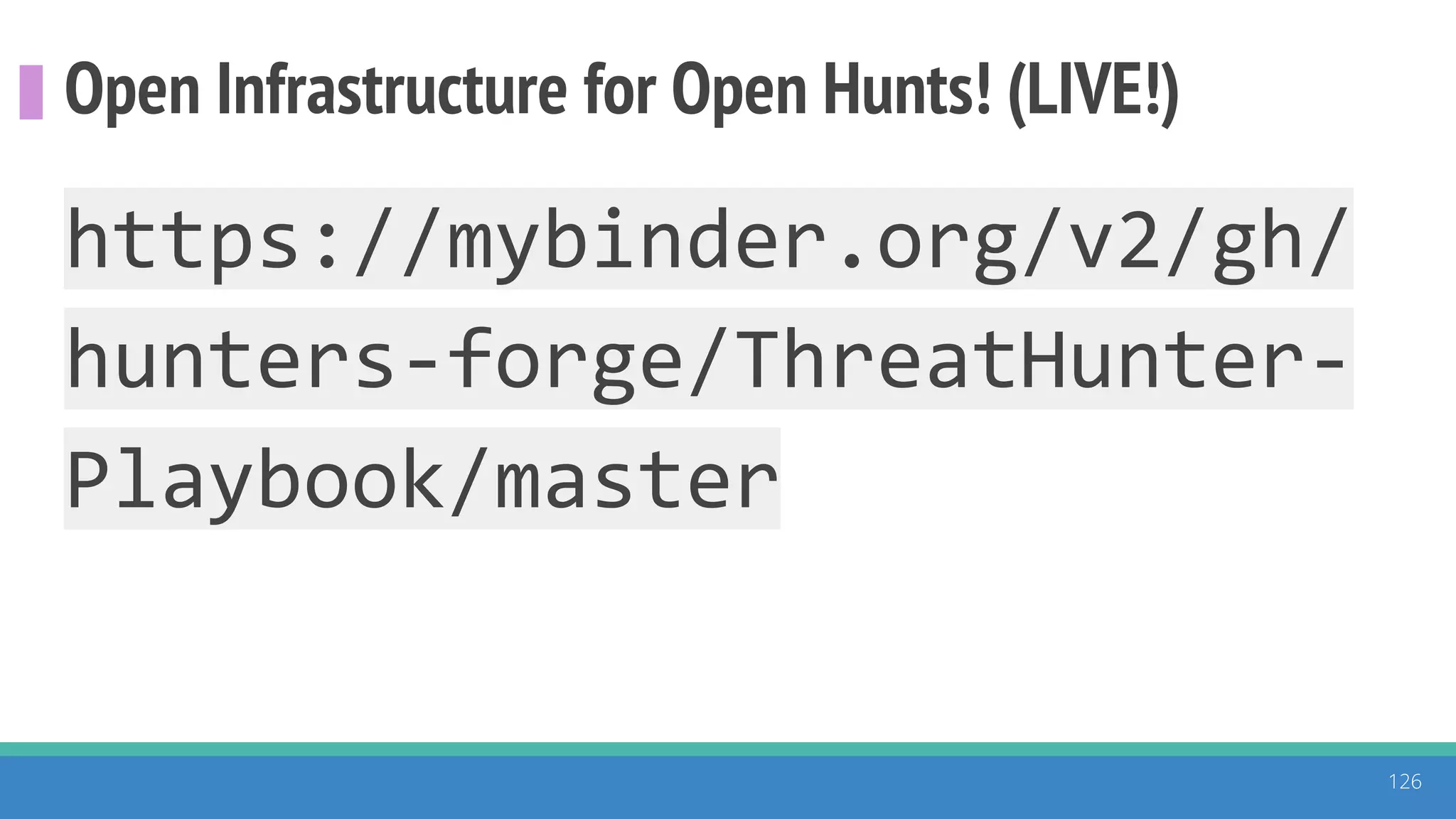
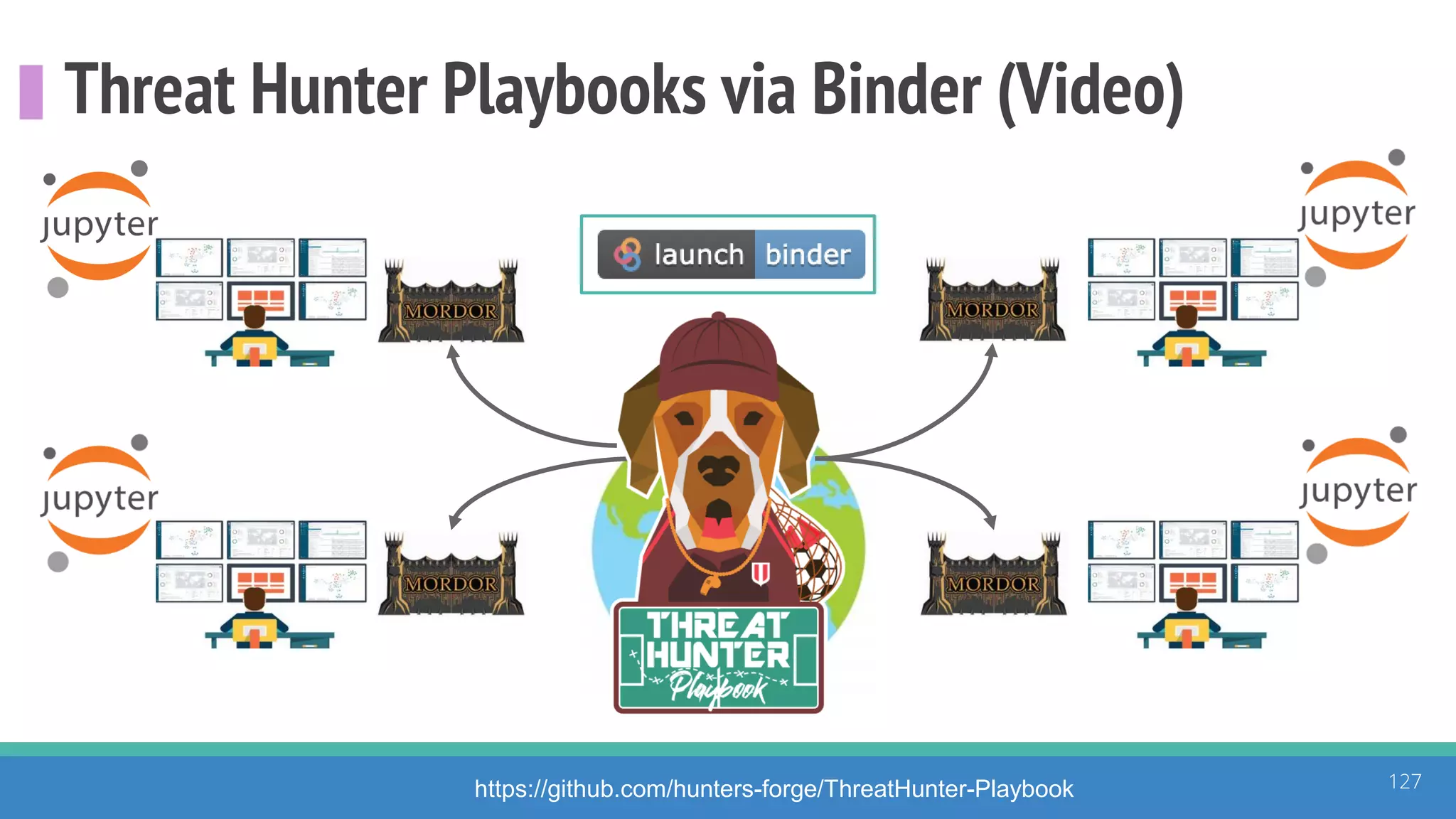
The document discusses the ATT&CK framework, highlighting the use of the ATT&CK data sources to improve security analytics and validation. It emphasizes various projects such as the ATT&CK Python client and the Mordor project, which simulate adversarial techniques with pre-recorded security events. Collaboration and opportunities for data source improvements are also explored, alongside recommendations for validating data analytics in security environments.