Embed presentation
Download as PDF, PPTX


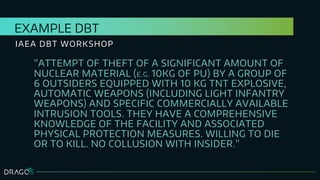
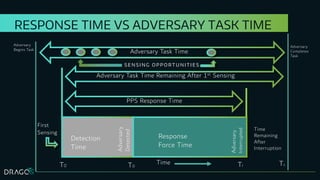

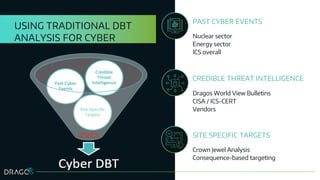

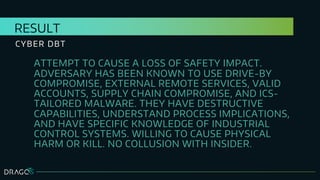


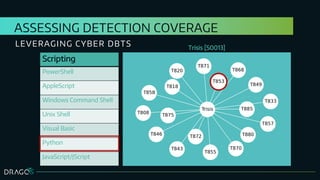

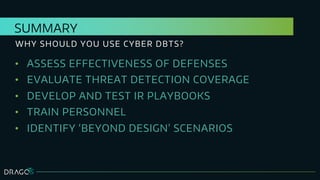

The document discusses the application of design basis threats (DBTs) in cybersecurity, particularly for the nuclear sector. It emphasizes the importance of understanding potential cyber threats, developing DBTs, and employing effective risk mitigation measures, along with specific examples and methodologies. Key concepts include adversary emulation, threat behavior analysis, and coverage assessment for both mitigation and detection strategies.














