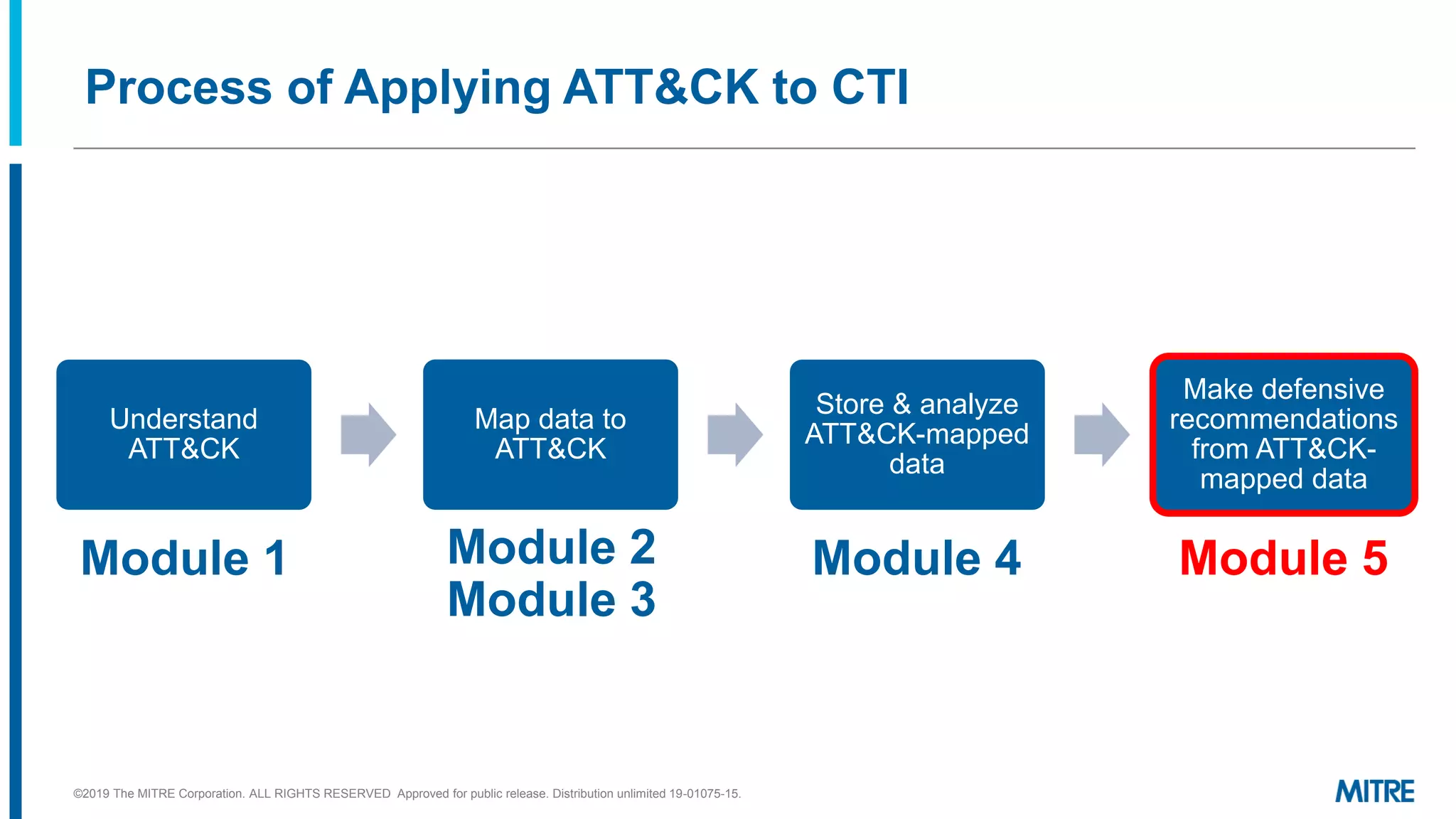
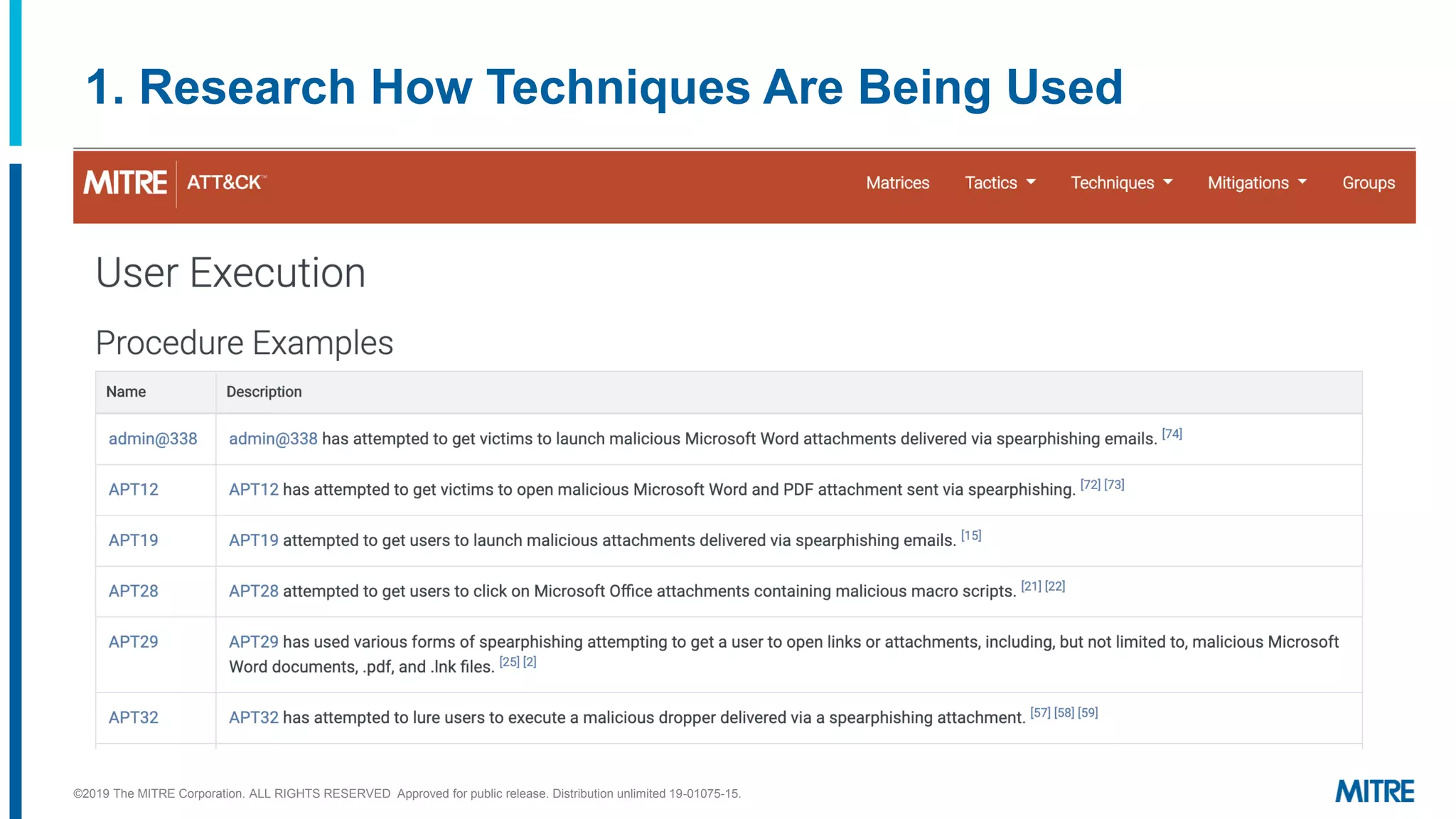
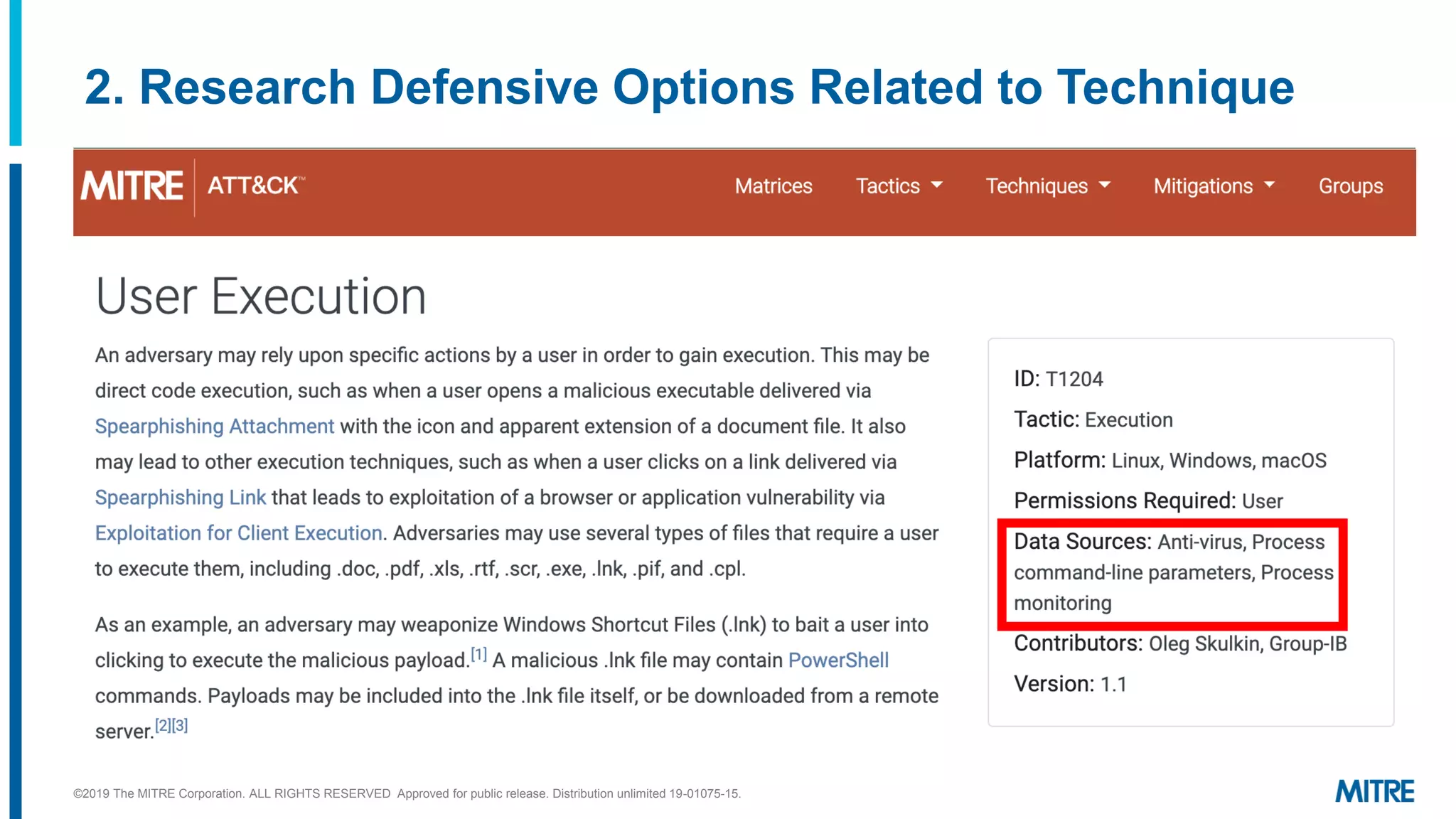
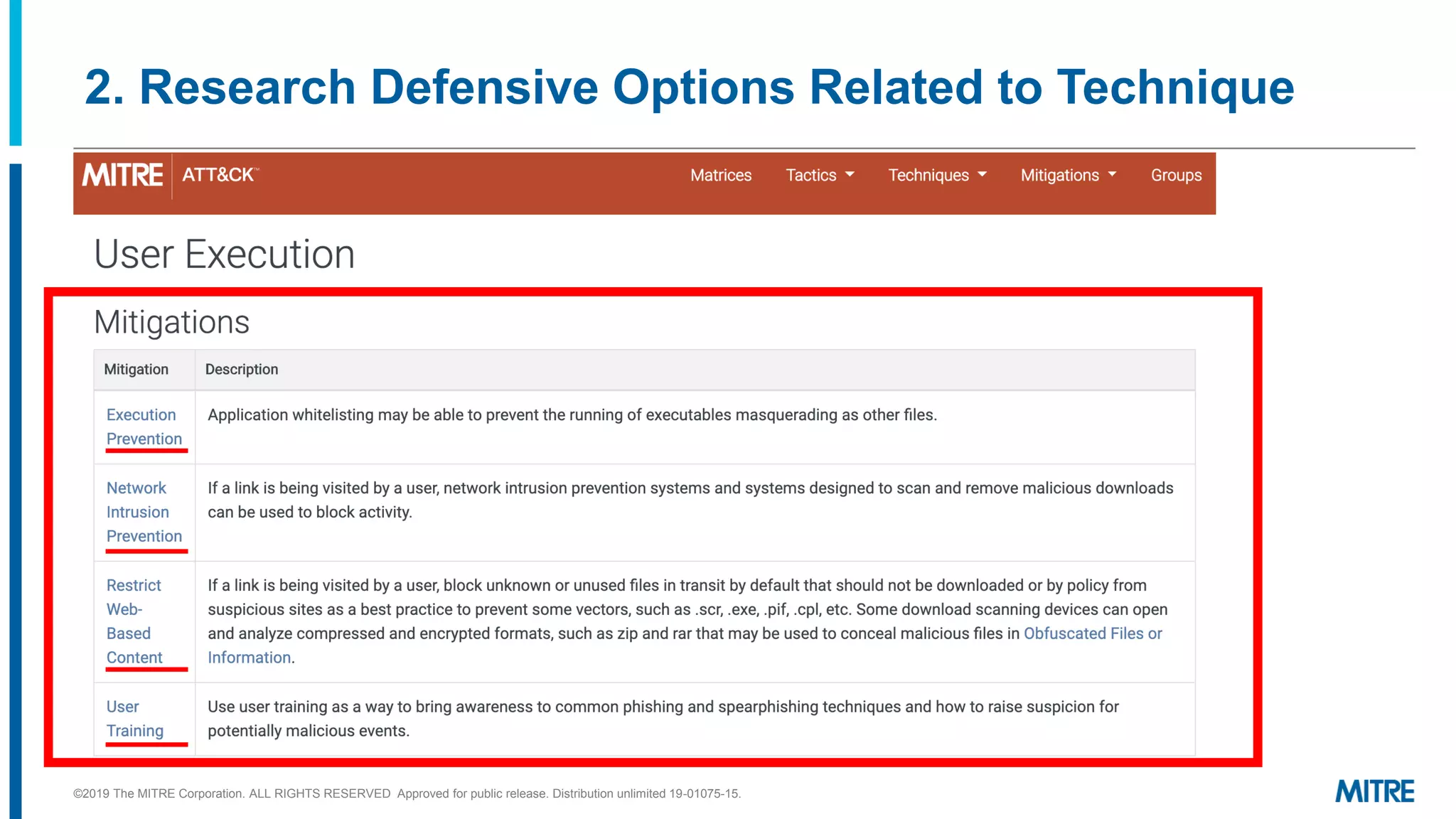
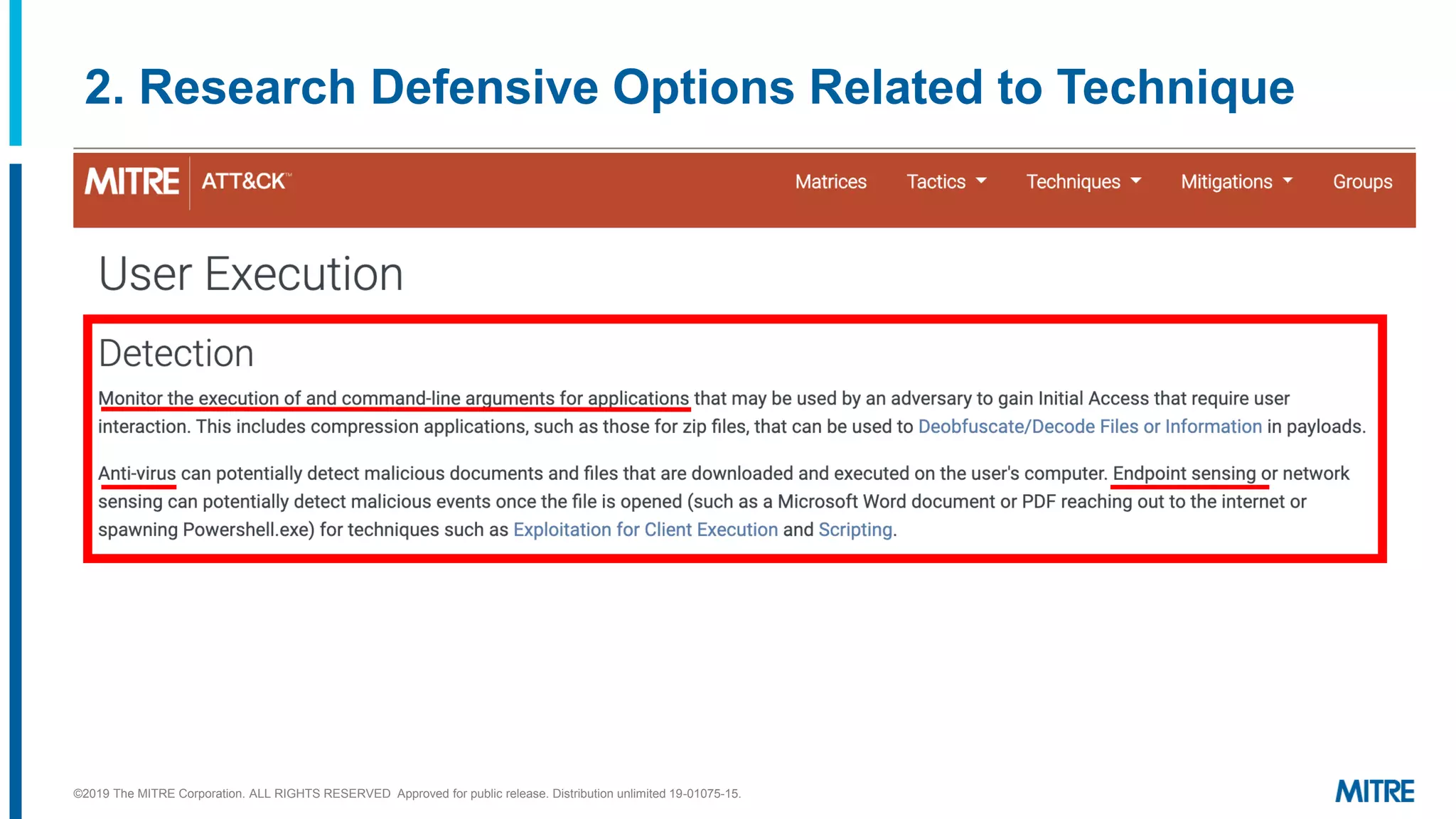
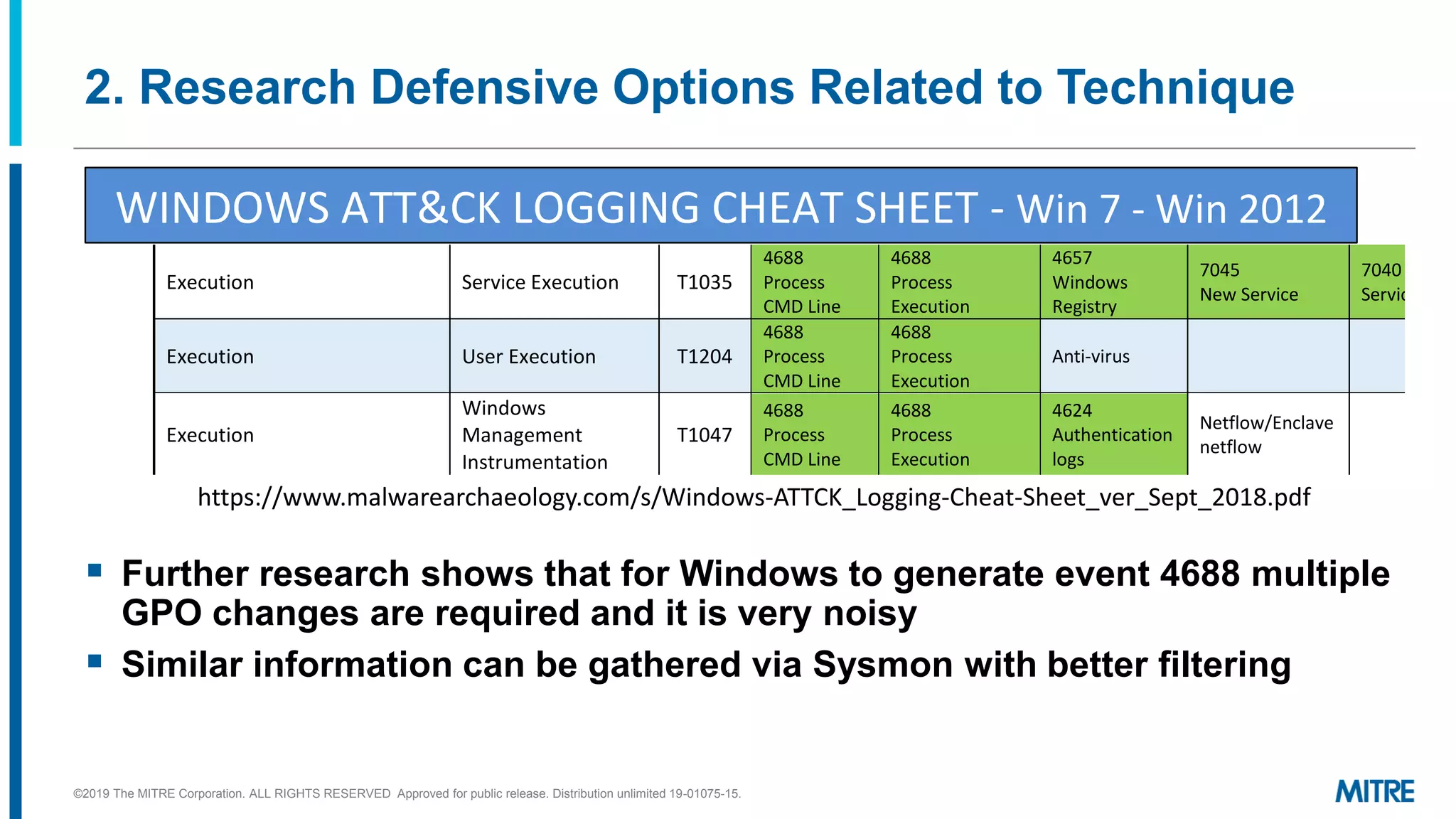
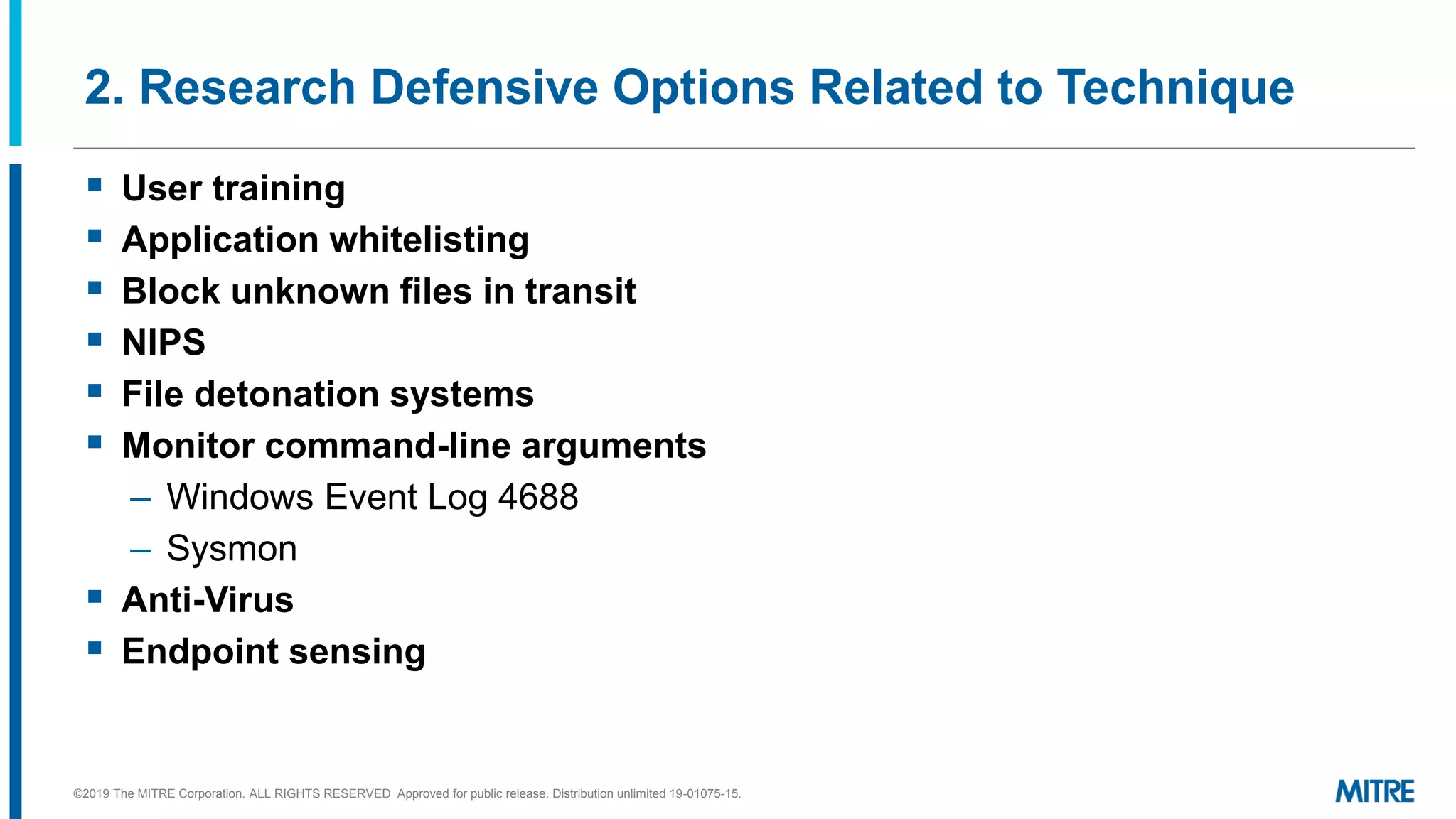
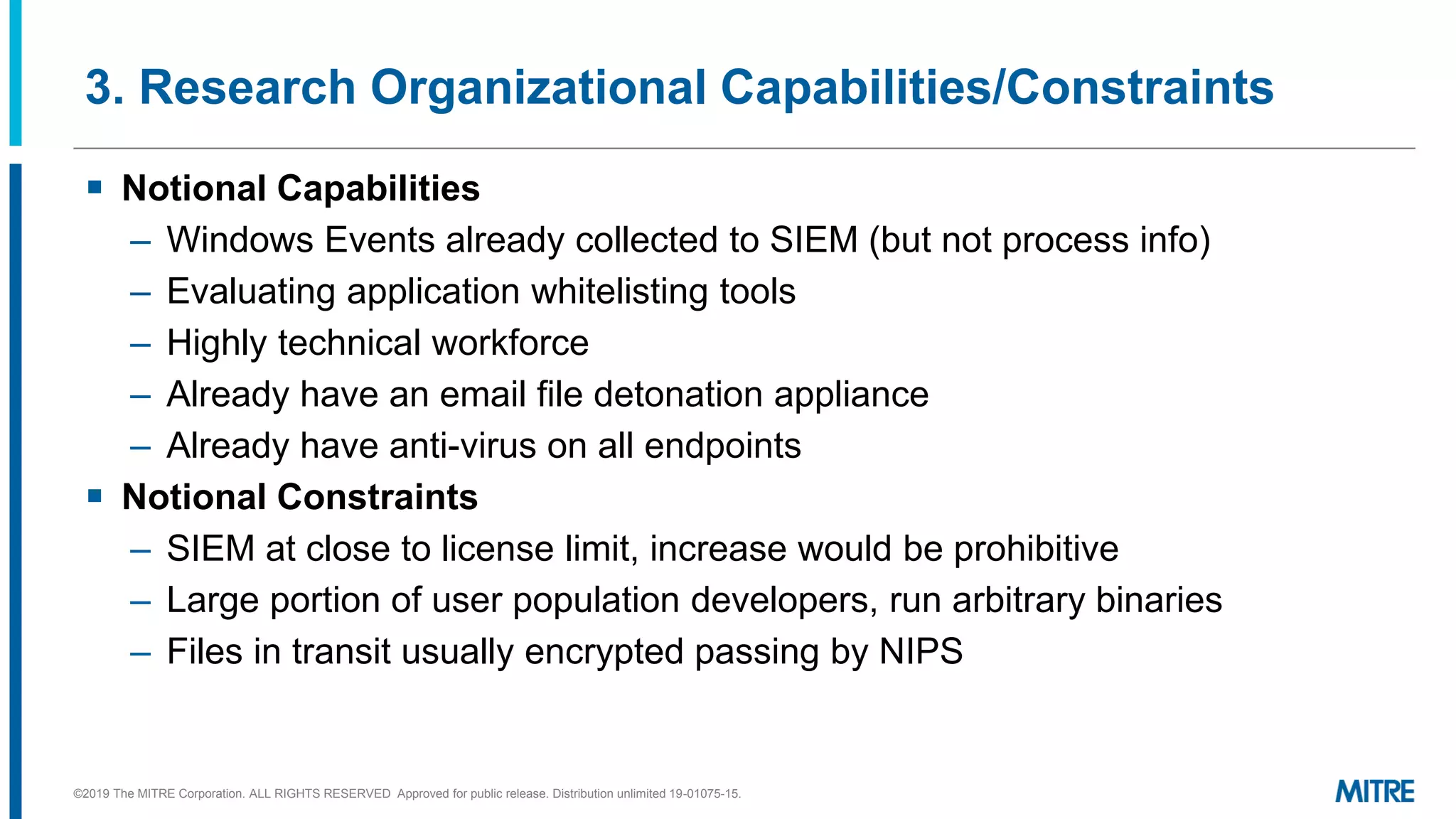
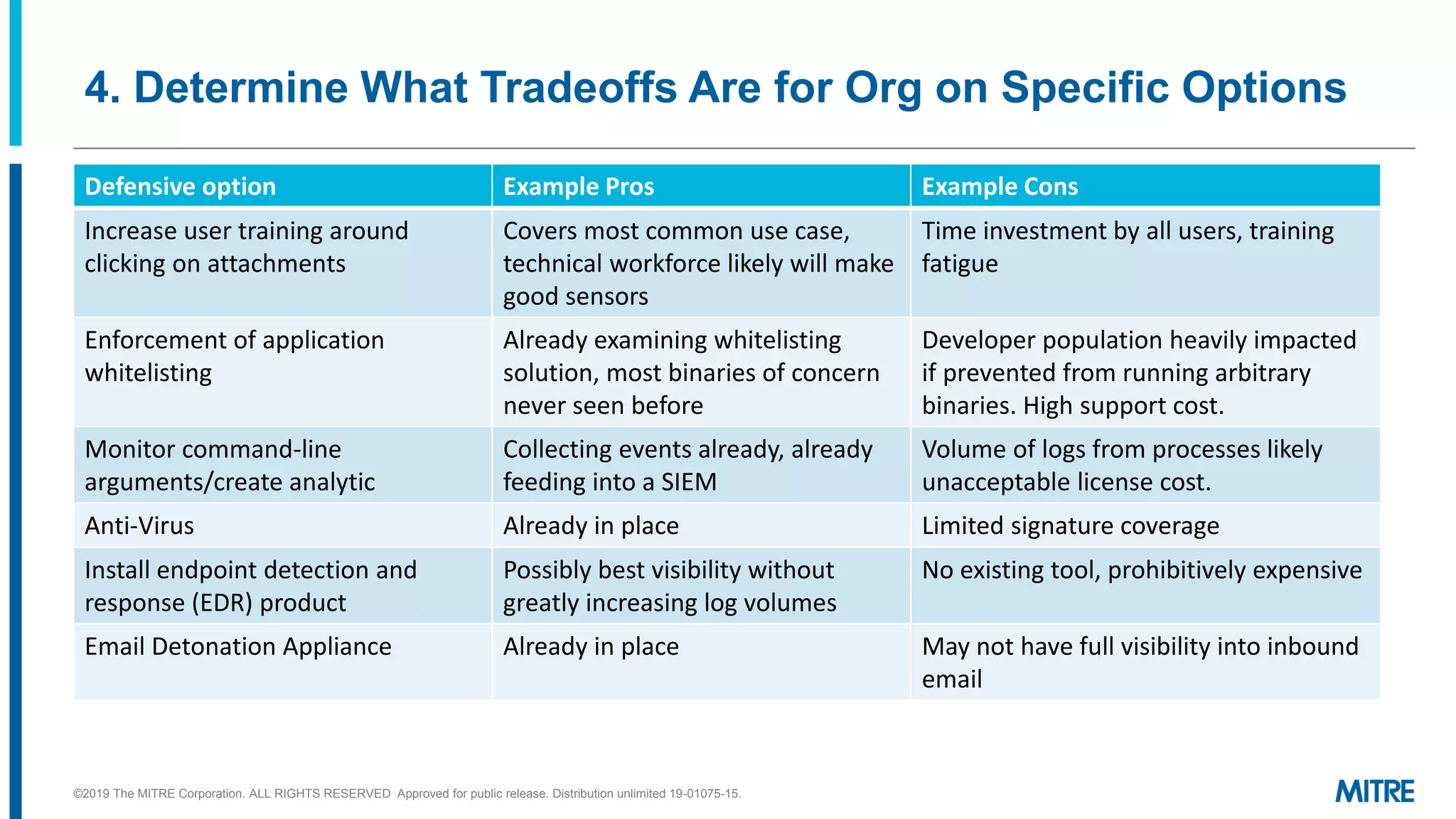
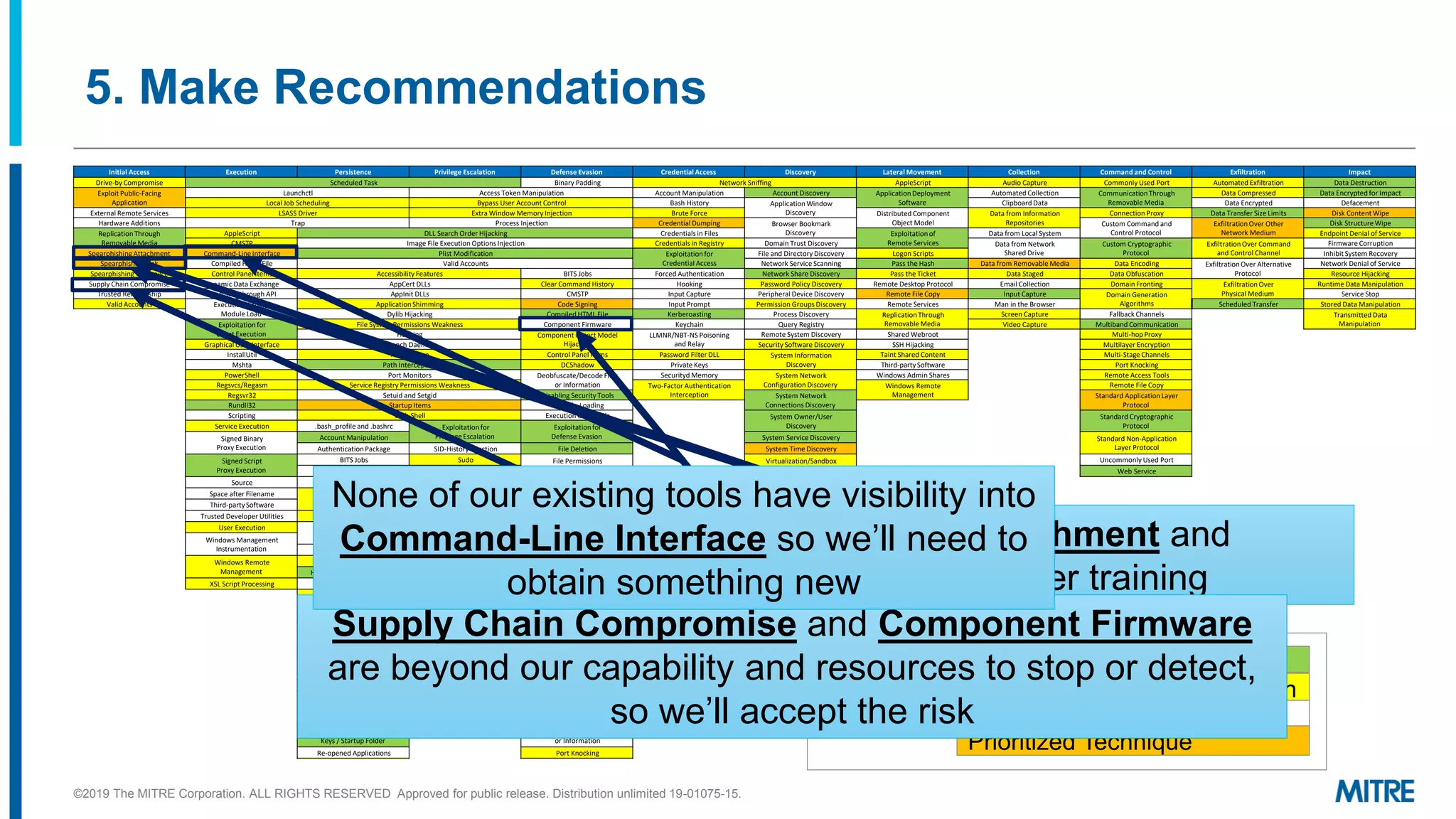
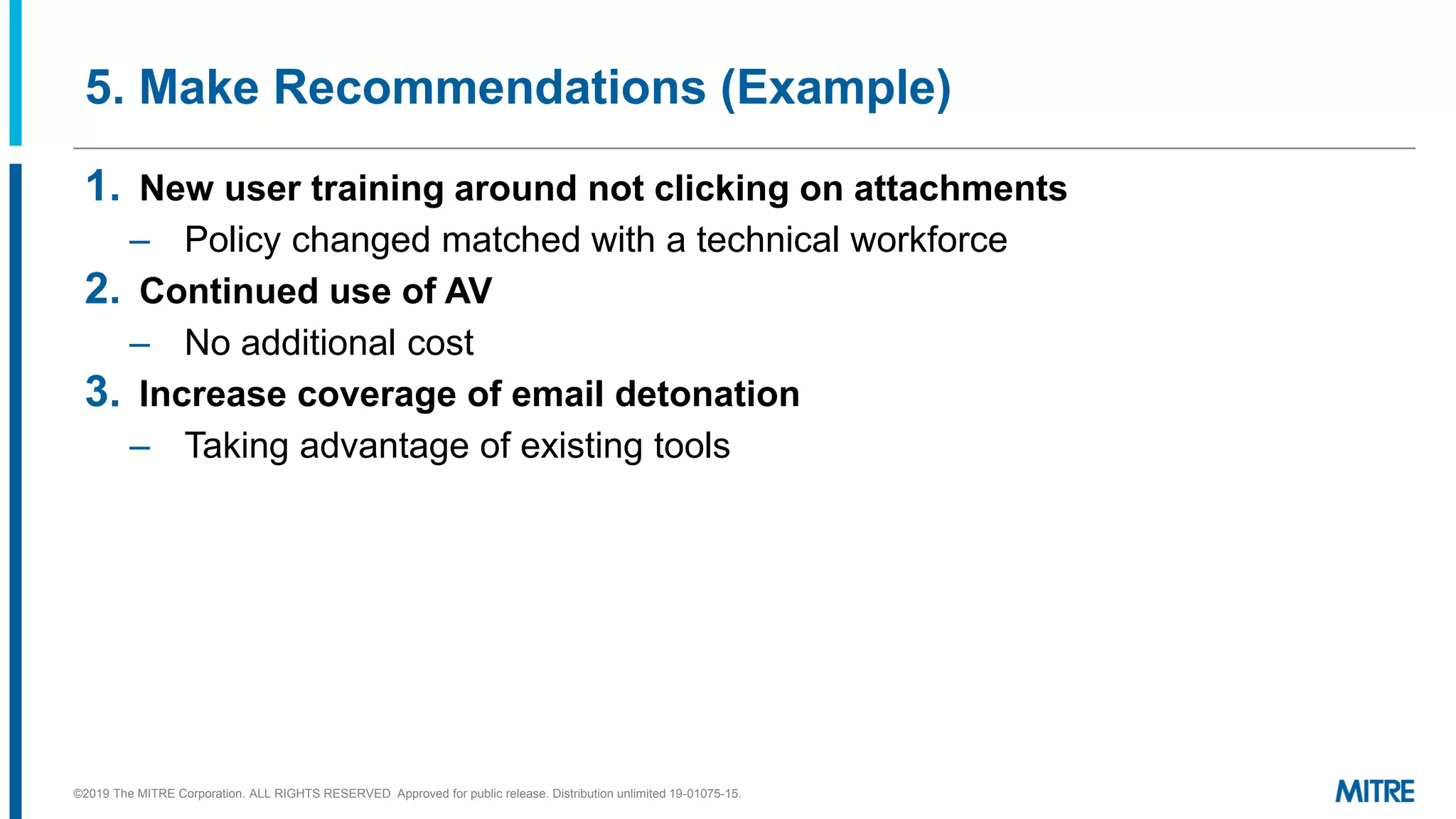
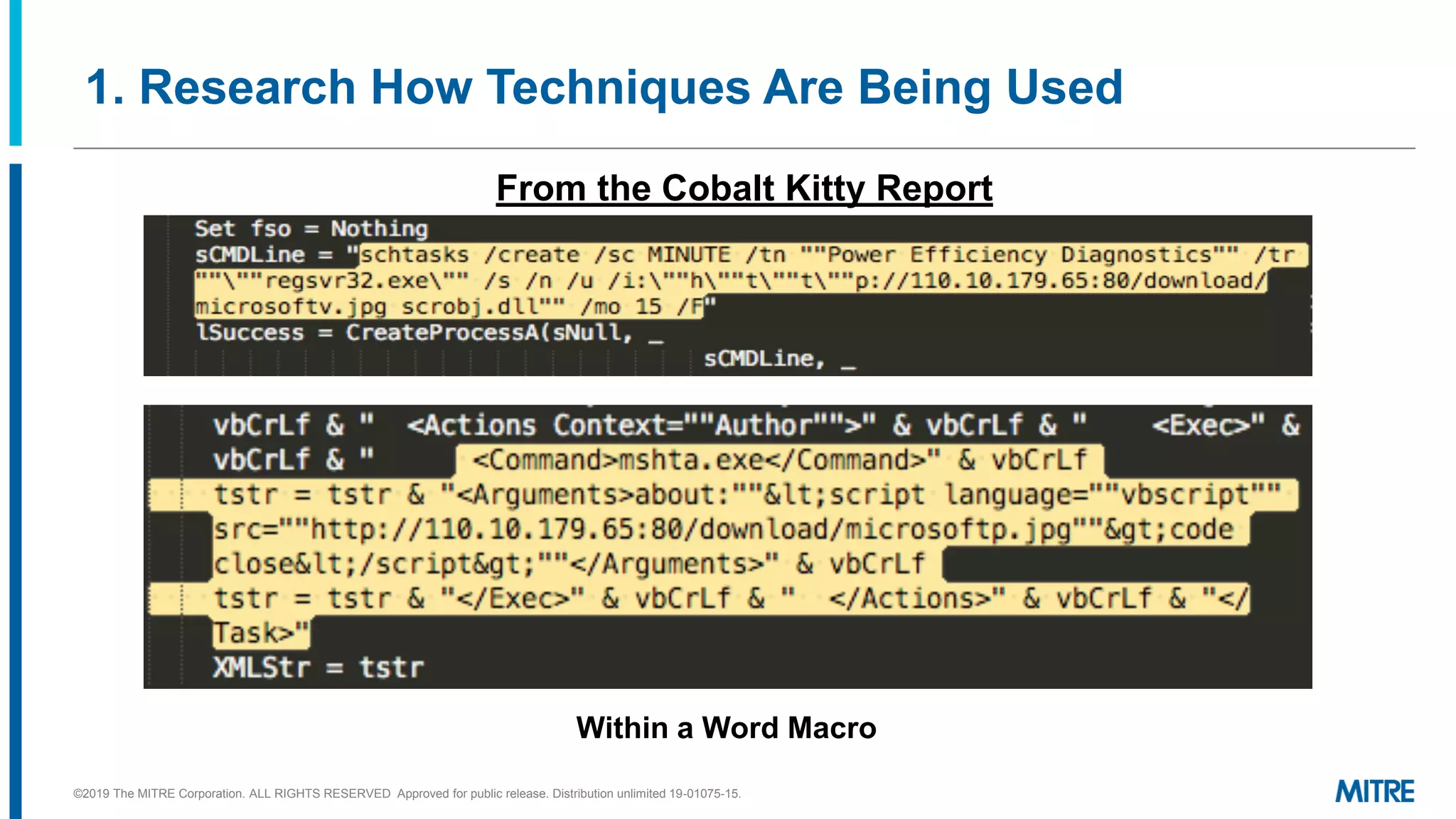
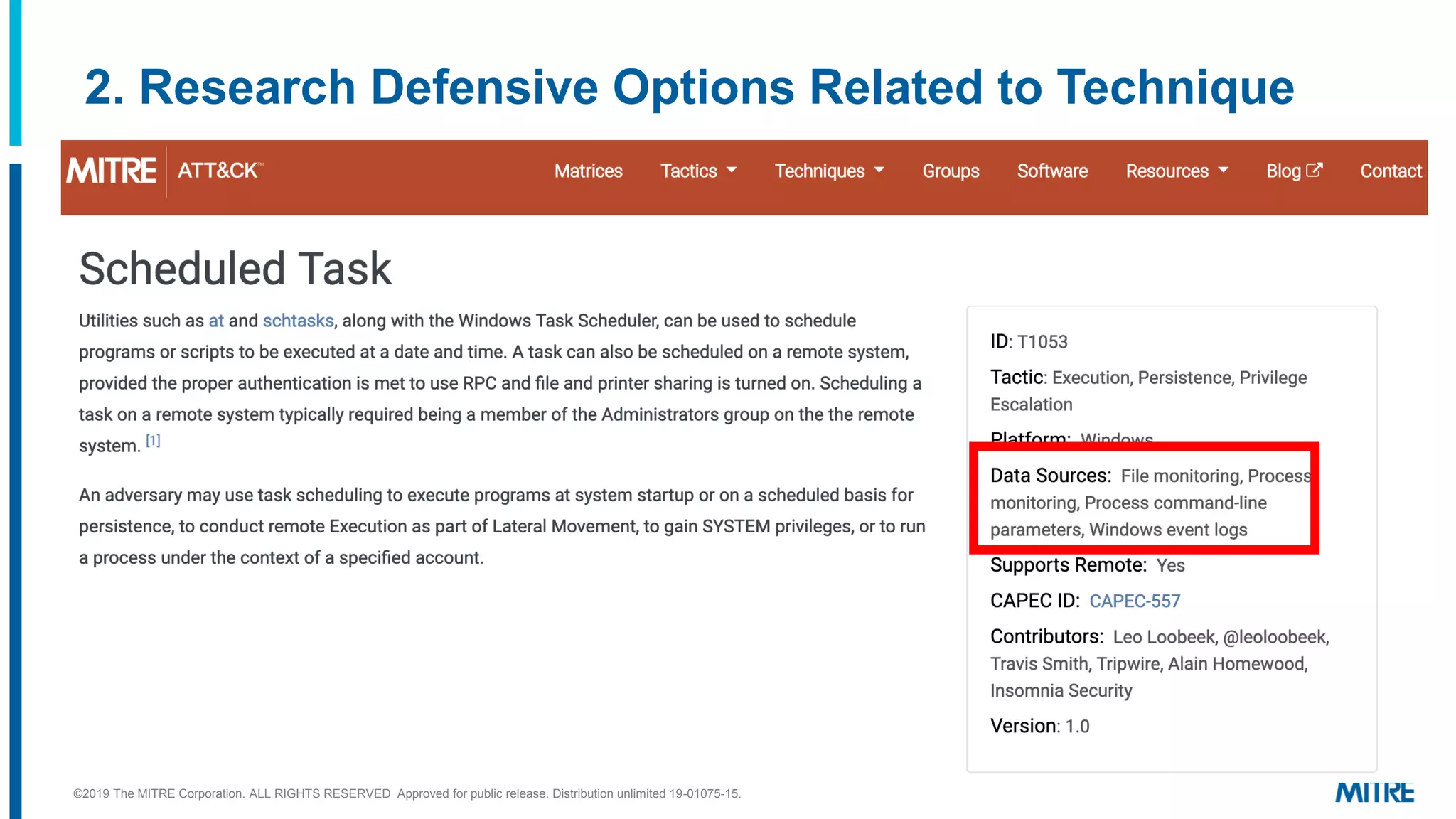
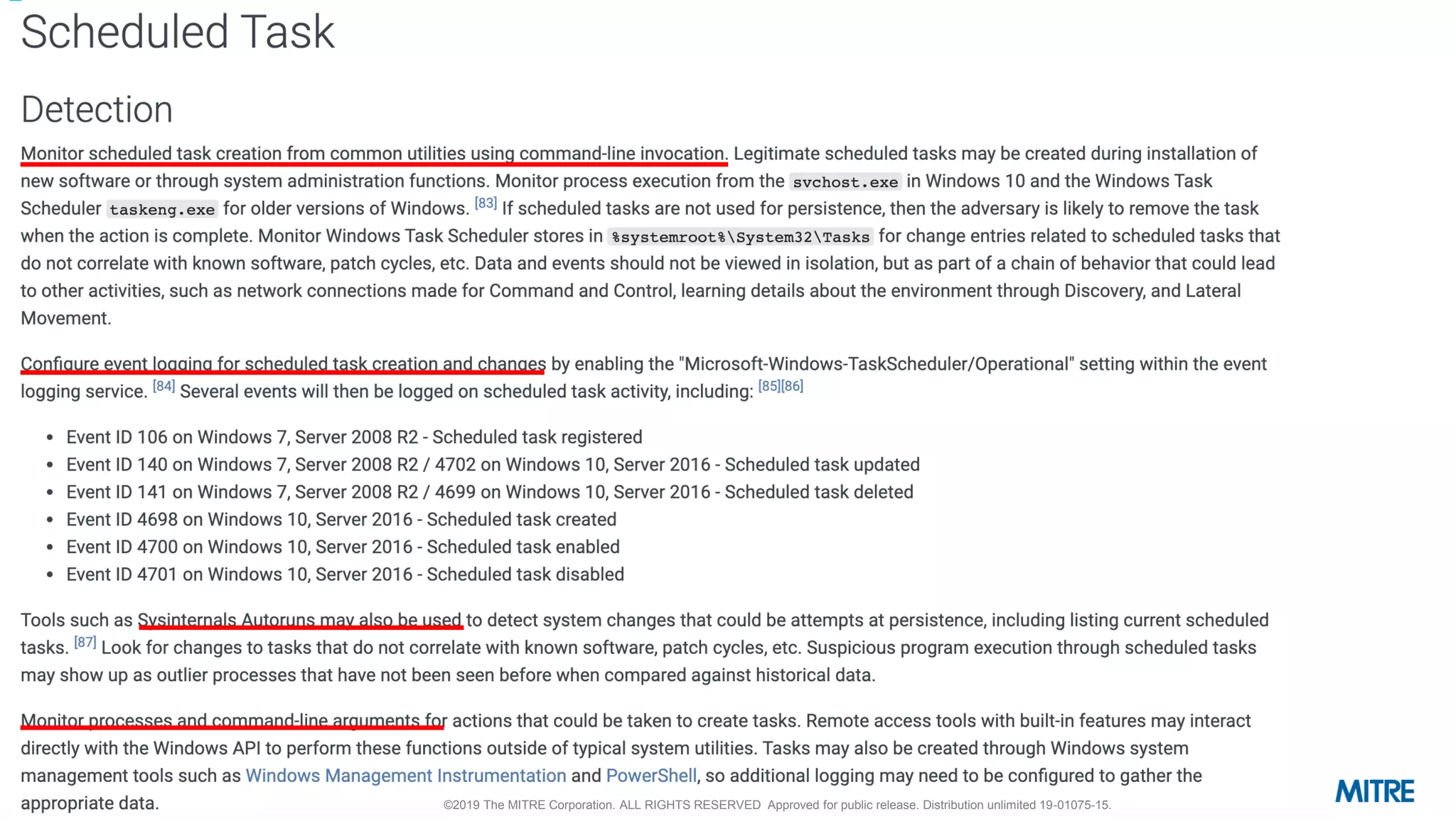
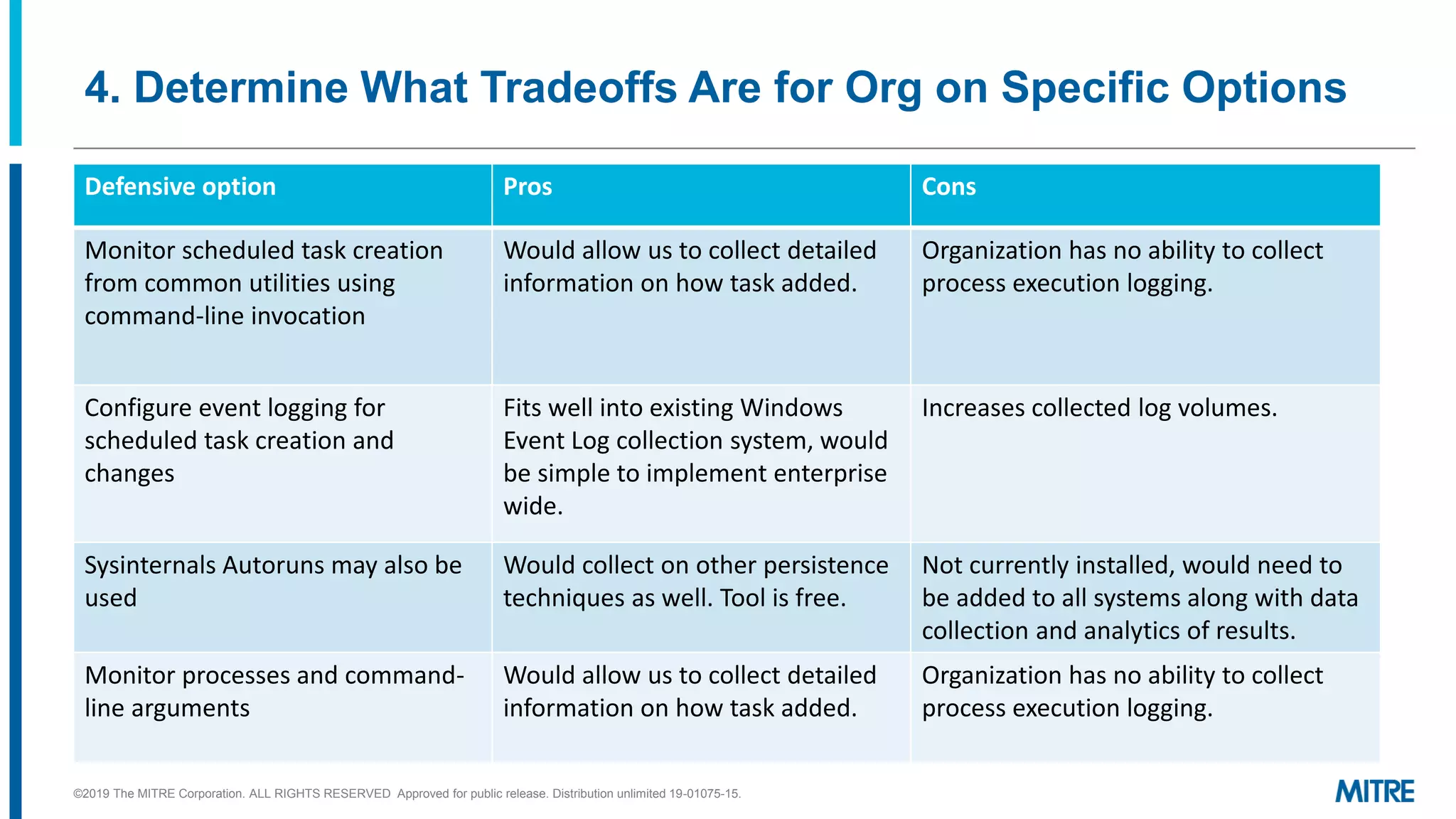
This document outlines a 5-step process for making defensive recommendations based on analyzing threat intelligence data mapped to the ATT&CK framework: 1) determine priority adversary techniques, 2) research how techniques are used in real world attacks, 3) research defensive options to counter the techniques, 4) consider organizational capabilities and constraints, and 5) make tailored recommendations. It provides examples for each step, highlighting sources like ATT&CK and the Cyber Analytics Repository that can help with researching techniques and defenses.