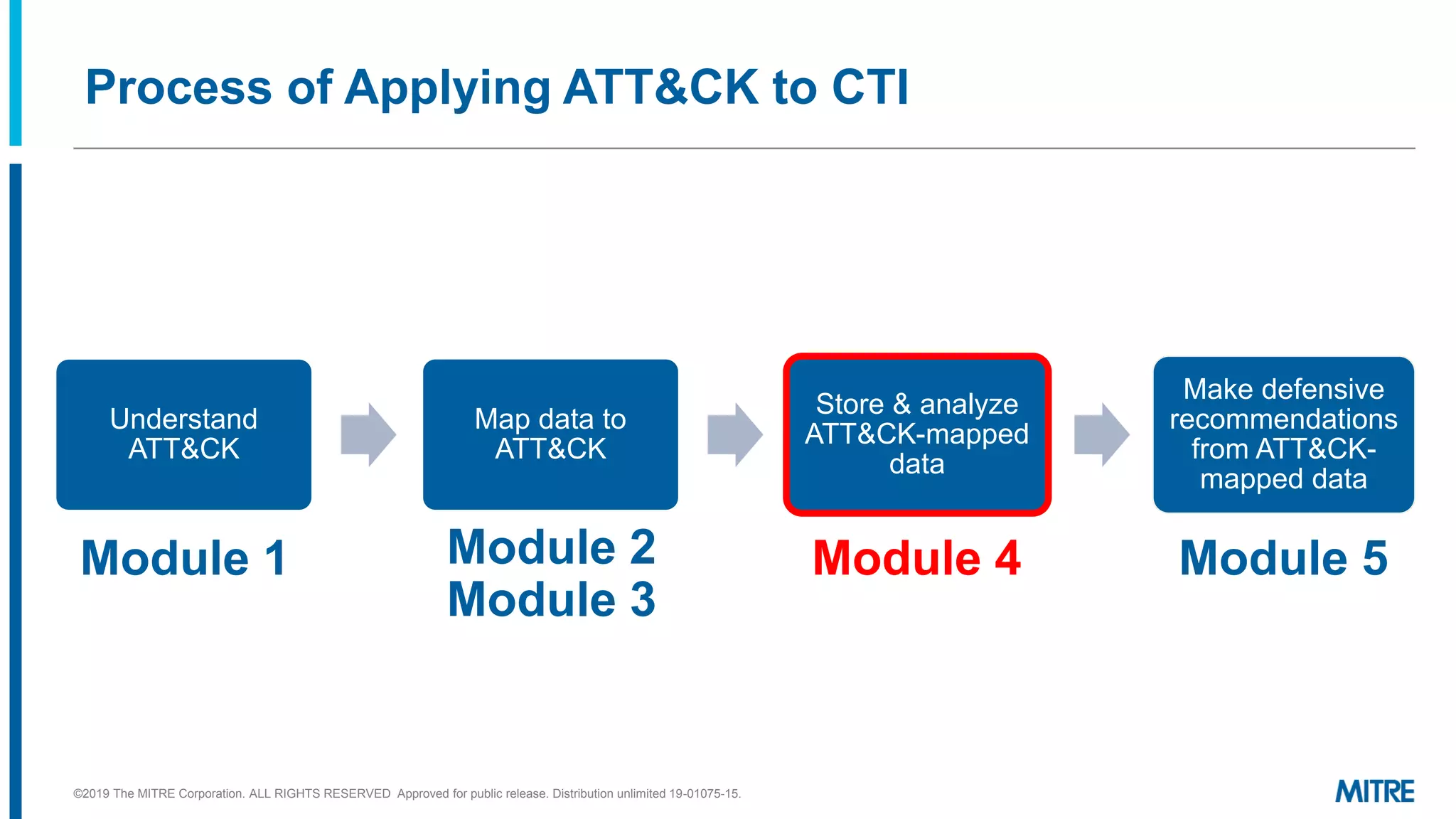
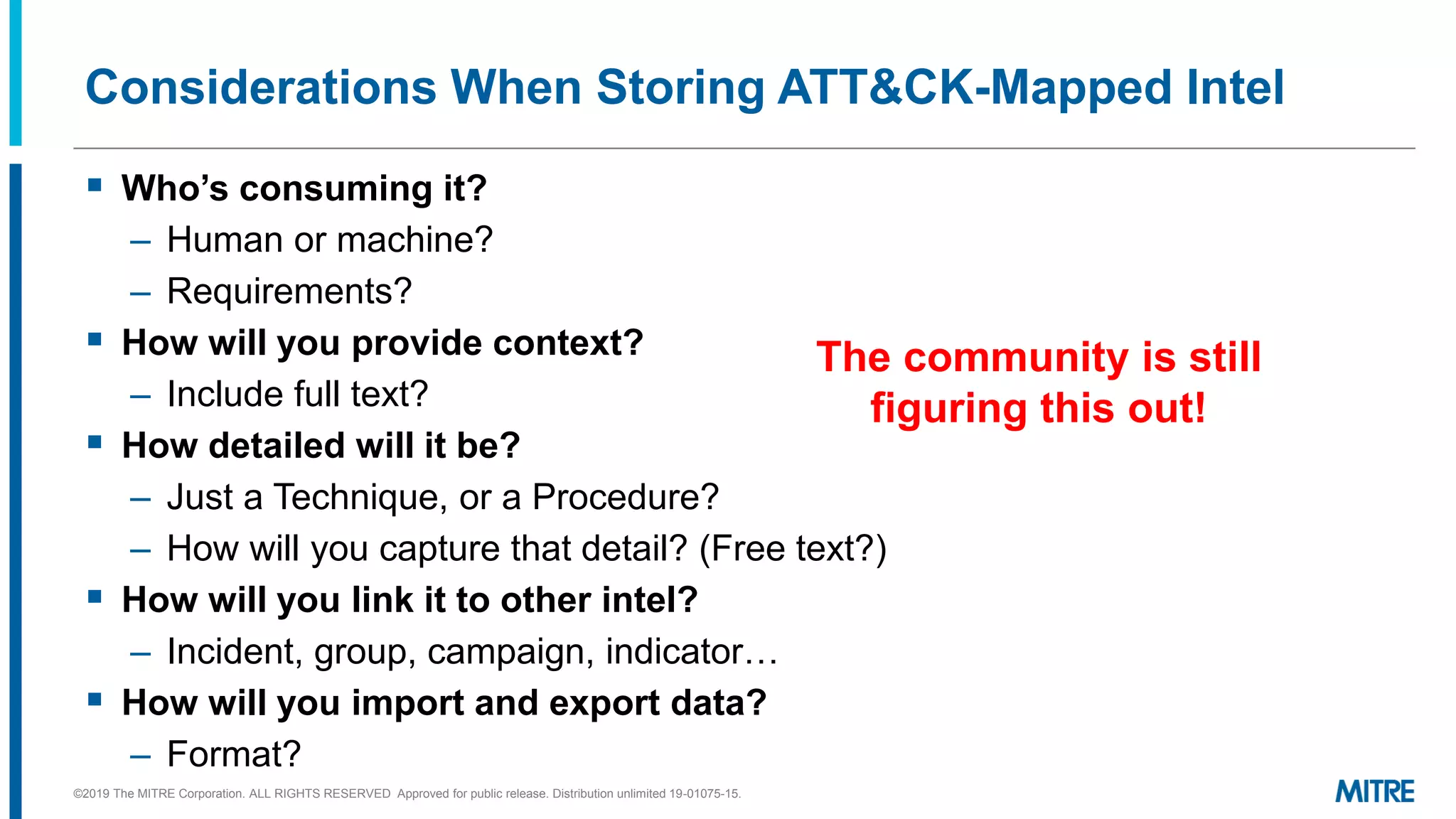
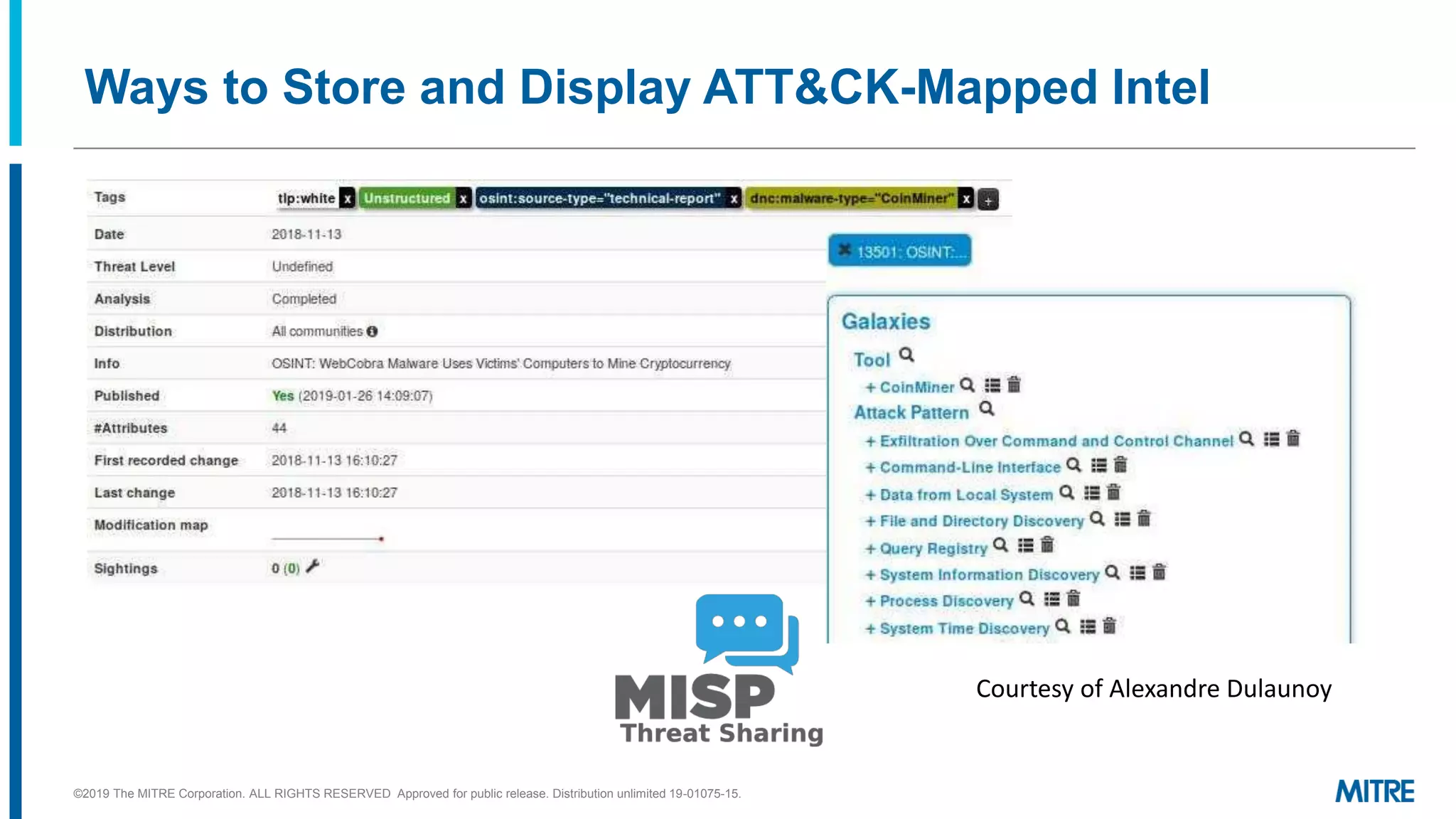
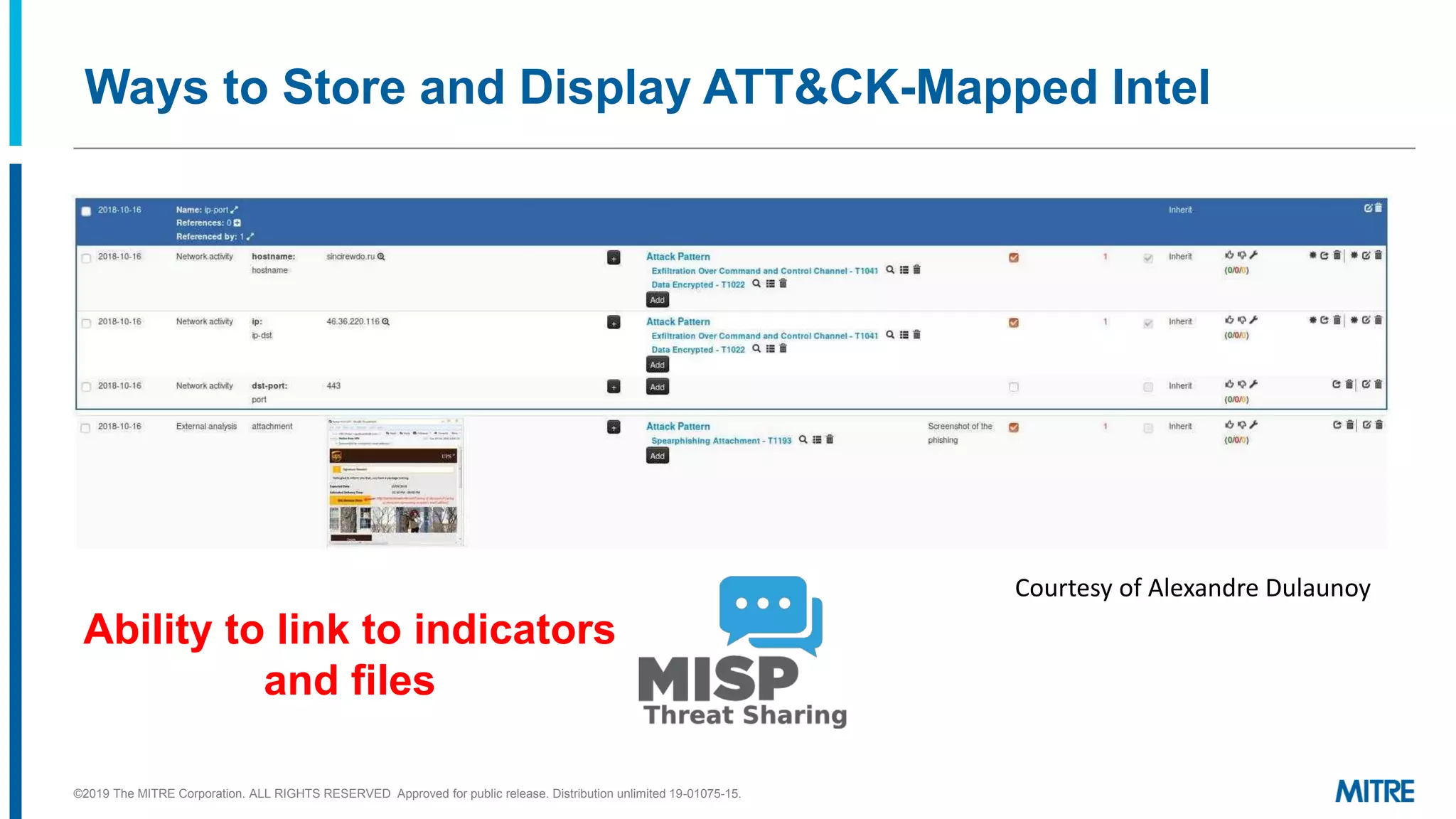
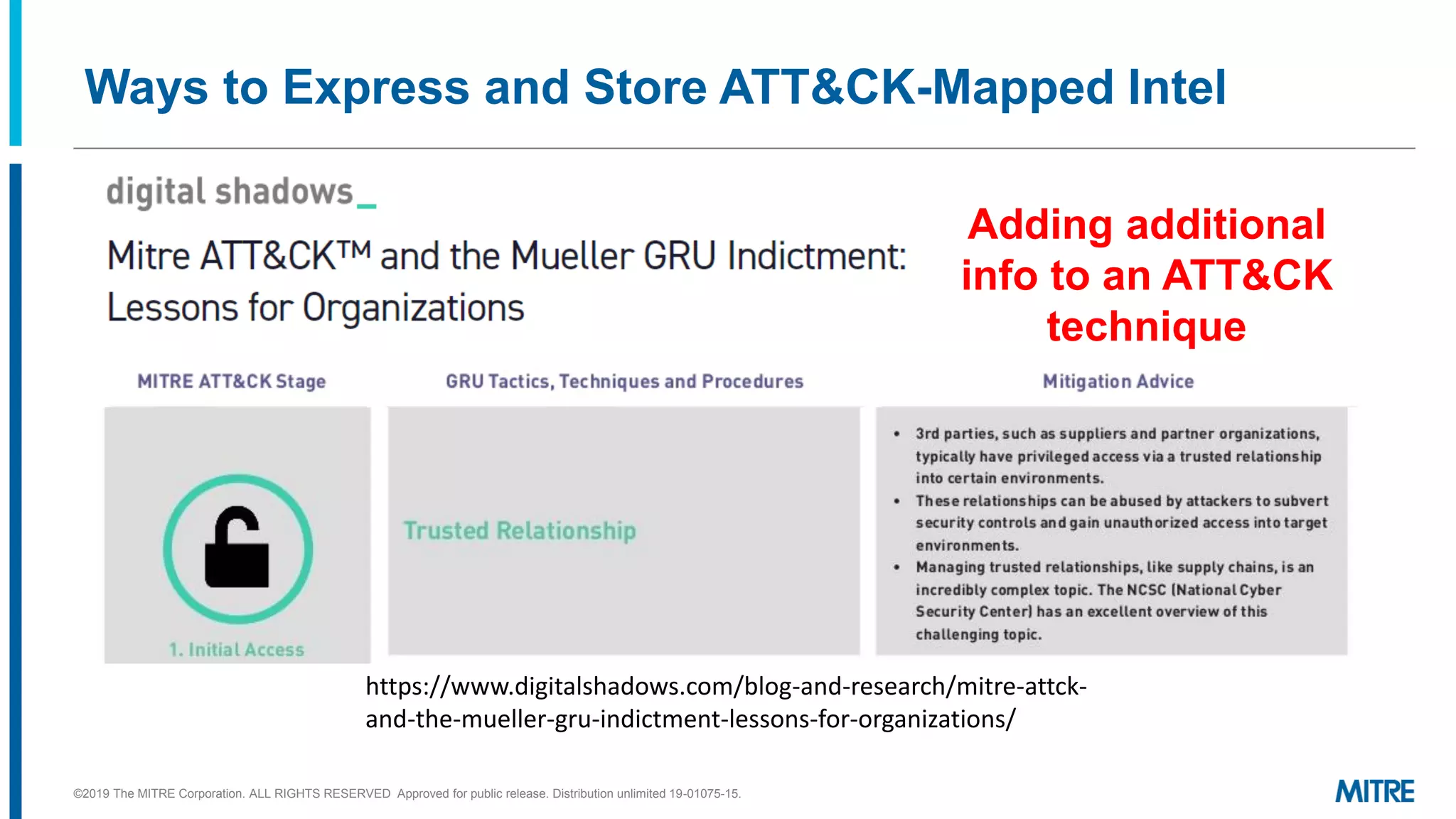
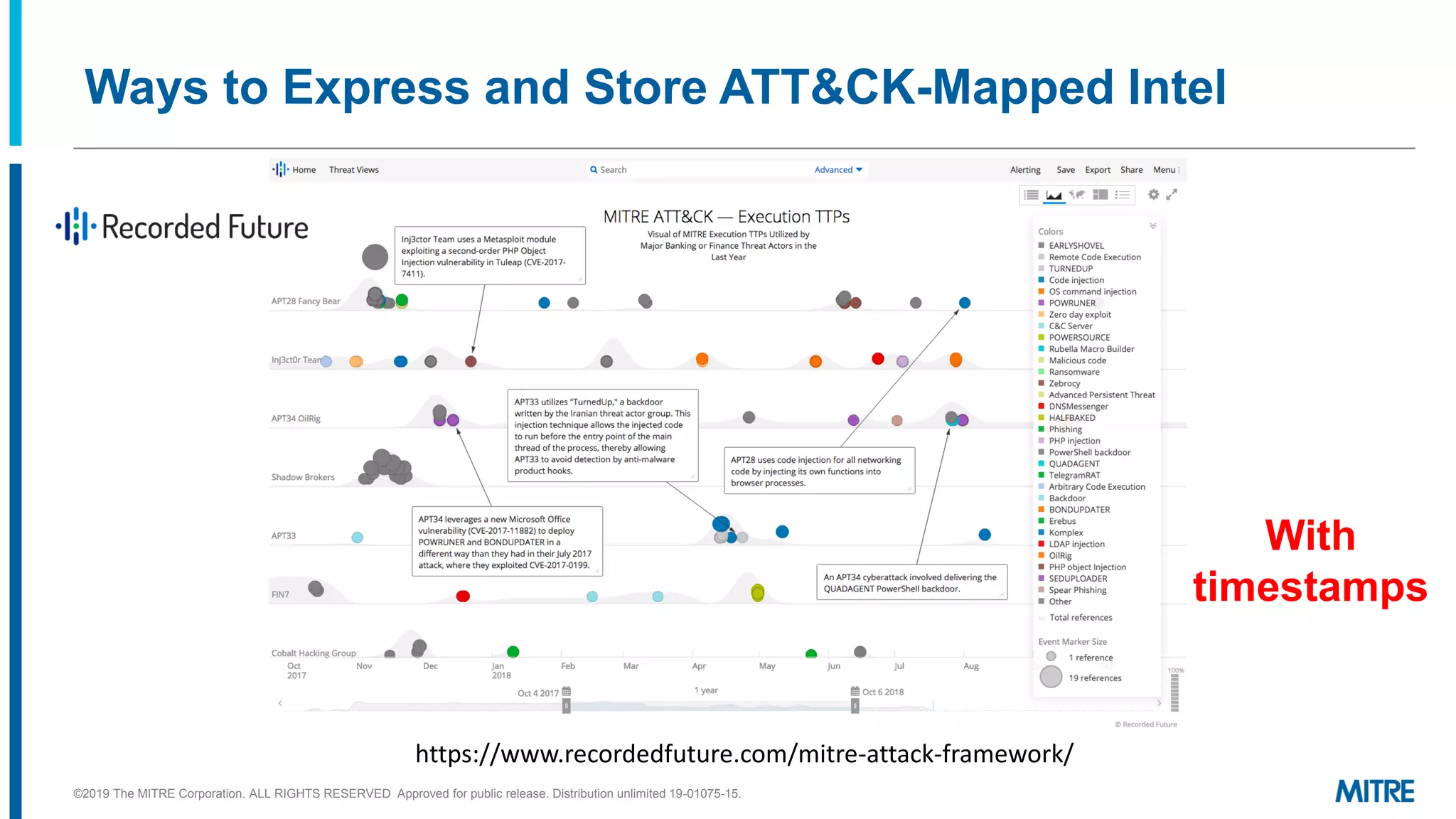
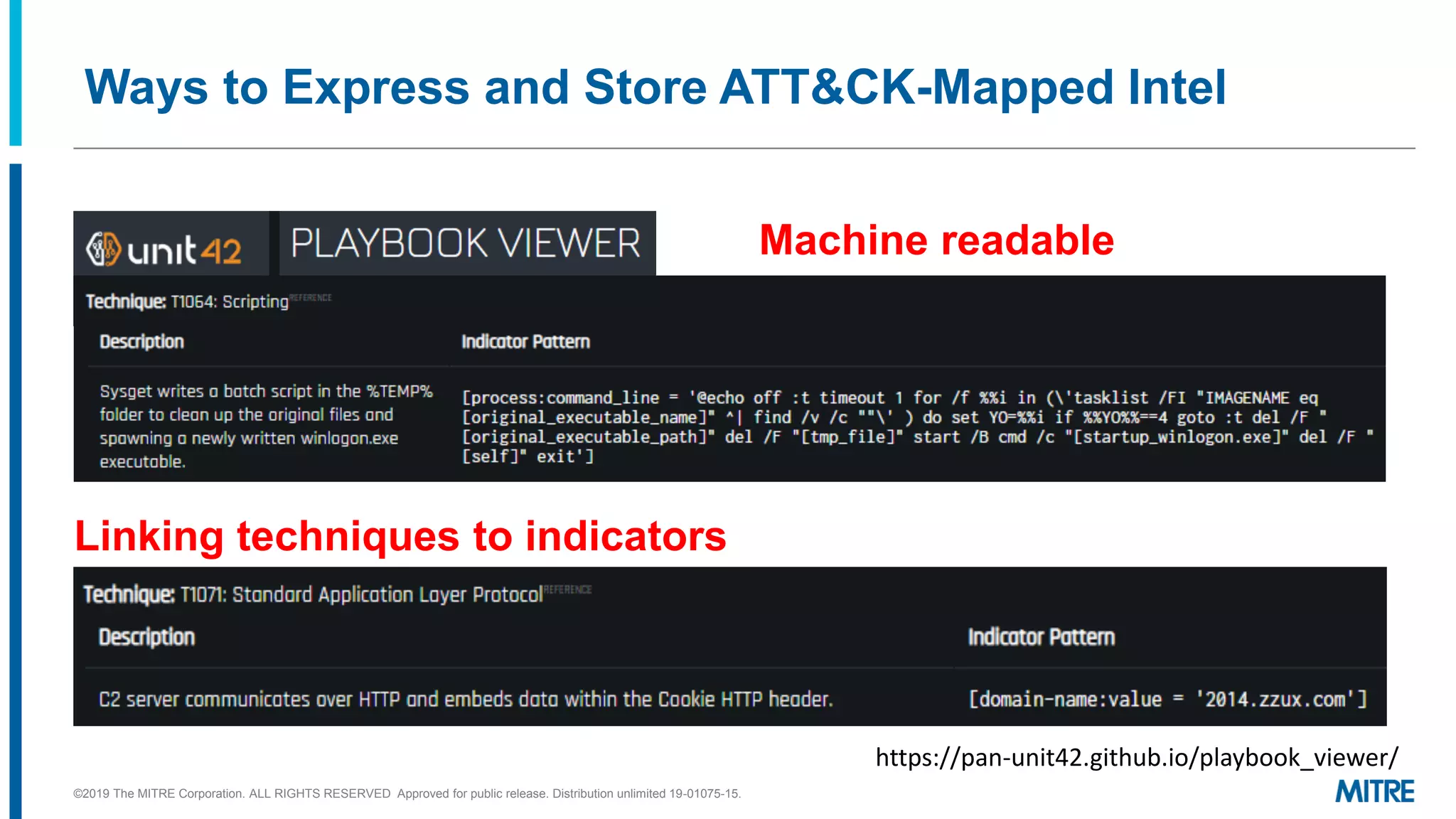
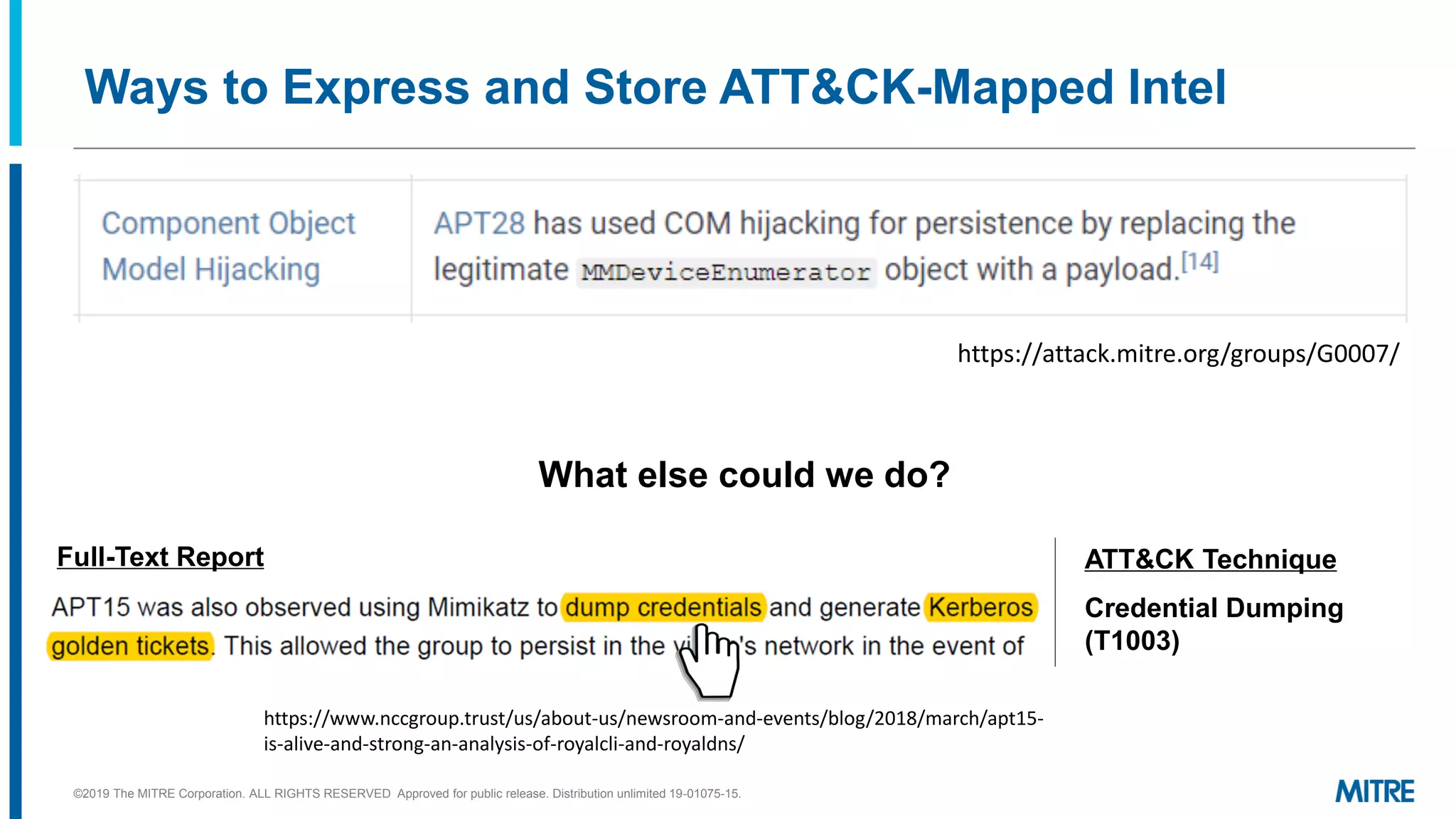
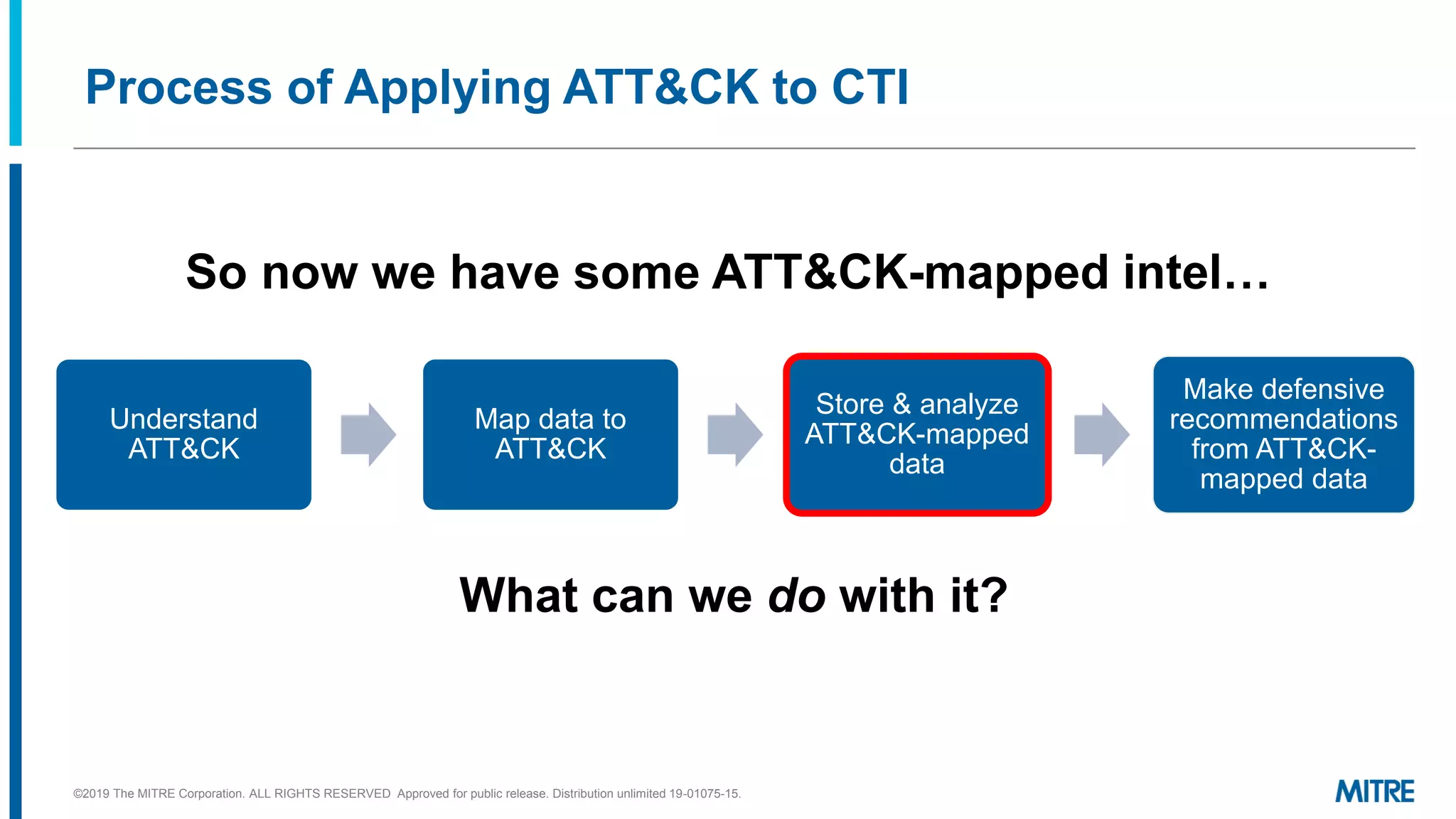
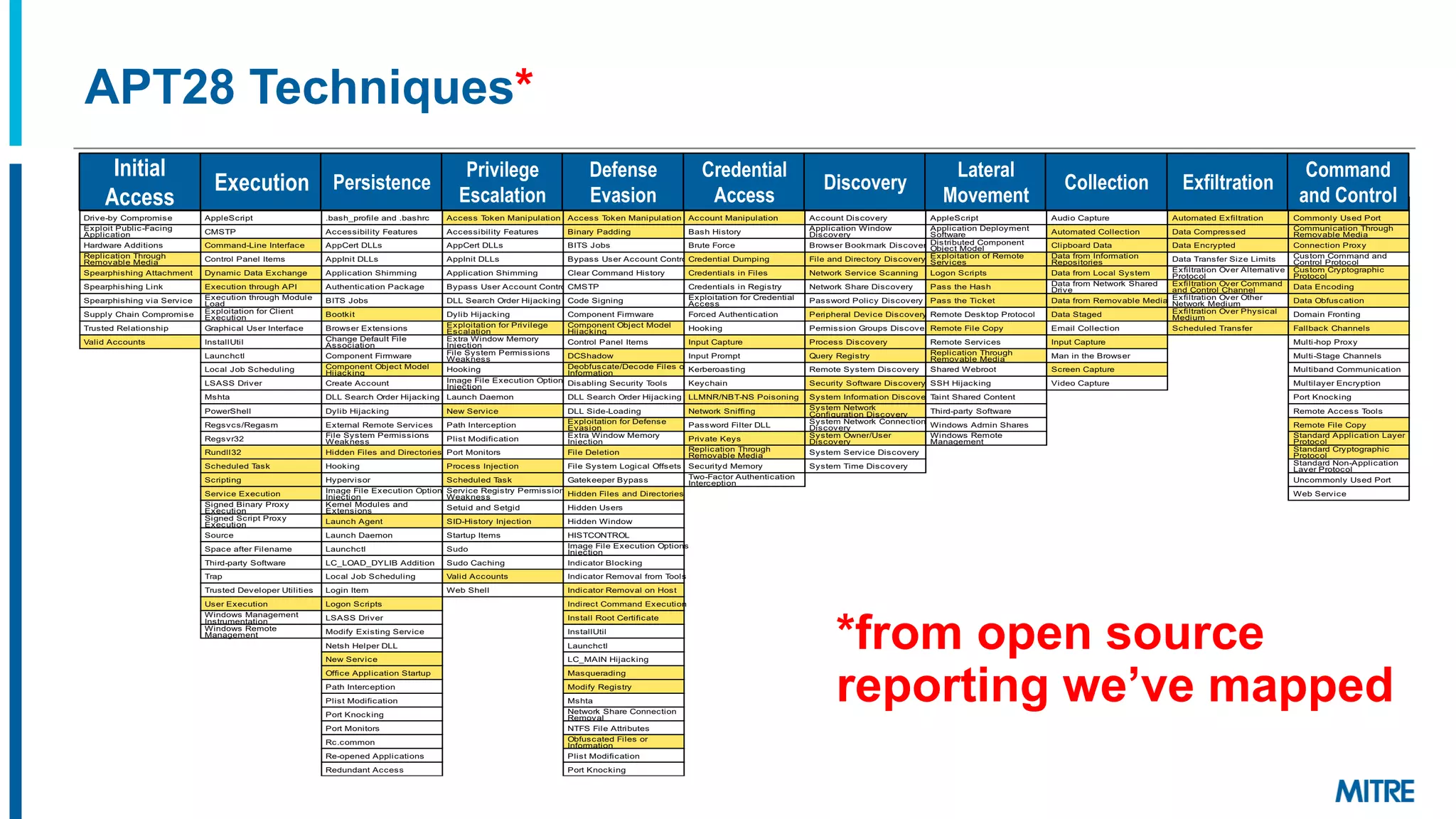
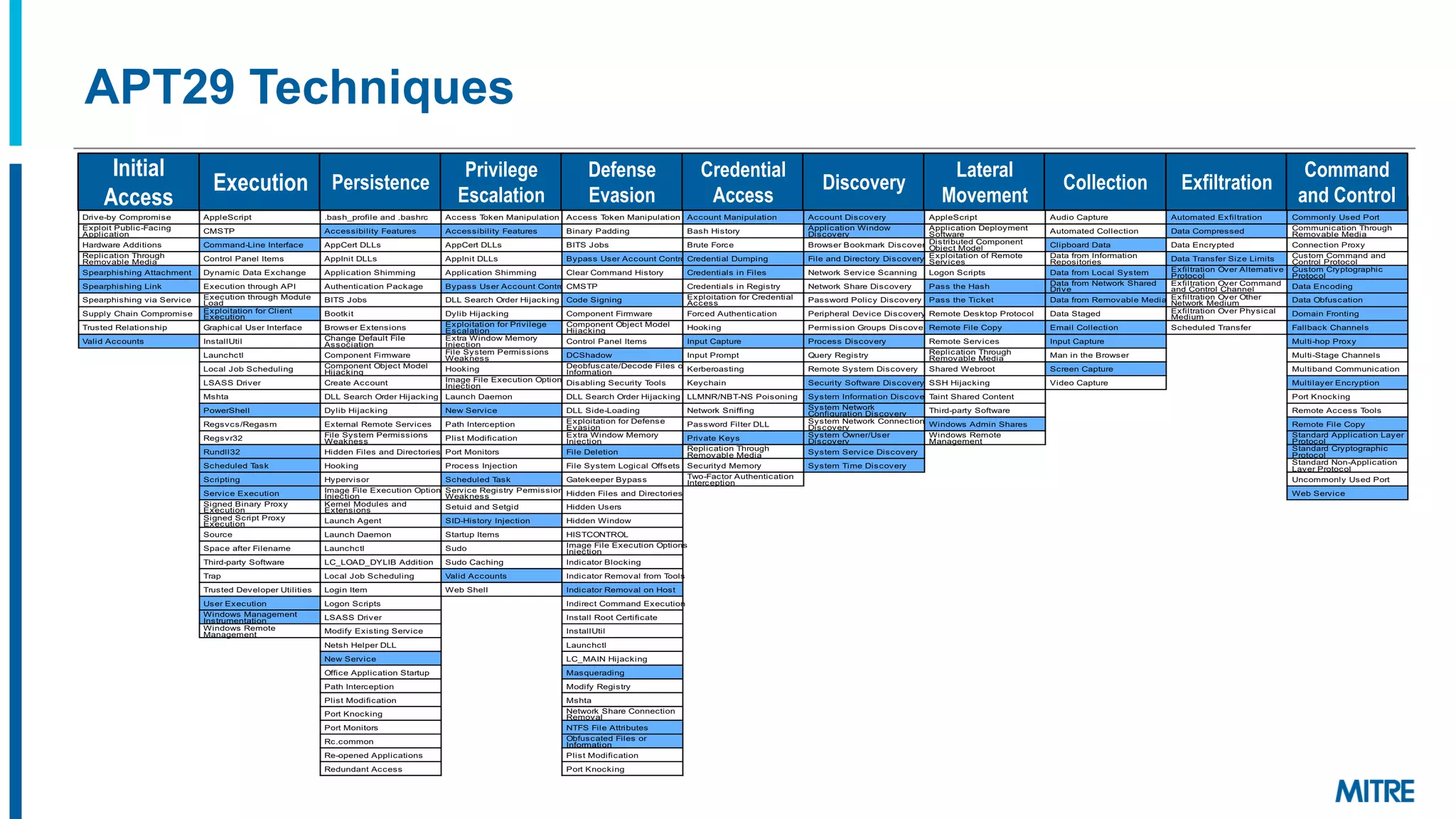
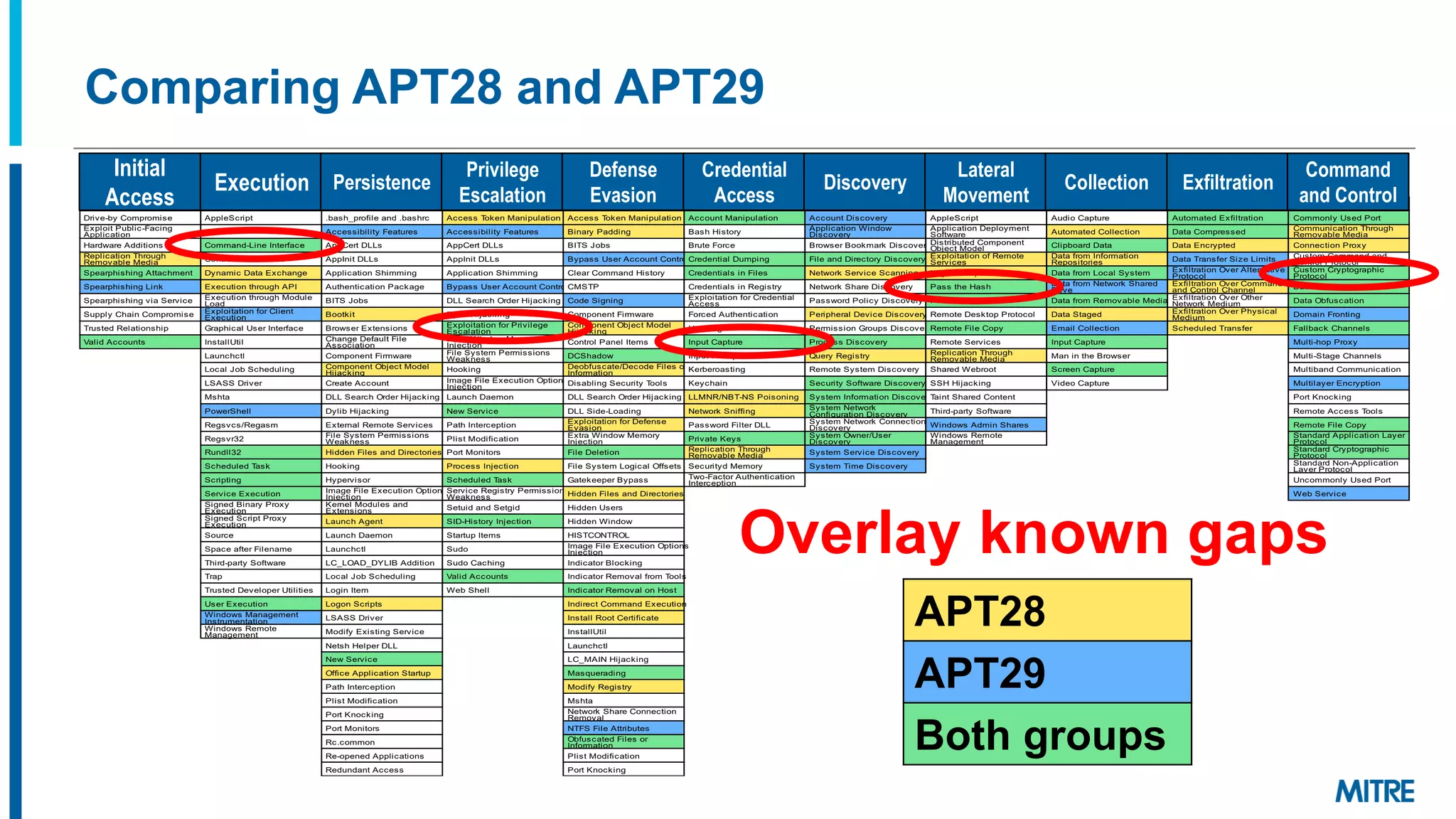
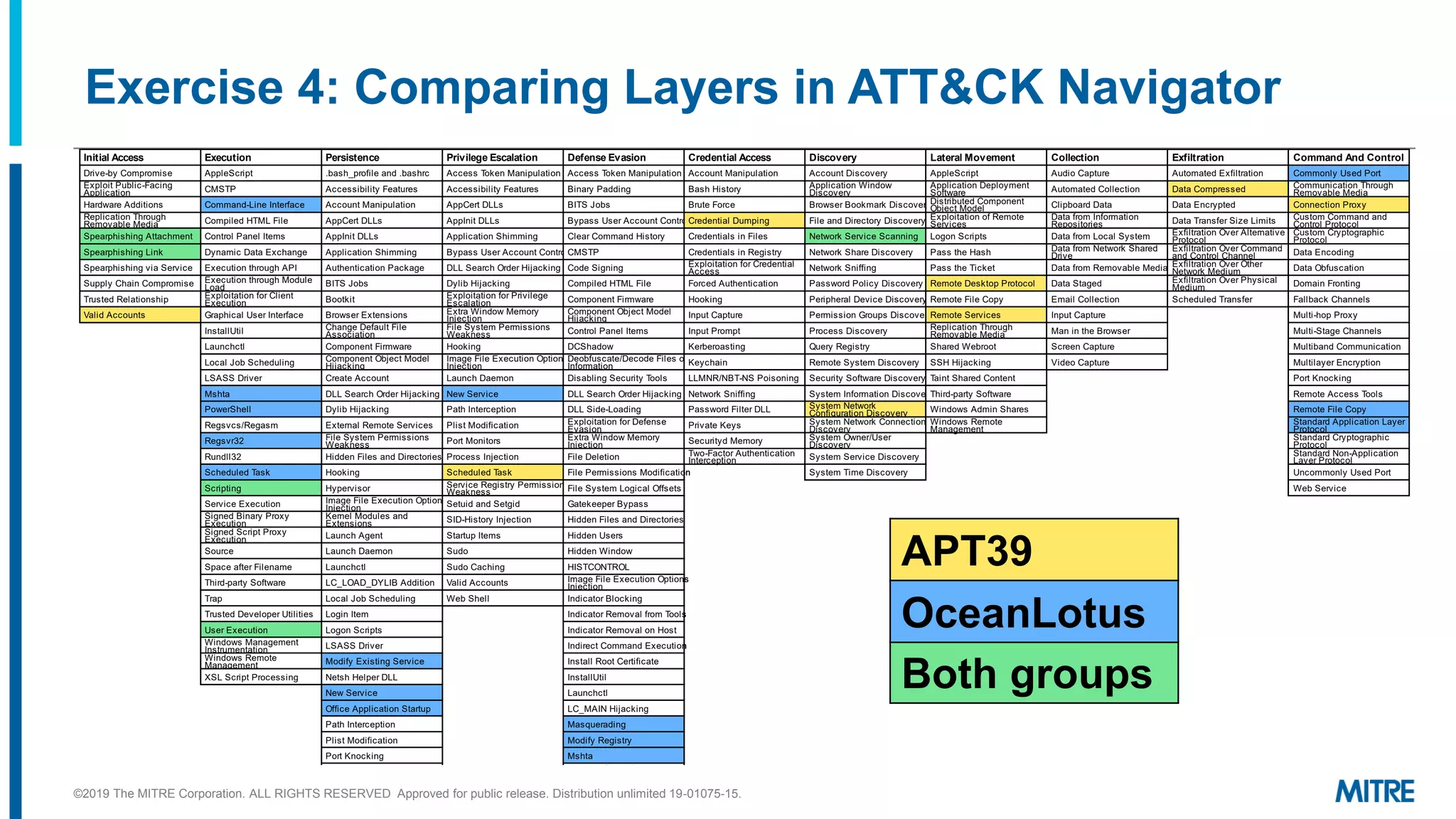
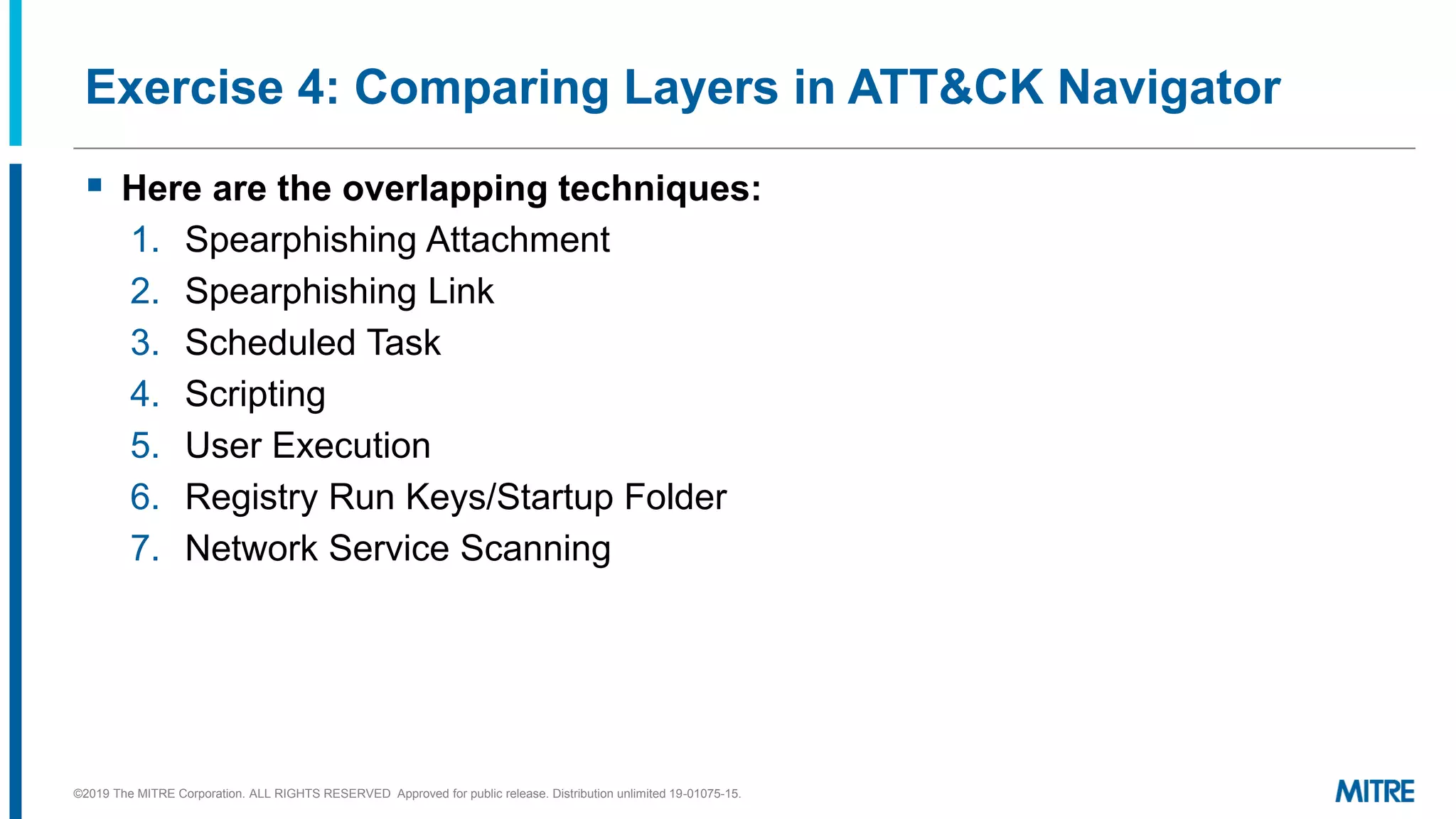
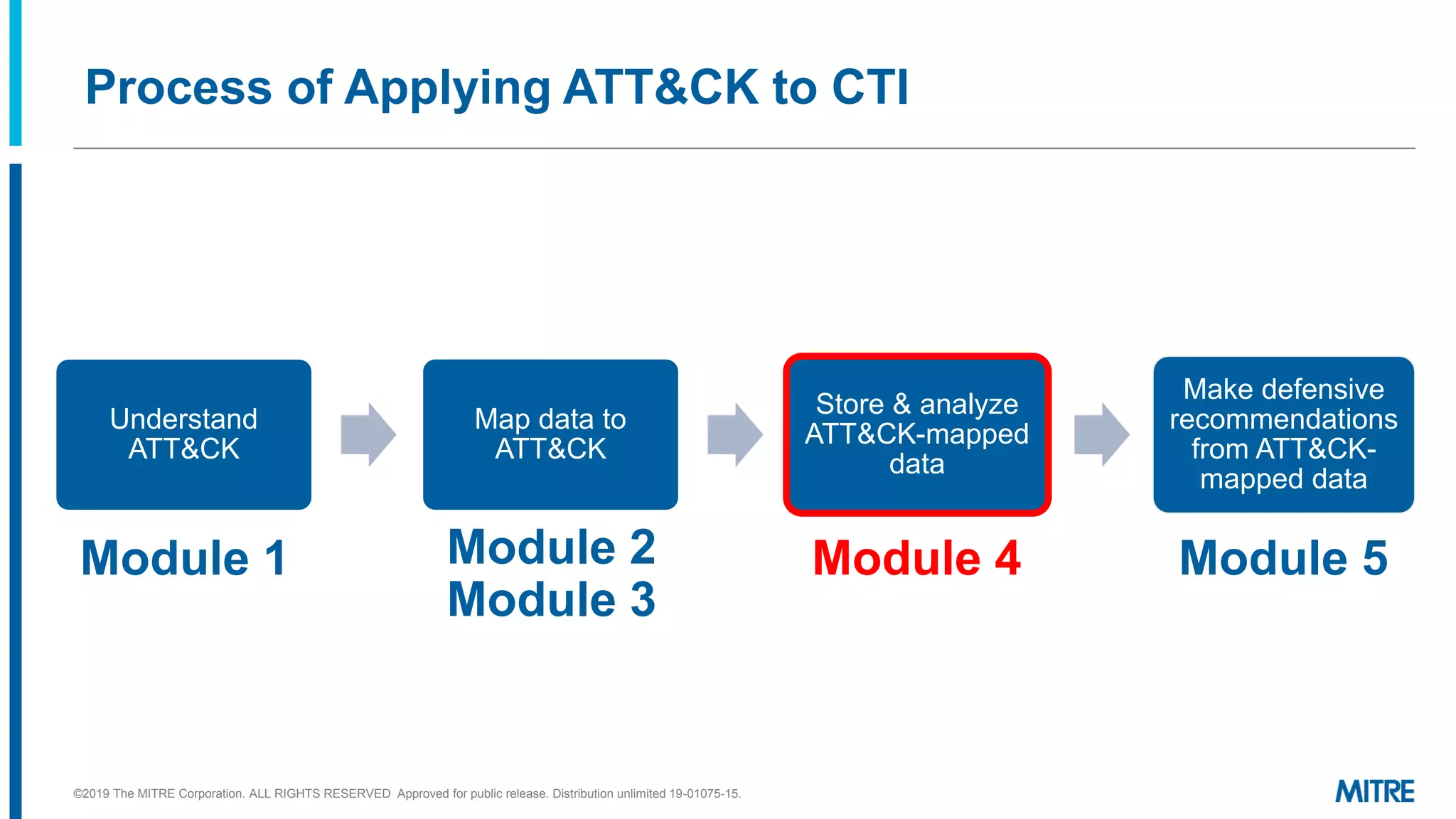
The document discusses various ways that threat intelligence data mapped to the MITRE ATT&CK framework can be stored and analyzed. It provides examples of how ATT&CK techniques have been included in security reports and notes that the community is still exploring the best methods and formats for capturing and linking ATT&CK data to other information like indicators. The goal is to be able to make defensive recommendations by analyzing stored ATT&CK-mapped intelligence.