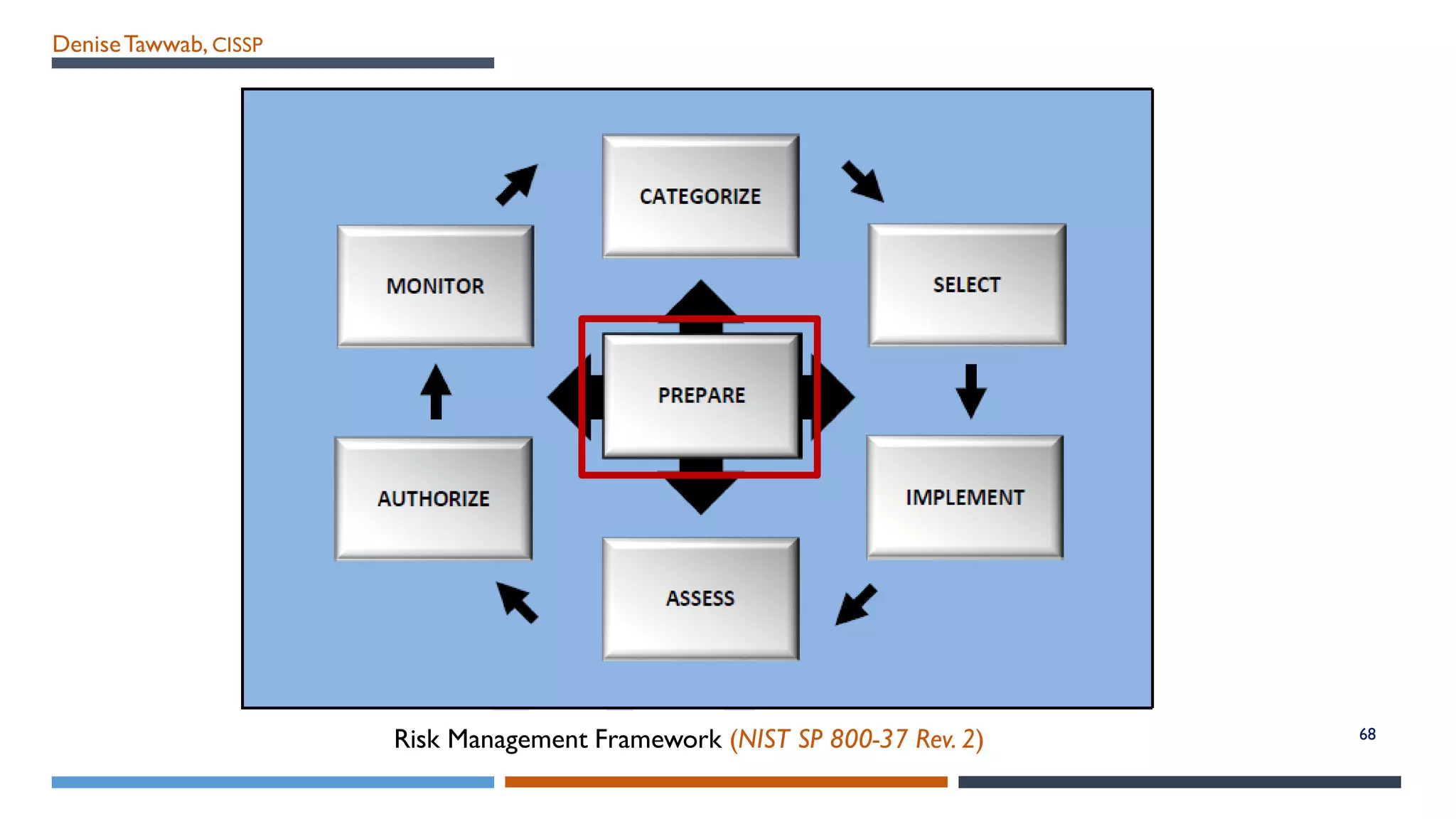
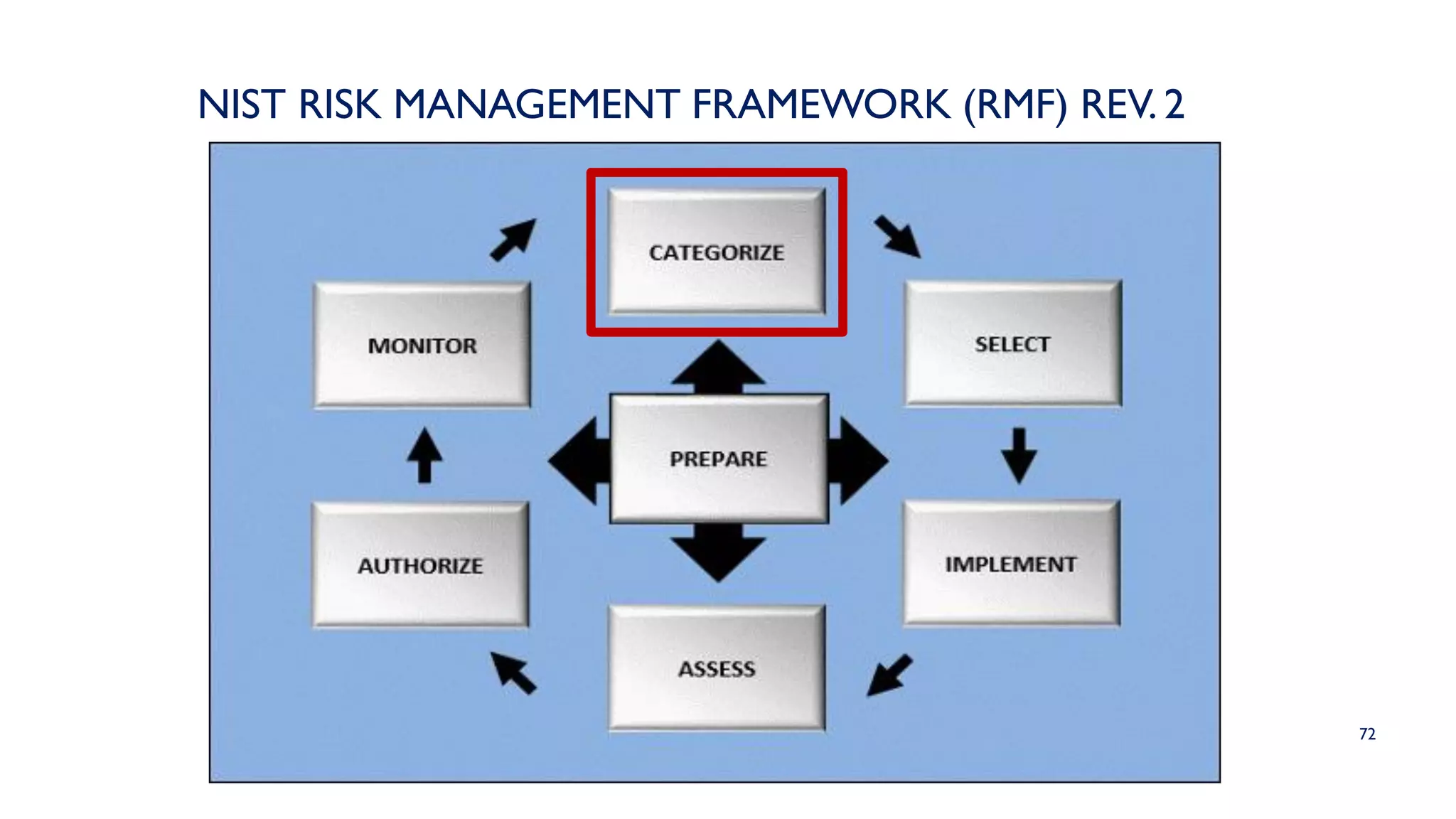
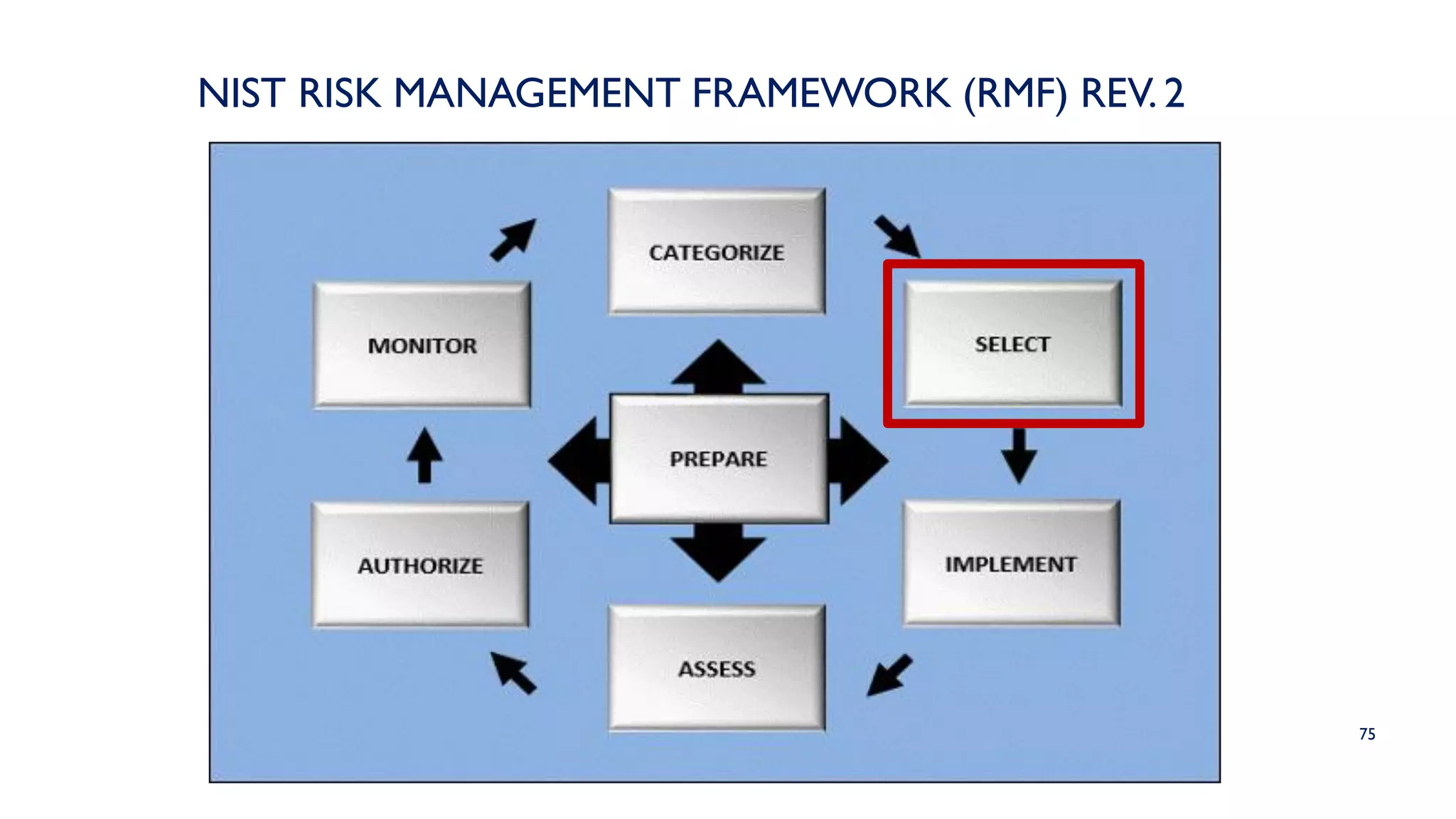
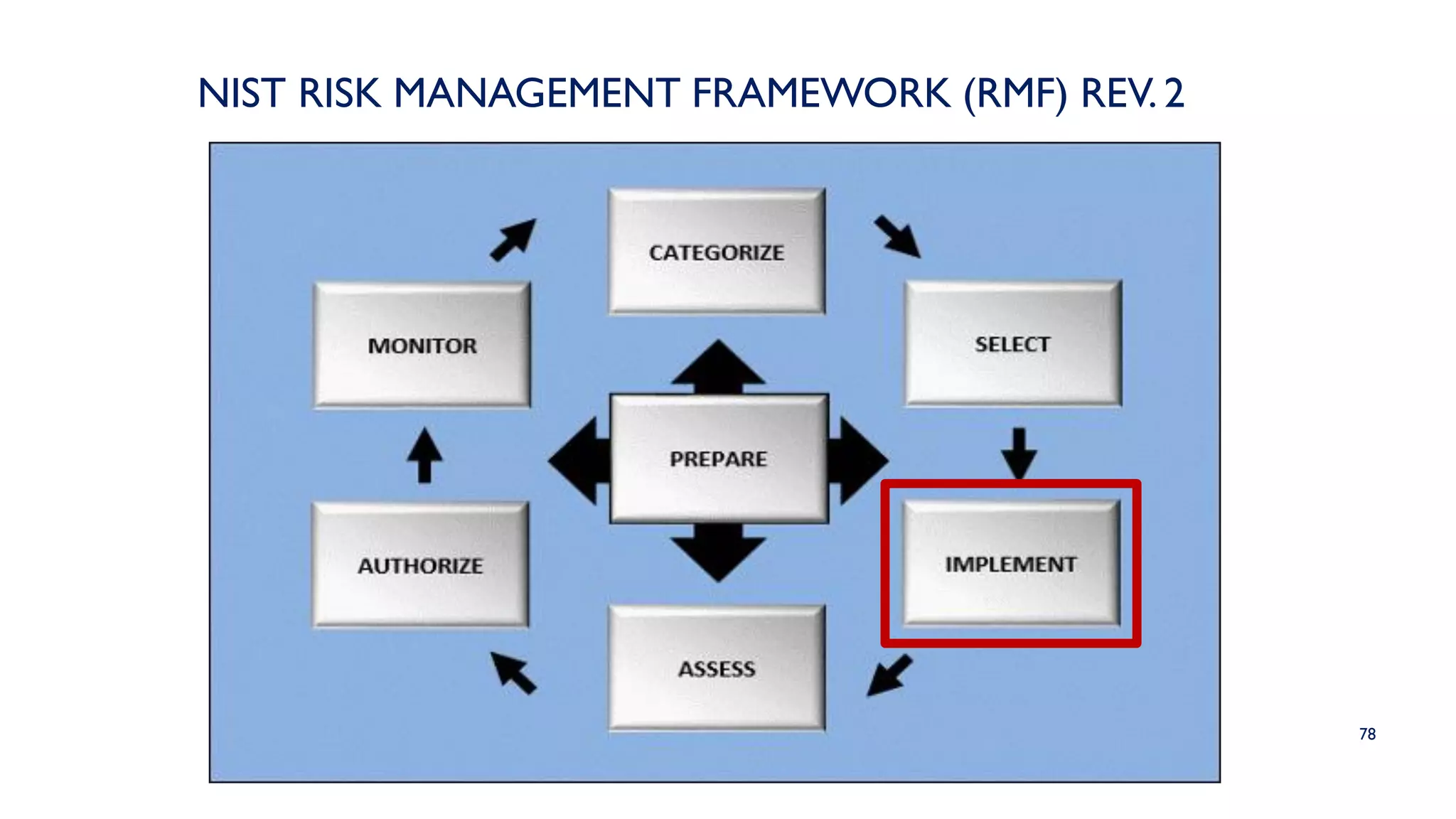
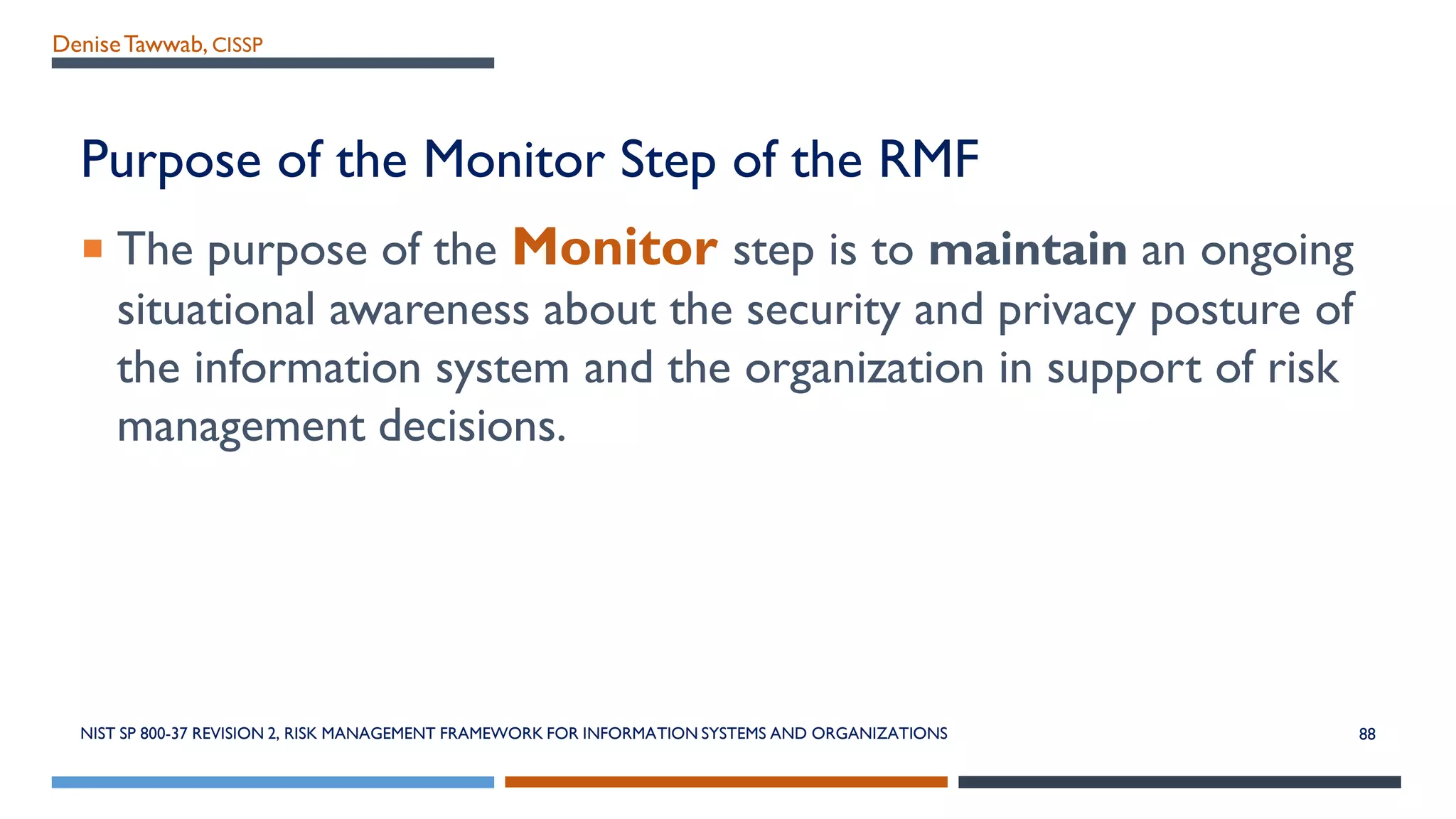
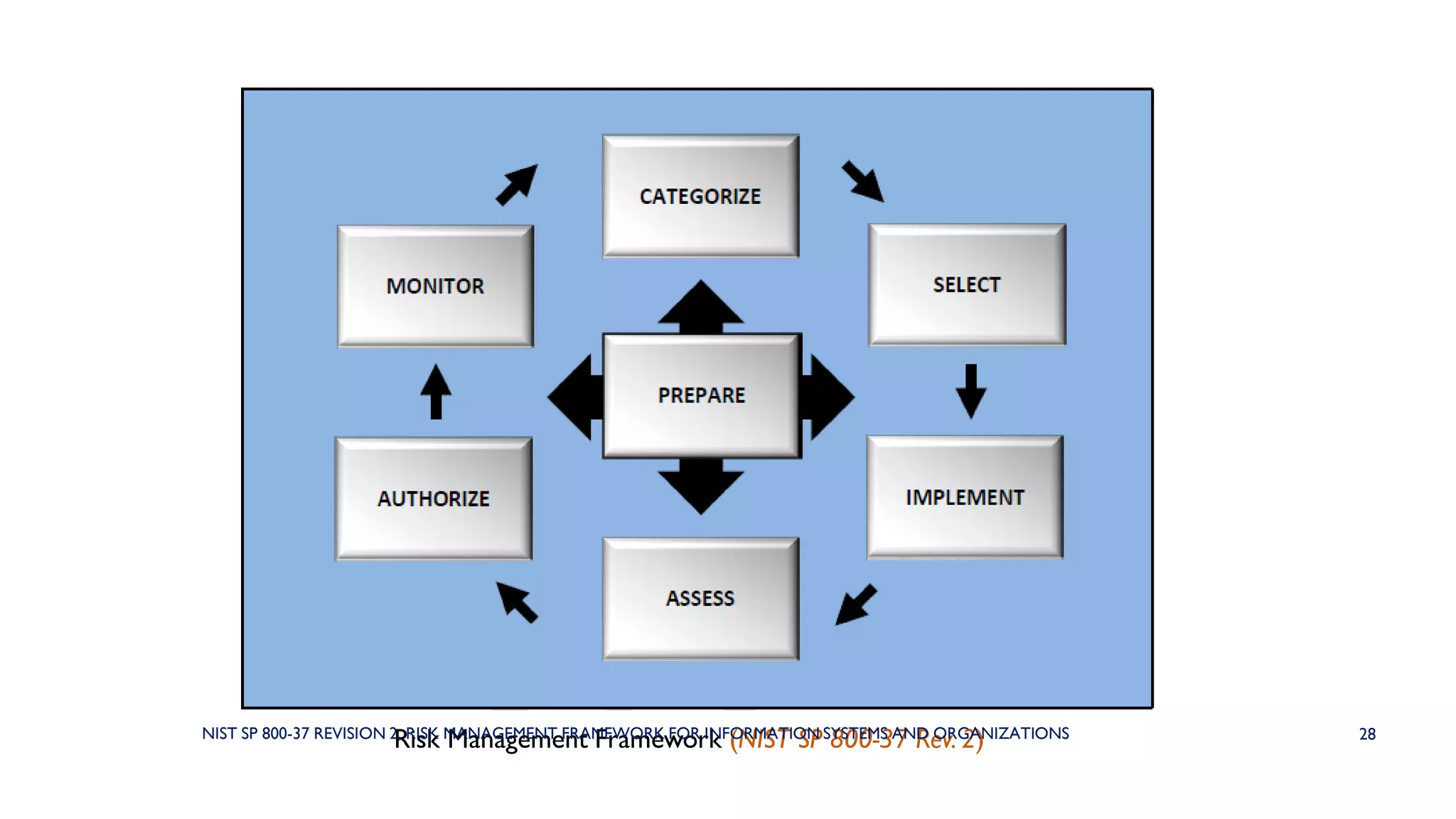
The NIST Risk Management Framework (RMF) outlined in SP 800-37 Revision 2 provides a structured approach for managing information security and privacy risks within organizations. It emphasizes the integration of security measures throughout the system development lifecycle and involves all organizational levels in risk management. The RMF consists of eight goals and seven key steps, facilitating effective risk assessment, control, and monitoring processes to maintain security and privacy compliance.
















































![Task P-2 Risk Management Strategy
Task 2 Establish a risk management strategy for the organization that includes a
determination of risk tolerance.
Potential Inputs: Organizational mission statement; organizational policies; organizational
risk assumptions, constraints, priorities and trade-offs.
Potential Outputs: Risk management strategy and statement of risk tolerance.
Primary Responsibility: Head of Agency
Supporting Roles: Senior Accountable Official for Risk Management or Risk Executive
(Function); Chief Information Officer; Senior Agency Information Security Officer; Senior
Agency Official for Privacy.
Discussion: Risk tolerance is the level or degree of risk or uncertainty that is acceptable to
an organization. Risk tolerance affects all components of the risk management process...
References: NIST Special Publication 800-30; NIST Special Publication 800-39
(Organization Level); NIST Special Publication 800-160,Volume 1 (Risk Management,
Decision Management, Quality Assurance, Quality Management, Project Assessment and
Control Processes); NIST Special Publication 800-161;NIST Interagency Report 8062; NIST
Cybersecurity Framework (Core [Identify Function]).
67NIST SP 800-37 REVISION 2, RISK MANAGEMENT FRAMEWORK FOR INFORMATION SYSTEMS AND ORGANIZATIONS](https://image.slidesharecdn.com/nist-rmf-denise-tawwab-technosecuritydigitalforensicsconf-2019june-190604143914/75/Understanding-the-NIST-Risk-Management-Framework-800-37-Rev-2-66-2048.jpg)