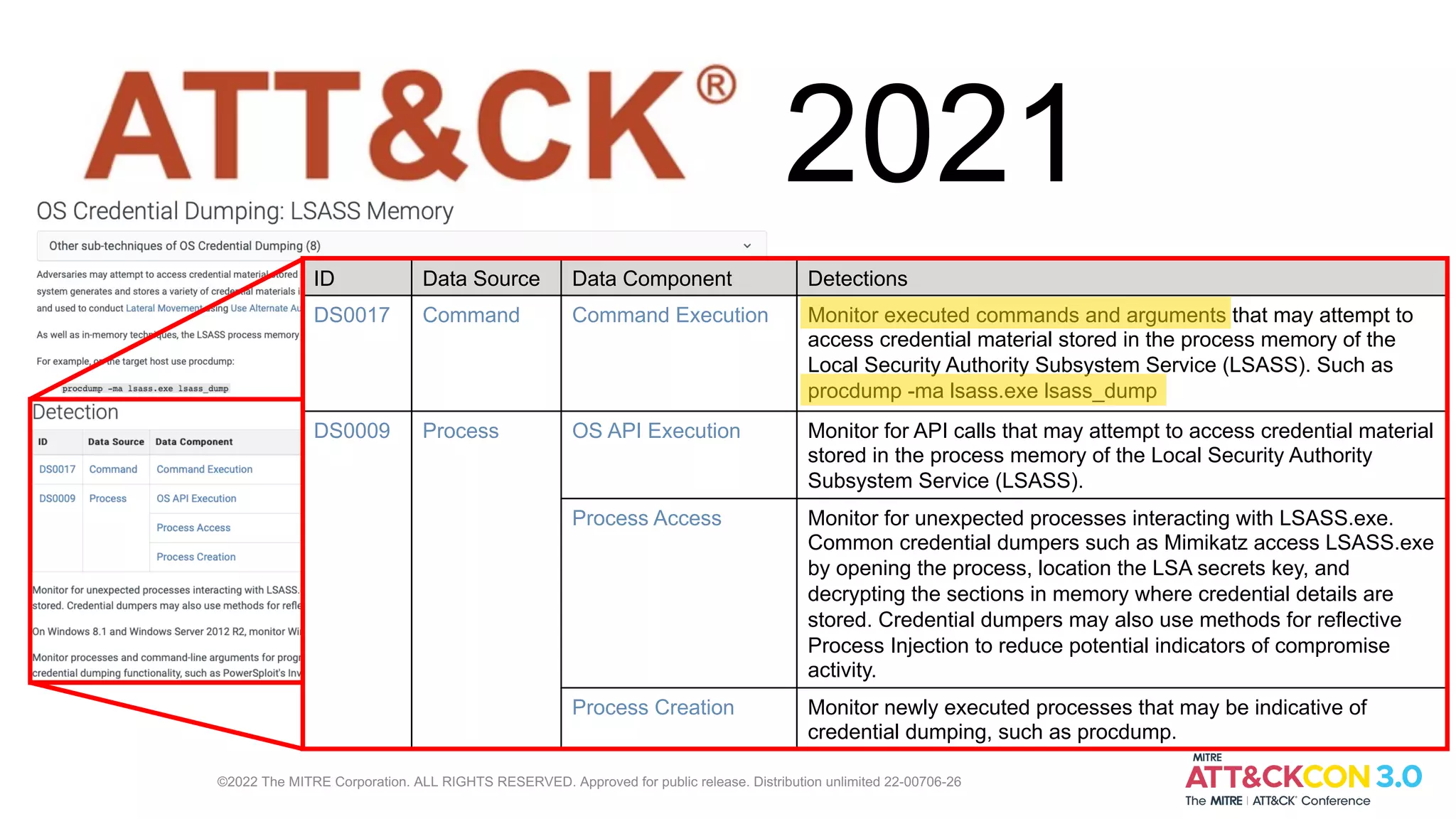
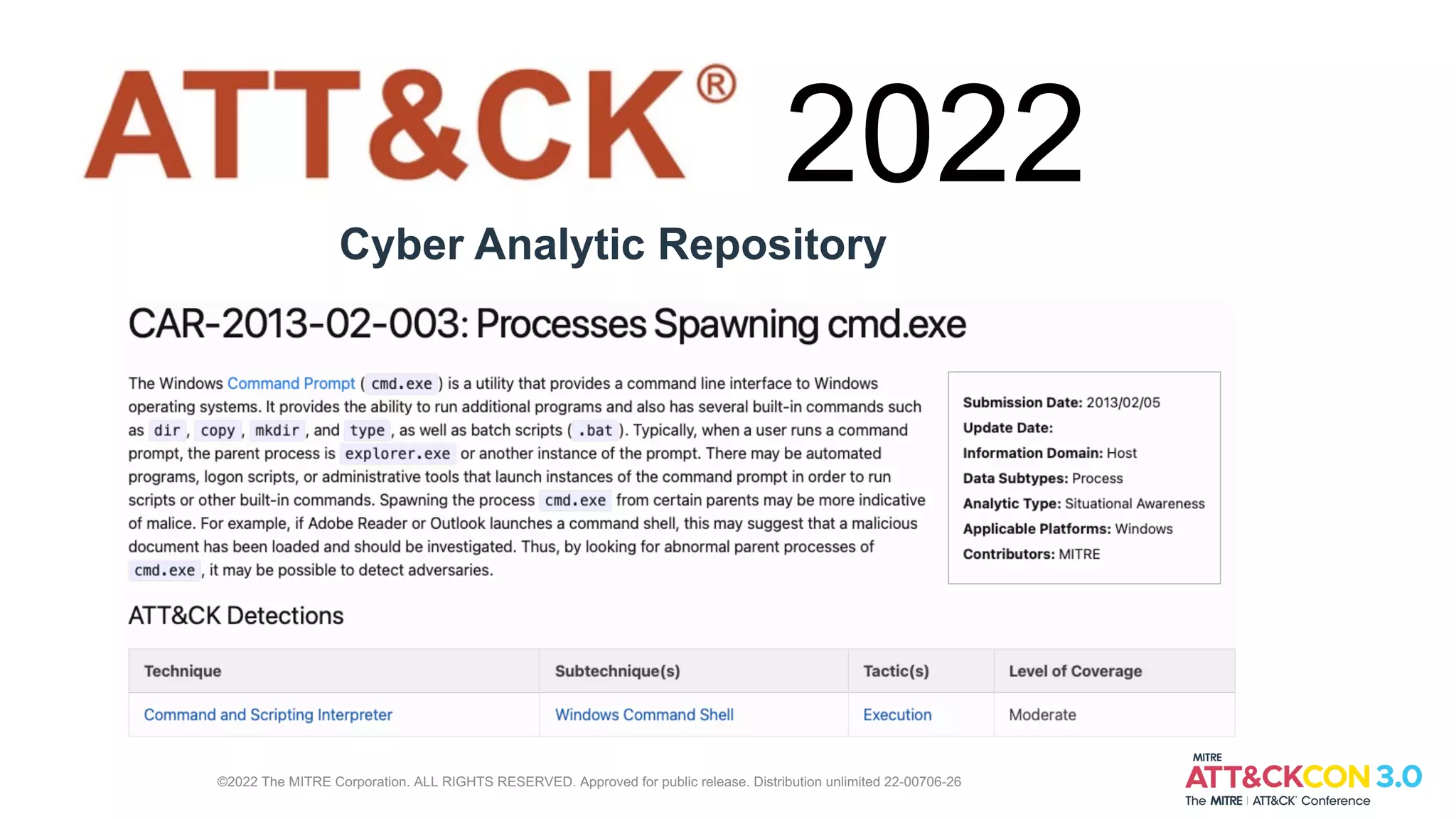
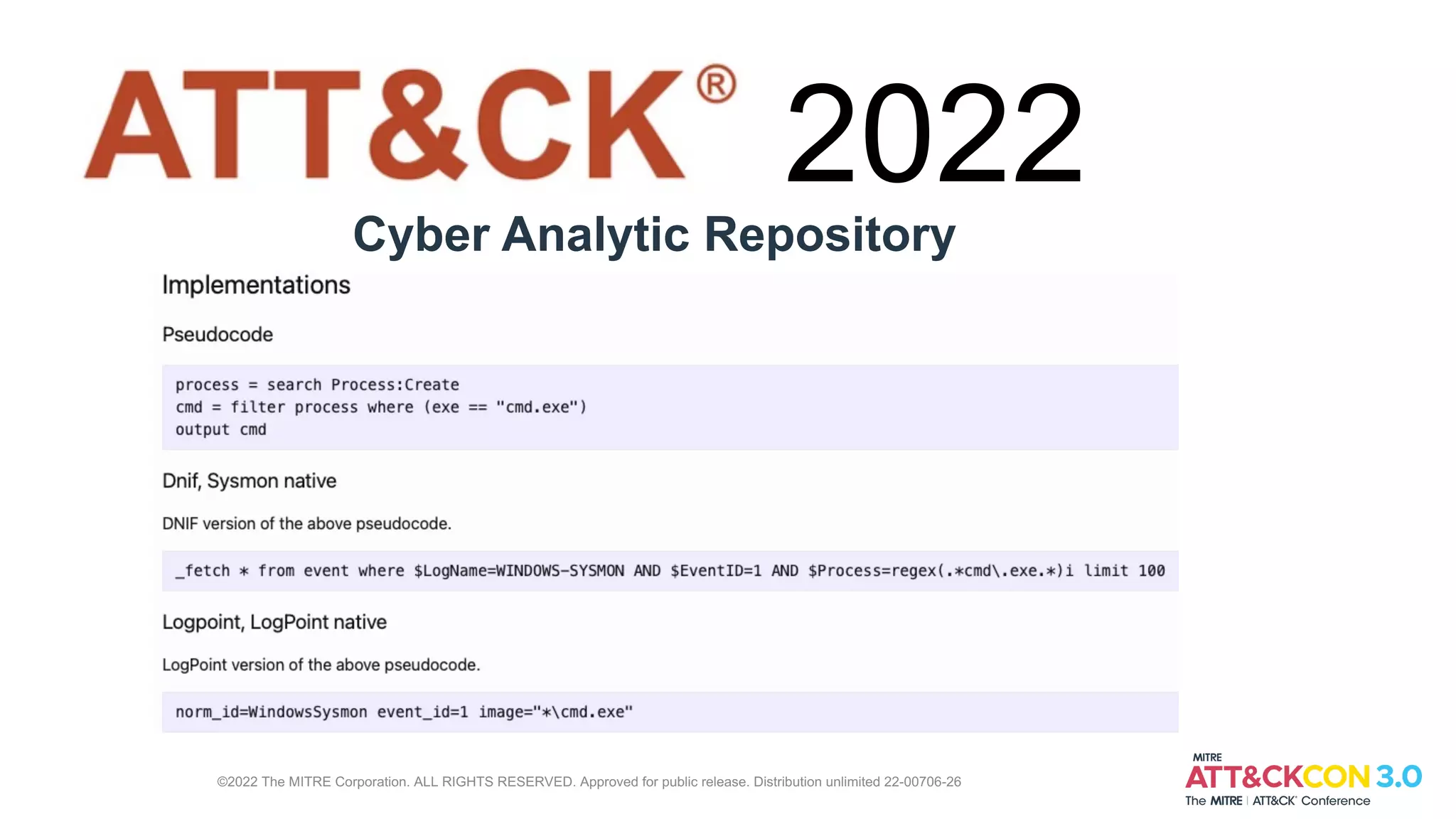
Lex Crumpton leads MITRE's defensive ATT&CK efforts. In 2021, they added data sources and detections for monitoring processes interacting with LSASS.exe and detecting credential dumping tools. In 2022, they plan to add more detections and develop the Cyber Analytic Repository to share analytic knowledge. Crumpton invites attendees to learn more about defensive ATT&CK on their website and contact them directly with any other questions.