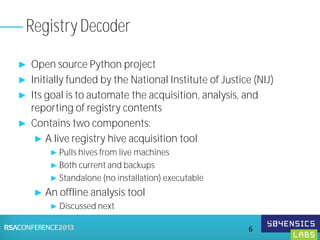
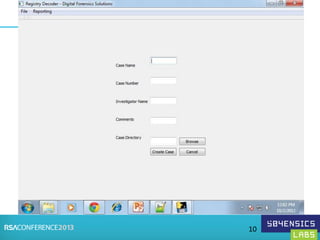
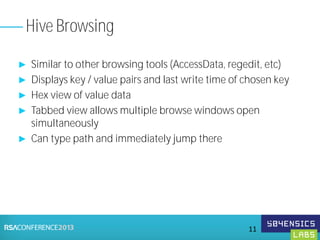
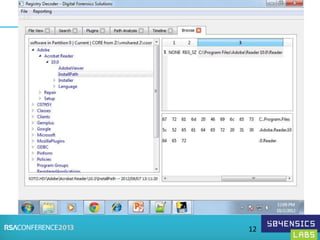
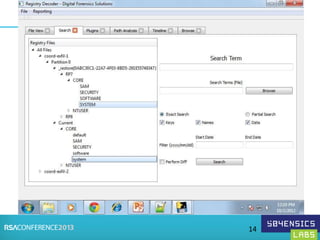
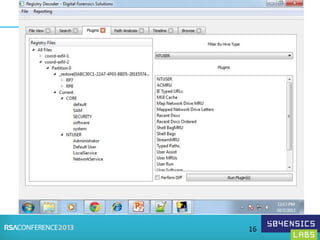
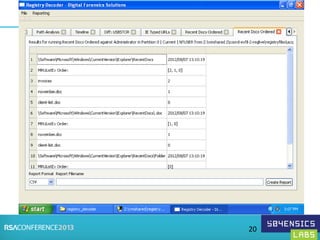
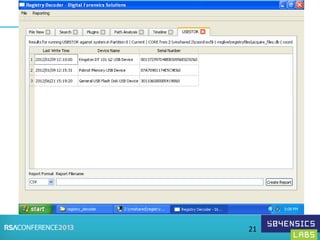
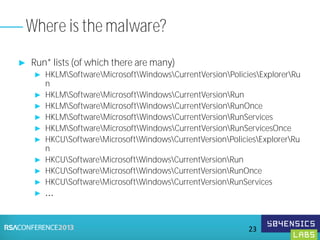
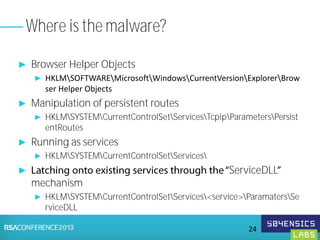
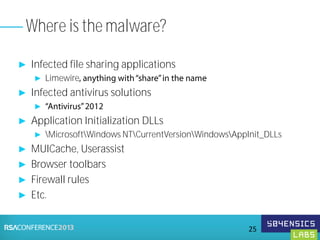
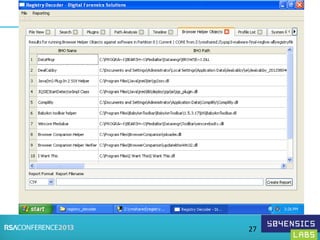
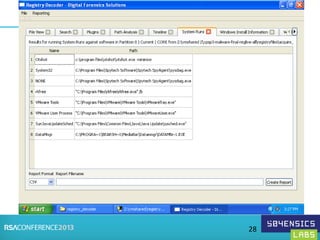
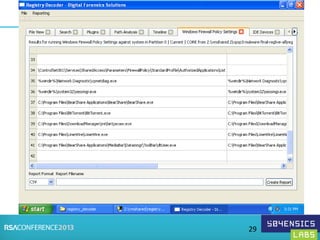
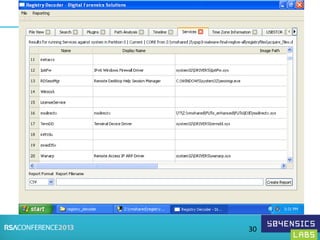
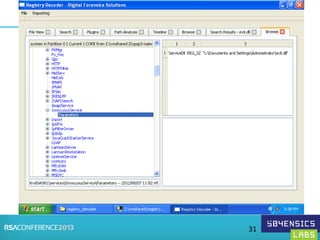
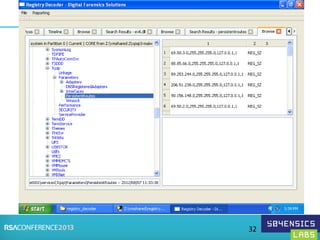
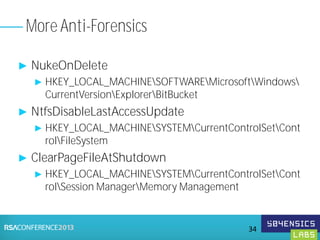
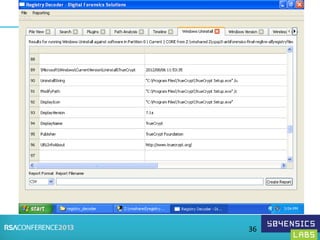
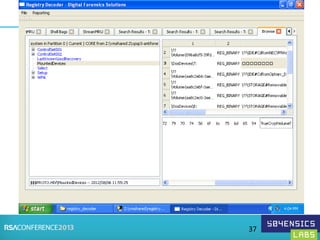
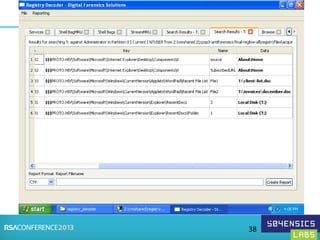
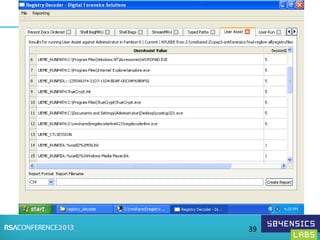
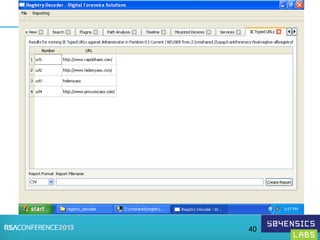
This document provides an overview of Registry Forensics and the Registry Decoder tool. It discusses how the Windows registry can be used to find evidence of data exfiltration, malware infections, and anti-forensics activities. It demonstrates how Registry Decoder allows automated acquisition, analysis and reporting of registry contents. Examples are given of specific registry keys and values that may indicate these types of activities.