This document provides an overview and outline for a research project titled "Finding Forensic Artifacts From Window Registry". The research aims to analyze the Windows Registry to find forensic artifacts from USB devices and unauthorized access. The summary provides background on the structure and contents of the Windows Registry. It also outlines some open problems regarding artifacts left in the Registry when USB devices are connected. The proposed solution will analyze specific locations in the Registry related to USB and other forensic artifacts. This research aims to build upon prior work by providing a deeper analysis of USB device identifiers and Registry locations beyond just installation locations.





















![XXVI
6.1.2 Conclusions
The majority of recovered artifacts were discovered in RAM, slack/free space, and FTK [Orphan]
directories. That being said, there was still enough information to provide useful information about
the user(s). Another commonality between the browsers is information contained within the System
Volume Information. For example, one study made the statement that it would be impossible to
trace residual information, other than USB identifiers, if a portable storage device was not
accessible to the investigator. Our research clearly shows that further data can still be recovered on
host machines without the portable storage device being present. Overall, our research is a valuable
resource pertaining to private and portable web browsing artifacts. Forensic investigations play a
significant role in today's working & legal environment, and thus it should be carefully considered.
The evidence provided in the registry is the most significant source of any investigation .The
actions performed on the computer gives the examiner an insight of the system. Thus, a careful
analysis of the Windows system Registry from a forensic point of view is the need of the hour & a
hot area of research in the present scenario. Study gathered and verified the existing knowledge
about the registry hive files .Study also revealed the importance of registry analysis by
demonstrating how it can help an investigator to progress in a case of tracking data transfer from a
system to a USB external device. Main aim to trace the registry artifacts left by the attacker on
Windows Registry .Further Study exhibits the importance of registry analysis by demonstrating the
computer artifacts left by VNC activities .Here, we expect this work could contribute in
understanding the characteristic of VNC & Windows 7 OS as a part of digital forensic investigation
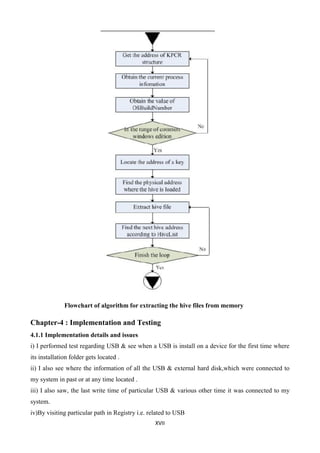
. In further studies , a method of extracting windows registry information from physical memory
has been proposed, which is proved to be effective in extracting hive files from windows dumps
imaged from Window XP, Windows Vista and Windows 7.How to make use of the registry data in
memory is also given.Finally, we can say Windows registry is a database that has been
implemented in the Microsoft Windows OS to hold the settings & configurations of the system
hardware application & user profiles. It is generally accepted that the Windows Registry holds
several potentially significant elements of information that may be valuable to forensic investigators
. Unique identifications should be noted to be persistent across identified platforms .The findings
raises some interesting issues ,for e.g.,an administrator can determine information of good known
authorized devices that have been attached to the system,from this information an administrator can
determine if any unauthorized USB based storage device has been installed on the respective
machine. Study also reveal that driver layer model can meet the requirements of majority
enterprises units for the security control of USB devices .Furthermore ,the key functions of
monitoring USB storage devices are all implemented in the driver layer .It is located in the Kernel
level,so it can control the USB storage devices preferentially .In final words we can say analyst](https://image.slidesharecdn.com/finalreport-150606084238-lva1-app6891/85/FINDING-FORENSIC-ARTIFACTS-FROM-WINDOW-REGISTRY-26-320.jpg)
![XXVII
must train himself to have a knowledge of the Windows system & the windows registry for proving
the authenticity of his all activities .
.
6.1.3 Future Works:-
Future work may include further RAM experiments, and more efficient methods to extract
information over an extended period of time instead of one controlled browsing session. Through
the detailed analysis of the registry hive files, activities of a system user can be traced. Hence
registry analysis should be carried as an integral part of digital forensic investigation process. We
can extend future work on comparison of registry & log files Moreover, more detailed information
can be extracted from windows registry as forensic evidence, which need to be done in future.
Moreover, we can work on crucial areas where a lot of information resides. We can work on USB &
how to track data theft from them. In future we can also emphasise more on remote access
technology & how to get more & more information about the attacker and to trace particular
artifacts of physically accessing the machine from the registry.Studies can also be set in the
directions like why in-built drivers get failed ,when particular USB was installed .Study of different
identifiers their end up locations ,tracing particular identifiers which remain active even after the
system has been shut down .Studying the communication principal of USB devices through the
study of WDM driver model ,study of USB filter drivers ,studying the Kernel with respect to USB
Window registry can be viewed as a Gold Mine of forensic investigation which could be used in
courts .In final words we can say that correlating our artefacts(findings) with timezone information
is a need of hour & a proper correlation between the two can put many intruders behind bars !!!!!!
References :-
1.Carvey, H., The Windows registry as a forensic resource, DigitalInvestigation, vol. 2(3), pp. 201–205,
Elsevier 2005.
2. Chang, K., Kim, G., Kim, K. and Kim, W., Initial Case AnalysisUsing Windows Registry in Computer
Forensics, Future GenerationCommunication and Networking, Volume 1, 6-8 Dec. 2007Page(s):564 –569.
[Online] DOI: 10.1109/FGCN.2007.151
3. Dashora, K., Tomar, D. S. and Rana, J. L., A Practical Approach forEvidence Gathering in Windows
Environment, International Journalof Computer Applications, Volume 5(10), August 2010.
4. Farmer, D. J., A Forensic Analysis of Windows Registry, Availableonline from
http://forensicfocus.com/downloads/windows-registryquick-reference.pdf, 2007.
5. Farmer, D. J., A Windows Registry Quick Reference: for the Everyday Examiner, Available online
fromhttp://eptuners.com/forensics/contents/A_Forensic_Examination_of_the_Windows_Registry.pdf,
2009.
6. Kim, Y. and Hong, D., Windows Registry and Hiding Suspects’Secret in Registry, In the Proceedings of the
2008 International.
7. www.wikipedia.com
8. Harlan. C, “The Windows Registry as a forensic resource”. Digital Investigation, Vol 2, pp. 201-205, 2005.
9. Timothy D.Morgan, “Recovering Deleted Data From the Windows Registry”. Digital Investigation, pp.33-
41, 2008.
10. Dolan-Gavitt.B, “Forensic Analysis of the Windows Registry in Memory”. Digital Investigation.
5(Supplement 1), pp.26-32, 2008.
11.Winhelponline. (2007). Determining the "Last Write Time" of a registry key?
from http://www.winhelponline.com/articles/12/1/](https://image.slidesharecdn.com/finalreport-150606084238-lva1-app6891/85/FINDING-FORENSIC-ARTIFACTS-FROM-WINDOW-REGISTRY-27-320.jpg)
