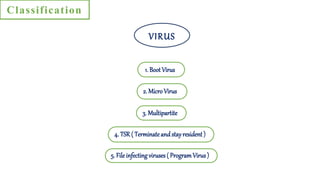
This document discusses computer viruses and anti-virus packages. It defines malware and viruses, explaining that viruses attach themselves to files and programs to spread. It describes different types of viruses like boot viruses, macro viruses, multipartite viruses, and file infecting viruses. Viruses can damage systems in various ways like interrupting use, modifying settings, and destroying data. The document recommends using antivirus software, firewalls, strong passwords, and updating systems to prevent virus infections.