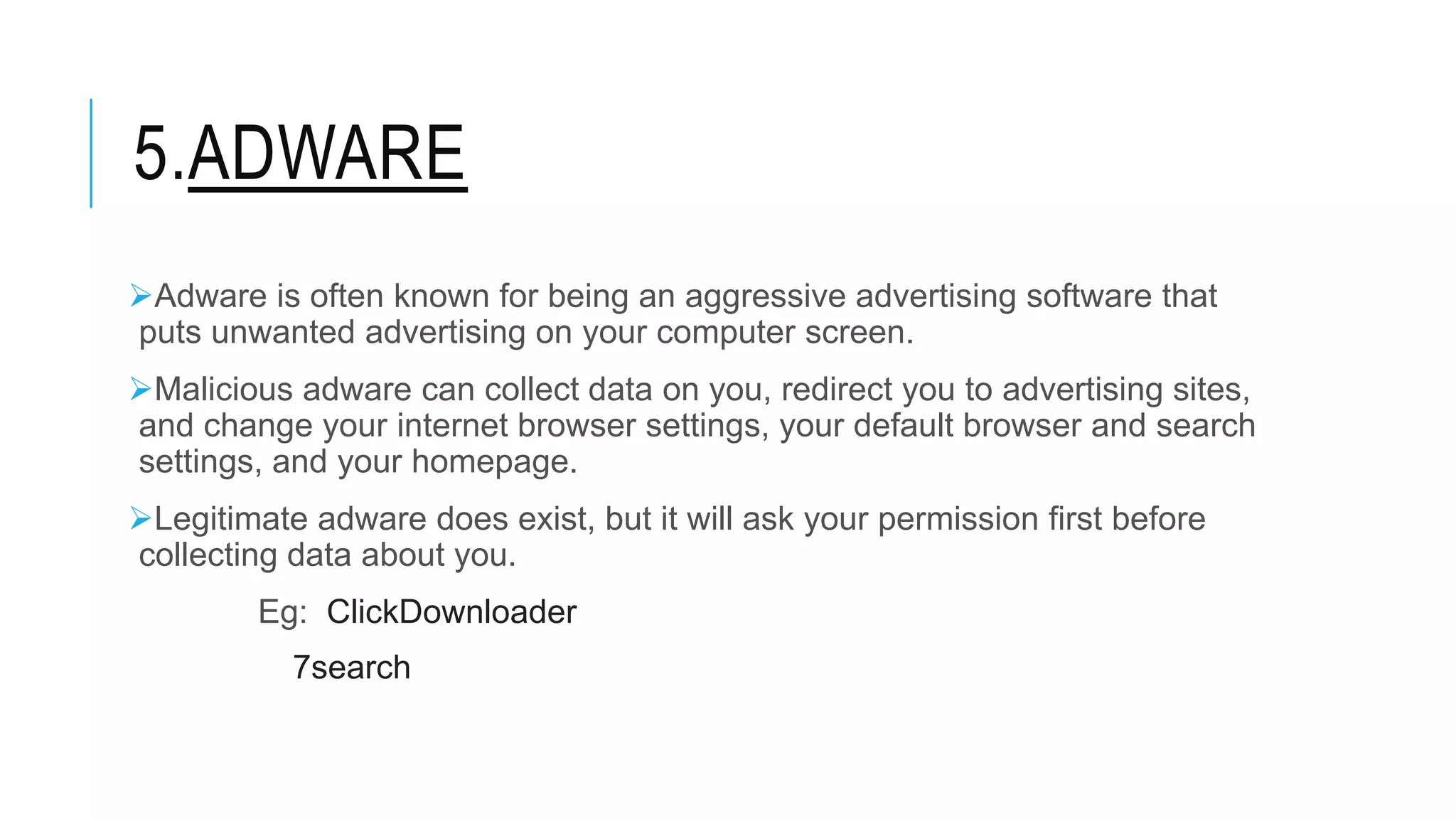
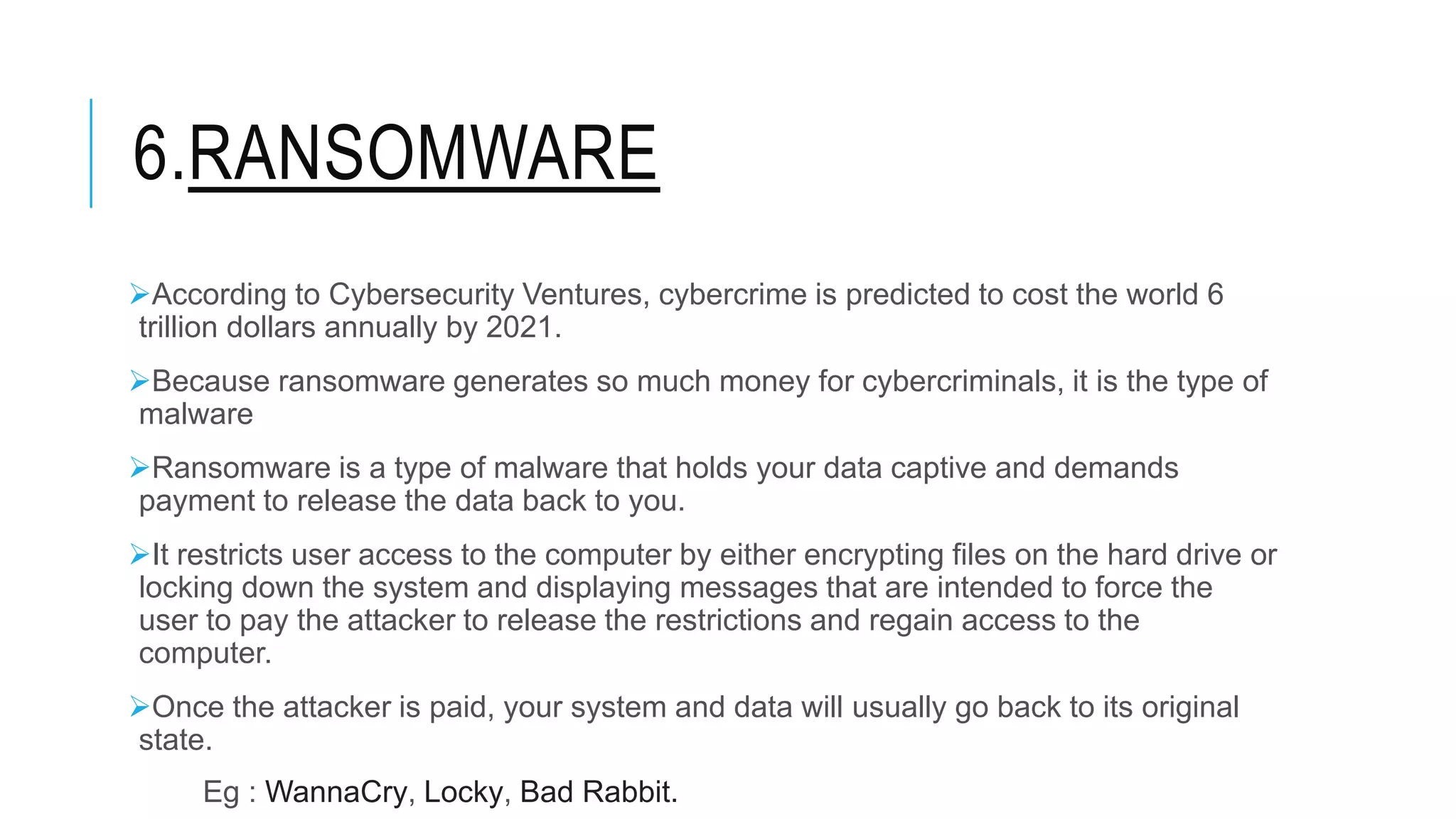
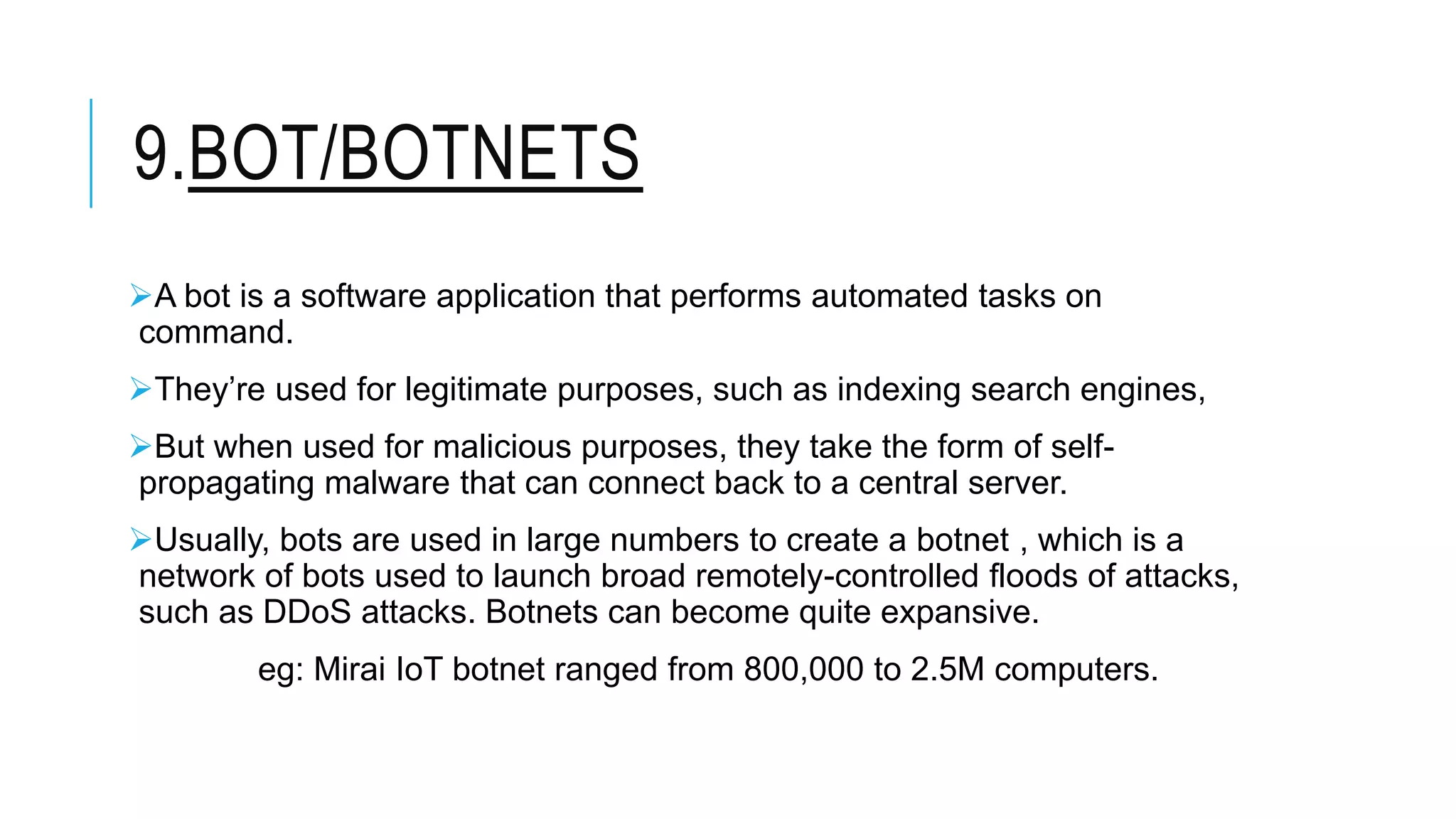
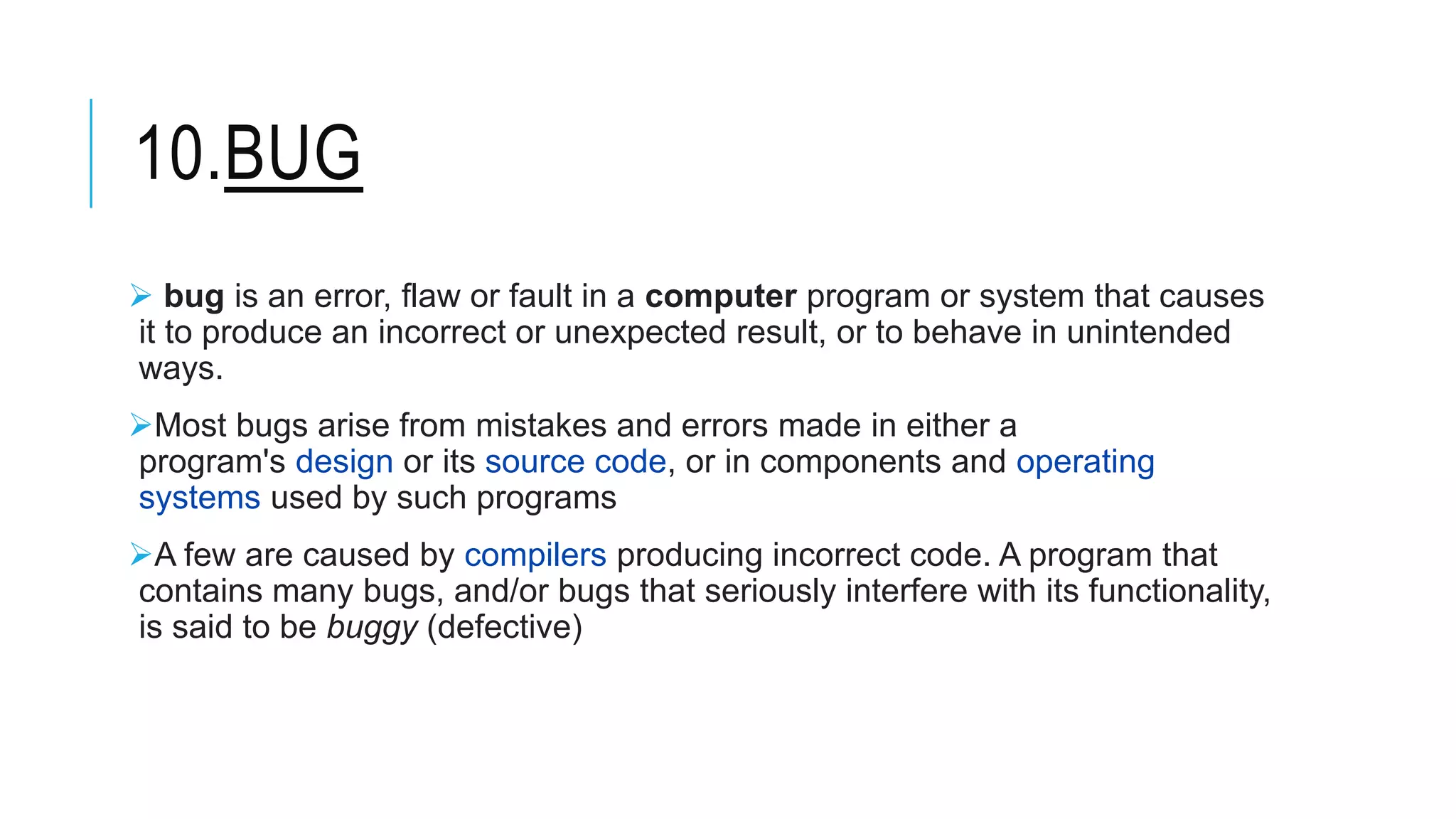
This document discusses different types of malware and methods for analyzing malware. It defines malware as malicious software designed to damage computers without consent. The document outlines 10 main types of malware: viruses, worms, Trojans, spyware, adware, ransomware, rootkits, keyloggers, botnets, and bugs. It also describes 3 methods of malware analysis: static analysis, which examines code without executing it; dynamic analysis, which observes behavior by running malware; and threat analysis, which identifies malware families and tracks criminal infrastructure over time.