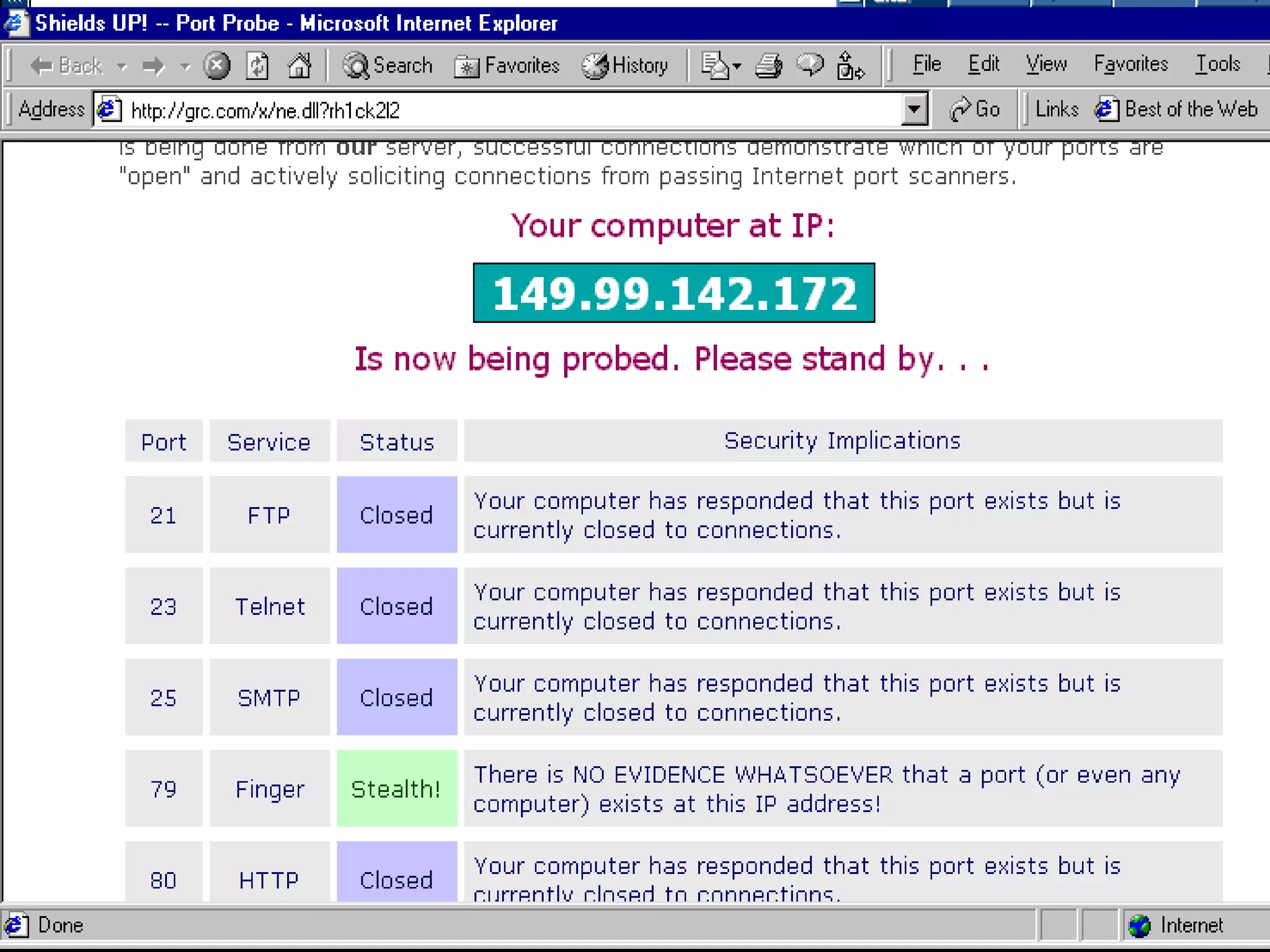
The document discusses various topics related to hackers and network intrusions, including:
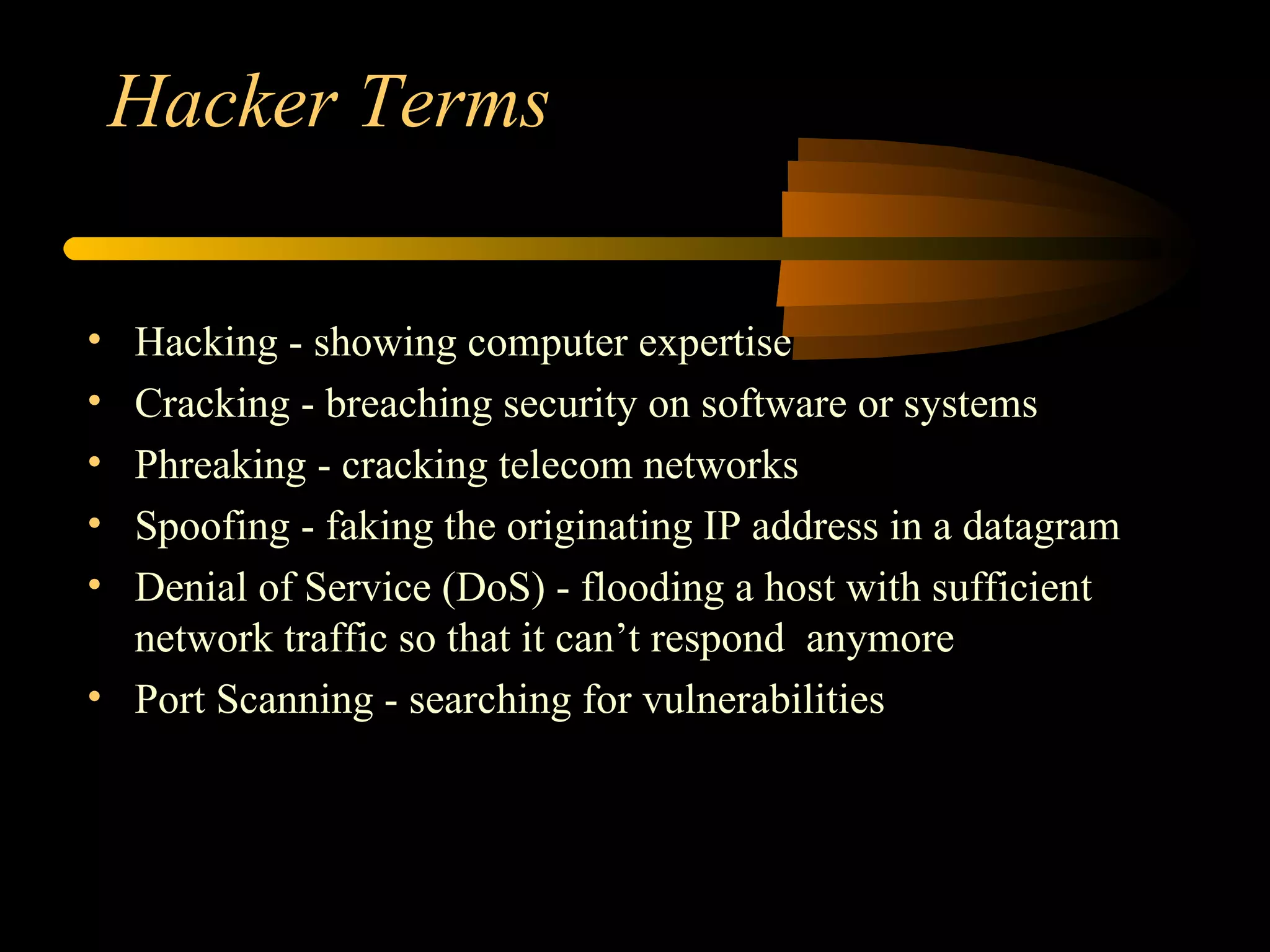
1) It defines common hacking terms like hacking, cracking, phreaking, spoofing, and denial of service attacks.
2) It describes different types of hackers like black hats, white hats, script kiddies, and criminal hackers.
3) It outlines common threats from hackers like denial of service attacks, data theft, and financial losses.
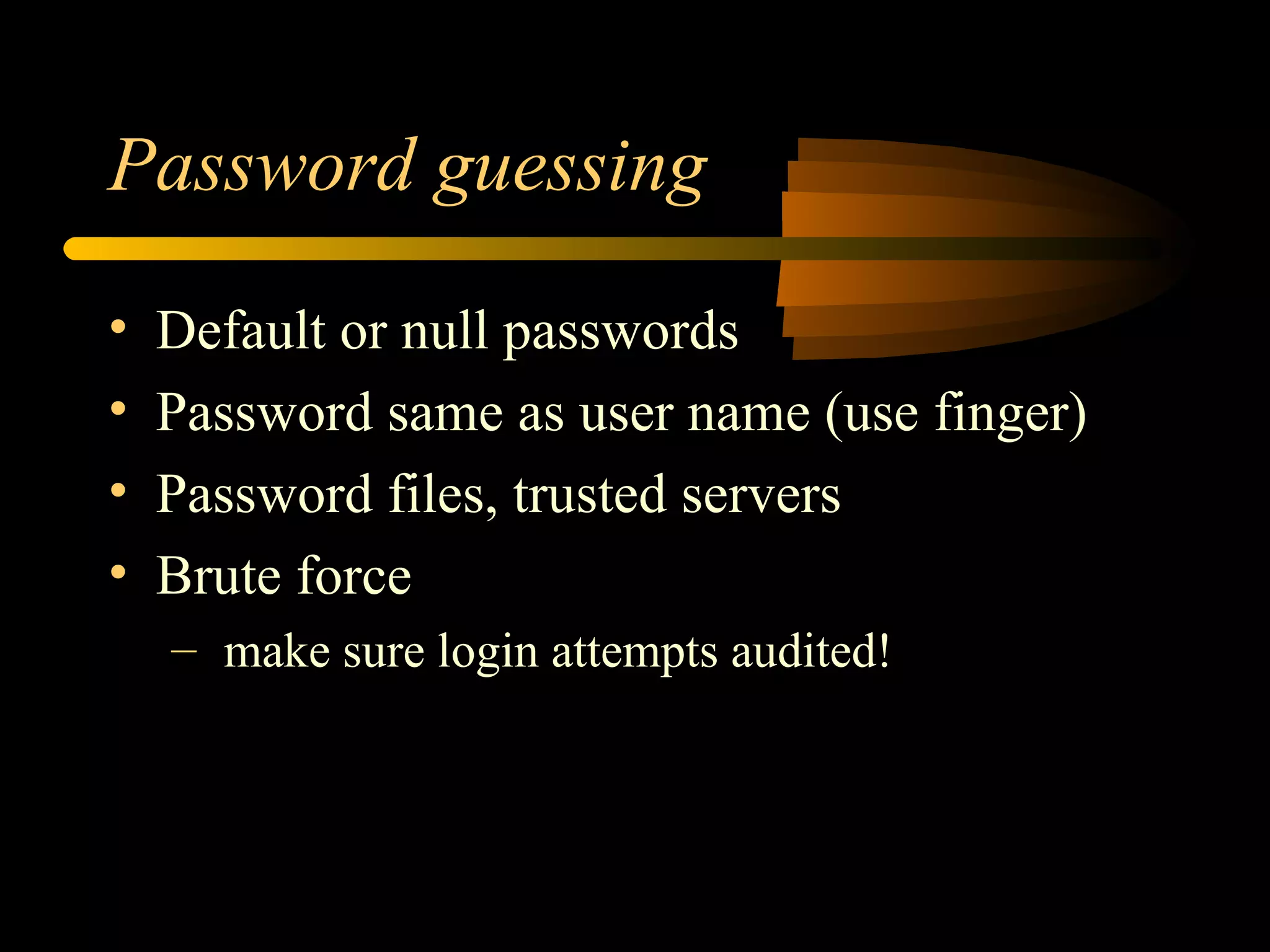
4) It discusses methods hackers use to gain access like exploiting software vulnerabilities, password guessing, and installing backdoors.