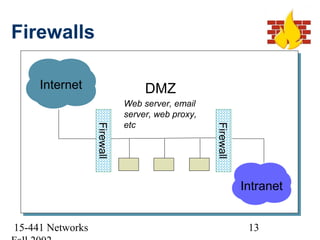
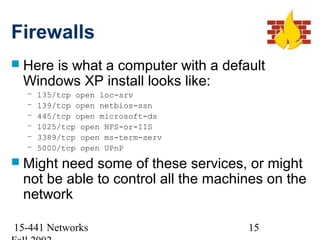
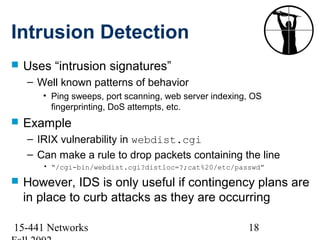
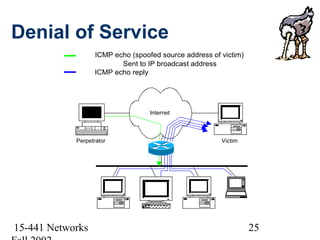
This document discusses network security and provides an overview of common security threats and countermeasures. It begins by defining security and explaining why security is needed to protect vital information, authenticate users, and ensure system availability. It then discusses who is vulnerable to security attacks, including individuals, organizations, and anyone on a network. The document outlines several common security attacks like firewalls, intrusion detection systems, denial of service attacks, TCP attacks, and packet sniffing. It provides details on each attack and potential countermeasures.