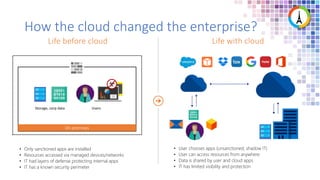
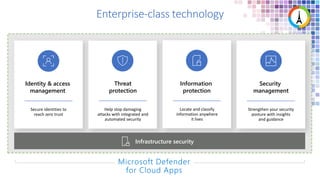
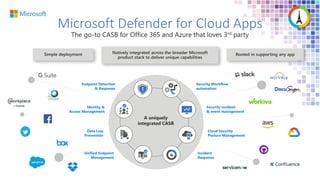
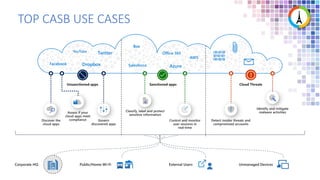
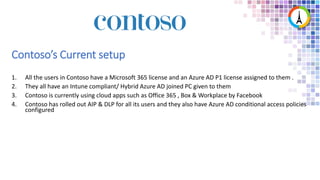
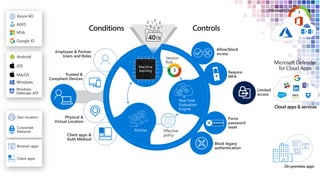
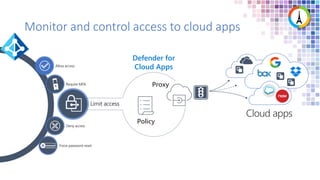
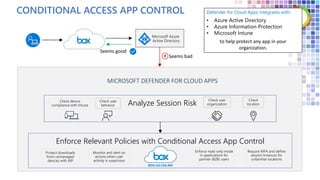
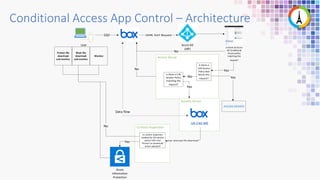
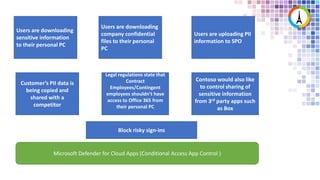
The Modern Workplace Conference Paris 2022 will be held online from January 24 to 26, focusing on the evolution of enterprise security in the cloud age. It discusses challenges like managing sensitive information and controlling access to cloud applications, highlighting Microsoft's security solutions. Attendees can expect insights on zero trust identity management, threat protection, and best practices for cloud app security.