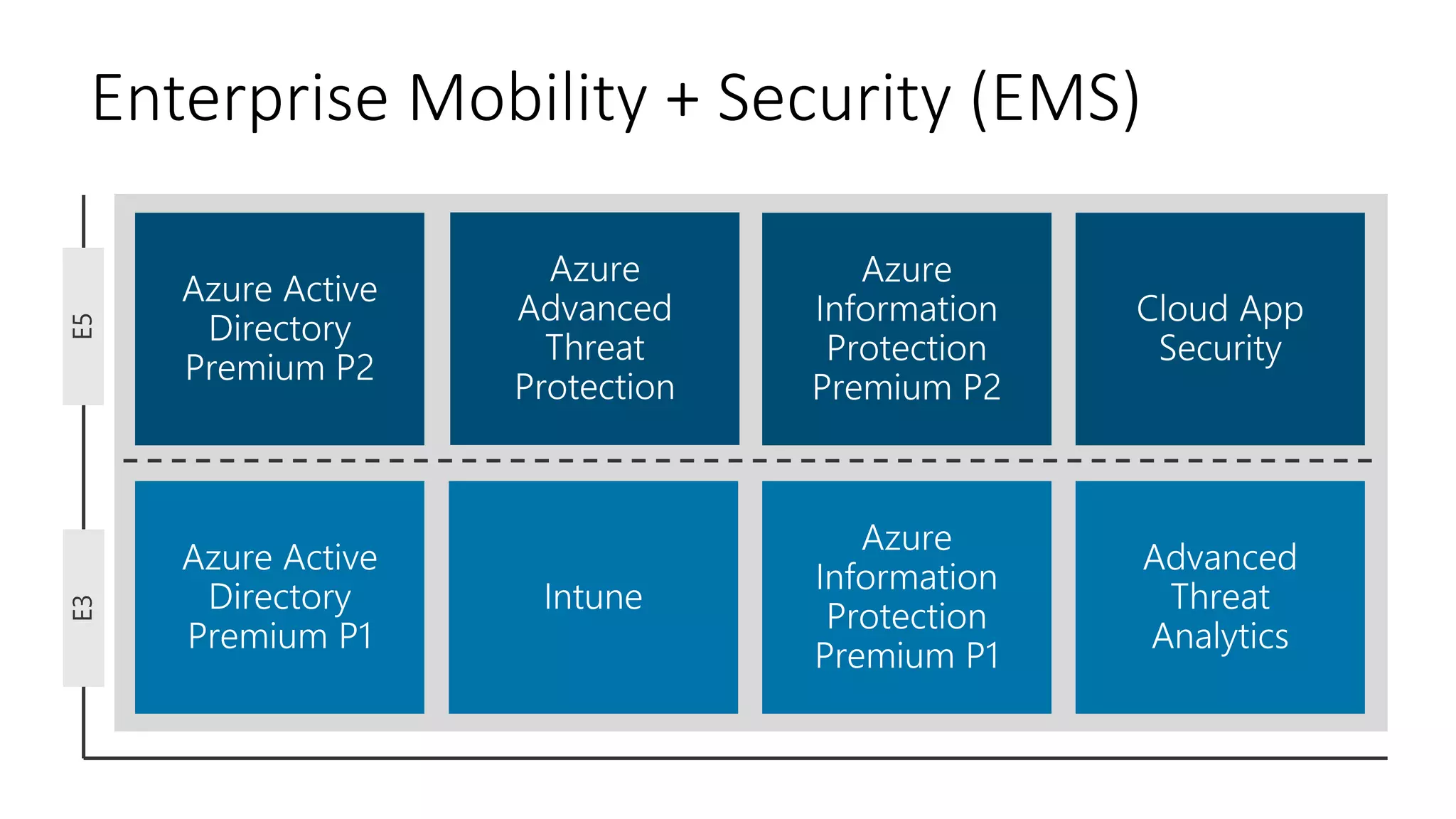
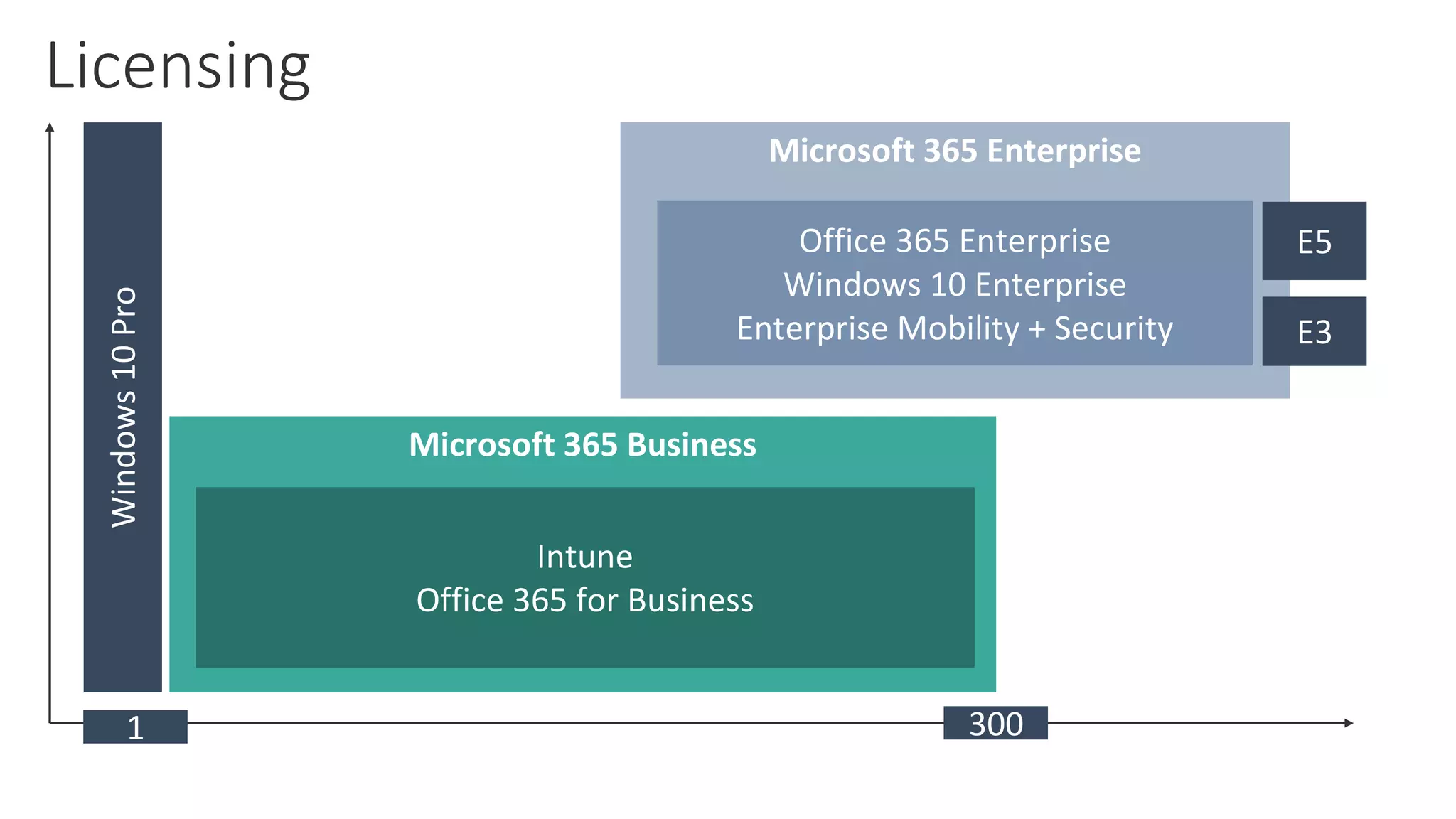
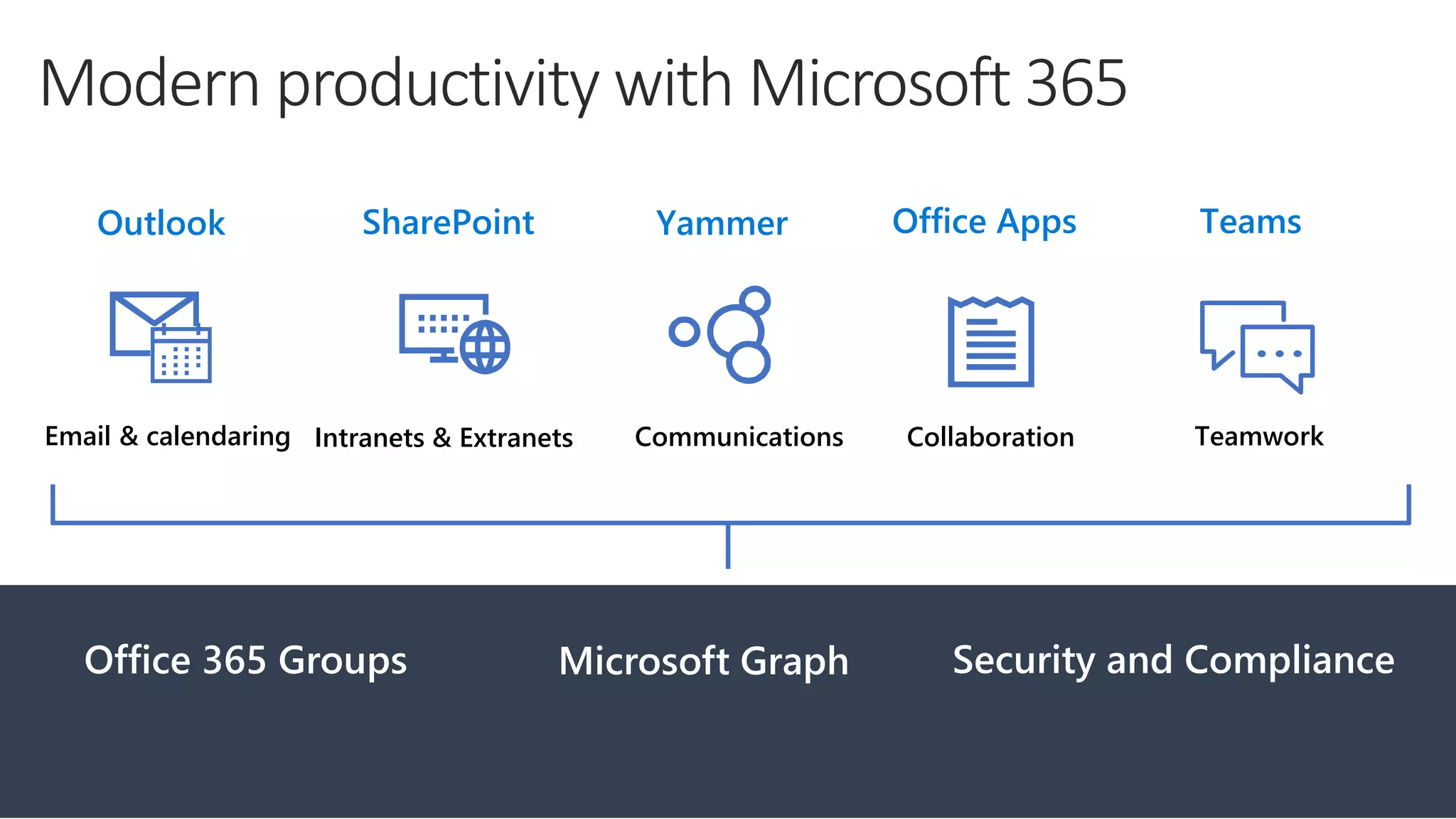
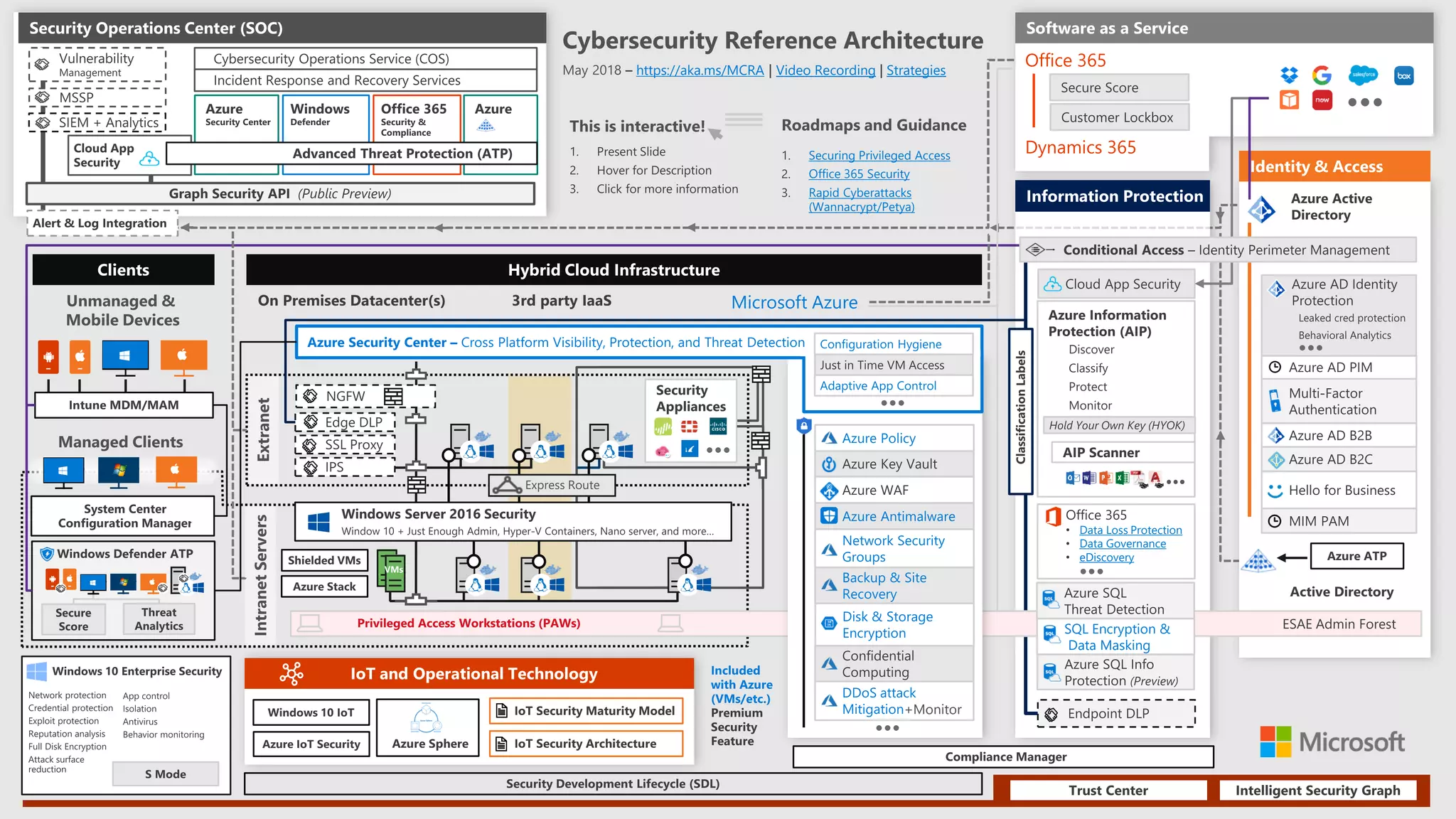
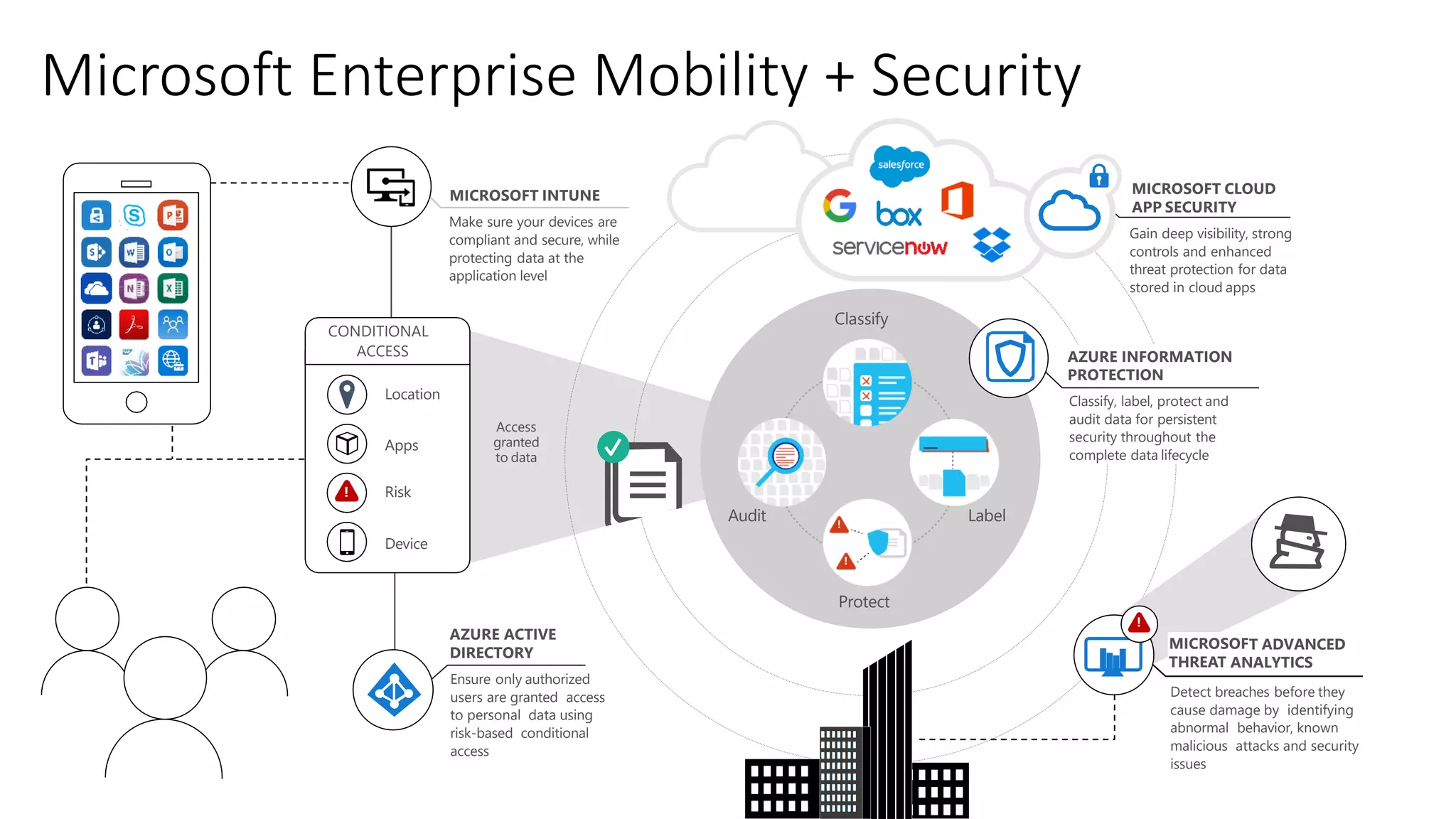
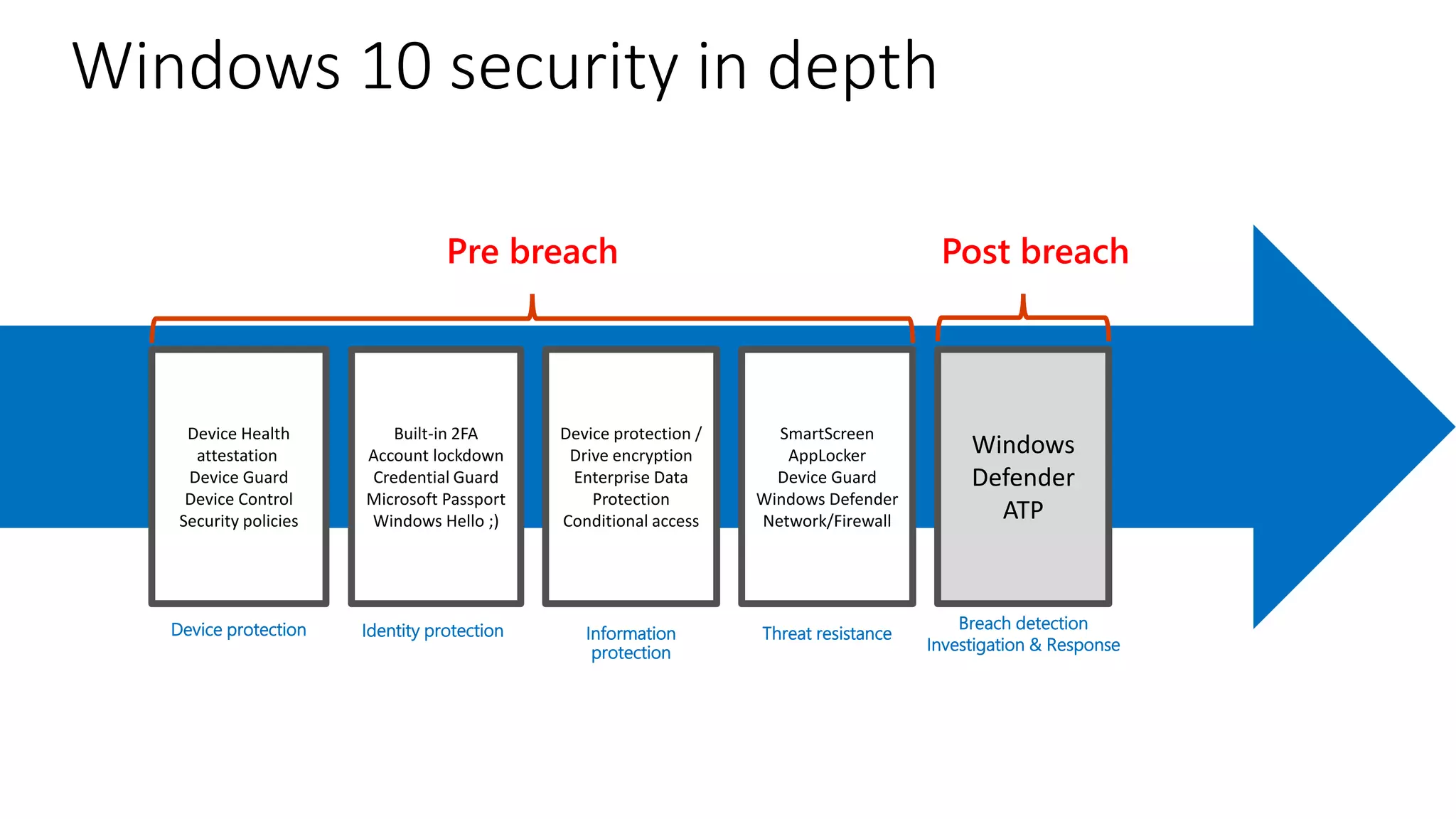
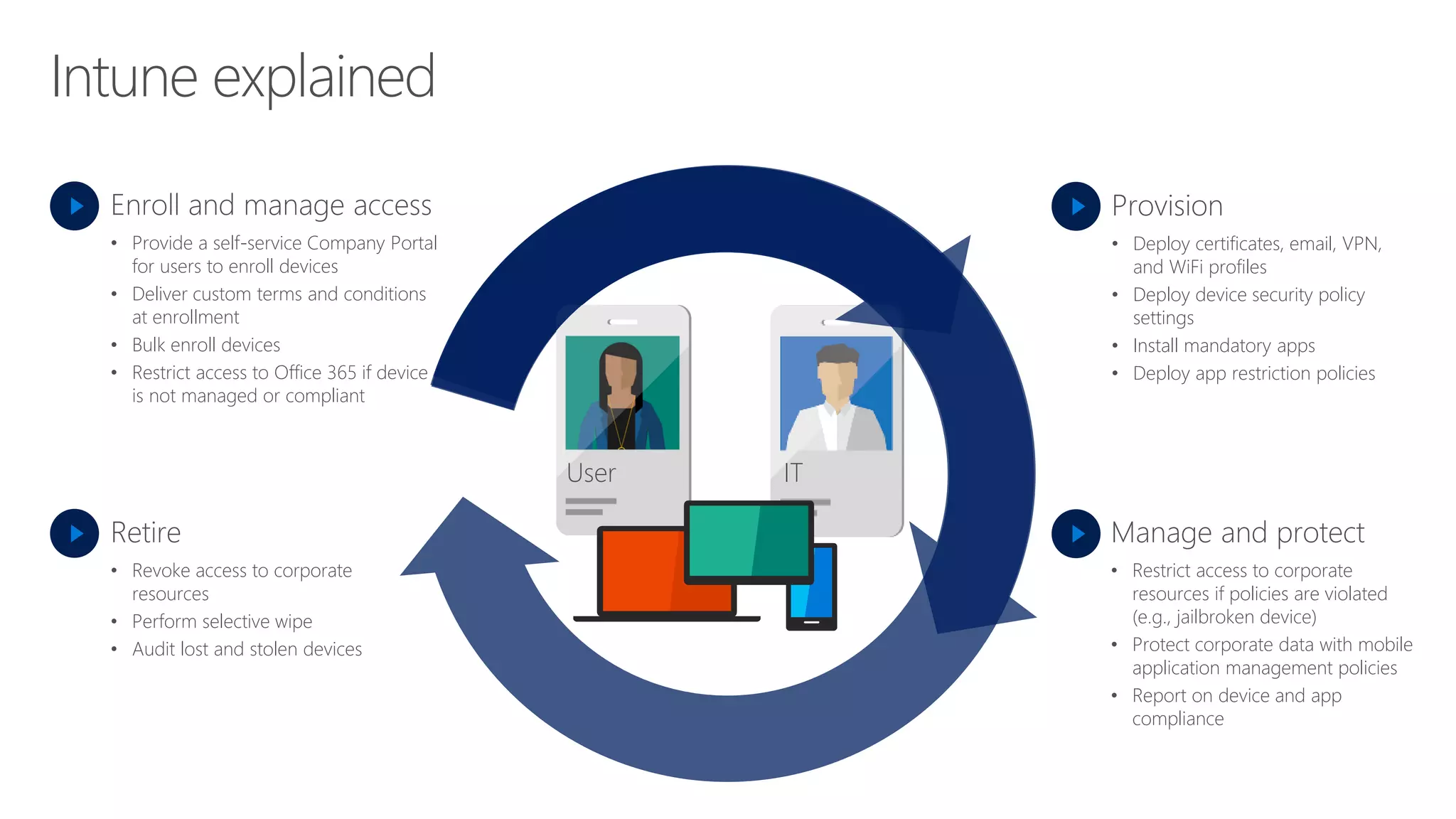
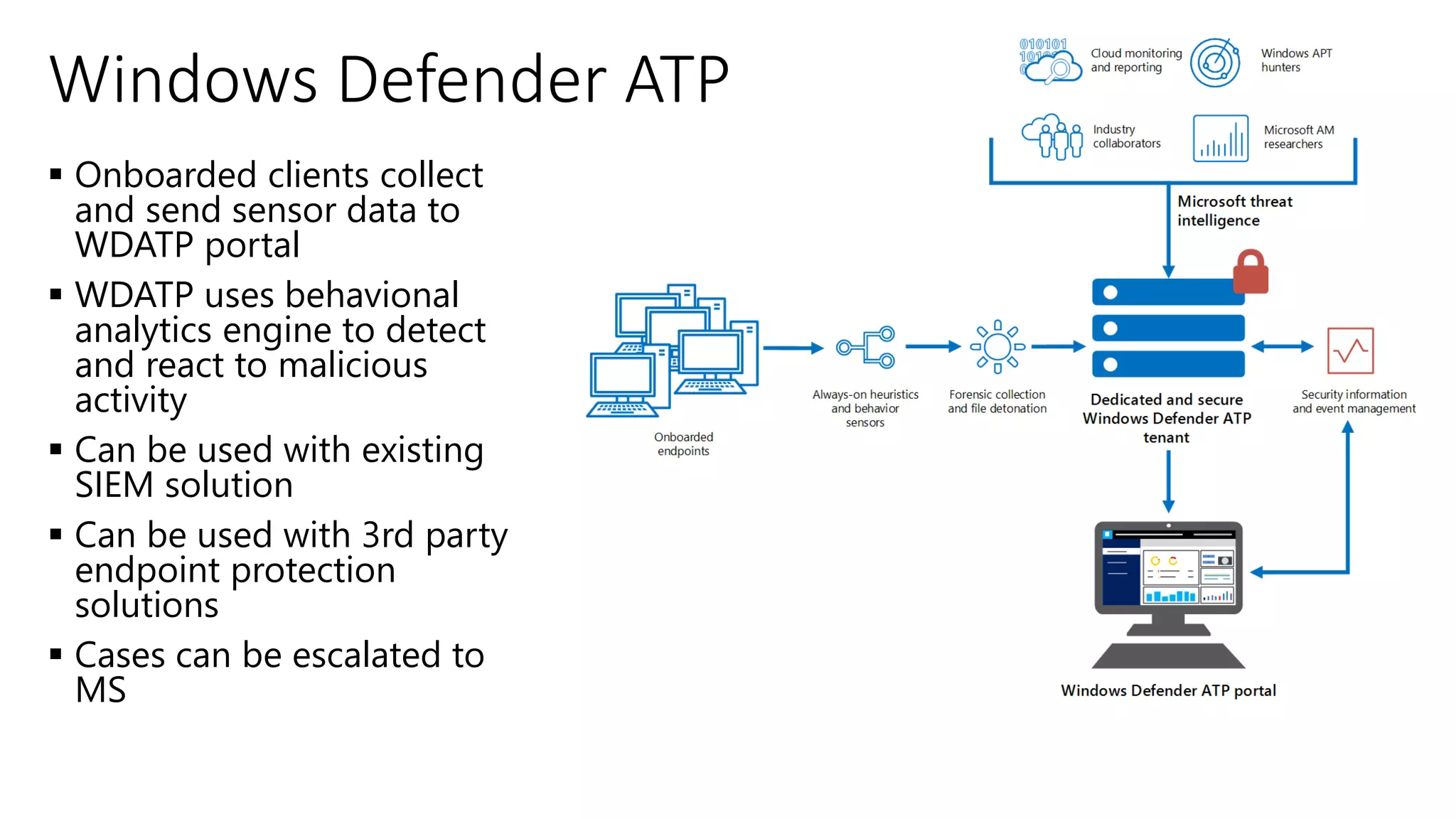
1) The document provides an overview of Microsoft 365 Enterprise and its key components such as Windows 10, Office 365, Enterprise Mobility + Security, and Azure Active Directory.
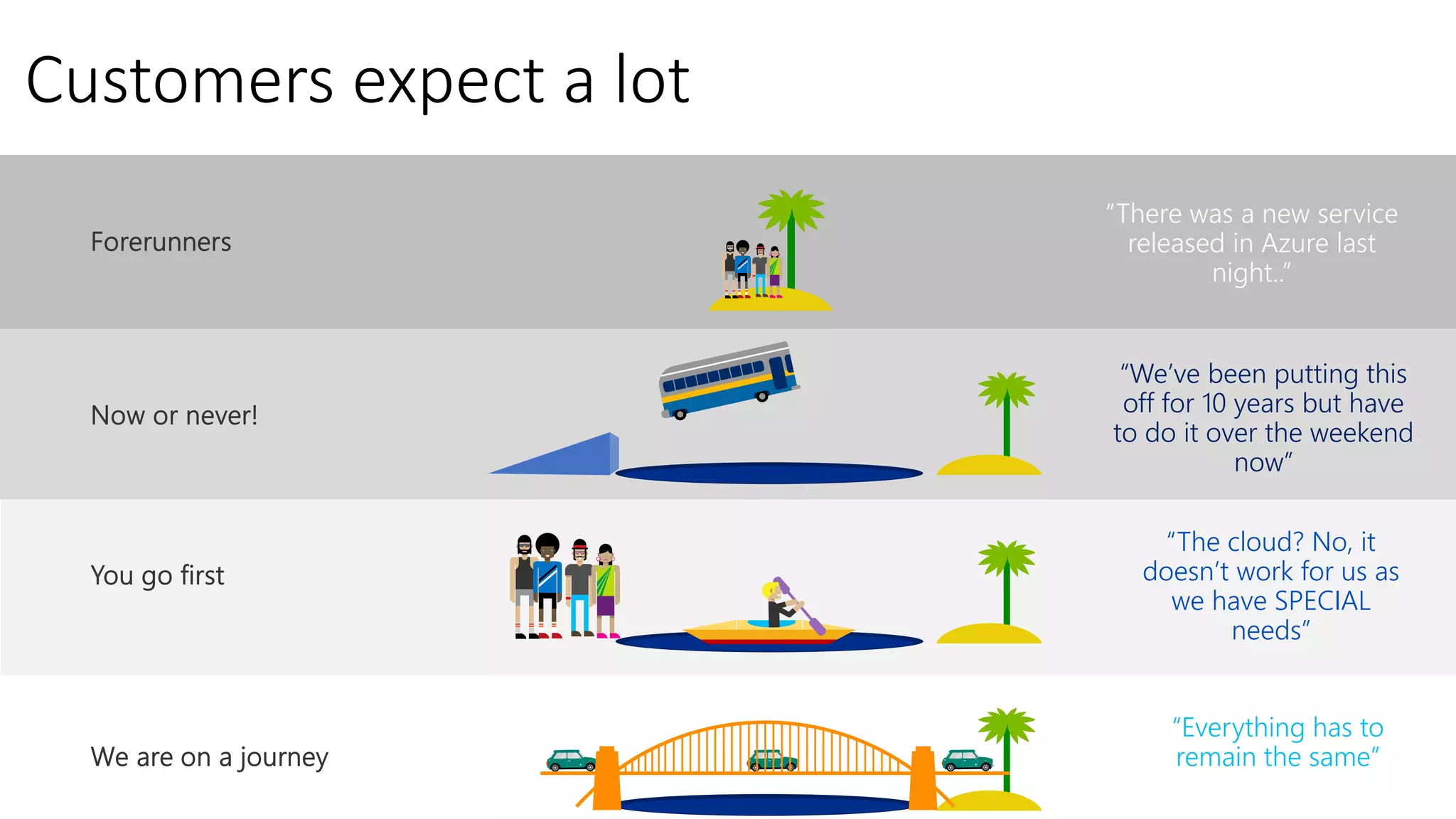
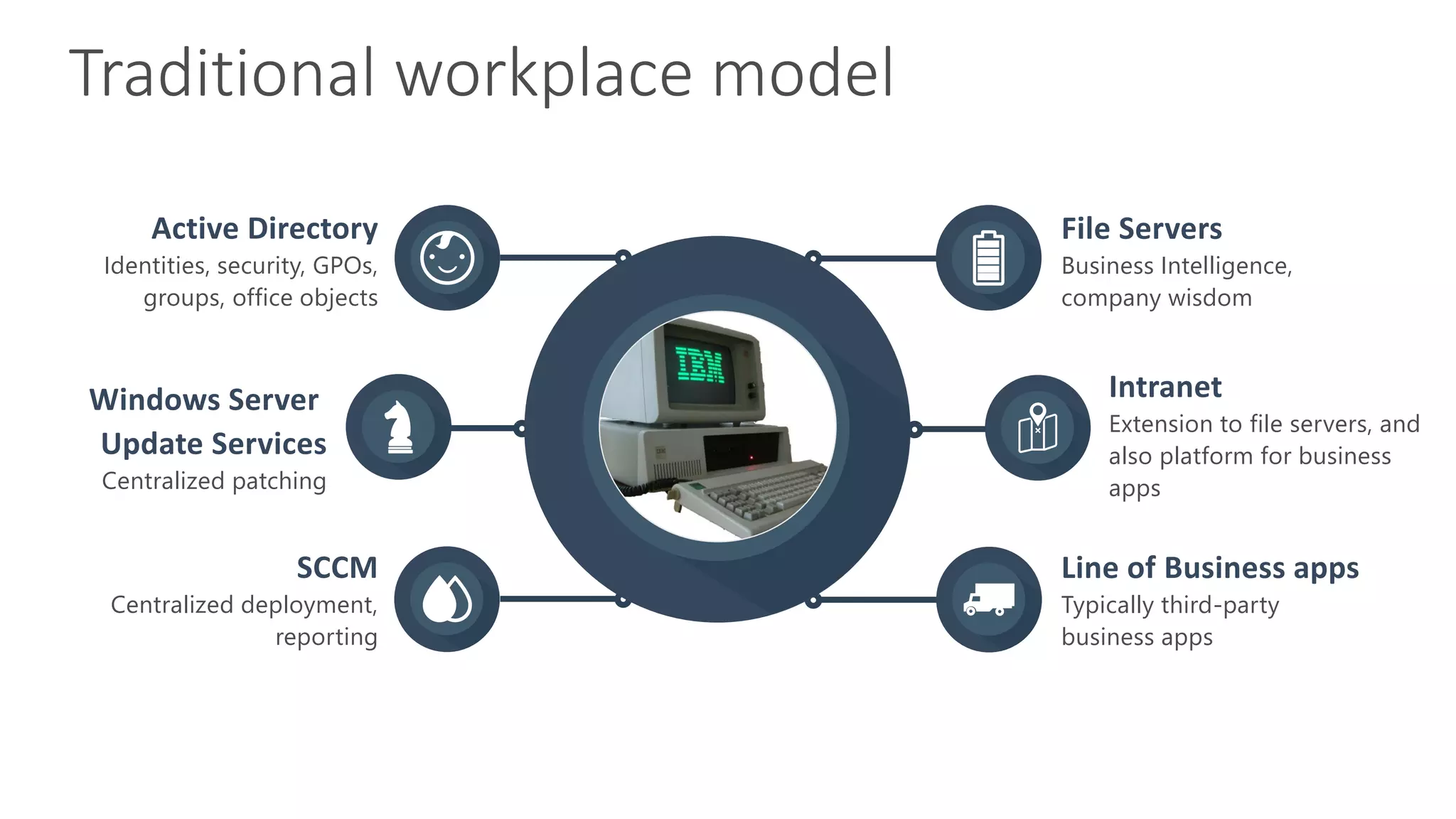
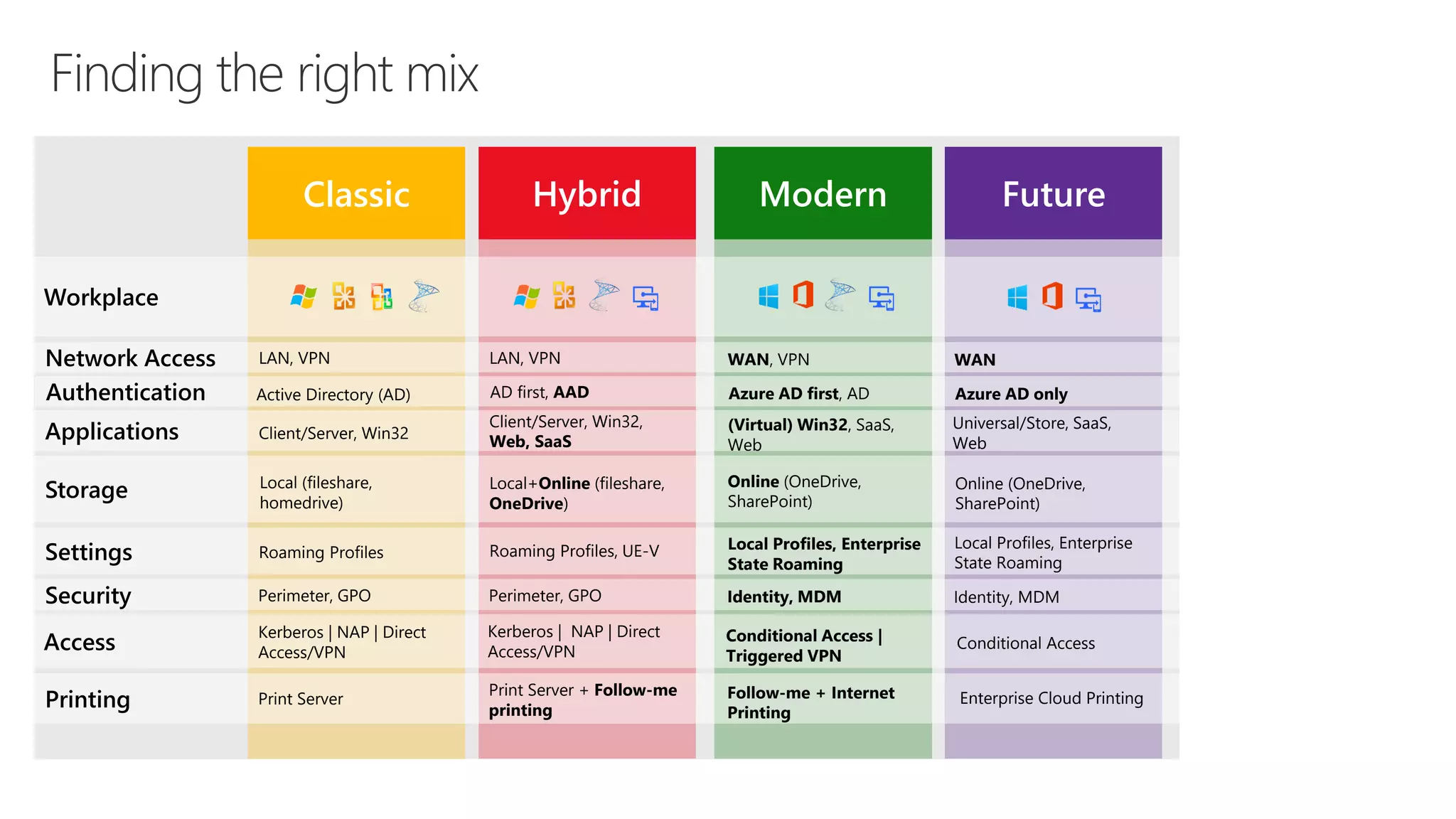
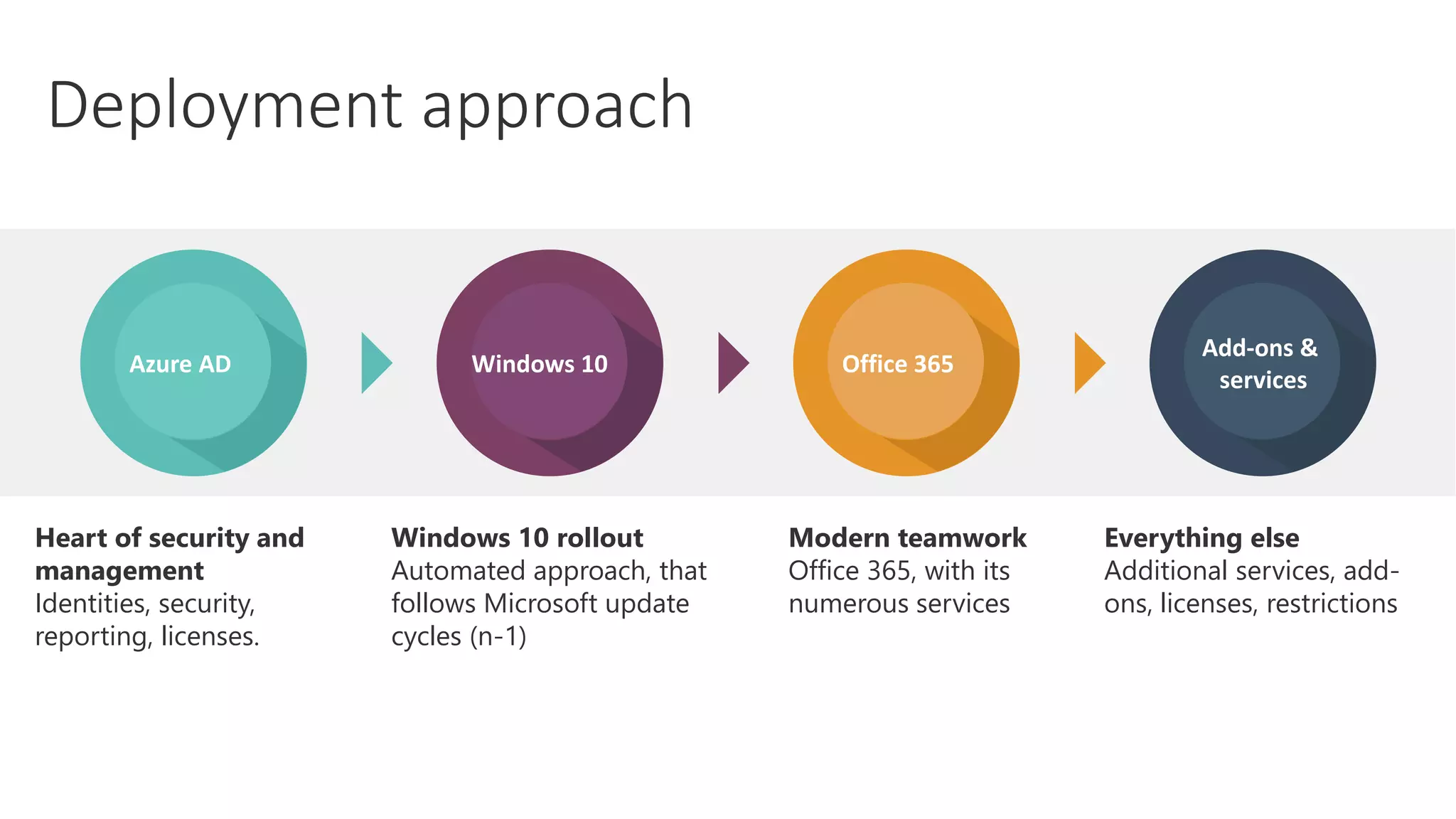
2) It discusses deployment strategies for Microsoft 365 including moving from on-premises to hybrid to cloud-based models and the steps involved in setting up identities, security, and applications.
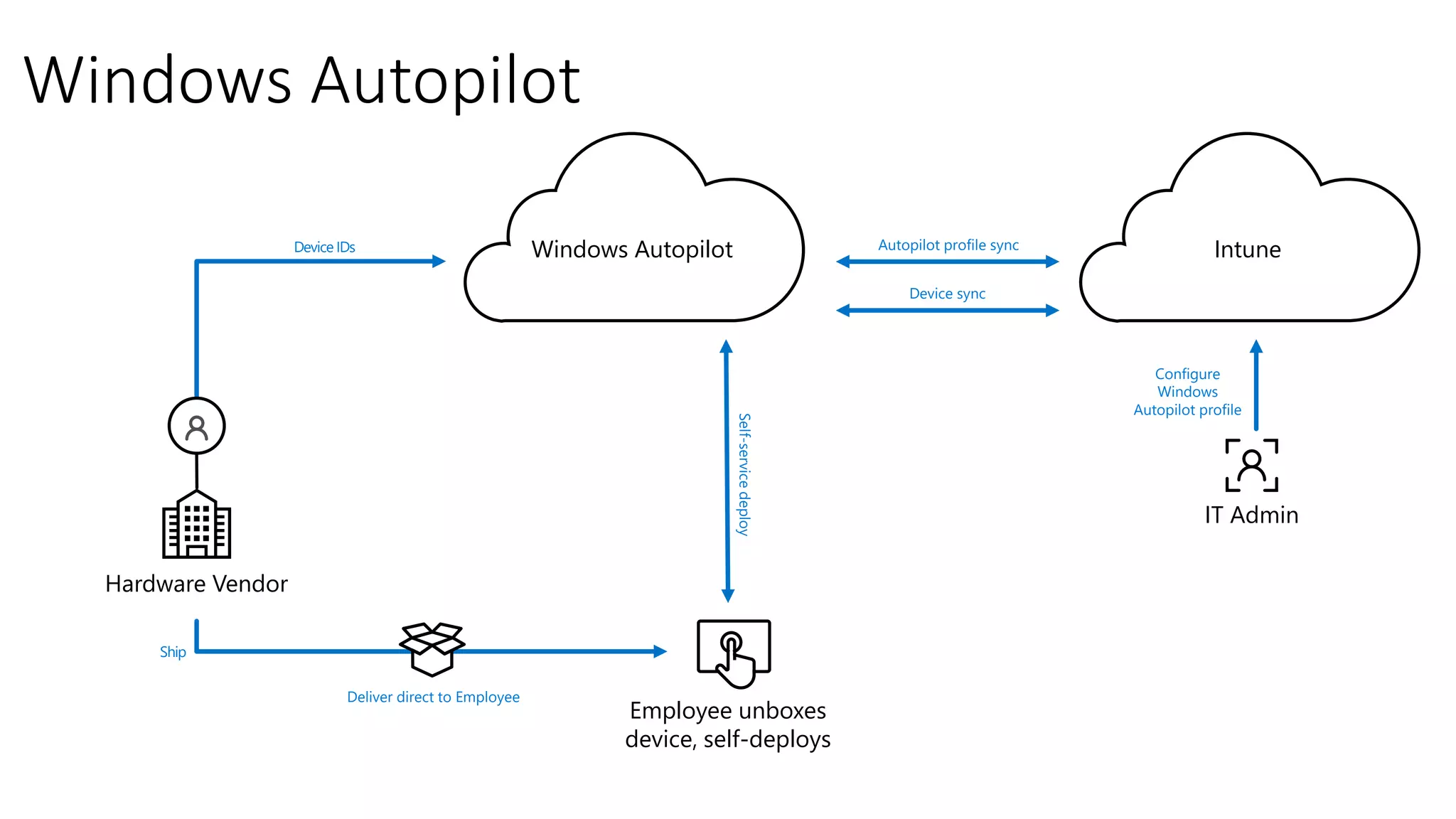
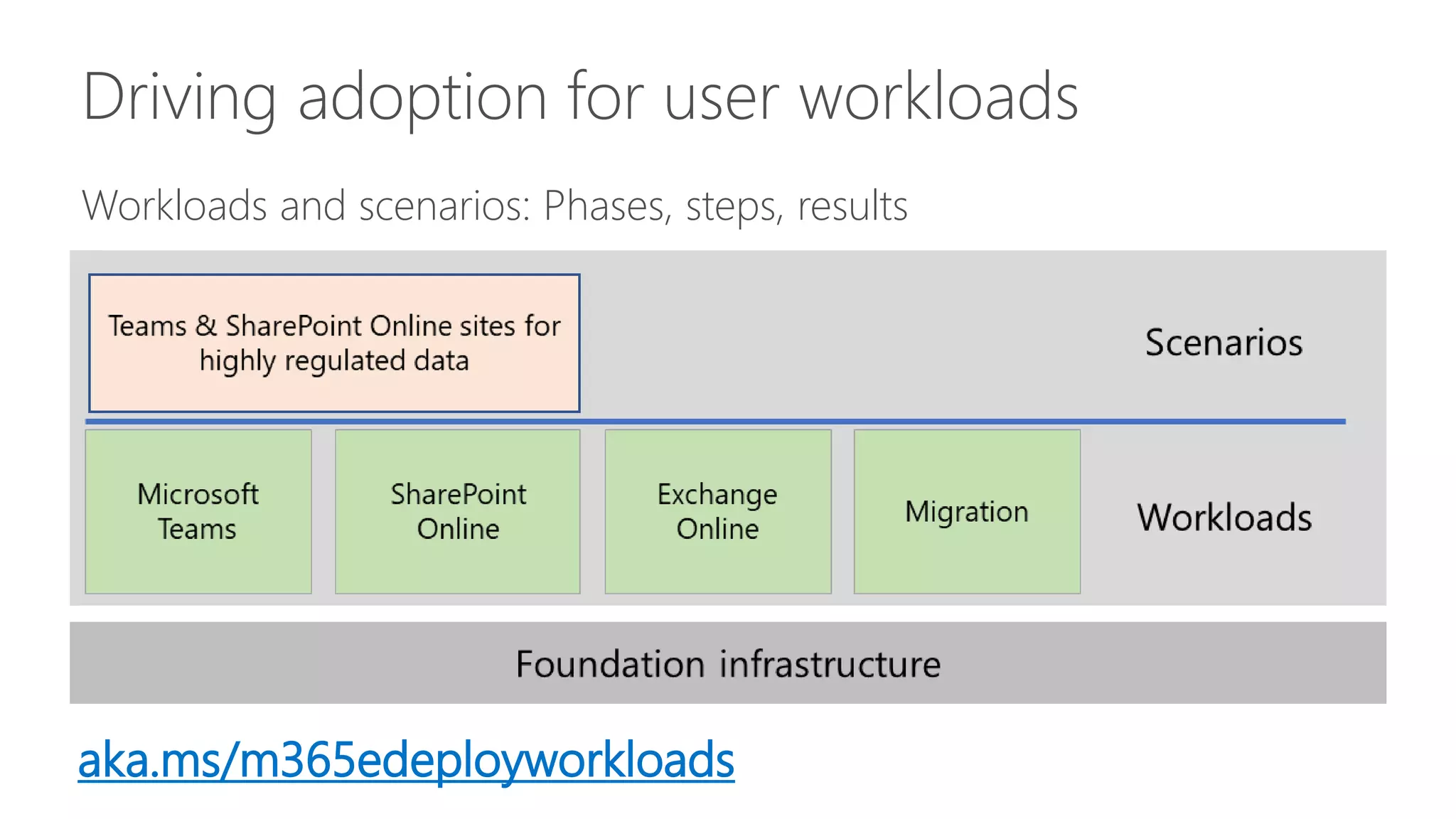
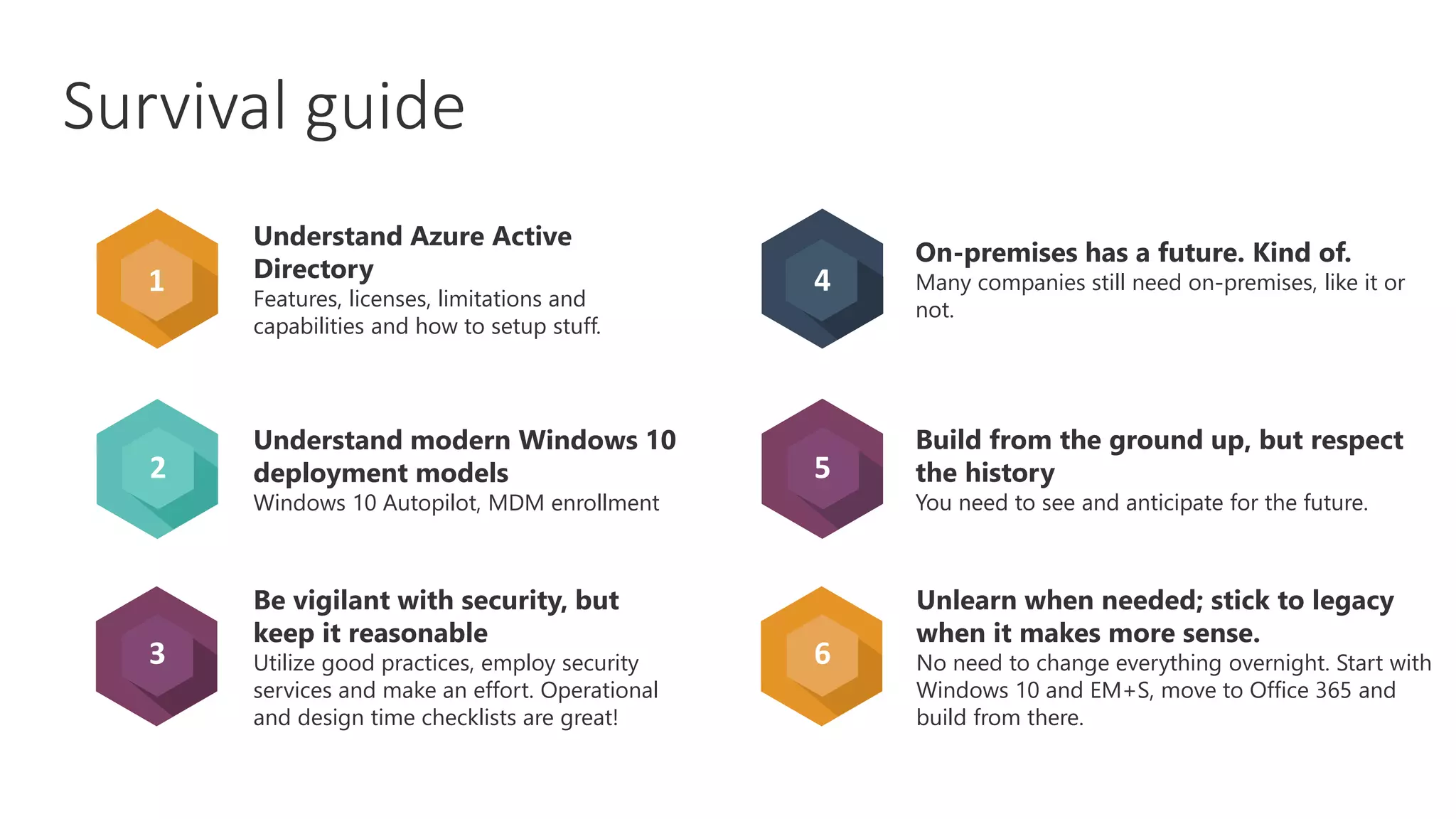
3) Recommendations are provided for getting started with Microsoft 365 such as understanding Azure Active Directory, deploying Windows 10 autopilot, focusing on security best practices, and moving existing workloads to Microsoft 365 gradually rather than all at once.