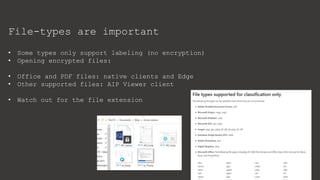
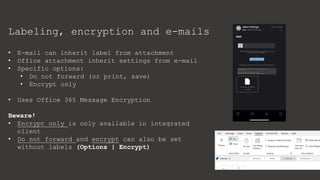
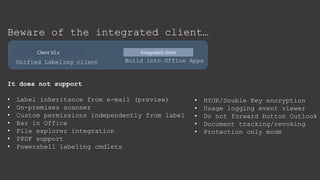
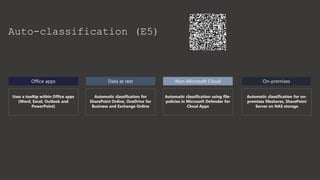
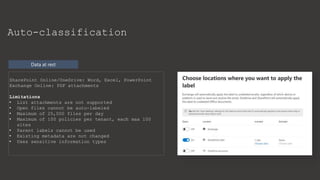
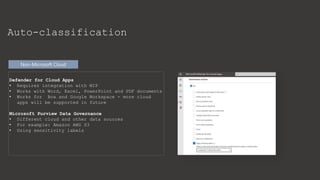
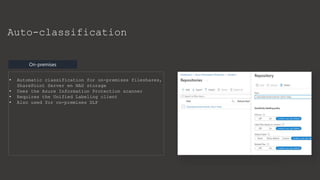
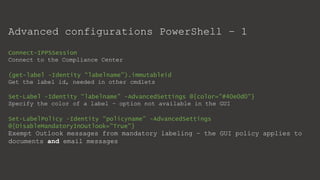
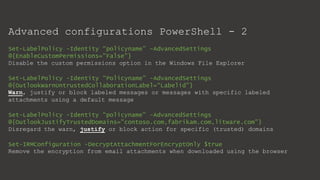
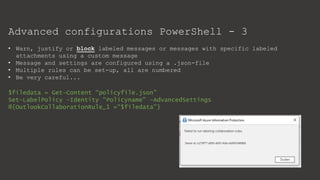
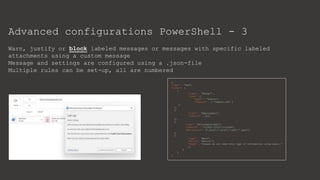
The document provides an overview of Microsoft Purview Information Protection and its functionalities, including sensitivity labels, automatic labeling, and advanced settings for data protection. It highlights the importance of managing insider risks and compliance through various tools and configurations. Additionally, it outlines the integration with different platforms, security measures, and advanced configurations available for optimal data governance and protection.