Embed presentation
Downloaded 22 times




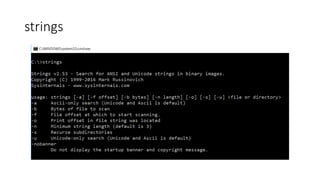
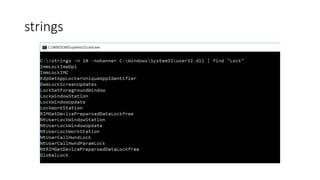
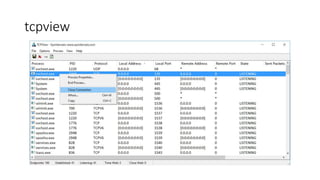
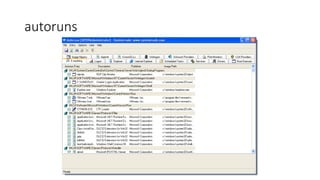
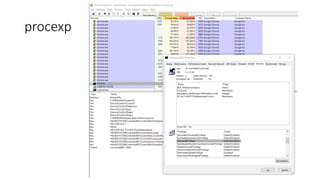
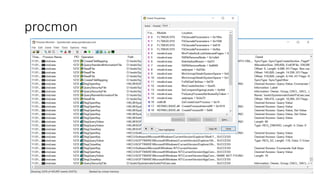
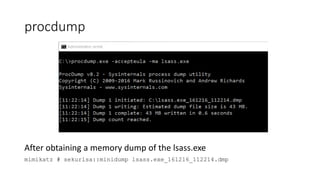
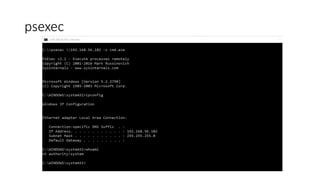



The document introduces Sysinternals tools, a collection of utilities developed to manage, diagnose, troubleshoot, and monitor Windows environments, originally created by Winternals Software LP and acquired by Microsoft in 2006. It highlights key tools such as Strings, TCPView, Autoruns, Process Explorer, Process Monitor, Procdump, and PsExec. Additionally, it includes references for further reading and insights from the author, Riyaz Walikar.













