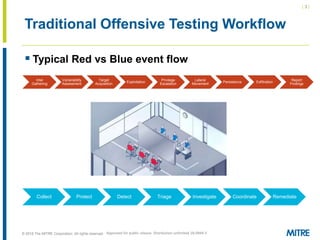
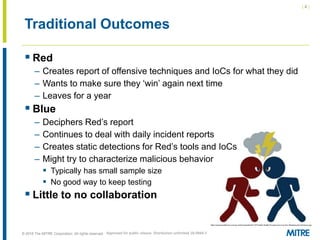
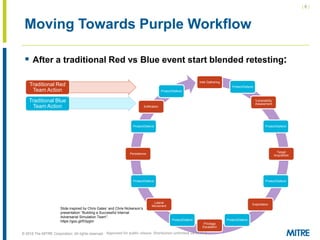
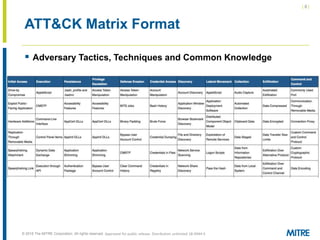
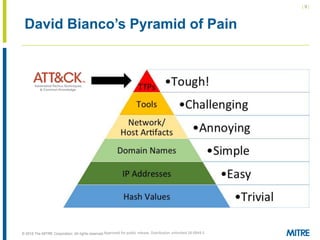
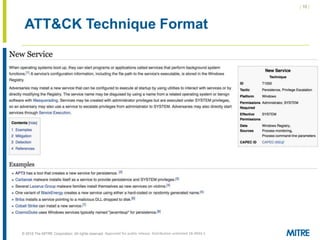
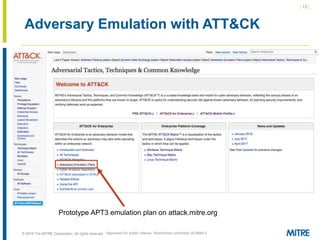
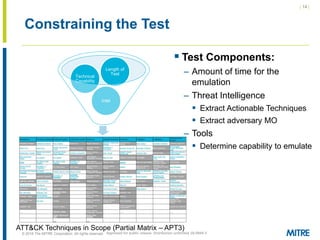
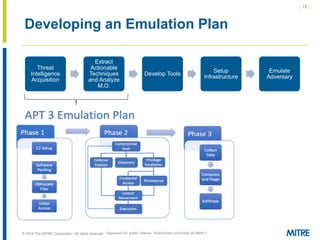
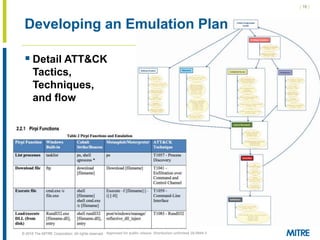
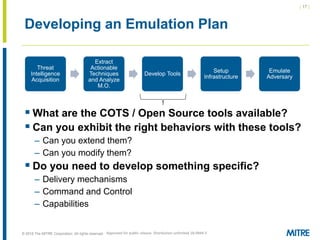
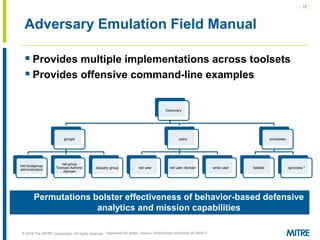
The document discusses the concept of threat-based purple teaming, which fosters cooperation between red and blue teams to enhance cybersecurity by sharing insights and strategies. It highlights the need for a common language and continuous testing to improve defensive capabilities, emphasizing behaviors over specific tool implementations. Additionally, it outlines the benefits of adversary emulation, providing tools and frameworks to better understand and mitigate potential threats.