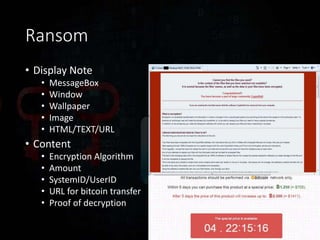
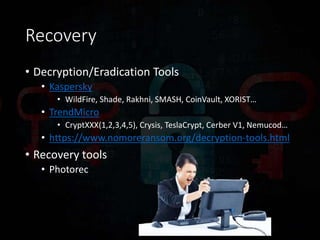
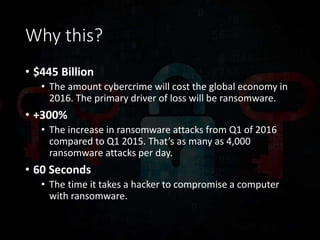
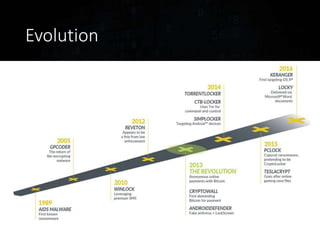
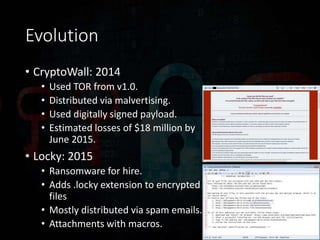
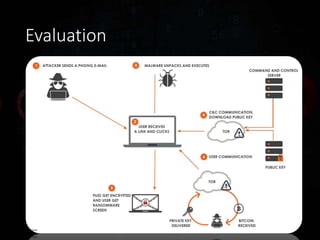
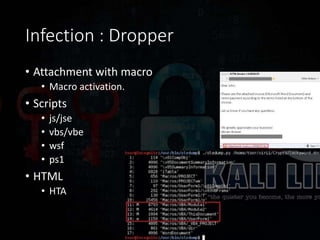
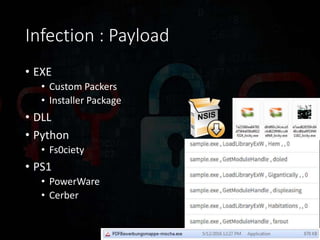
Ransomware has evolved significantly over time and now poses a major threat to the global economy. Ransomware attacks increased over 300% from Q1 2015 to Q1 2016, averaging 4,000 attacks per day. Ransomware operators can see returns over 1400% for a 30 day campaign, with the ransomware economy estimated to cost $1 billion per year. Early ransomware used encrypted file names and lockers, while modern variants like CryptoLocker and CryptoWall encrypt entire disks and use stolen encryption keys, making file recovery nearly impossible without paying ransoms in bitcoin. Researchers continue developing decryption tools, but education around avoiding risky behaviors remains the best defense against ransomware infections.


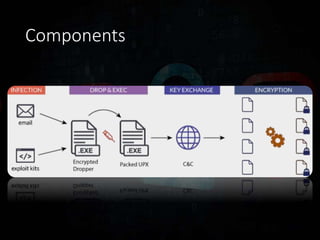







![Encryption
• Targets
• File Types
• doc, xls, ppt, jpg…
• Disks
• Extensions
• locky, crypt, locked, [random]…
• Exclusions
• Program Files
• Windows
• .exe, .dll, .sys](https://image.slidesharecdn.com/null-meet-pune-dec-2016-ransomware-3e-161210084546/85/3Es-of-Ransomware-19-320.jpg)