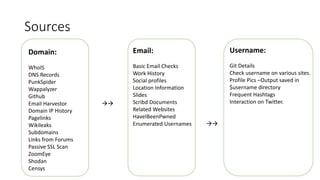
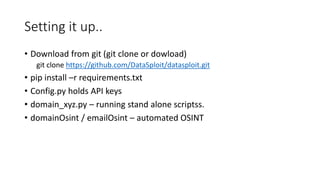
Datasploit is an automated OSINT tool designed for reconnaissance on domains, emails, usernames, and IPs, operating in passive mode without sending packets to targets. It offers various functionalities such as email checks, domain information retrieval, and integration with social network APIs, reporting in formats like CSV and JSON. The project welcomes contributions and feedback from users and provides setup instructions via GitHub.