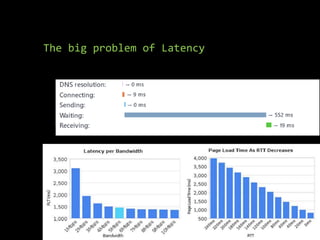
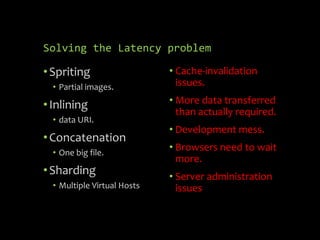
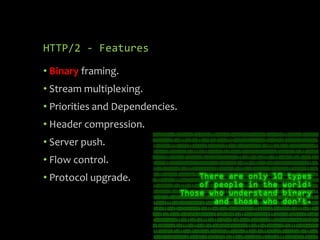
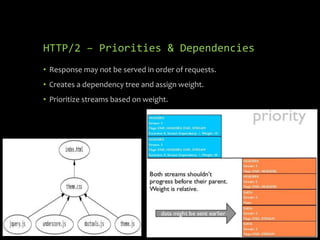
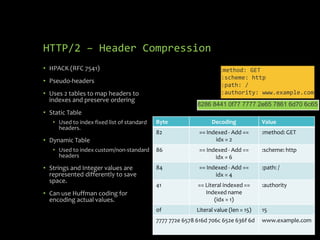
HTTP/2 provides improvements over HTTP/1.1 by using binary framing, stream multiplexing, header compression and server push to reduce latency. It retains HTTP semantics and promotes the use of TLS for security. While improving performance, it also brings challenges for web application firewalls and other intermediaries due to its binary nature. Future protocols like QUIC aim to further reduce latency by running HTTP/2 over UDP instead of TCP.