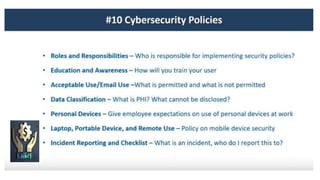
HIPAA is a federal law that requires the protection of sensitive patient health information. It established national standards to protect patients' medical records and other personal health information from being disclosed without consent or knowledge. The U.S. Department of Health and Human Services issued rules under HIPAA, including the Privacy Rule and Security Rule, which protect health information and set guidelines for how it can be collected, used, and shared. HIPAA gives patients more control over their information and defines penalties for any violations of its standards.