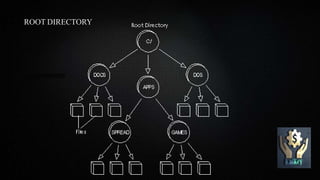
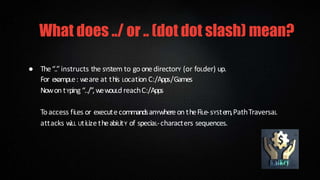
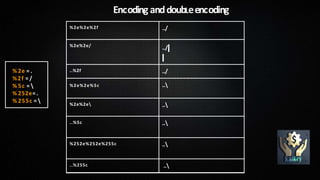
Path traversal attacks aim to access files outside the web root folder by using special character sequences like "../" to traverse directories. These attacks work by exploiting the ability of web servers to follow links containing such sequences to access files anywhere on the file system. Preventing path traversal attacks involves filtering user input to remove special characters, ensuring the web server is configured securely, keeping sensitive files outside the web root, and keeping software updated.