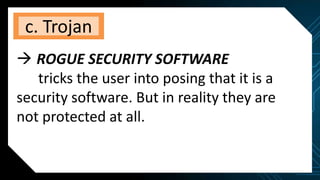
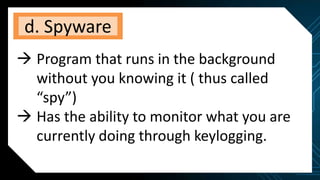
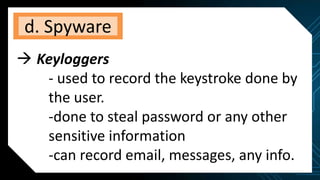
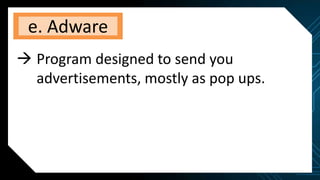
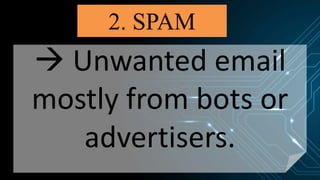
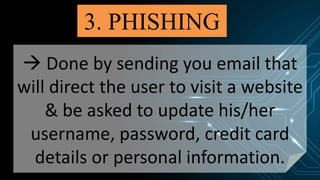
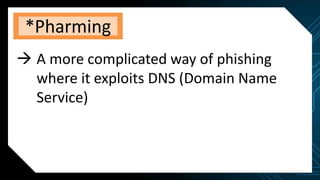
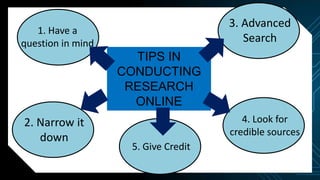
This document discusses various internet threats such as malware, spam, and phishing. It defines different types of malware like viruses, worms, trojans, spyware and adware. Viruses and worms are malicious programs that replicate and spread from one computer to another. Trojans pose as useful programs but leave computers unprotected. Spyware and keyloggers monitor users' activities without their knowledge. Spam refers to unwanted emails, while phishing tricks users into sharing private information on fake websites. It also provides tips to avoid copyright infringement and conduct safe online research.