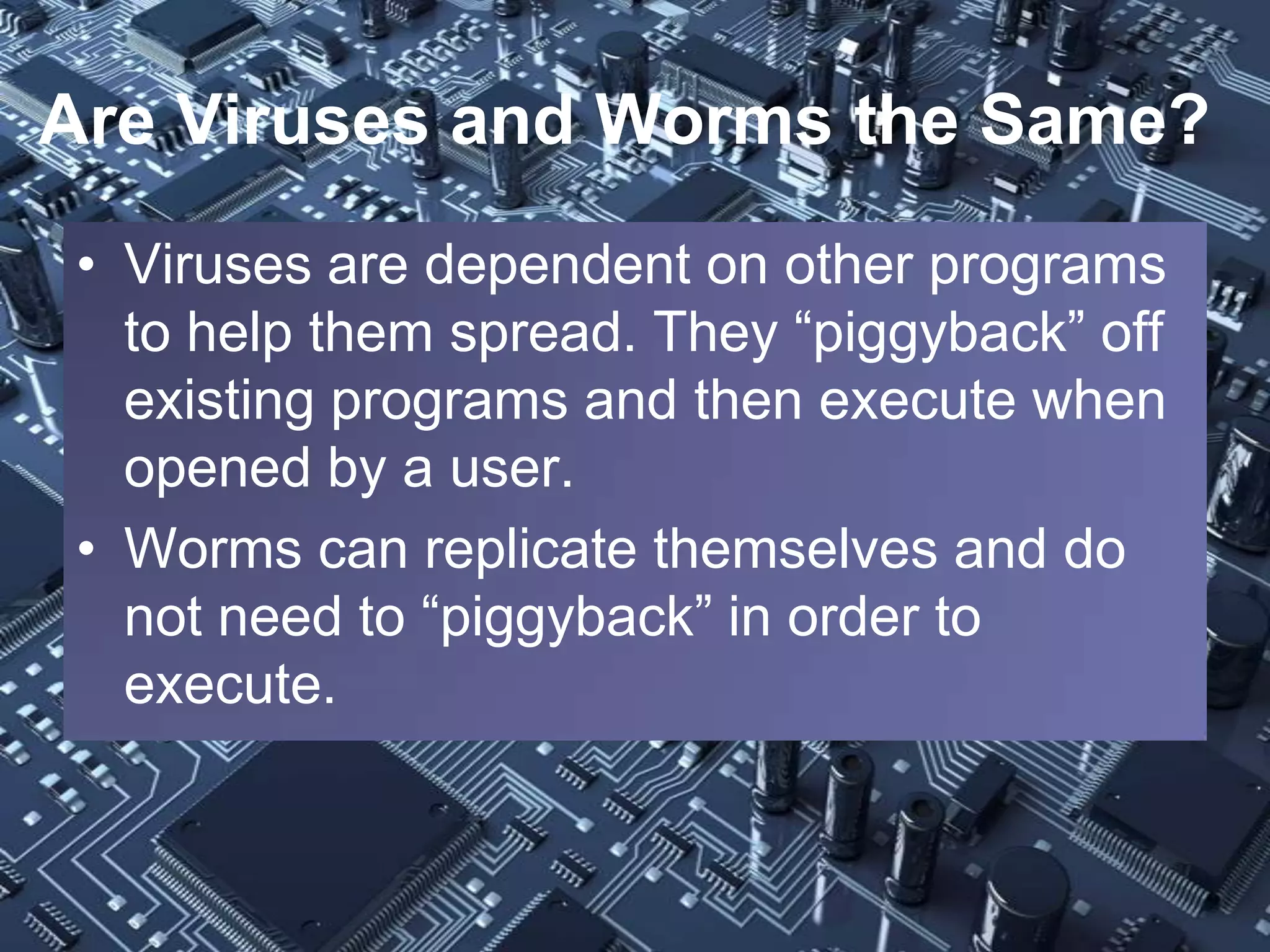
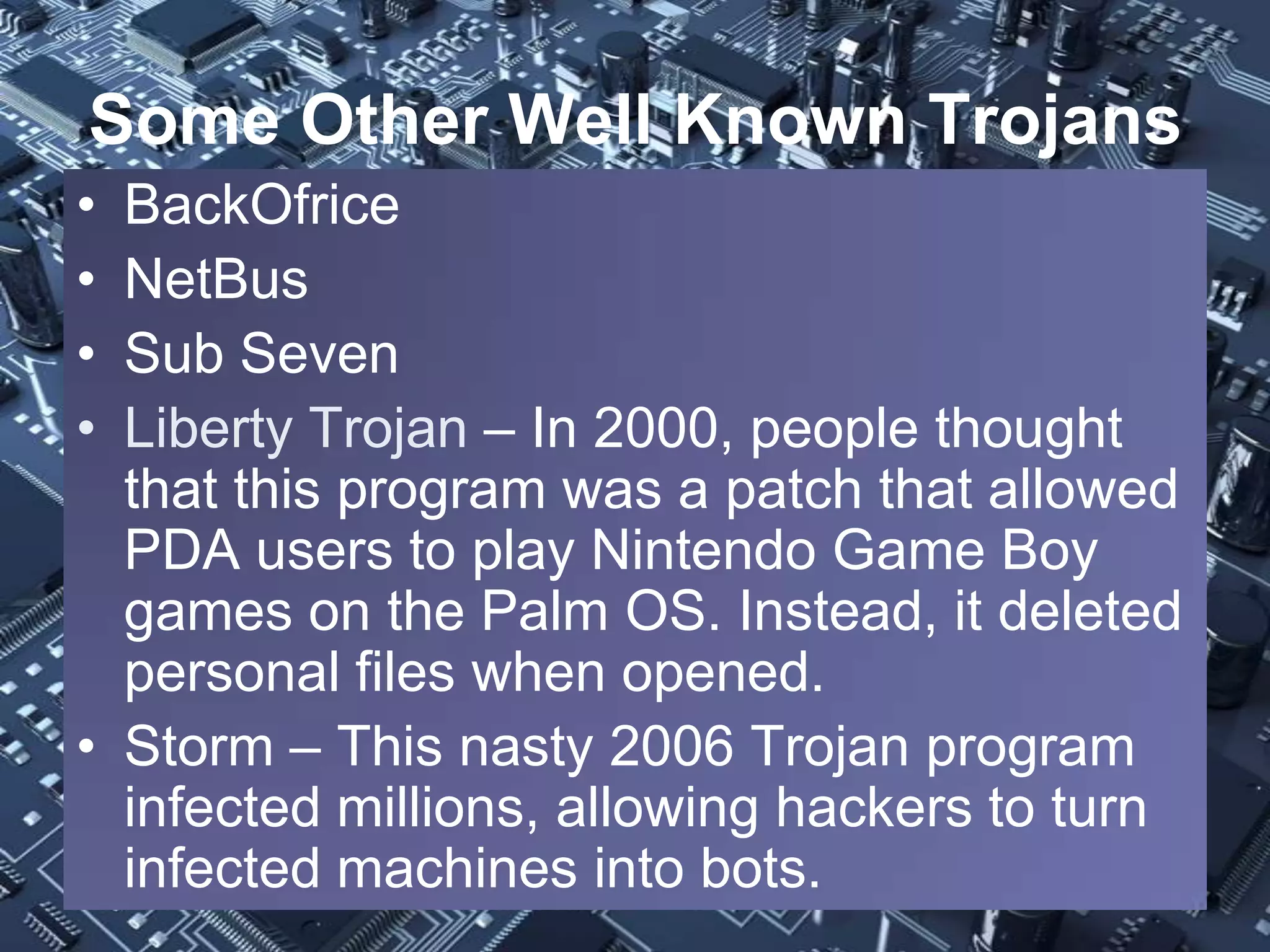
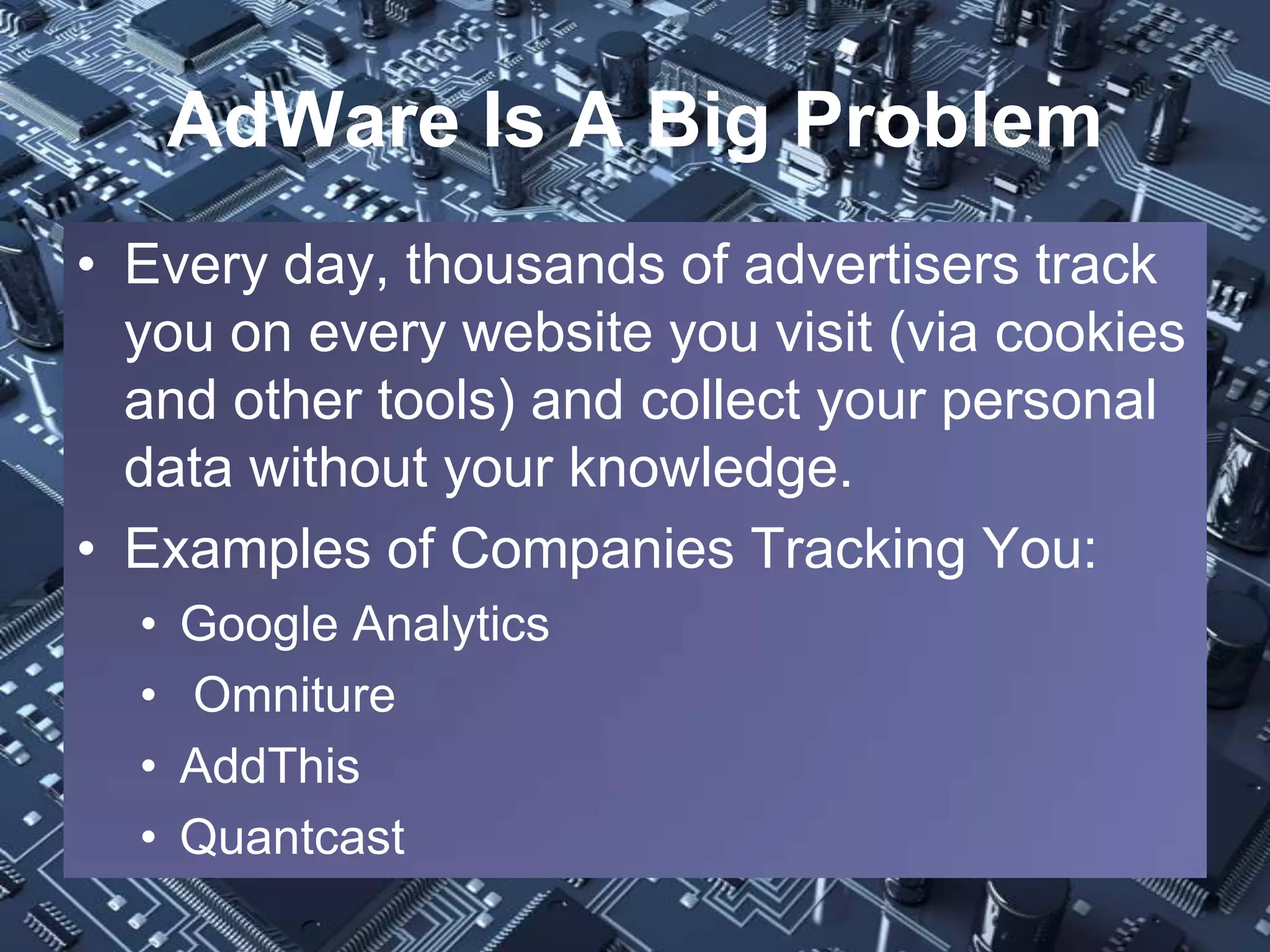
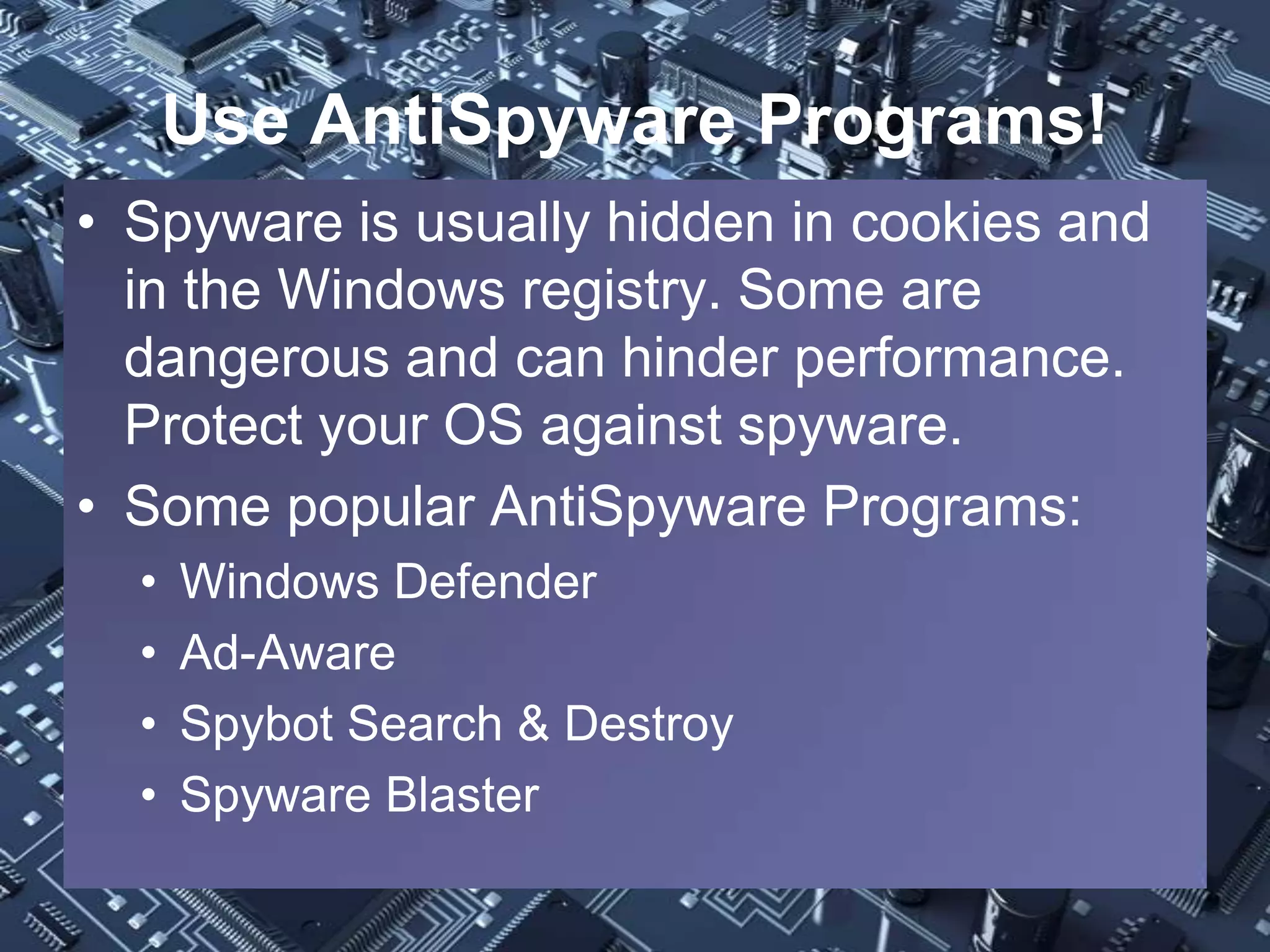
The document provides a comprehensive overview of computer viruses, their history, and various types of malware, including prominent examples like the Melissa virus and the first Trojan horse. It outlines the destructive capabilities of these malicious programs, their evolution, and methods of prevention such as using antivirus software, firewalls, and antispyware. The importance of user education and regular updates for software is emphasized as critical for defending against these threats.