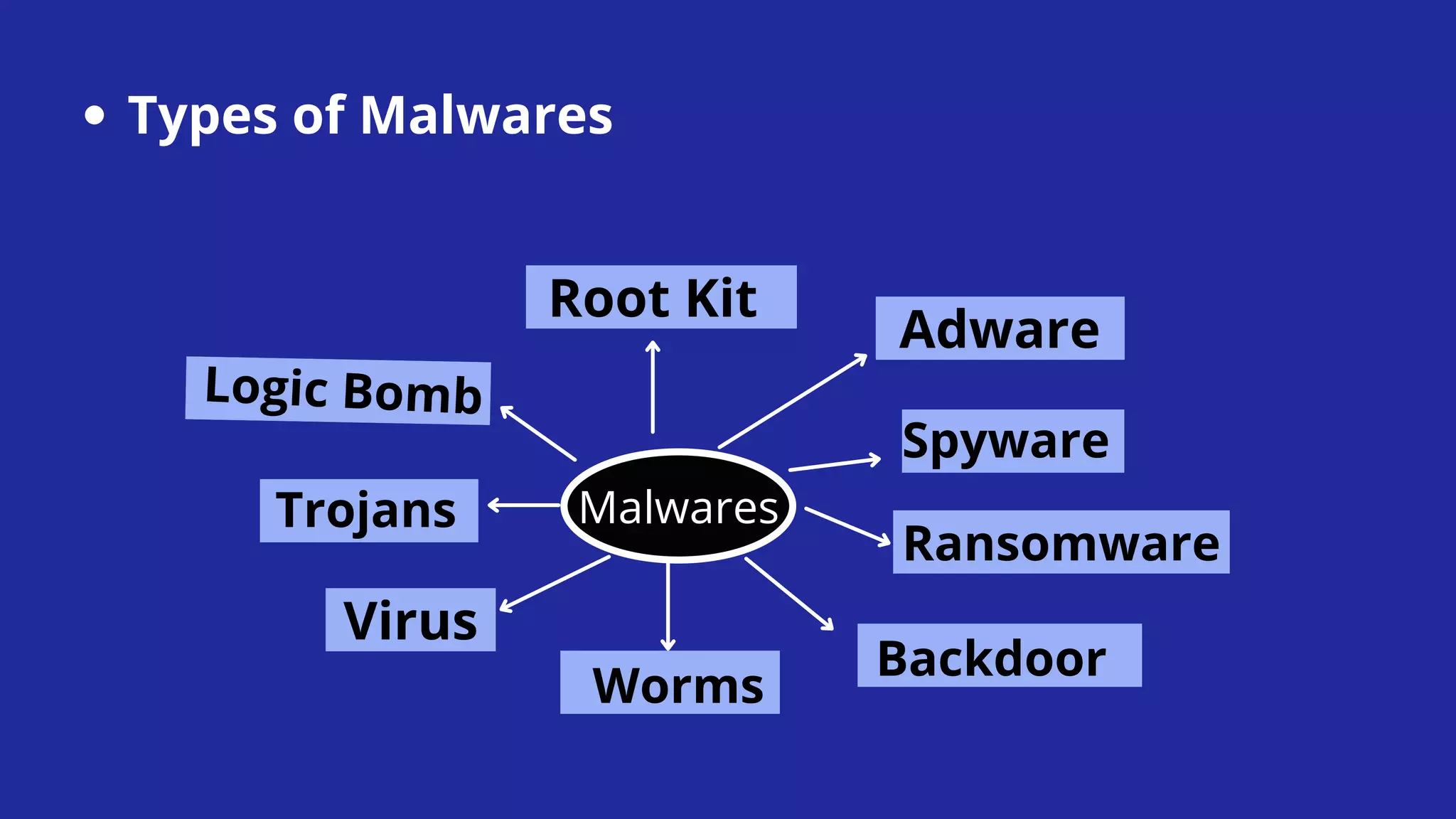
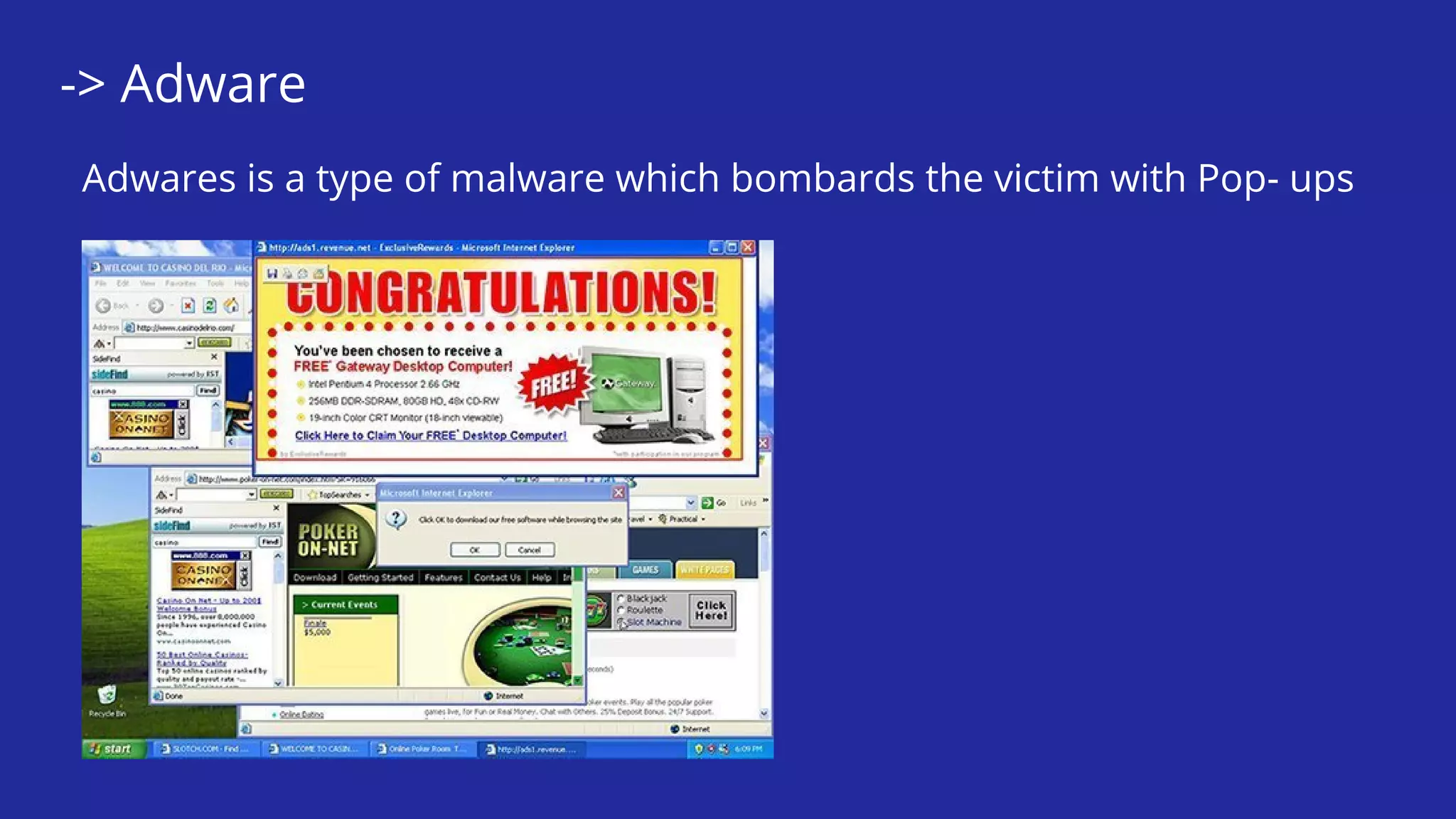
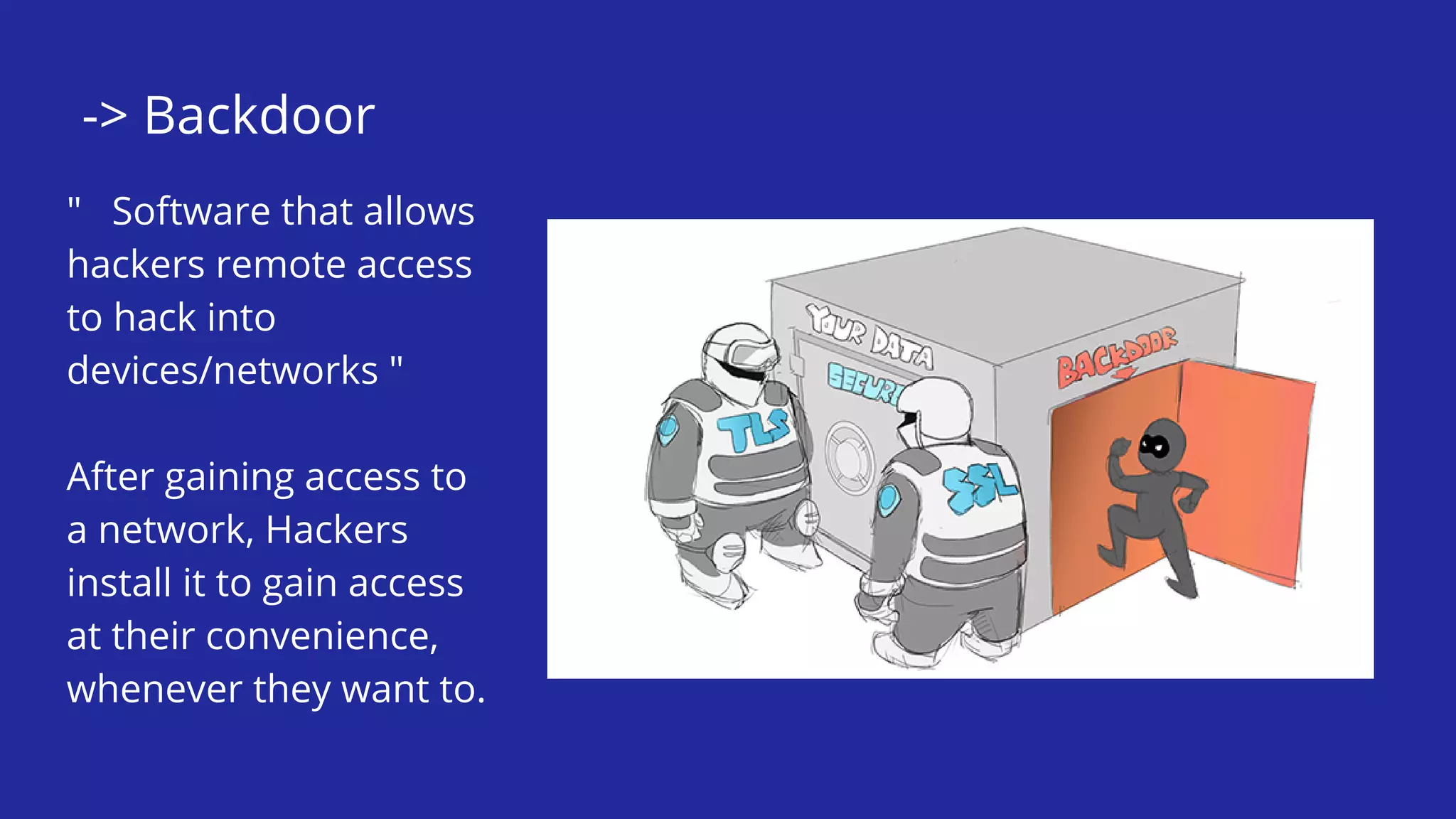
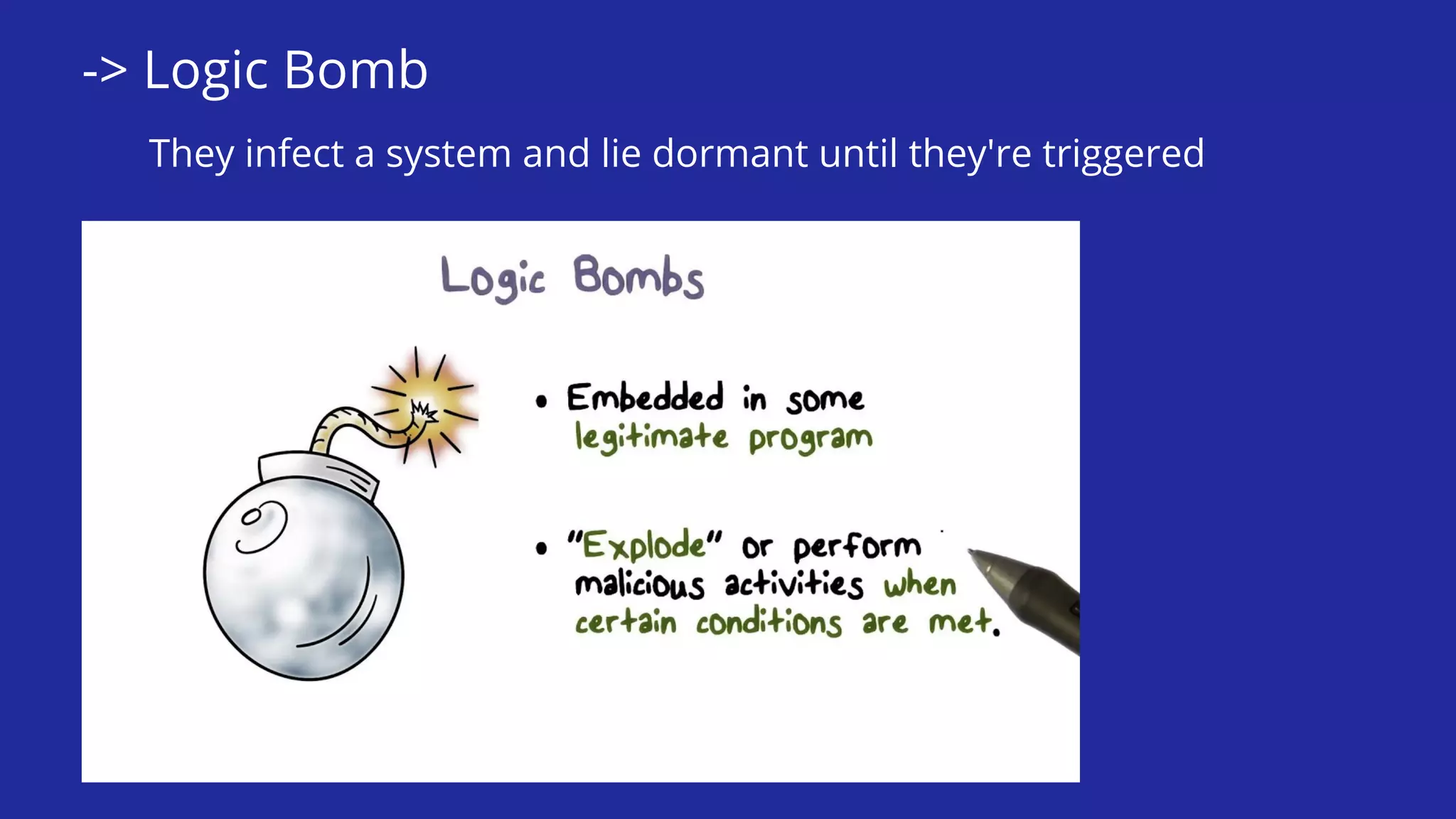
This document defines and describes various types of malware including worms, viruses, Trojans, spyware, adware, rootkits, backdoors, logic bombs, and ransomware. It explains that malware is malicious software designed to damage computers and networks. Examples of specific malware attacks discussed include WannaCry, Mirai, Ghost, Kovter, and Zeus/ZBot.