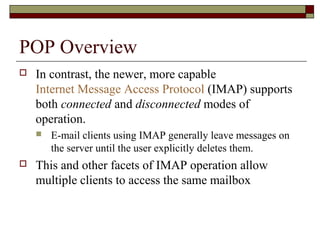
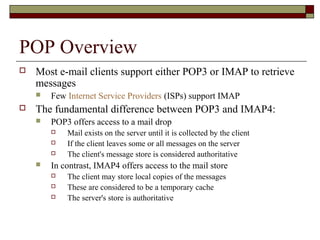
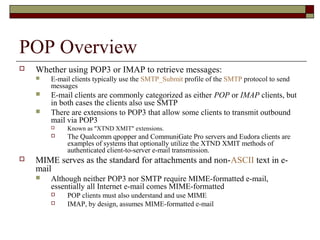
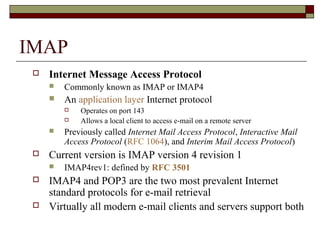
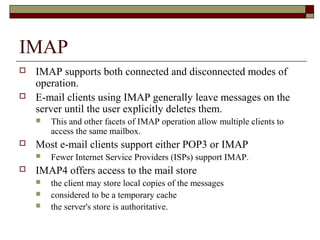
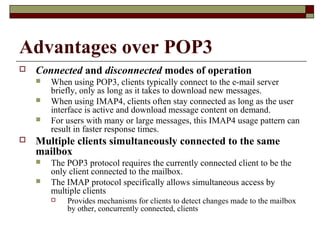
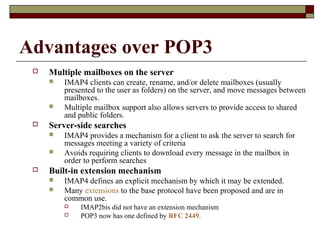
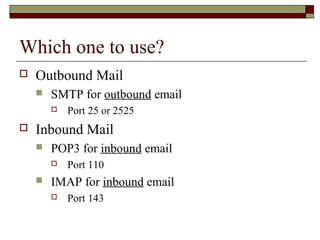
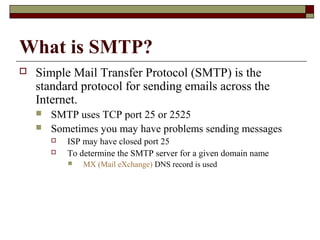
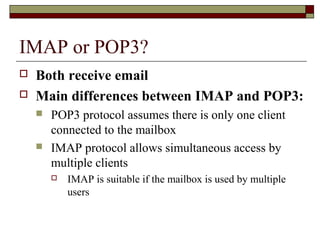
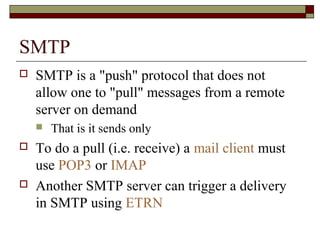
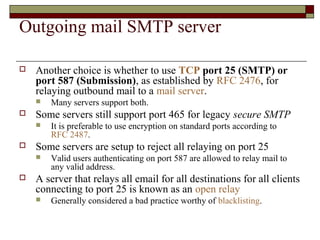
This document summarizes three major mail services - SMTP, POP3, and IMAP - and provides details on how each protocol works. SMTP is used for outbound email and uses port 25. POP3 and IMAP are for inbound email, with POP3 using port 110 and IMAP using port 143. The main difference between POP3 and IMAP is that POP3 assumes only one client can access the mailbox at a time, while IMAP allows simultaneous access from multiple clients.






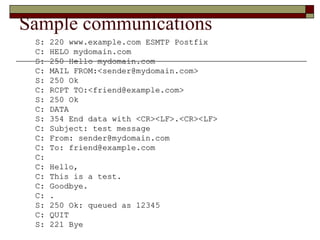


![Sample communications
For the edit planning of giant files or sending with older clients, users can
manually determine in advance the maximum size accepted by ESMTP
servers.
The user telnets as above, but substitutes "EHLO mydomain.com" for the
HELO command line:
S: 220-serverdomain.com ESMTP {postfix version and
date}
S: 220 NO UCE. {etc., terms of service}
C: EHLO mydomain.com
S: 250-serverdomain.com Hello mydomain.com [127.0.0.1]
S: 250-SIZE 14680064
S: 250-PIPELINING
S: 250 HELP
This serverdomain.com declares that it will accept a fixed maximum
message size no larger than 14,680,064 octets (8-bit bytes).
Depending on the server's actual resource usage, it may be currently
unable to accept a message this large.](https://image.slidesharecdn.com/mailservices-130526044930-phpapp01/85/Mail-services-18-320.jpg)